LAN vs VLAN w/ unifi switch and UDM PRO
-
@mr-singh Are you doing igmp snooping in them or any other sort of filtering? I assume you have some wireless in there - prob more related to those..
I don't really have any unifi switches in my setup - I have one of the flex mini - got it to play with.. Its little, give you that. But overall feature set limited.. Its sitting on a shelf right now..
I could see where they could be useful, and guess if I was unifi across the board for switches already - and I needed a little one, would use them.
-
@johnpoz igmp snooping is enabled in UI controller, is there anything specific I need to do as well. On the IoT streaming VLAN there are only 2 devices to test. Laptop and nvidia shield.
I also have the Switch Flex, but only AP is on it.
-
@mr-singh try turning off igmp snooping.. This might prevent discovery because it can limit who sees multicast unless the client joins the group, etc.
So try turning it off, also their other multicast features - and see if that helps.
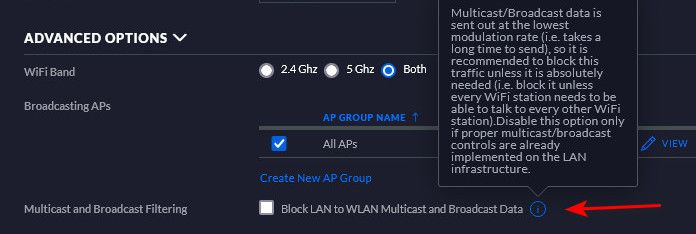
Also anything that might be doing L2 isolation could cause you grief

You might want to check over on their forums for info - like I said pfsense has nothing to do with such communication
-
@johnpoz The issue I don't understand is:
I created a VLAN 40 on both pfsense and unifi. DHCP setting works and I get the IP. No casting because when I search using chrome on the Win10 Laptop shield doesn't pop up. They both are on the same VLAN.In Unifi switch, I specifically change the port profile to that of the specific VLAN network.
When the same devices are on "ALL" port profile, casting works both with wired and wireless clients with shield. So how is unifi blocking casting on VLAN ports
-
This post is deleted! -
@mr-singh said in LAN vs VLAN w/ unifi switch and UDM PRO:
They both are on the same VLAN.
Again that has zero to do with pfsense - zero! Pfsense has nothing to do to block traffic happening between devices on the same switch or via an AP..
There is no way you could block multicast on an L2 network with pfsense even if you wanted to..
Unless pfsense was bridge between segments of an L2.. Say something like this
L2 --- interfaceA (pfsense bridge) ineterfaceB --- L2
-
@johnpoz Can DNS be an issue? My LAN interface has private 10.160.15.1/24 and IoT 11.160.30.1/24.
By any ways can these conflicting with anything?
I am also running pfblocker -
@mr-singh if your trying to actually resolve something that doesn't resolve sure dns could be a problem.
Are you trying to access something via fully qualified domain name? host.domain.tld - if so does it resolve?
pfblocker has ZERO to do with some multicast discovery that happens on some L2 network.
I am not a fan of discovery stuff, but discovery protocols normally have nothing to do with dns, since that is not really discovery ;) They might send a mdns query, but that is on the L2 and all devices on the same L2 would see that traffic and pfsense has nothing to do with that.
-
@johnpoz I have a L3 unifi switch, but I am not using any of those features.
I was able to get a avahi reflector working on a rpi 4.
My desktop on the lan interface is able to see the entry via avahi browse but nothing pops in chrome
weird thing is my phone also on the LAN interface wifi(unifi ap) can see the chromecast device. But only my phone. Not any other wired or wirless devices like desktop and laptops
-
@mr-singh said in LAN vs VLAN w/ unifi switch and UDM PRO:
My desktop on the lan interface is able to see the entry via avahi browse but nothing pops in chrome
Well what ports are being used to actually cast? Those would have to be allowed, if a multicast stream wouldn't work - because avahi just allows for the discovery via mdns.
-
@johnpoz Since both my phone and desktop are on LAN and the phone can see the chromecast and cast to it and the desktop cannot.
doesn't that mean something is wrong somewhere?