pfBlockerNG blocking SMTP
-
@gertjan
It's Microsoft, Mailjet, Google...etc SMTP servers that are blocked.
These IPs are in multiple feeds so seems a bit too much to disable all these feeds -
You can white list here :
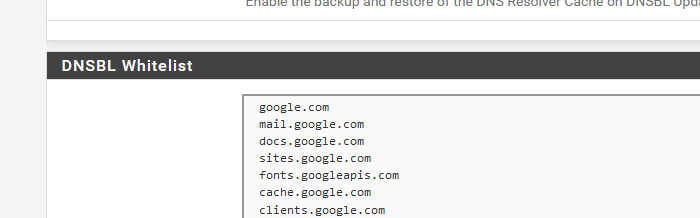
and whatever you list will be removed from all the lists.
You are hosting a mail server : be very careful with what you block, because if you block them, they can start to block you, as "Microsoft, Mailjet, Google...etc SMTP" can also send you ligit mails ....
I'm use myself a mail server (postfix), with a dozen or so domain names and as much IPv4 (and IPv6).
No pfSense in front of it, and certainly not something like pfBlockerNG, as it isn't ment to be used like that ( IMHO ). -
@gertjan
My mail server is in my lab so behind my pfsense.
That why i'm looking for a way to exluce my VIP from pfBlockerNG -
I understood.
Why would you need a VIP ? What about a dedicated interface network for your mail server, NAT port 25 from WAN to the 'mail' interface, mail server IP port 25 and done.
Exclude this mail server interface from any pfblockerng interference. This will also solve your issue (subject).Your WAN IP isn't an IP from some ISP, right ? As most, if not all, of them are known, and serious mail servers (the big ones) will not accept mail from servers "@home".
As soon as you are able to send a mail, send one to gmail.
Your mission : don't stop before you have 3 x ¨PASS". SPF+DKIM+DMARC isn't optional any more. I wonder if they will be strict with the PTR of your WAN IP ....edit :
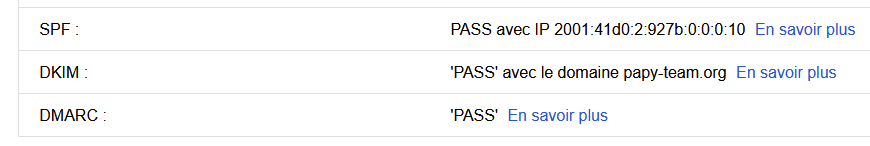
-
@gertjan
Great idea, didn't think about that !
I've asked my ISP to fix my VIP on available ports.
I already have PTR on these VIP.
Thanks mate
-
@gertjan
This solution brought me another problem ^^
Did you find a way to assign a dedicated interface ?
My ISP gave me multiple IPs but with only one WAN.
As you may know, it's impossible to assign another interface with the same gateway. -
@alek said in pfBlockerNG blocking SMTP:
My ISP gave me multiple IPs but with only one WAN.
Ok, I get it, I think : you've created VIP using Firewall > Virtual IPs and multiple IP aliases to your WAN interface.
These IP+port 25 could be NATted to the right local IP+port 25 == mail server, right ?
Assigning an interface to a gateway is needed here (I think again).
You will have to map the mailserver's outgoing traffic through to VIP IP. (I keep on thinking ;))Can say more, as I have never dealt with these multi IPs on WAN before.
I do use a lot of IPv4 addresses on the NIC of my mail server, :root@ns311465:~# ifconfig eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 188.xxx.201.123 netmask 255.255.255.0 broadcast 188.xxx.201.255 inet6 2001:41d0:2:xxx::10 prefixlen 128 scopeid 0x0<global> inet6 2001:41d0:2:xxxx::2 prefixlen 128 scopeid 0x0<global> inet6 fe80::225:yyy:fe71:bf86 prefixlen 64 scopeid 0x20<link> inet6 2001:41d0:2:xxxx::11 prefixlen 128 scopeid 0x0<global> inet6 2001:41d0:2:xxxx::15 prefixlen 128 scopeid 0x0<global> inet6 2001:41d0:2:xxxx::3 prefixlen 128 scopeid 0x0<global> inet6 2001:41d0:2:xxxx:: prefixlen 64 scopeid 0x0<global> inet6 2001:41d0:2:xxxx::20 prefixlen 128 scopeid 0x0<global> inet6 2001:41d0:2:xxxx::1 prefixlen 128 scopeid 0x0<global> ether 00:25:00:71:bf:86 txqueuelen 1000 (Ethernet) RX packets 152768770 bytes 37714762815 (35.1 GiB) RX errors 2 dropped 123638 overruns 0 frame 2 TX packets 201134377 bytes 186610834588 (173.7 GiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 device interrupt 16 memory 0xfbce0000-fbd00000 eth0:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 46.xxx.79.38 netmask 255.255.255.255 broadcast 46.xxx.79.38 ether 00:25:00:71:bf:86 txqueuelen 1000 (Ethernet) device interrupt 16 memory 0xfbce0000-fbd00000 eth0:1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 87.xxx.136.44 netmask 255.255.255.255 broadcast 87.xxx.136.44 ether 00:25:00:71:bf:86 txqueuelen 1000 (Ethernet) device interrupt 16 memory 0xfbce0000-fbd00000 eth0:2: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 5.xxx.43.182 netmask 255.255.255.255 broadcast 5.xxx.43.182 ether 00:25:00:71:bf:86 txqueuelen 1000 (Ethernet) device interrupt 16 memory 0xfbce0000-fbd00000 eth0:3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 87.xxx.174.106 netmask 255.255.255.255 broadcast 87.xxx.174.106 ether 00:25:00:71:bf:86 txqueuelen 1000 (Ethernet) device interrupt 16 memory 0xfbce0000-fbd00000 eth0:4: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 188.165.53.87 netmask 255.255.255.255 broadcast 188.165.53.87 ether 00:25:00:71:bf:86 txqueuelen 1000 (Ethernet) device interrupt 16 memory 0xfbce0000-fbd00000 eth0:5: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 217.xxxx.46.28 netmask 255.255.255.255 broadcast 217.xxx.46.28 ether 00:25:00:71:bf:86 txqueuelen 1000 (Ethernet) device interrupt 16 memory 0xfbce0000-fbd00000My firewall (iptables) is close to empty - no NAT rules neither.
Works great for the last 15 years or so.
This is a dedicated bare bone server in a data centre. -
@gertjan
Yes I did it this way.
I got a port forward + outbound rule between one VIP to my local IP.
I didn't understand, you mean adding a new interface ? Because this is exactly what I'm trying to do but can't coz same gw. -
@alek said in pfBlockerNG blocking SMTP:
I didn't understand, you mean adding a new interface ? Because this is exactly what I'm trying to do but can't coz same gw
I thought it was like adding interfaces, but it isn't.
I've edited my post above to show you that I also add several IPv4 (and IPv6) to the same physical interface. That is a standard Debian based web mail server. -
@alek
My bad, didn't get the whole text.
I guess the best way would be to have a dedicated pfsense box without pfblocker, assigned to one of my VIP and serving my mails servers. No ? -
@alek said in pfBlockerNG blocking SMTP:
No ?
That's the easy / easier way.
Have a look at this list : Youtube Netgate everything you always wanted to know, and more.
There is a Muti WAN video. There is a video about VIP, Carps, etc.The videos are old, but still very valid and very informative. It's a guy from Netgate talking about Netgate/pfSense.