pfsense constantly losing connectivity to NordVPN
-
* [code_text](link url -
@vova-0 What ???
-
@pftdm007 said in pfsense constantly losing connectivity to NordVPN:
Re-switching the default GW to NORDVPN
That's a bad idea, I think.
Better select "Automatic" for the default gateway.
I guess, NordVPN will push the default route to you. So the gateway changes anyway, when the VPN is established. Otherwise you could set that in the client settings. -
When I select "automatic", my public IP becomes visible... That's an issue I had while setting up everything and could NEVER find the cause of this issue... Very strange, NordVPN were unable to troubleshoot....
The workaround was to manually set the default GW to NORDVPN which made my public IP hidden.
Perhaps that workaround is causing other issues afterall... Your thoughts?
-
I think DNSBL is the root cause of all my problems. I just realized that on the subnets behind DNSBL, my public IP is visible to the internet, but on the subnets not behind DNSBL, the public IP is hidden.
Moreover, DNSBL seems to be intermittently working as sometimes forbidden websites are accessible, sometimes not...
I think the overall issue is some sort of bug or corruption or just that it is impossible to use OpenVPN+DNSBL+VLAN's with pfsense... Hopefully I am wrong.
Out of curiosity, are anyone using DNSBL alongside OpenVPN?
If so, how are the DNS servers passed to the LAN clients behind the VPN? Where are these DNS server defined ??
-
@pftdm007 said in pfsense constantly losing connectivity to NordVPN:
The workaround was to manually set the default GW to NORDVPN which made my public IP hidden.
Perhaps that workaround is causing other issues afterall... Your thoughts?By setting the default gateway to NordVPN will cause that there is no traffic able to going out, when the VPN is down. Hence also DNS request cannot be not passed out and resolution will fail.
This can only work, if you state an IP for the VPN server and the VPN connection is up all the time.
I think DNSBL is the root cause of all my problems. I just realized that on the subnets behind DNSBL, my public IP is visible to the internet, but on the subnets not behind DNSBL, the public IP is hidden.
So you might rather talk about DNS leaks than your upstream traffic going out to WAN?
How is the DNSBL done in your setup? Is it on pfSense or on an other server?
-
@pftdm007 said in pfsense constantly losing connectivity to NordVPN:
RESOLVE: Cannot resolve host address: ca1234.nordvpn.com:1194 (Name does not resolve)
How do you have DNS configured? This makes me wonder if it's getting into a situation where it's trying to resolve hostnames via your VPN gateway when the VPN connection is down. I would highly recommend using IP addresses instead of hostnames in your VPN client configurations so that the establishment of VPN client connections is not dependent on DNS at all.
-
@viragomann said in pfsense constantly losing connectivity to NordVPN:
So you might rather talk about DNS leaks than your upstream traffic going out to WAN?
Yes I am. Long story short, if I do a "whats my IP" search, google returns Nord's IP, Duckduckgo returns my public (real) IP from ISP, expressvpn also returns my real IP, etc... Its all over the place. Clearly something's not right. Just to be clear, this ONLY happens when the system default GW is set to automatic or WAN... Not with Nordvpn. However setting the default GW to Nordvpn, the issue I described here initially will happen (Cannot resolve host address: ca1234.nordvpn.com:1194 (Name does not resolve))
Also DNSBL is on pfsense, on the same machine as OpenVPN. DNSBL protects VLAN 1 & 2, while VLAN3 bypasses DNSBL completely (the DNS servers IP's are passed to the clients from the DHCP server settings).
In short:
VLAN 1 -> DNS servers blank in DHCP server so unbound is used , FW rules send traffic to Nord's gatewayVLAN 2 -> Identical to VLAN1
VLAN 3 -> DNS servers are specified by DHCP server so DNSBL is completely bypassed, FW rules send traffic to Nord's gateway
@thenarc said in pfsense constantly losing connectivity to NordVPN:
How do you have DNS configured? This makes me wonder if it's getting into a situation where it's trying to resolve hostnames via your VPN gateway when the VPN connection is down. I would highly recommend using IP addresses instead of hostnames in your VPN client configurations so that the establishment of VPN client connections is not dependent on DNS at all.
I will try using Nord's IP instead of the FQDN in OpenVPN's client config and see what happens, but in the end, why do I need to set the system's default gateway to Nordvpn instead of automatic to prevent DNS leakage (or my real IP being visible)?
-
@pftdm007
So you will have to direct DNS upstream traffic from unbound is directed out to the VPN gateway.If you only need the Resolver for VLANs which should not get internet access, when the DNS is down anyway, you can simply state to VPN interface only for outgoing connections in the settings.
If you want unbound to also resolve when the VPN is down, you will have to run it in forwarder mode. So it directs DNS requests to the servers stated in General settings accordingly to the routing table.
-
@viragomann said in pfsense constantly losing connectivity to NordVPN:
So you will have to direct DNS upstream traffic from unbound is directed out to the VPN gateway.
Not sure I understand that. Can you elaborate a bit? Unbound is serving VLAN 1 & 2 because I want DNSBL on those. VLAN3 doesnt need DNSBL (its a DMZ) so I am passing Nord's DNS servers directly via the DHCP server settings. Simple enough.
@viragomann said in pfsense constantly losing connectivity to NordVPN:
If you only need the Resolver for VLANs which should not get internet access, when the DNS is down anyway, you can simply state to VPN interface only for outgoing connections in the settings.
Sorry, this sentence doesnt make sense to me.
@viragomann said in pfsense constantly losing connectivity to NordVPN:
If you want unbound to also resolve when the VPN is down, you will have to run it in forwarder mode.
Its already running in FW mode, always has been.
-
@pftdm007 said in pfsense constantly losing connectivity to NordVPN:
why do I need to set the system's default gateway to Nordvpn instead of automatic to prevent DNS leakage (or my real IP being visible)?
Presumably because NordVPN is not the default gateway.
I guess, you have checked "Don't pull or don't add routes" in the client settings.@pftdm007 said in pfsense constantly losing connectivity to NordVPN:
@viragomann said in pfsense constantly losing connectivity to NordVPN:
So you will have to direct DNS upstream traffic from unbound is directed out to the VPN gateway.
Not sure I understand that. Can you elaborate a bit? Unbound is serving VLAN 1 & 2 because I want DNSBL on those. VLAN3 doesnt need DNSBL (its a DMZ) so I am passing Nord's DNS servers directly via the DHCP server settings. Simple enough.
pfSense routes out upstream traffic accordingly to its routing table as already mentioned. So if your WAN gateway is the default, DNS traffic goes out on WAN.
Hence if you want VLAN 1 & 2 to use unbound cause of DNSBL you have to direct outgoing requests from unbound to the vpn gateway.
My assumption is that VLAN 1 & 2 should never go out to the WAN, but only to the VPN. If that's the case, you can also direct ounbound's upstream strictly to the VPN gateway.
But I think, that won't be possible in forwarder mode, except if you state the NordVPN's IP in the client settings. -
@viragomann said in pfsense constantly losing connectivity to NordVPN:
I guess, you have checked "Don't pull or don't add routes" in the client settings.
You are right. This was recommended by Nord's if I recall correctly to minimize chance of DNS leaks...
@viragomann said in pfsense constantly losing connectivity to NordVPN:
Hence if you want VLAN 1 & 2 to use unbound cause of DNSBL you have to direct outgoing requests from unbound to the vpn gateway.
Already setup Unbound to use only the VPN gateways.
@viragomann said in pfsense constantly losing connectivity to NordVPN:
My assumption is that VLAN 1 & 2 should never go out to the WAN, but only to the VPN
NONE of the VLAN's should go out thru WAN, all should go thru VPN. The only distinction is that VLAN3 doesnt use Unbound for DNS resolution but use Nord's DNS directly. However, it is forced to go out thru VPN because of the FW rule which forces traffic to use the VPN gateway.
Thats the only interface behaving 100% as expected. Bypassing unbound seems to do the trick........
-
Regarding the main issue of this thread
It is still a no go... A few days ago I setup a multi-gateway VPN group following the instructions found here. First of all, congrats to whoever wrote this site, its flawless and super well detailed.
Things worked out very reliably until now. FYI I work from home and use my internet connection with pfsense all day. About 10mins ago, I got a notification email from pfsense saying
Notifications in this message: 1 ================================ 16:49:13 MONITOR: NORDVPN3_VPNV4 has packet loss, omitting from routing group NORDVPN_Group 10.8.0.1|10.8.0.3|NORDVPN3_VPNV4|15.596ms|4.6ms|27%|down|highlossI tried to send emails, browse the web, here we go again. No internet.
I am no longer seeing DNS resolution issues in OpenVPN's logs because it is now configured with Nord's IP adresses instead of their FQDN.
When the connection crashed, the dashboard widget had the 3rd VPN gateway (from the group) saying Status = "Unknown" & RTT, RTTsd & Loss = "Pending"
I restarted all three OpenVPN services under Status > OpenVPN and the internet came back. However, things are not perfect yet (see screenshot).
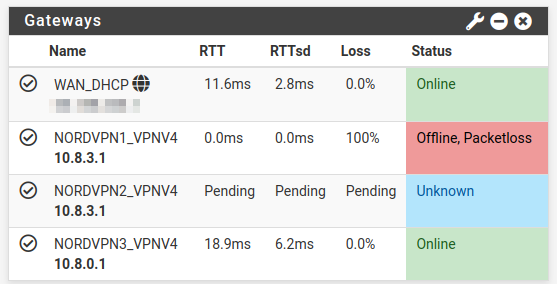
So whats going on with this ? Is it Nordvpn having issues ? I will send them this forum thread so they can see for themselves, but I suspect an issue with pfsense or openvpn more than anything else at this point.Not to complain per se, but before setting up this VPN "stuff" (!) pfsense was rock solid for many years...
-
@pftdm007 I can say from experience that Nord's servers (and I would venture to guess most VPN providers' servers) have relatively frequent transient latency and packet loss spikes. It's definitely not something you'd want to rely on for anything where ~100% uptime is mission critical.
-
I feel the same, but why pfsense doesnt use the leftover interface from the VPN group that still is connected to their servers?
In other words, why am I losing 100% connectivity to the internet if only one or 2 of the gateways are down? Shouldn't the 3rd one take over and cover everything until the other two that are down or experiencing timeouts,packet loss come back to normal?
-
@pftdm007 You're correct, it should. And in my experience it does, but in can take a minute or two as existing connections through the tunnel that went down are broken and then need to be re-established through one that's still up. So it's not something that would be transparent for sure, but you're saying it just doesn't happen at all no matter how long you wait?
I'm wondering whether you may want to try this option ( System > Advanced > Miscellaneous) to immediately kill all connections when a gateway goes down to (hopefully/maybe) reduce the lag time between a tunnel going down and any active connections using it being forced to reestablish over a tunnel that's still up. Of course it will have the byproduct of also killing any connections that are already going through a tunnel that's still up and making them reestablish as well. But maybe worth trying to see if it improves your observed behavior.
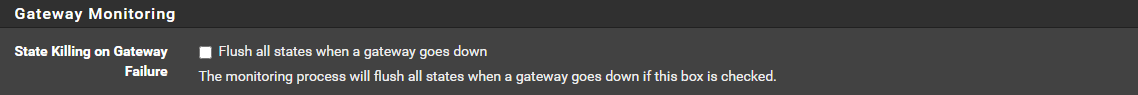
-
@thenarc said in pfsense constantly losing connectivity to NordVPN:
So it's not something that would be transparent for sure, but you're saying it just doesn't happen at all no matter how long you wait?
Yes, at least whne it happened yesterday I waited about 5 minutes or so but the status of the gateways stayed the same, and the connection was still down. After I force restarted the Openvpn service, the gateways went back up (albeit 2 of them still screwed up as per screenshot I posted above).
@thenarc said in pfsense constantly losing connectivity to NordVPN:
making them reestablish as well. But maybe worth trying to see if it improves your observed behavior.
I agree with you, that makes sense, it has pretty much the same effect as issuing a force restart on the underlying services (without of course restarting them for real)... But I wonder, can it cause data corruption or other issues with services that are actively communicating, etc? I have in mind, for example, if I am on a VOIP call, will my call be dropped or will I only see a small "hiccup" and nothing else? This is more of a general networking question than a VPN question.....
EDIT: I just realised that my VOIP ATA has been offline for many hours, if not for more than a day hence causing me to miss several phone calls... The ATA couldnt, for some esoteric reasons, establish a connection to the VOIP server even if the FW rules are all in order (and worked for many years before implementing this disaster of vpn). Rebooting pfsense solved it but I dont trust this for long. Will give myself a few days then I'm reverting everything and cancelling nordvpn.