Upgraded pfSense from 2.4.5 to 2.5.2 or 2.6.0 and OpenVPN no longer works
-
@jhdeval
The pfSense log only shows entries from a client running on pfSense itself, but not from the server and external clients connecting to it.Since the client log let you assume that he cannot reach the server, ensure that the inbound packets are allowed on pfSense and that the OpenVPN server is listening to the correct interface and IP address.
Something the listing addresses are messed up on upgrades. -
@jhdeval I get the same error after upgrading to 2.6 on multiple pfsense boxes. I suspect it is related to the issue I posted earlier today (https://forum.netgate.com/topic/171878/client-export-fails-after-upgrade-to-2-5-2-2-6.) I'll bet if you try to use the client export tool you will get the same "private key" error.
-
@kitdavis I do get the same error. I tried to re-export the client file and it still did not work with the original OpenVPN server config.
-
I'm using openVPN - SSL/TLS + Auth
I have an "old client export" from a 2.4.?? (left side) , and a new "client export from today on pfSense+ 22.01 (Legacy client ticked) to match my old 4.x.x
Here is what a "diff" (linux meld) shows
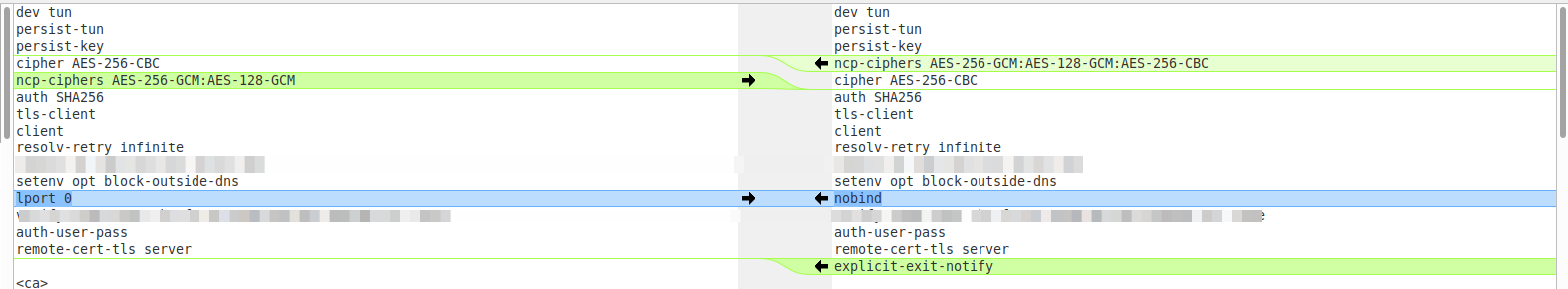
Old has lport 0
New has nobind and explicit-exit-notify
Not a bit has changed in the whole cert or tls key section.
Note: This is on 22.01 "pfSense plus"
/Bingo
-
I appreciate the information and I am also using ssl/tls + auth settings but using either the new or old config I am unable to connect to any OpenVPN server that was created in 2.4.x. As I said in my original post I can see the connection going through the firewall and I can see it "attempt" to connect to the OpenVPN server but it seems like it half connects then just drops the connection and tried again. There is no meaningful data in the logs to indicate what the failure is.
-
@jhdeval Try modifying the server to just use ssl/tls and I think it will work - at least for me the problem is only with the ssl/tls + authentication and is related to the private key error. This isn't a solution, since you have to re-export the client config but I think it narrows the problem.
-
Could this be a match ?
https://redmine.pfsense.org/issues/12475 -
@jhdeval said in Upgraded pfSense from 2.4.5 to 2.5.2 or 2.6.0 and OpenVPN no longer works:
There is no meaningful data in the logs to indicate what the failure is.
May we see it anyway?
If the packets are reaching the server, there must be log entries, telling you what's going on on the server.
-
@viragomann I took a working 2.4.4 installation (i.e. I could connect to it via OPENVPN) and upgraded it to 2.5.2 - after the upgrade the openvpn connection cannot be established and the error in the log is:
May 3 05:03:21 openvpn 24521 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]167.94.138.105:64805
May 3 00:16:50 openvpn 24521 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]146.88.240.4:46211running openvpn from the client terminal I see:
2022-05-03 10:59:43 OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
2022-05-03 10:59:43 TLS_ERROR: BIO read tls_read_plaintext error
2022-05-03 10:59:43 TLS Error: TLS object -> incoming plaintext read error
2022-05-03 10:59:43 TLS Error: TLS handshake failed
2022-05-03 10:59:43 SIGUSR1[soft,tls-error] received, process restarting -
@kitdavis
Seems the server log lines have nothing to do with the error on the client.Obviously there is something wrong with the server cert from the point of the client. Normally you can see details one line above of that one you've posted.
But your error differs totally from the above.
-
@viragomann I am working on the logs. Since this is a production server I had to restore from backup to bring users live again. I will need to clone this server and use it in a closed environment to get the logs.
-
@viragomann I agree there is something wrong with the certificate. As per my other thread, once the upgrade occurs - if I try to use the client export took, I get the private key missing error which I think it referenced in: https://redmine.pfsense.org/issues/12475
-
S Stewart referenced this topic on
-
@kitdavis @jhdeval @viragomann
I know this post is a few months old but I ran into the same thing with the same update path and the same errors. I can't find that you were able to resolve your problem but I wanted to post my experience here as it was one of the first threads that popped up while searching. I found in my case that the issue was the new version of OpenVPN restricts the age limit of the certificates to about 13 months whereas before the default was 10 years. If the certificates extend beyond the time threshold then the client considers it to be invalid. I had to regenerate my certificates with shorter times and reissue them to the workstations for it to work.
-
@stewart
https://forum.netgate.com/topic/172870/crl-has-expired/24
https://blog.nuvotex.de/pfsense-crl-has-expired/ -
@khodorb said in Upgraded pfSense from 2.4.5 to 2.5.2 or 2.6.0 and OpenVPN no longer works:
https://blog.nuvotex.de/pfsense-crl-has-expired/
Thanks. I tried that patch and it was unsuccessful in fixing the issue. This was my post.