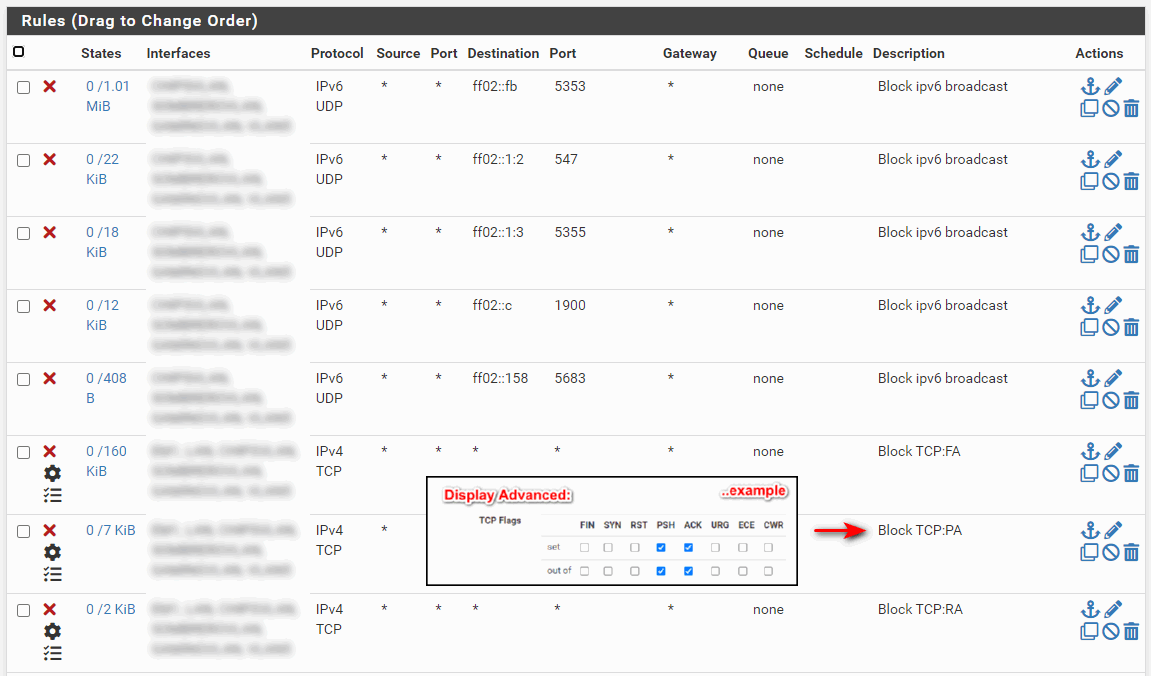
Default deny rule IPv4 (1000000104) - from Firewall to Internet
-
@rcoleman-netgate i need to try figure out what this rule looks like.. i dont think i have deleted any of this. But I could have made a mistake

-
@stiga said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
But I could have made a mistake
That's why people post their WAN, LAN and Floating rules on the forum.
Example :
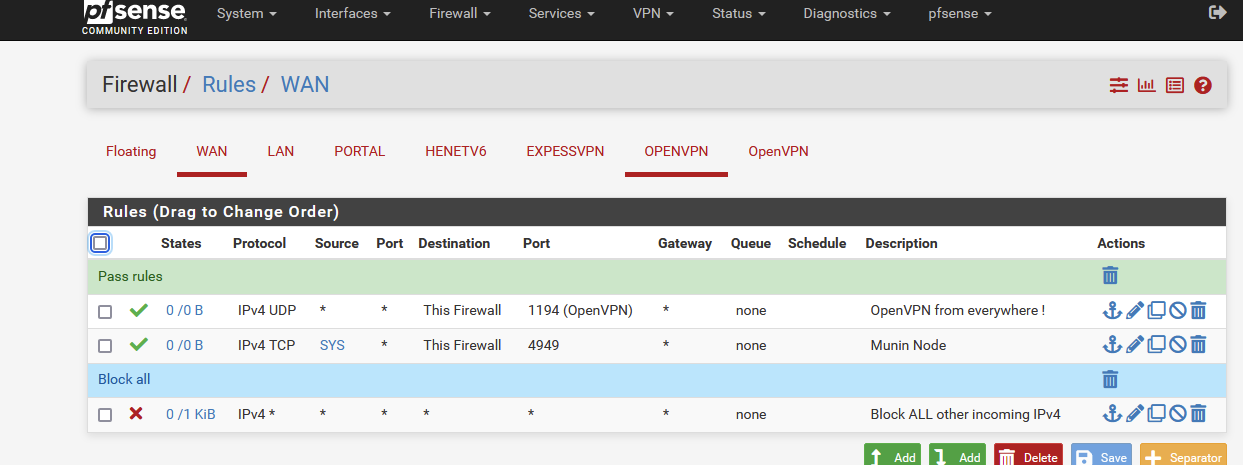
@stiga said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
i need to try figure out what this rule looks like
Ok, you've asked for it. Here you go :
You will see all the rules, also rule number 1000000104.
-
@gertjan
The public ip are like this:
-
@stiga those are all out of state outbound.. If your state table flushed then you could see those..
That 40.90.x.x is MS owned IP
173.222 is Akamai International, that 20.42 is MS as well.
I can not think of any reason why pfsense would make connections to those networks. Are you running proxy? Are you loading ip lists from pfblocker or something.
There should be no reason out of the box pfsense itself would connect to those network.. It checks for updates, and packages - those wuld not be hosted by those IPs AFAIK.
-
@johnpoz
Seems to me they are "origining on em1" wouldn't that possible be "Lan" , and that it could be M$ clients checking for updates or just babbling "home".I see a burst of that stuff (PA/FA) , whenever i "open my linux laptop" from sleep, and it tries to resume whatever it did 1h ago , when i closed the lid.
/Bingo
-
@bingo600 yeah but they are outbound, and he says its pfsense IP as source.. Which he is hiding - so assume its the wan public IP? Why would he hide a rfc1918 address.. And its outbound, with those public as destination, so how would that be lan?
-
@gertjan
cat /tmp/rules.debug
shows me a looooong list of rules and other stuff. I found this too:#---------------------------------------------------------------------------
default deny rules
#---------------------------------------------------------------------------
block in log inet all tracker 1000000103 label "Default deny rule IPv4"
block out log inet all tracker 1000000104 label "Default deny rule IPv4"@bingo600
em1 is the outside interface. I have several network interfaces on the machine.
I wish I could set the WAN as a alias - and point it to the outside interface been used. :)@johnpoz
Aha!
So i disabled all the services running.
I enabled them and let them run for a couple of minutes...
And as soon as I enabled ntopng - the 1000000104 firewall rule kicked in.ntopng - is the reason for these firewall log messages.
Should they be allowed for the ntopng to function properly?
-
@stiga said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
ntopng - is the reason for these firewall log messages.
But by default all traffic from firewall is allowed..
cat /tmp/rules.debug
pass out inet all keep state allow-opts ridentifier 1000012115 label "let out anything IPv4 from firewall host itself" pass out inet6 all keep state allow-opts ridentifier 1000012116 label "let out anything IPv6 from firewall host itself"So to be honest I don't see how those would be blocked, unless the state was killed.
-
I have an Android TV Box , used w. a 23" touchscreen (Giant wall mounted tablet) , for the wifes recipe looking etc.
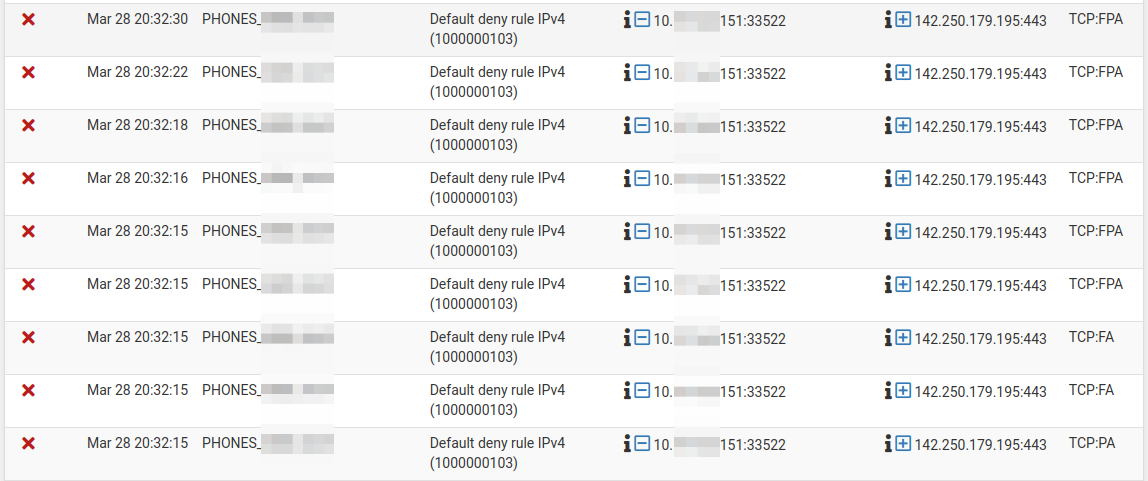
It often gives me bursts of the above.
The Box is calling back home to G , and then shuts up long enough for the state to time out. Then it tries to resume the same connection , and we have the fwall yelling ....
Same goes for my lappy , when i open the lid ...
States are timed out , but the lappy doesn't know, and firefox etc just tries to continue where it left.Btw ... How do you show those interface direction triangles ??
-
@bingo600 said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
How do you show those interface direction triangles ??
https://docs.netgate.com/pfsense/en/latest/monitoring/logs/firewall.html
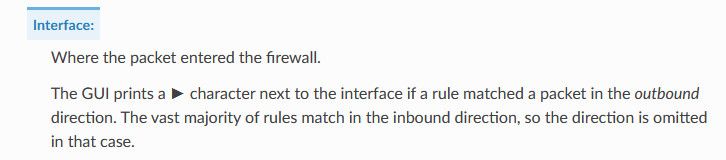
They will be shown any time something is blocked in outbound direction.
edit: Curious what version of pfsense that is - since current seems to show it like this
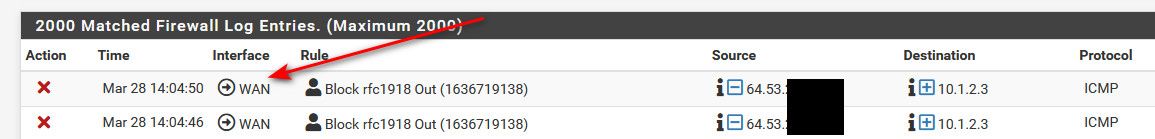
edit: odd that its saying em1 vs wan as well?
Your block is normally what you would see when traffic initiated on the lan side of pfsense, since it would be blocked as the traffic enters pfsense.
I have a specific outbound rule to block outbound of my wan to rfc1918.. Being a good netizen..
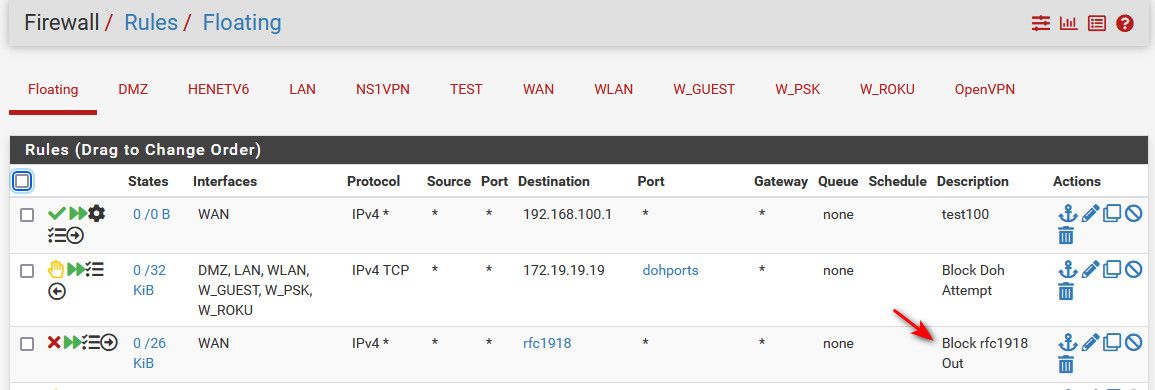
-
@johnpoz
Ahh ... Now i see
Outbound block would be either a floating or a purged state.Your RFC1918 has to be a floating, in order to block outbound .. correct ?
/Bingo
-
@bingo600 yeah see my edit, added my rule for clarity. Then forced the log by generating some traffic to some rfc1918 that is not local.
what is odd, is the let anything out from the firewall rule should allow the traffic, unless there was no state - maybe the traffic syn went out a different interface - odd why its showing em1 vs wan for example.
-
Version 2.5.2-RELEASE showing this direction triangle.
(I just haven't upgraded yet.. due to uptime ;)) -
@johnpoz
@stiga said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:em1 is the outside interface. I have several network interfaces on the machine.
I wish I could set the WAN as a alias - and point it to the outside interface been used. :)I think OP might have multiple WAN IF's
So maybe the Syn went astray ...
But i fail to see NTOPNG causing that traffic ...
Maybe the Akamai (update check) .. But the M$ traffic ???
M$ = Github ... Hmmm .... Would they have relocated GH to their ip's ?NTOPNG might put the IF's in promiscius , but it shouldn't cause any influence on states or data
-
@bingo600 said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
So maybe the Syn went astray ...
That would explain the block, but would bring about the ? of why? If state was on interface X, and then traffic tried to go out Y (where there was no state) that would kick off the default deny.
Why would the syn go out X, but at some other point would rest of the traffic try to go out Y?
-
@johnpoz said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
@bingo600 said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
So maybe the Syn went astray ...
Why would the syn go out X, but at some other point would rest of the traffic try to go out Y?
You're right , and since OP talks about switching , it seems that it is a manual task , to change WAN IF's.
-
I have several interfaces, but they are not in use..
But I only use one interface for "WAN" - I use the em1. -
This post is deleted! -
-
@stiga said in Default deny rule IPv4 (1000000104) - from Firewall to Internet:
how is rfc1918 defined?
What do you mean?
https://datatracker.ietf.org/doc/html/rfc1918
I just created an alias with the rfc1918 space in it.
I still do not see how that is happening to be honest.. There should be no reason for those rules, because traffic shouldn't be leaving from pfsense out some different interface it didn't create the state via..
 )
)