Snort Application and site blocking Problem!
-
Hello, I need your help with Snort;
I made the settings by following youtube and this site. However, I could not do any application or site blocking. (for example, whatsup, telegram, anydesk,
Facebook)
The thing is, I blocked all messaging apps, but it still doesn't. how can I do that?
I looked at the site a lot and couldn't figure it out.
2) If we leave the IPS Policy Selection setting in balanced mode, does it release everything or does it block bad/unwanted traffic with certain rules?
safe mode required for partial blocking?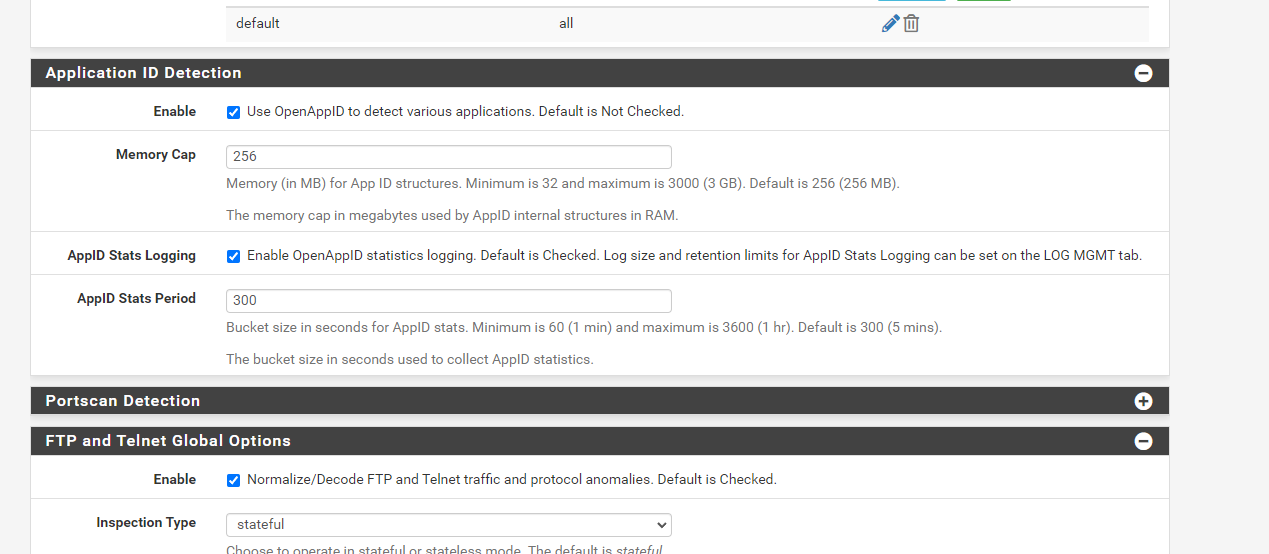
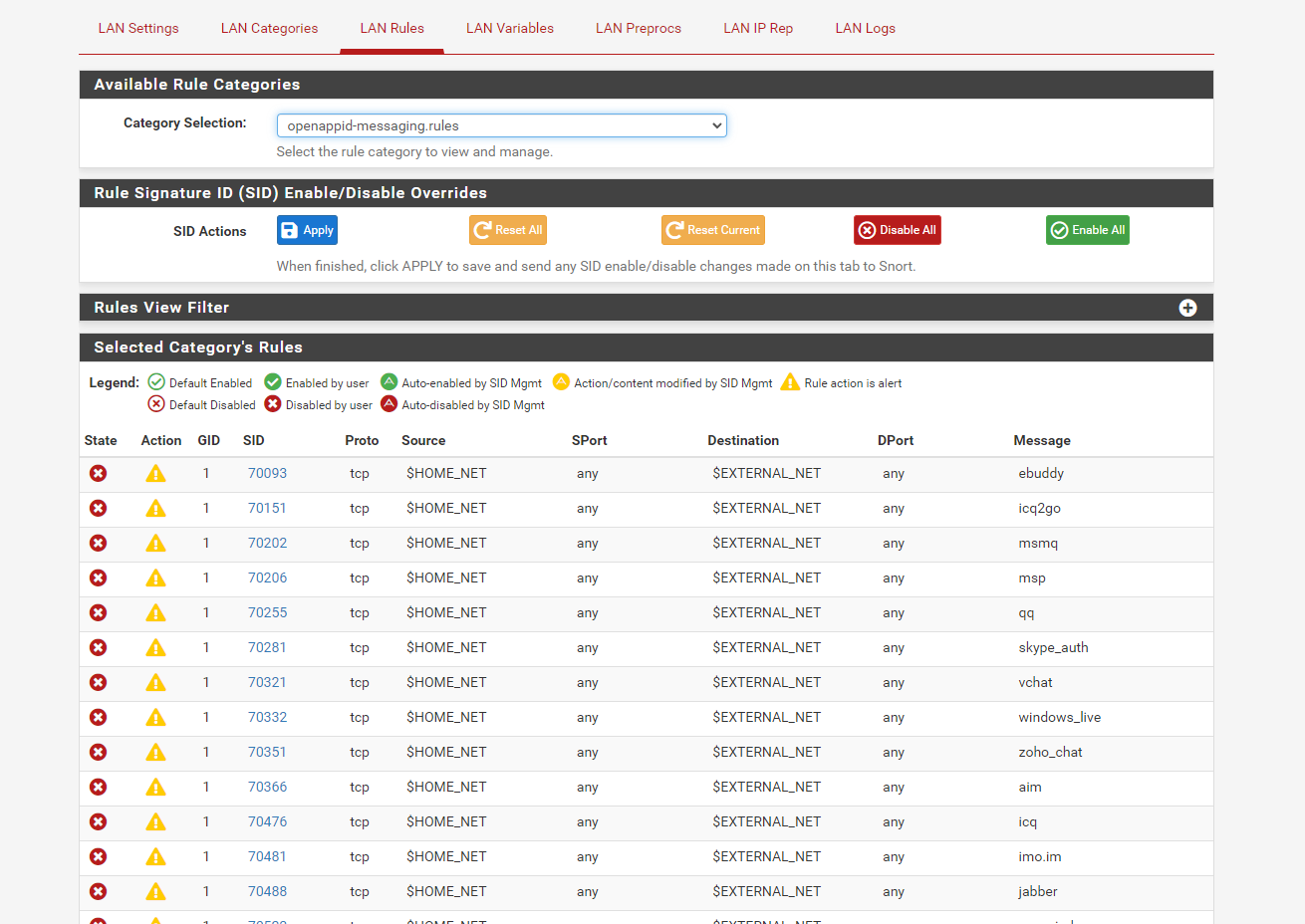
 image url)
image url) -
You actually have NOT blocked all messaging apps. You have in fact just DISABLED all of those rules, so none of them are being loaded and used. From the looks of your posted screen captures, you've done the exact opposite of what you desired. That's one reason you are not seeing any blocks.
On the RULES tab, when you "User Force Disable" a rule, that means you turn that rule off and it is ignored by Snort. It is never loaded into memory. So the first thing you need to do is go to that RULES tab, select each category you clicked to "disable", and click the button "Reset All" to restore the default states for the rules in each category.
What YouTube site did you visit? And why did you click the "Disable All" button on the RULES tab? The "Disable" button there disables a rule, or turns it off so Snort ignores that rule and does not inspect traffic against it. And if you click "Disable All", that will disable ALL of the rules so that Snort loads none of them in that category. You want rules "enabled" in order for Snort to check traffic against them and take action. Generally speaking, especially if administering an IDS/IPS is new to you, you should not click a single thing on the RULES tab. Don't touch anything on that tab! Later, as you gain experience, you might choose to customize rule choices using the options on the RULES tab.
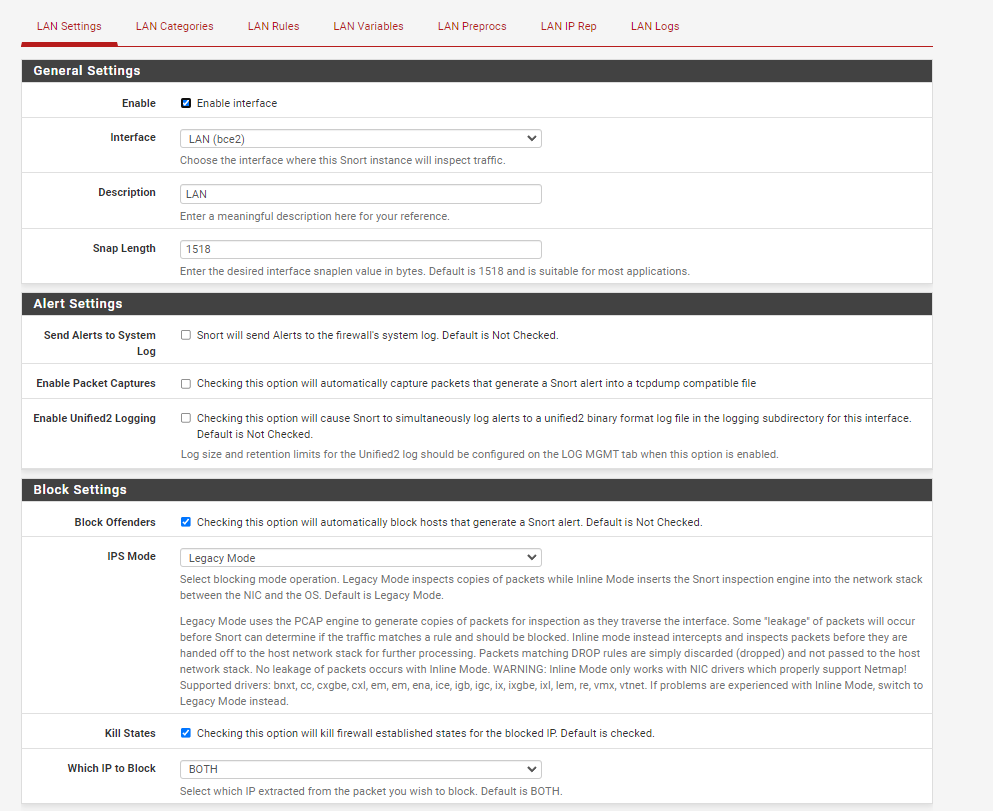
The second requirement for actually blocking traffic is to have either Legacy Blocking Mode or Inline IPS Mode enabled on the INTERFACE SETTINGS tab for the interface. Have you done that?
It seems you need to read through the official Netgate documentation on configuring the Snort package. You can find that here: https://docs.netgate.com/pfsense/en/latest/packages/snort/setup.html. One suggestion, while the official docs screen shots show Snort configured on the WAN, I strongly suggest you use the LAN instead. I need to get around one day to updating the documentation image.
-
-Settings
When you do as in the picture, messaging applications started to be blocked. (except signal)
But it does this as a category. if I only want to do one how do I do it?
E.g; Whatsup, or any website.-After reading your (bimeks) advice in the Forum, I configured it in the LAN.
-I've looked at the pfsense documentation. but again more careful
I will examine.Thank you for your interest.
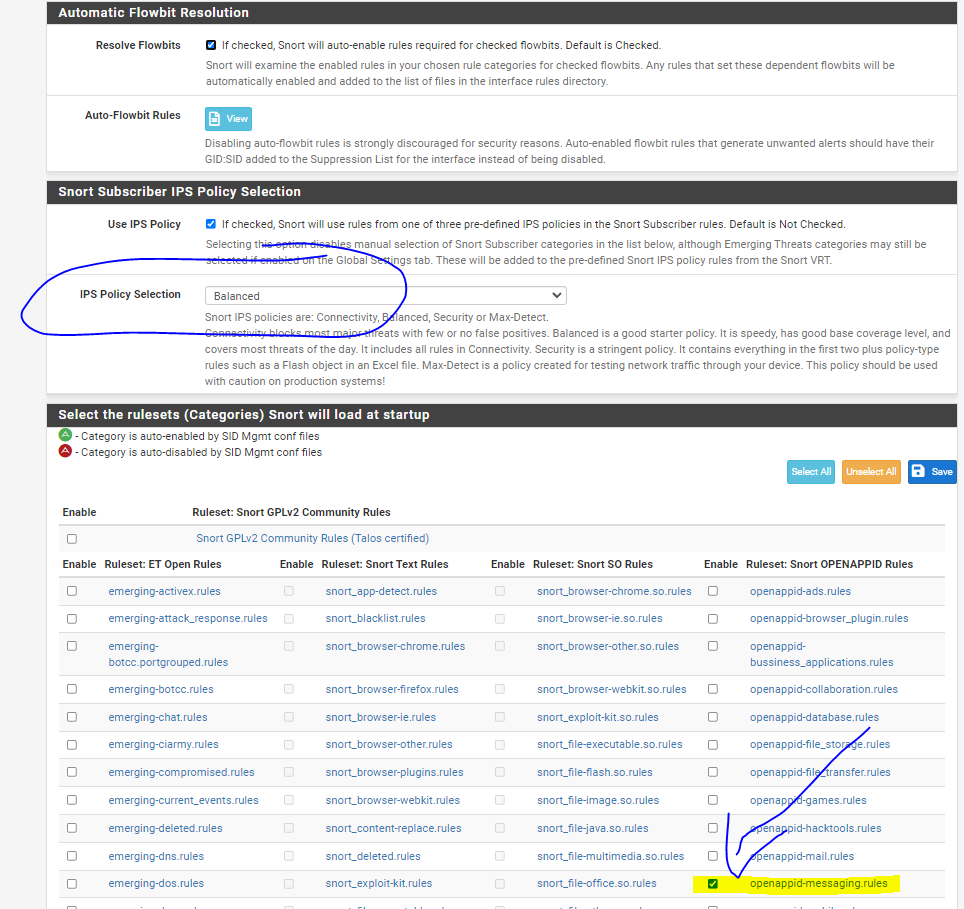
-
@enesas
Do you understand what an IPS Policy is in Snort? Why do you have the IPS Policy Selection box circled in the image above?OpenAppID requires you, as the admin, to either download or create your own text rules in order to actually detect and block applications. If you want customized action by OpenAppID, then you must write your own customized rules to achieve that.
If you want to only activate a single rule, that is best done using the SID MGMT feature tab. There are example configuration files available on that tab. There are also a couple of sticky threads at the top of this forum that address using SID MGMT with Snort and Suricata. Both packages work the same way with regards to SID managment.
-
@bmeeks I reviewed what you said. However, I couldn't quite figure it out.
For example, is there an example list of blocked drops for Youtube or another site? Also, when you add this list to SID MGMT, will it work directly, is a different setting required?When the communication problem due to language is added, it becomes a little difficult to understand.
I'm sorry for making you tired.
-
@enesas said in Snort Application and site blocking Problem!:
@bmeeks I reviewed what you said. However, I couldn't quite figure it out.
For example, is there an example list of blocked drops for Youtube or another site? Also, when you add this list to SID MGMT, will it work directly, is a different setting required?When the communication problem due to language is added, it becomes a little difficult to understand.
I'm sorry for making you tired.
An IPS Policy is a pre-defined collection of rules designed to provide a given base level of security. There are four defined policies, but only three of them are useful in a production setup. The fourth policy (max-detect) is an extreme security policy designed primarily for testing only. It will block all manner of likely desired traffic.
Here are the three IPS Policies (ordered by increasing protection):
- IPS Policy Connectivity
- IPS Policy Balanced
- IPS Policy Security
These are created by the Snort rule authors (also known as the Snort Vulnerability Research Team, or VRT). The policies exist via metadata tags included within each Snort text rule (but excluding OpenAppID; those rules are NOT part of any IPS Policy directly). When creating rules, the Snort VRT will tag each rule with one or more IPS Policy tags. That allows an automated rule selection algorithm to pick the rules tagged with a chosen policy tag.
For IDS beginners, it is best to start with the IPS Policy Connectivity policy as that one provides reasonable protection from common threats without generating too many false positives. I strongly recommend you never go higher than IPS Policy Balanced unless you are protecting military secrets or something. The "Security" policy will block a ton of desirable stuff -- meaning lots of "normal" network traffic will get blocked and cause you headaches and frustration.
However, if new to an IDS/IPS, you should start with NO blocking enabled. Choose rules but do NOT enable blocking at first. You need to let your choice of rules run in your network environment for several days or even weeks. Check the ALERTS tab often in Snort to see what alerts have triggered. Research them and determine if they might actually be false positives in your network. That is highly likely these days due to the way modern web sites work to serve adds and due to the encryption of lots of other traffic. For false-positive triggering rules, you should probably disable them.
Now lets talk about OpenAppID. For that to work you must have two different kinds of rules downloaded (or else custom created by you, the admin). One requirement is the OpenAppID rule stubs that come from the Snort VRT. That set of stubs defines the applications that Snort OpenAppID can detect and gives Snort the internal "how-to" instructions for detection. The other required piece of OpenAppID is a set of text rules that leverage those detector stubs to actually scan traffic and produce alerts. This latter set of text rules tells Snort which applications you want to look for. You must either write these text rules yourself, or you can take advantage of a starter-set of OpenAppID text rules created by a group at a University in Brazil. You can enable the download of these starter rules on the GLOBAL SETTINGS tab of Snort where you enable the download of the OpenAppID stub rules. Then on the CATEGORIES tab you can enable one or more categories of OpenAppID rules. But be aware these categories were created by a team of volunteers (University students, actually), so they may not be complete. Additionally, they have not been updated in several years. Thus many more modern applications are missing detection rules and thus won't be detected by Snort using these OpenAppID starter rules. So for any missing applications in the starter rules package, you would need to create your own Custom Rules containing the necessary syntax. You can find out more about writing OpenAppID rules here:
https://blog.snort.org/2014/04/openappid-application-rules.html
You can search on Google for other OpenAppID tutorials. Be aware that most of the recent effort with OpenAppID has been targeted for Snort3 and not legacy Snort as used on pfSense. The pfSense package is based on Snort 2.9.x and is NOT compatible with Snort3 rules! Do not attempt to use any Snort3 rules on pfSense. Doing so will totally break the Snort package on pfSense.