Nested firewall: no webGUI access on WAN
-
I can see the (first step of a) connection made successfully if I try to "wget http://192.168.1.<pfsense WAN>:80" but it never proceeds to actually access what should be accessible there and open the interface or download the page etc. Something seems to interfere and block the connection on WAN
-
@dangersheep but you can open from one of your lan IPs? behind pfsense.
Now sure why your hiding private addresses?
Please post your firewall rules. on your wan. Do you have any rules on floating? So your saying the firewall logs the S and its allowed.. And you see the nginx log showing the get, but just no answer ?
-
@johnpoz I can open from any device connected to either LAN interface "behind pfsense", yes.
What do you mean 'hiding private addresses'?
I'm not sure where best to get the firewall rules, so I've copied everything below "#User-defined rules follow":
anchor "userrules/*" pass in quick on $OpenVPN inet from any to any ridentifier 1650056314 keep state label "USER_RULE: OpenVPN myVPN wizard" pass in log quick on $WAN reply-to ( igb0 192.168.1.1 ) inet from any to 192.168.1.131 ridentifier 1651958809 keep state label "USER_RULE: Allow all on WAN" pass in quick on $WAN reply-to ( igb0 192.168.1.1 ) inet proto icmp from any to any icmp-type echoreq ridentifier 1650530485 keep state label "USER_RULE" pass in quick on $LAN inet from 10.0.0.0/24 to any ridentifier 0100000101 keep state label "USER_RULE: Default allow LAN to any rule" # source address is empty. label "USER_RULE: Default allow LAN IPv6 to any rule" pass in quick on $LAN2 inet from any to any ridentifier 1652196321 keep state label "USER_RULE: LAN2 allow any" # VPN Rules anchor "tftp-proxy/*"Hopefully that dump also answers your questions about 'rules on floating' - if not please could you tell me where to find that.
In answer to your final question, yes I see the firewall log shows the TCP:S connection is allowed and I see the nginx log showing the GET, but firefox fails to load the page and the connection eventually 'times out'. A wget command just keeps on retrying ad nauseam...
-
@dangersheep screen shot of the rules is easy for everyone to read.
As to hiding I mean the point of this.
allowed source 192.168.1.<my laptop>:51488 destination 192.168.1.<pfsense WAN>:80 TCP:S
why would it not be say 1.40 and 1.1 or 1.254, etc.. whatever your actual wan IP is..
On your firewall tab "floating" do you have any rules set - if so what are they?
If pfsense wan is 192.168.1.254 for example, and you have some box that trying to open the gui is also on this 192.168.1 network? say 192.168.1.40? Where exactly is this device your trying to open the gui from on the wan?
-
@johnpoz I see! Yes, no need to 'hide' the IP I agree.
I'll check the 'floating' tab later and report back.
To answer your second question, the device at 192.168.1.40, which is trying to open the gui on the WAN, is connected by wifi to my ISP's router which, in turn, is connected directly to my pfsense WAN port.
I have problems with any sort of connection into the WAN interface - I can't ssh to the (activated) SSH server on the pfsense box through WAN (I can from LAN); even OpenVPN has problems establishing a connection through that interface to pfsense (I managed to connect openvpn occasionally but only ever a single time after I reboot my macbook air, strangely and not successively). I'll try from another device, just in case the problem is on the laptop end
-
@dangersheep so if you plug say a laptop into your isp router and get 192.168.1.42 for example... Does that work?
-
@johnpoz thanks for your patience. I took a laptop and plug ethernet directly into pfsense LAN, and I can access the configurator. But if I replug into my ISP router - which connects to the pfsense WAN - I get no access to the configurator. So it wasn't just a problem of the other laptop on wifi.
A few more things:
- Port scanning my pfsense box from a device connected to my ISP router (i.e. WAN interface) shows that ports 22, 53, and 80 are open, in the first 1000 ports or so. So everything's open that I'd expect to be. I can ping the pfsense box. I was a bit surprised to see the DNS port open so I may be mistakenly running a DNS there... but I don't think it should break connectivity.
- You asked about floating firewall rules; none are defined.
-
And here's a screenshot of the WAN rules, for completeness:
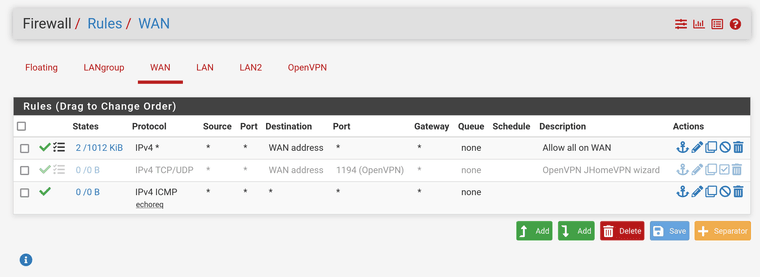
-
Little bit confused by the DNS listener on WAN - DNS resolving is disabled in pfsense but DNS forwarding is enabled. But the DNS forwarding is only active on the LAN interfaces, not on WAN. I wonder why port 53 is open on WAN... but I don't think this is connected to my lack of WAN gui connectivity.
-
Out of interest, as soon as I try to load the gui over the WAN, I see the following state appear:
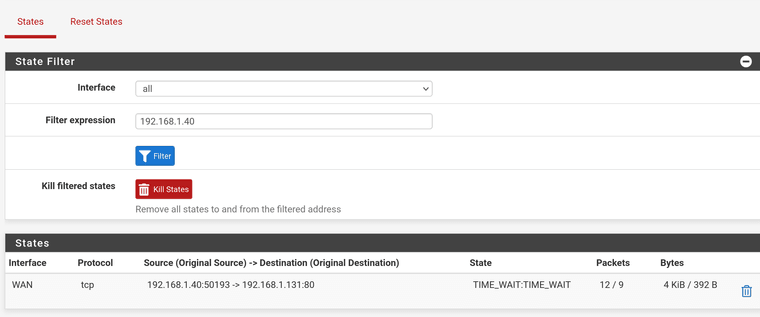
The connection then times out, as before.
-
My pfsense rules are, in case anything stands out:
pfTop: Up Rule 1-91/91, View: rules RULE ACTION DIR LOG Q IF PR K PKTS BYTES STATES MAX INFO 0 Pass Any 0 0 0 all 1 Pass Any 0 0 0 all 2 Block In Log Q 0 0 0 drop inet from 169.254.0.0/16 to any 3 Block In Log Q 6 360 0 drop inet from any to 169.254.0.0/16 4 Block In Log 21153 1560686 0 drop inet all 5 Block Out Log 0 0 0 drop inet all 6 Block In Log 1 52 0 drop inet6 all 7 Block Out Log 0 0 0 drop inet6 all 8 Pass Any Q ipv6-icmp K 0 0 0 inet6 all 9 Pass Any Q ipv6-icmp K 0 0 0 inet6 all 10 Pass Any Q ipv6-icmp K 3 216 0 inet6 all 11 Pass Any Q ipv6-icmp K 2 136 0 inet6 all 12 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 13 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 14 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 15 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 16 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 17 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to ff02::/16 18 Pass Out Q ipv6-icmp K 2 112 0 inet6 from fe80::/10 to ff02::/16 19 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to ff02::/16 20 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to ff02::/16 21 Pass Out Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to ff02::/16 22 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 23 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 24 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 25 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 26 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to fe80::/10 27 Pass In Q ipv6-icmp K 0 0 0 inet6 from ff02::/16 to fe80::/10 28 Pass In Q ipv6-icmp K 0 0 0 inet6 from ff02::/16 to fe80::/10 29 Pass In Q ipv6-icmp K 0 0 0 inet6 from ff02::/16 to fe80::/10 30 Pass In Q ipv6-icmp K 0 0 0 inet6 from ff02::/16 to fe80::/10 31 Pass In Q ipv6-icmp K 0 0 0 inet6 from ff02::/16 to fe80::/10 32 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to ff02::/16 33 Pass In Q ipv6-icmp K 2 112 0 inet6 from fe80::/10 to ff02::/16 34 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to ff02::/16 35 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to ff02::/16 36 Pass In Q ipv6-icmp K 0 0 0 inet6 from fe80::/10 to ff02::/16 37 Pass In Q ipv6-icmp K 0 0 0 inet6 from ::/128 to ff02::/16 38 Pass In Q ipv6-icmp K 0 0 0 inet6 from ::/128 to ff02::/16 39 Pass In Q ipv6-icmp K 0 0 0 inet6 from ::/128 to ff02::/16 40 Pass In Q ipv6-icmp K 0 0 0 inet6 from ::/128 to ff02::/16 41 Pass In Q ipv6-icmp K 0 0 0 inet6 from ::/128 to ff02::/16 42 Block Any Log Q tcp 0 0 0 drop inet from any port = 0 to any 43 Block Any Log Q udp 0 0 0 drop inet from any port = 0 to any 44 Block Any Log Q tcp 2 120 0 drop inet from any to any port = 0 45 Block Any Log Q udp 0 0 0 drop inet from any to any port = 0 46 Block Any Log Q tcp 0 0 0 drop inet6 from any port = 0 to any 47 Block Any Log Q udp 0 0 0 drop inet6 from any port = 0 to any 48 Block Any Log Q tcp 0 0 0 drop inet6 from any to any port = 0 49 Block Any Log Q udp 0 0 0 drop inet6 from any to any port = 0 50 Block Any Log Q 0 0 0 drop from to any 51 Block Any Log Q 0 0 0 drop from any to 52 Block In Log Q tcp 0 0 0 drop from to (self) port = ssh 53 Block In Log Q tcp 0 0 0 drop from to (self) port = http 54 Block In Log Q 0 0 0 drop from to any 55 Pass In Q igb0 udp K 1 576 0 from any port = bootps to any port = bootpc 56 Pass Out Q igb0 udp K 0 0 0 from any port = bootpc to any port = bootps 57 Pass In Q igb0 udp K 0 0 0 inet6 from fe80::/10 port = dhcpv6-client to fe80::/10 por 58 Pass In Q igb0 udp K 0 0 0 from any port = dhcpv6-server to any port = dhcpv6-client 59 Pass Out Q igb0 udp K 0 0 0 from any port = dhcpv6-client to any port = dhcpv6-server 60 Block In Log !igb0 75 16184 0 drop inet from 192.168.1.0/24 to any 61 Block In Log 0 0 0 drop inet from 192.168.1.131/32 to any 62 Block In Log igb0 0 0 0 drop inet6 from fe80::2e0:67ff:fe2c:5cbe/128 to any 63 Block In Log !igb1 0 0 0 drop inet from 10.0.0.0/24 to any 64 Block In Log 0 0 0 drop inet from 10.0.0.1/32 to any 65 Block In Log igb1 0 0 0 drop inet6 from fe80::2e0:67ff:fe2c:5cbf/128 to any 66 Pass In Q igb1 udp K 12 3816 0 inet from any port = bootpc to 255.255.255.255/32 port = b 67 Pass In Q igb1 udp K 0 0 0 inet from any port = bootpc to 10.0.0.1/32 port = bootps 68 Pass Out Q igb1 udp K 0 0 0 inet from 10.0.0.1/32 port = bootps to any port = bootpc 69 Block In Log !igb2 0 0 0 drop inet from 10.0.1.0/24 to any 70 Block In Log 0 0 0 drop inet from 10.0.1.1/32 to any 71 Block In Log igb2 0 0 0 drop inet6 from fe80::2e0:67ff:fe2c:5cc0/128 to any 72 Pass In Q igb2 udp K 0 0 0 inet from any port = bootpc to 255.255.255.255/32 port = b 73 Pass In Q igb2 udp K 53 17864 0 inet from any port = bootpc to 10.0.1.1/32 port = bootps 74 Pass Out Q igb2 udp K 0 0 0 inet from 10.0.1.1/32 port = bootps to any port = bootpc 75 Pass In lo0 K 0 0 0 inet all flags S/SA 76 Pass Out lo0 K 0 0 0 inet all flags S/SA 77 Pass In lo0 K 0 0 0 inet6 all flags S/SA 78 Pass Out lo0 K 0 0 0 inet6 all flags S/SA 79 Pass Out K 14385 1005684 0 inet all flags S/SA allow-opts 80 Pass Out K 10 860 0 inet6 all flags S/SA allow-opts 81 Pass Out K 167474 80826132 0 route-to ... inet from 192.168.1.131/32 to ! 192.168.1.0/2 82 Pass In Q igb1 tcp K 0 0 0 from any to (igb1) port = http flags S/SA 83 Pass In Q igb1 tcp K 0 0 0 from any to (igb1) port = ssh flags S/SA 84 Pass Any 0 0 0 all 85 Pass In Q openvp K 0 0 0 inet all flags S/SA 86 Pass In Log Q igb0 K 4374 1067667 0 reply-to ... inet from any to 192.168.1.131/32 flags S/SA 87 Pass In Q igb0 icmp K 0 0 0 reply-to ... inet all 88 Pass In Q igb1 K 26523 12027979 0 inet from 10.0.0.0/24 to any flags S/SA 89 Pass In Q igb2 K 175964 73522641 0 inet all flags S/SA 90 Pass Any 0 0 0 all -
Any more thoughts as to what I might try? I hope the firewall rules dump gives some insight into why my wan interface is not performing as expected?
Many thanks in advance... I'm totally stuck!
-
So, after a few days I (in desperation!) reached out to the great people at Protectli who sold me the router hardware in the first place. Their support was awesome. Thanks protectli!
Someone there set up a working example and then exported the xml description (diagnostics > backup & restore) so that I had something to compare against, line-by-line. After an hour or so combing through mine and theirs, I discovered I had wrongly configured a static route early in my experimenting with pfsense, which was disrupting access on the WAN interface to the gui. Once removed (and after a reboot) access via WAN was restored. "Problem" resolved.
Many thanks @Bob-Dig and @johnpoz for helping me through the initial stages patiently; much appreciated.