How to trunk 2 ports to switch on SG-2100?
-
@johnpoz Thank you for the reply.
Mine is the same as in your example, all of my VLANs have 5 added as a tagged member for the uplink .
So the two VLANs (VLAN Tag 10 & 20) I created on the 2100 have members, 4,5t for the uplink
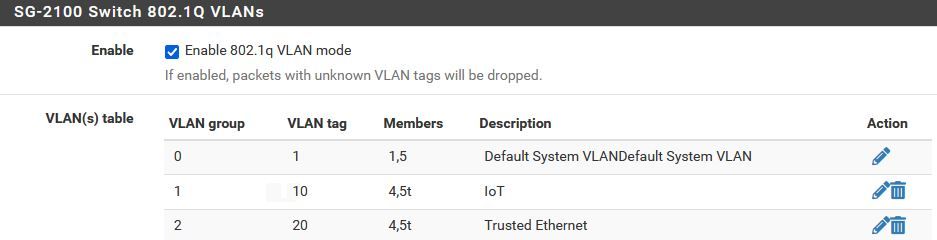
I have also tried setting both VLANs as tagged on Port 4 making it 4t,5t but this seems to break the link back to the 2100, devices connected to the switch are unable to obtain DHCP with those settings.
Anything else I should check?
-
If your going to run more than 1 vlan on the same port, ie your port 4 listed there.. Atleast 1 of them has to be tagged.. You can not run 2 untagged vlans on the same port and expect anything to work.. Then the port on your switch that is connected to this port has to be setup to match what you have tagged and what you have as native or untagged..
You can tag all vlans if you want, etc.. But you show untagged there for both vlan 10 and 20 - this is never going to work correctly.
You can only have 1 untagged vlan on a port at any given time.
-
@johnpoz
Oh right okI just tried setting VLAN 20 as a tagged member so the members are 4t,5t
VLAN 10 members = 4,5tI set ports 2-6 on the Aruba switch as tagged on VLAN 20 and Ports 7-8 as untagged on VLAN 10
I also tried the reverse, setting VLAN 10 as tagged. Members= 4t, 5t and VLAN 20 as untagged. Members =4,5t
I then set ports 2-6 on the Aruba switch as untagged on VLAN 20 and Ports 7-8 as tagged on VLAN 10So that the switch config matched the VLANs on the firewall. Neither configuration worked, devices were unable to get DHCP lease and only the native VLAN 1 untagged allocated 10.1.20.X
Have I understood correctly?
-
@worldhopp said in How to trunk 2 ports to switch on SG-2100?:
I set ports 2-6 on the Aruba switch as tagged on VLAN 20
Huh? Why would you do that? What do you have connected to them?
Do they have more than 1 vlan on them? Are you setting the device connected to that port to use tags for some reason?
The only port that needs to have vlans tagged is when there is more than 1 vlan on the port, say as uplink to another switch, or a AP or something. If you connecting a computer to said port then the vlan you want on that device would be untagged.
Here is old drawing I did for some thread long time back - showing where tagged an untagged would be used
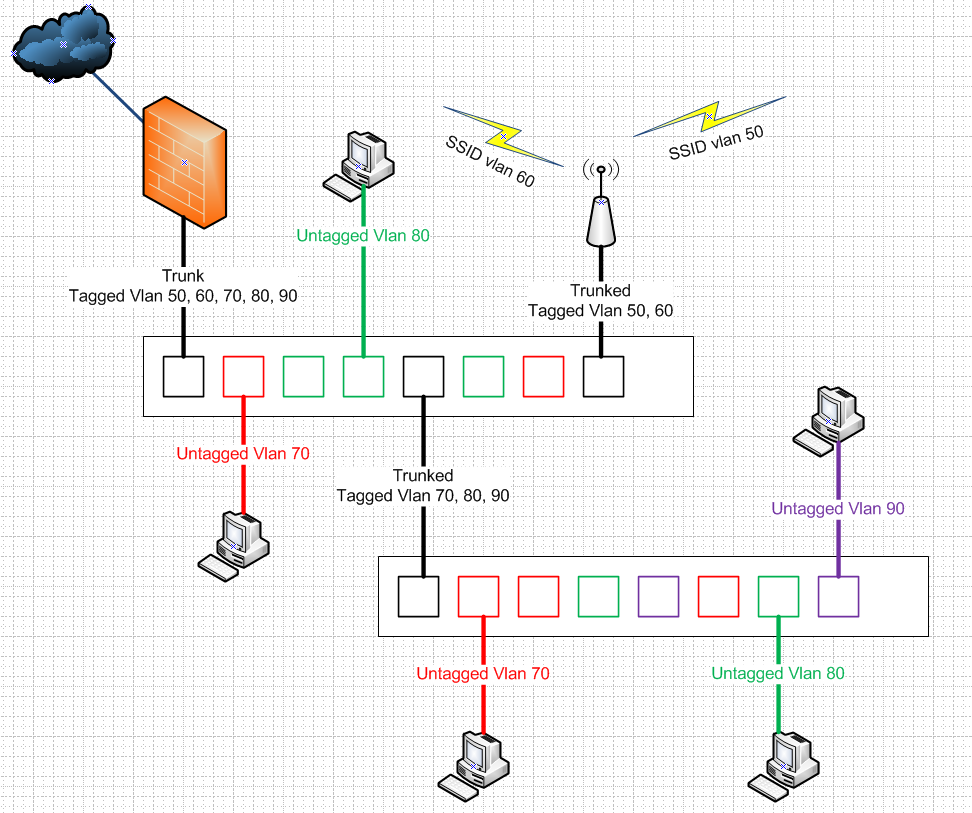
edit: Keep in mind that on your switch port your going to connect a device in a specific vlan, and its going to be untagged. You need to make sure the ports PVID is set to that vlan as well - so when the port sees ingress traffic that is no tagged it knows what vlan that traffic belongs too.
-
@johnpoz Thanks the image is making things more clear now.
I think the problem is the initial trunk from the 2100, I have set my switch config up as per that image but still the untagged ports for the IoT VLAN 10 aren't getting DHCP lease. PVIDs are set correctly.
The trunk port 1 has PVID of 1 - I take it that is correct?
On the 2100 only for VLAN 10 Port 4 is tagged and Port 5 for uplink so it looks like 4t,5t
VLAN 20 is untagged on port 4 so it looks like 4,5tI may just leave it as is but it means I'm not really taking advantage of the managed switch as this stage. As everything else has worked for my network upgrade apart from trunking these two VLANs to the switch.
Anything else you could suggest? No problem if not
thank you for the help
-
@worldhopp said in How to trunk 2 ports to switch on SG-2100?:
The trunk port 1 has PVID of 1 - I take it that is correct?
Is your native vlan 1? The pvid of the port on the switch should be what vlan you want untagged traffic to be in..
There is nothing saying you have to trunk anything... If you have ports available for uplink on your switch, and on your router there is no reason to carry vlans over the same physical port.
Your still isolating the vlans on your switch, so yeah your taking advantage of its features. The only reason you need/want to run multiple vlans on the same physical is ports being available or not, etc.
I personally run a few like that myself.. Since I have the ports to use.. I just trunk the vlans that don't do a lot of intervlan traffic and that use less bandwidth overall. My wireless vlans share an uplink..
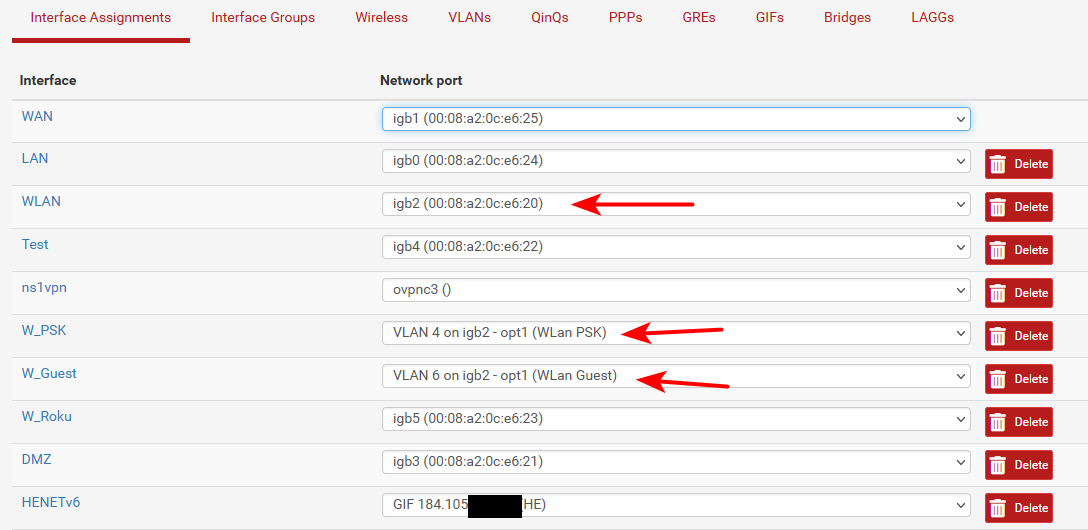
You can see that vlan 4 and 6 ride on the interface igb2, which also has an untagged vlan on it vlan 2, these 3 networks are mostly wireless devices on psk and guest. And they never talk to each other. But they do talk to my roku vlan, which is on its own interface.
Even you used no tagged vlans at all - you would still be leveraging capabilities of your switch by actually isolating the different L2 - be it they are tagged or not to external devices.
-
@johnpoz
Thank you for your help. Everything is working now as planned.
-
Glad you got it sorted.
-
@worldhopp What was the outcome here? I literally have the same issue. Would love know.
-
At the time of this forum post I was still inexperienced when it comes to networking. I kind of had the wrong idea about ROAS.
Steps taken to enable router on a stick.
SG2100
Interfaces > Switch > VLANs
Enable 802.1q VLAN mode
Add the required VLANs to Netgate VLANs table - set required VLANs as tagged on the LAN port that connects to the switch and tagged on the uplink virtual port 5Layer 2 Switch
Exact steps will vary depending on your model.... but generally...
Add VLANs to the VLAN table on your switch
Set the port that links back to Netgate as a trunk port or set all required VLANs as tagged on the port that links back to the Netgate
Then you can continue to setup your access aka untagged ports on the switch for end user devicesYour switch should now have a link back to the Netgate, enabling inter-VLAN routing.
Hope it helps
-
@worldhopp I believe you just solved my issue! I was just visualizing tagged and untagged backward. I'll let you know for sure how it turns out.
Thanks for the response on this old forum.
-
 P patient0 referenced this topic on
P patient0 referenced this topic on