No action on LAN
-
@viragomann
I did a reset last night, and will reconfigure from beginning. Don't know if old rules are cleared automatically. One would think so.
My system is a Proliant DL360pGen8 server. I loaded pfSense 2.6.0 on to a 150G RAID6 drive. So don't know if there is any default LAN as you described.
I'll find out in an hour.... -
@ptt said in No action on LAN:
Also set up the LAN with my desired Network address and Gateway & DHCP (3 addresses)
Check: https://docs.netgate.com/pfsense/en/latest/troubleshooting/connectivity.html#lan-interface
Went through the document twice. Then reset to defaults and set up again to see if something wasn't getting cleared. Still no joy.
WAN is set correctly... STATIC IP, Gateway, Gateway is confirmed Using the correct subnet mask 30.
No Gateway set on LAN. Subnet mask 24.
DNS resolution seems to be correct, but there are settings that are not shown. I'm using WAN any LAN any
Supposedly Outbound NAT is automatically set....
Still DEAD as a DOORNAIL -
@viragomann said in No action on LAN:
@dhenzler said in No action on LAN:
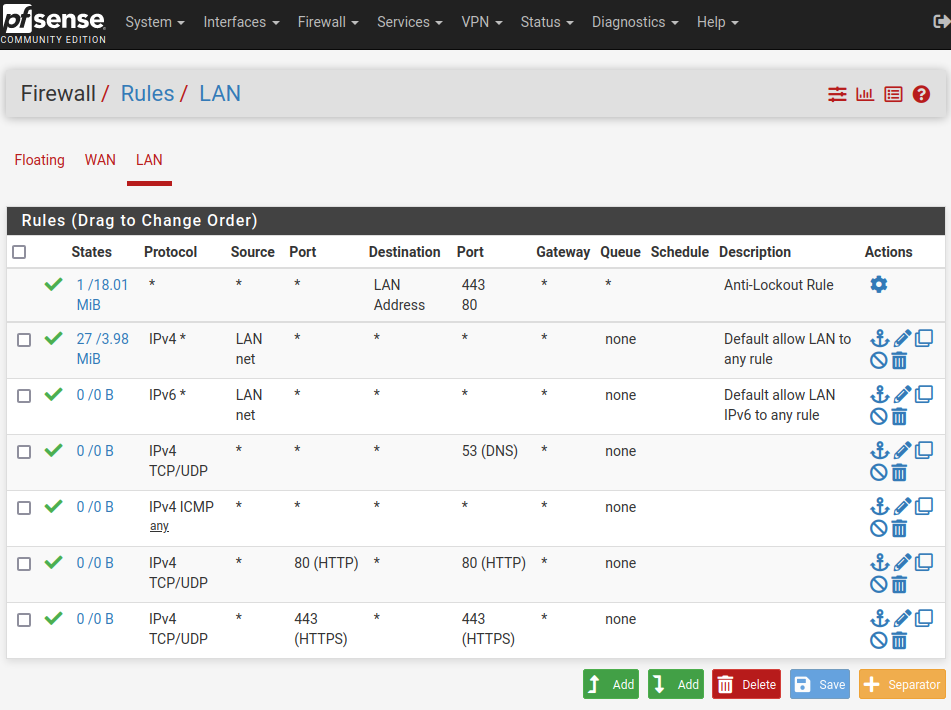
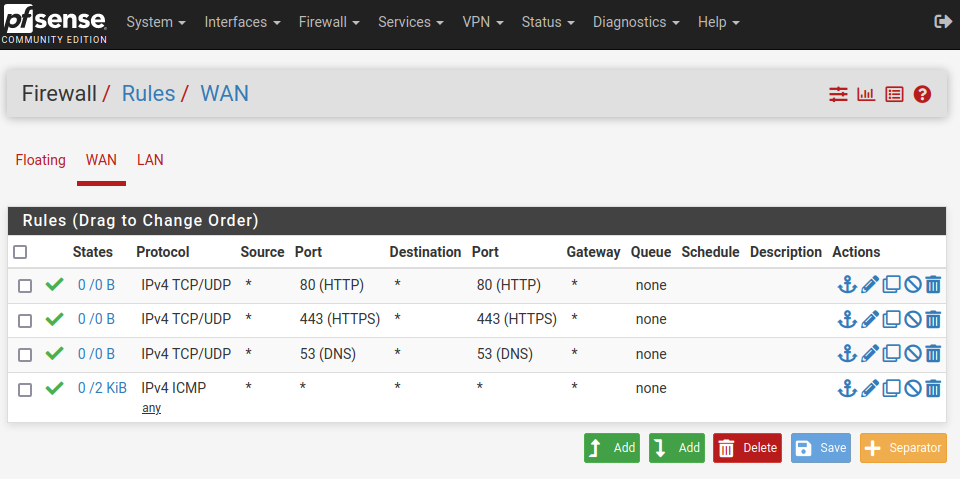
As can be seen in the screen shot above a default deny rule IPV4 is preventing DNS from providing an IP. Yet there is no such rule in the Firewall setting for WAN or LAN.
The default deny rule is a default rule built in in pfSense. It's at the end of the rule set, so that it is applied if no other (pass) rule matches before.
You need add rules to LAN to allow out outbound traffic and DNS requests to pfSense.
By default pfSense has an allow any to any rule on LAN so that it works out of the box. You might have removed this one.I host websites and so use Port Forwarding successfully on my Cisco RV-130
So you should set another port for the pfSense web GUI in System > Advanced > Admin to avoid that pfSense is catching packets to port 443.
What order should the LAN rules (added) be in...
DNS
HTTP
HTTPS
ICMPOrder is critical yes ?
-
@dhenzler
The rules are probed sequentially from top of the rule set to the bottom. If one matches it is applied and the followings are omitted.So in your example, the order does not matter at all, since each rule only matches to one specific port or protocol.
However, consider that a rule with destination = "LAN address" only allows access to pfSense LAN IP, but not to the internet.
So if you want to allow access to internet for HTTP and HTTPS you have to set the destination to "any" in these rules. -
Thanks for the rules info. I get concerned as I read, that I'm backwards and getting worn out changing things around with ZERO results.
I did however open a terminal window on the LAN and I can ping the LAN address, the Public Gateway address, and the Public Internet address. However I cannot get any response from a known IP on the Internet.
DNS resolution seems to be working as I get this...
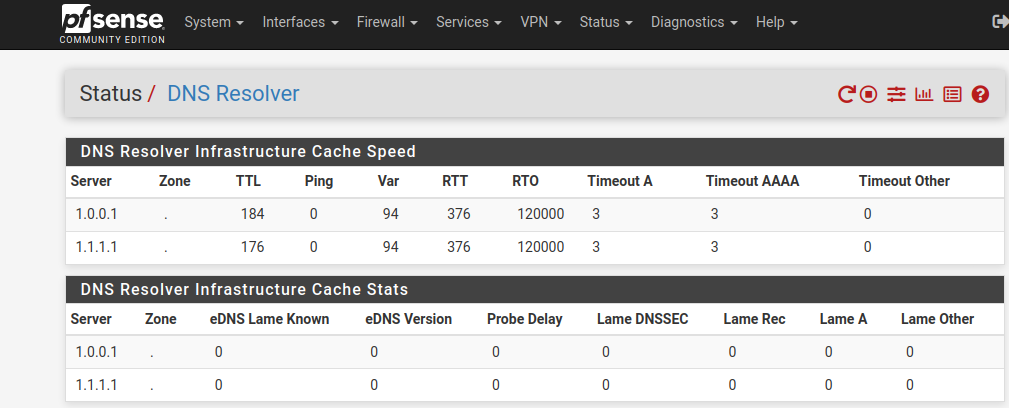
Am worn out with this... I don't understand some of the settings for DNS, and that seems to be the blockage...
If there was an easy way to get someone to finish it for $50. I'd jump at it...
-
@dhenzler
Normally that all works out of the box. Don't see why you're messing with settings before you get it up.To rule out DNS issues ping 8.8.8.8 from a LAN device.
If that's not successful ping it from pfSense. -
@viragomann
It failed to work with my WAN is why I'm "messing" with it...
Determined to figure it out.
I have always started with FRESH install, and didn't add anything not indicated by the manual pages I was sent...However it fails to work. I am connecting to a second port on my modem... it has 4 ports. I tested the port with my laptop, and it worked concurrent with my existing network... so I assumed that it would also work through the firewall. It is my intent to get it operational... configure the Port Forwarding required by my network, and cutover...
Seems like a reasonable path... eh?
It worked when I used my LAN as a WAN and hooked my laptop to a new IP as LAN... worked very welll and FAST.
However that is NOT what I need. I need it to work with existing WAN and LAN addresses so I can swap out my ol faithful Cisco RV-130
-
@viragomann
When you say "out of the box" it makes me think you believe I'm using a Netgate appliance. I'm not... It's a Proliant Server with pfSense loaded on it.So "out of the box" is a very minimal configuration...
-
This post is deleted! -
@dhenzler said in No action on LAN:
When you say "out of the box" it makes me think you believe I'm using a Netgate appliance.
No, I'm talking about the default configuration of pfSense.
When you install pfSense on whatever hardware, it asks you for the WAN interface settings and a LAN IP and network mask.
Then you get into the general setup, where you can state DNS servers.
That's in nearly cases all what is needed to get access from a LAN device to the internet.As mentioned, there is by default a rule on the LAN interface, which allows anything. But you've removed it.
There is no gateway to state in the LAN interface settings. I mentioned that already as your post let me assume you did that. But you did not respond,
So it's really hard to get forward here. -
@viragomann What are your Firewall rules for the LAN interface? "Default deny rule" means there's no rule to pass your traffic. If you created a different interface and then called it LAN and removed the original LAN that would explain the inability to look up any traffic. You could also have only TCP passing and not UDP, too.
-
@rcoleman-netgate
That's not the case... set up was done NON-GUI... set interfaces, and assigned IP'sI'm reading about DNS and hopefully will find the right combination. Being able to ping LAN, and WAN & WAN Gateway has given me some faith that I'm close.
I only get a couple hours a day to work on this, and unfortunately cannot access the Internet while doing it. Oh I can if I use my laptop. But not conveniently. I'm heading up to the LAB area now and will try a couple things.
Getting DNS working will be the ticket.
-
@dhenzler can you post an image of the LAN interface rules?
-
-
I've used a Cisco RV-130 successfully for the past 8 years
Doesn't seem that you're really experienced in firewalling.
You must not state a source port for HTTP(S) traffic! The port is dynamic and can be any.
However, apart from this you should a least get internet access from LAN with that setup. Don't you?
-
@dhenzler said in No action on LAN:
Back at the log... where it says dns is blocked.
Have you added a gateway to LAN?
I believe doing so makes it function as a WAN interface with a default block incoming rule. -
Yes, that's true... in the past I've purchased router/firewall appliances and just configured them. I'm no network expert.
Previously I had added a LAN gateway, but since have reset to defaults to be sure everything was starting fresh, and DID NOT configure a LAN gateway this time.
I think what I need now is to configure the DNS. A page full of settings, and the default ones don't work for me.
-
@dhenzler In my opinion, you should start over with a Factory Defaults under the Diagnostics tab.
Then, when your box boots back up, follow the Setup Wizard steps.
https://docs.netgate.com/pfsense/en/latest/config/setup-wizard.html
The important parts here are getting your DNS servers set correctly. You can use something like 8.8.8.8 for google, or you should also be able to leave the DNS settings blank. If you leave blank, your pfsense box will grab DNS server address from upstream, usually your ISP.
Your WAN IP address you can leave to DHCP, if you have another modem/router upstream, like from your ISP. You say you're in a LAB setting, so I'm assuming you have another device connected to your pfsense WAN port.
When you get to the LAN settings, you have to make it something different than your WAN IP address space. Something like 10.0.1.X, or 172.16.0.X is a good choice. If your WAN address is in the 192.168.X.X space, you can also assign your LAN address space in this range, but make it something different, like 192.168.30.X addresses. You can't have a subnet conflict, things break and behave really weird in a case like this. Set your LAN address space to use a /24 mask size, and you'll be good to go.
Again, reset to default settings and follow the setup wizard. You don't have to add too much stuff to the wizard, then it just works.
You might also have to reboot your ISP modem/router for pfsense to work properly. This is a function of the ISP gear, not your pfsense box. The ISP equipment usually has to "lock on to" a new MAC address to begin sending traffic.
-
@akuma1x
Thank you for the advice. However I've been down that road a couple times already. Additionally the task at hand is to configure it to be configured so that I can swap out the existing ROUTER/FIREWALL.I have a STATIC IP thus DHCP on WAN won't work for me, and setting up the WAN to use my existing LAN as a source worked. However that puts me back to SQUARE ONE where configuring it to be a SWAP for the ol firewall is concerned.
The Rules thing is confusing to me.... WAN or LAN rules can have port specific settings... is that on the SOURCE or DESTINATION or BOTH?
I've posted much of my configuration, and no one has addressed the settings as correct, or incorrect.
As I write the TCP/UDP ports are blocked (see previous clips) which is preventing DNS from working.
I just switched from DNS Resolver to DNS Forwarding as it seems more in line with the way it's been handled before.
The LAN is still blocked from sending/receiving port 53 from pfSense
Off to a late breakfast and the dump!
-
@dhenzler said in No action on LAN:
@akuma1x
Thank you for the advice. However I've been down that road a couple times already. Additionally the task at hand is to configure it to be configured so that I can swap out the existing ROUTER/FIREWALL.No offense intended, but then you didn't set it up correctly. I have setup pfsense dozens of times, as well as others here that have done it many many many more times than that. The default factory settings work almost all the time.
Let's go thru the setup wizard after a factory reset, one step at a time...
- You get the welcome splash screen, click the next button.
- General Info screen, you can leave all of this blank. Like I said, if you want to use google DNS servers, you can set them here. Let's do that, so enter 8.8.8.8 in the primary and 8.8.4.4 in the secondary boxes. Leave the "override" box checked, as this will force DNS requests to use google for now.
- NTP and time zone - all you have to do here is pick your time zone out of the list.
- WAN config - this is where I think you're getting messed up. You say you're connecting it to one of the 4 ports on your ISP modem/router. That's fine and works, if you're going to leave the ISP modem in "router" mode. You typically don't want to do this, since you first have to point traffic on your ISP router to your pfsense router, then on your pfsense router to your internal machines. That's called double NAT and is generally not good. But, for testing purposes, getting a DHCP address from your ISP modem/router is ok. So let's leave it DHCP for now. In the future, if you want to use your pfsense box as your edge device, you're going to have to set your ISP modem/router into "bridge" mode. This passes all traffic directly from the internet to pfsense and then you use the static IP address from your ISP on the WAN port. Using this method, you then setup firewall rules to get internet traffic to your internal LAN devices. Be aware, if you use static IP address on your WAN interface, you also need to know the address, the network mask size, and the upstream gateway info from your ISP.
- LAN interface - this is also where I think you're getting confused. If you use a DHCP address on your WAN interface, like I recommended above, for testing purposes, you need to use a DIFFERENT address range here. For example, if your ISP modem gives your pfsense WAN interface a 192.168.1.X address, in the LAN address, you must use something different, like 192.168.8.X for example. Or 172.16.0.X as another example. It's totally up to you, but this address MUST be private address space. Use a subnet mask size of /24 for now, that's the default.
- Set a new admin password and click the next button.
That's it, you're done. All you have to do is wait about a minute for settings to be saved, then use the new LAN address you just programmed in step 5 above. You should be able to log in to the web gui. That's all there is to it.
You say this pfsense box is going to be the swap box for your existing router. That's fine, and can be addresses a little later. Get the default settings (the six steps above) going first, then we/you can worry about the specific settings for the swap later.