Suricata Force Disabled Rules List
-
Over time I've disabled these rules. Does anyone see rules I perhaps should not have disabled and instead been more granular in my approach?
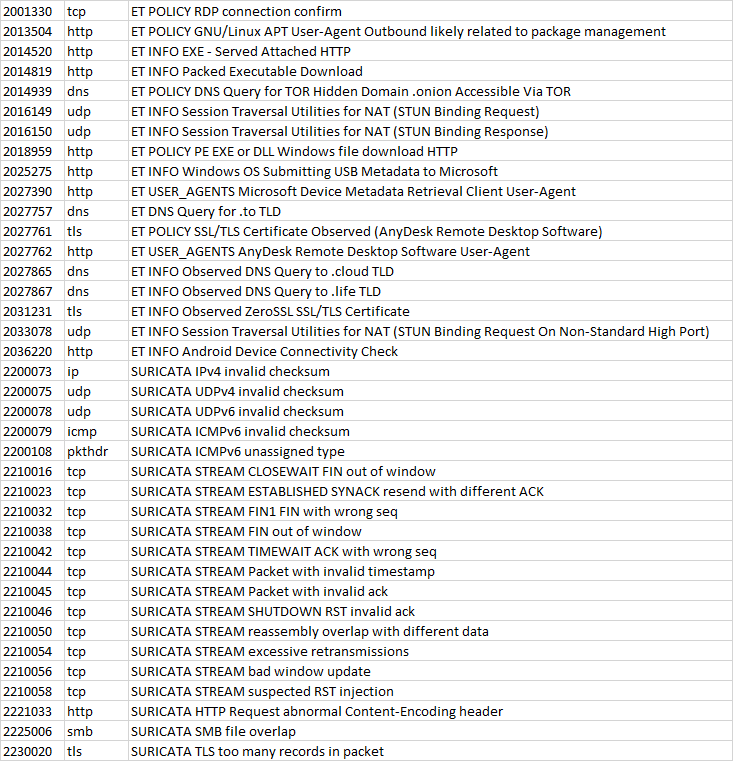 2001330 tcp ET POLICY RDP connection confirm
2001330 tcp ET POLICY RDP connection confirm
2013504 http ET POLICY GNU/Linux APT User-Agent Outbound likely related to package management
2014520 http ET INFO EXE - Served Attached HTTP
2014819 http ET INFO Packed Executable Download
2014939 dns ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR
2016149 udp ET INFO Session Traversal Utilities for NAT (STUN Binding Request)
2016150 udp ET INFO Session Traversal Utilities for NAT (STUN Binding Response)
2018959 http ET POLICY PE EXE or DLL Windows file download HTTP
2025275 http ET INFO Windows OS Submitting USB Metadata to Microsoft
2027390 http ET USER_AGENTS Microsoft Device Metadata Retrieval Client User-Agent
2027757 dns ET DNS Query for .to TLD
2027761 tls ET POLICY SSL/TLS Certificate Observed (AnyDesk Remote Desktop Software)
2027762 http ET USER_AGENTS AnyDesk Remote Desktop Software User-Agent
2027865 dns ET INFO Observed DNS Query to .cloud TLD
2027867 dns ET INFO Observed DNS Query to .life TLD
2031231 tls ET INFO Observed ZeroSSL SSL/TLS Certificate
2033078 udp ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard High Port)
2036220 http ET INFO Android Device Connectivity Check
2200073 ip SURICATA IPv4 invalid checksum
2200075 udp SURICATA UDPv4 invalid checksum
2200078 udp SURICATA UDPv6 invalid checksum
2200079 icmp SURICATA ICMPv6 invalid checksum
2200108 pkthdr SURICATA ICMPv6 unassigned type
2210016 tcp SURICATA STREAM CLOSEWAIT FIN out of window
2210023 tcp SURICATA STREAM ESTABLISHED SYNACK resend with different ACK
2210032 tcp SURICATA STREAM FIN1 FIN with wrong seq
2210038 tcp SURICATA STREAM FIN out of window
2210042 tcp SURICATA STREAM TIMEWAIT ACK with wrong seq
2210044 tcp SURICATA STREAM Packet with invalid timestamp
2210045 tcp SURICATA STREAM Packet with invalid ack
2210046 tcp SURICATA STREAM SHUTDOWN RST invalid ack
2210050 tcp SURICATA STREAM reassembly overlap with different data
2210054 tcp SURICATA STREAM excessive retransmissions
2210056 tcp SURICATA STREAM bad window update
2210058 tcp SURICATA STREAM suspected RST injection
2221033 http SURICATA HTTP Request abnormal Content-Encoding header
2225006 smb SURICATA SMB file overlap
2230020 tls SURICATA TLS too many records in packet -
Per other posts here, the Info and Policy categories are mostly informational and it's been recommended to not block those. (and if you don't, no need to load/use them hence no need to disable)
We found long ago we had to disable all the "stream" entries because of a lot of false positives.
Is "Disable hardware checksum offload" checked in System->Advanced->Networking? Having offloading on caused a lot of false positives also.
-
Thanks. I selected to Disable hardware checksum offload. Are these the rulesets (categories) to deselect? Is there a set for STREAM?
emerging-icmp_info.rules
emerging-info.rules
emerging-policy.rules -
@pfgate Not sure offhand what emerging-icmp_info.rules is. In most cases for our clients ICMP is not enabled through the router anyway so no need to look for that. I was referring to the other two.
The other category is stream-events.rules.
-
@pfgate Do you have any notes about the 2225006 smb SURICATA SMB file overlap rule? I just came across that event being triggered, and no idea what it means.
-
@steveits so curious about your IPS/IDS setup at your workplace. You sending alerts to a SIEM?
-
@michmoor Depends on the setup but often not.