CREATE RULE NAT OVER OPEN VPN SITE TO SITE TUNNEL
-
@charneval said in CREATE RULE NAT OVER OPEN VPN SITE TO SITE TUNNEL:
Connect to the network of the place B there is a NAS with this IP "172.16.9.240" and it respose on the port 8080. If from network A i go to the NAS all work regulary, but i would like to create a NAT rules from any on the place network A to the NAS connect to the place network B by the tunnel VPN.
Can you explain a bit more clearly what you intend and what's not working at this time?
-
I DON'T THINK IT IS POSSIBLE!
-
Hi.
The public ip address of the site A is : 92.245.173.212 and I create a nat rule from any to the port 8080 of the nas 172.16.9.240 connected in the site B. This nat doesen’t work.
I think the problem in the outgoing nat configuration.
I connected the site B by an openvpn site to site and the pfsense in the site A can’t correct forward the packet.
How can I configure the outbound nat by the openvpn tunnel.Thanks
Andrea
-
@charneval said in CREATE RULE NAT OVER OPEN VPN SITE TO SITE TUNNEL:
The public ip address of the site A is : 92.245.173.212 and I create a nat rule from any to the port 8080 of the nas 172.16.9.240 connected in the site B.
So at site A you have a port forwarding rule for destination WAN address 8080 to 172.16.9.240 8080, correct?
If you don't need any information about the origin source address, you can simply masquerade the packets at site A.
Are both VPN endpoints pfSense and are both the default gateway in their respective local network?
-
@viragomann said in CREATE RULE NAT OVER OPEN VPN SITE TO SITE TUNNEL:
If you don't need any information about the origin source address, you can simply masquerade the packets at site A
Hi.
For masquerade the packets at site " A " I must do an Hybrid Outbound NAT rule generation right ?
Do I have to mask all the packets of the wan arriving on the 8080 port towards the network configured in the openvpn?
Or there is another method ?Thanks
-
@charneval
Yes, switch the Outbound NAT at A into hybrid mode.
Then add a rule with at least these parameters:interface: the OpenVPN interface you have asigned to the VPN connection, if any, otherwise can also add it to OpenVPN (interface group)
source: any
destination: 172.16.9.240
translation: interface addressOr there is another method ?
Other than masquerading? Yes, masquerading is a workaround, which is easy to configure. You can also forward it without NAT, but you would have to obey some precepts.
-
@viragomann
Hi.
Can you check if this configuration is correct ?
I can't find the targethttp://euroservizi.hopto.org:8080
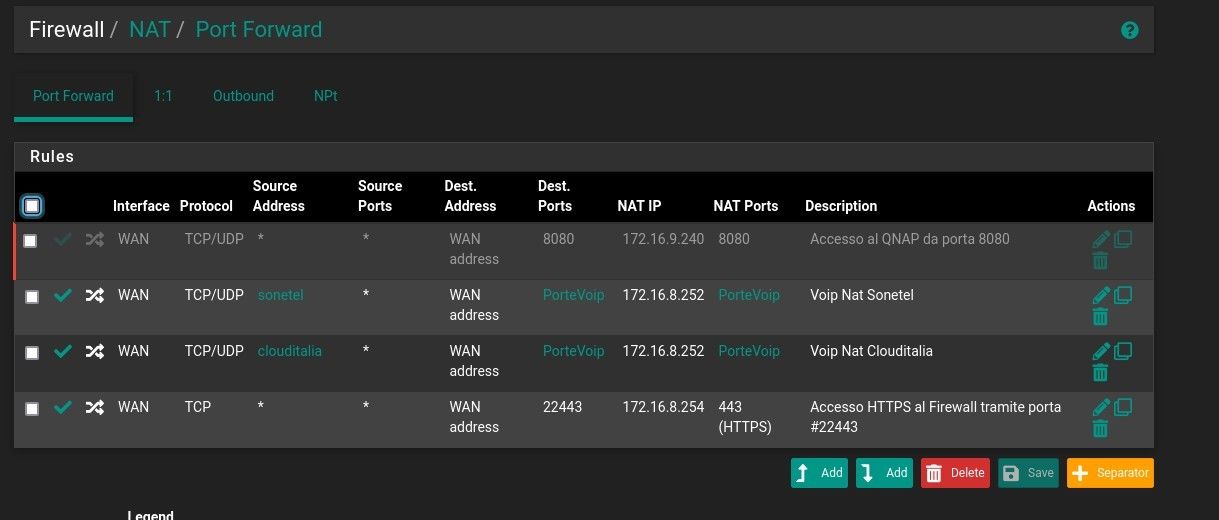
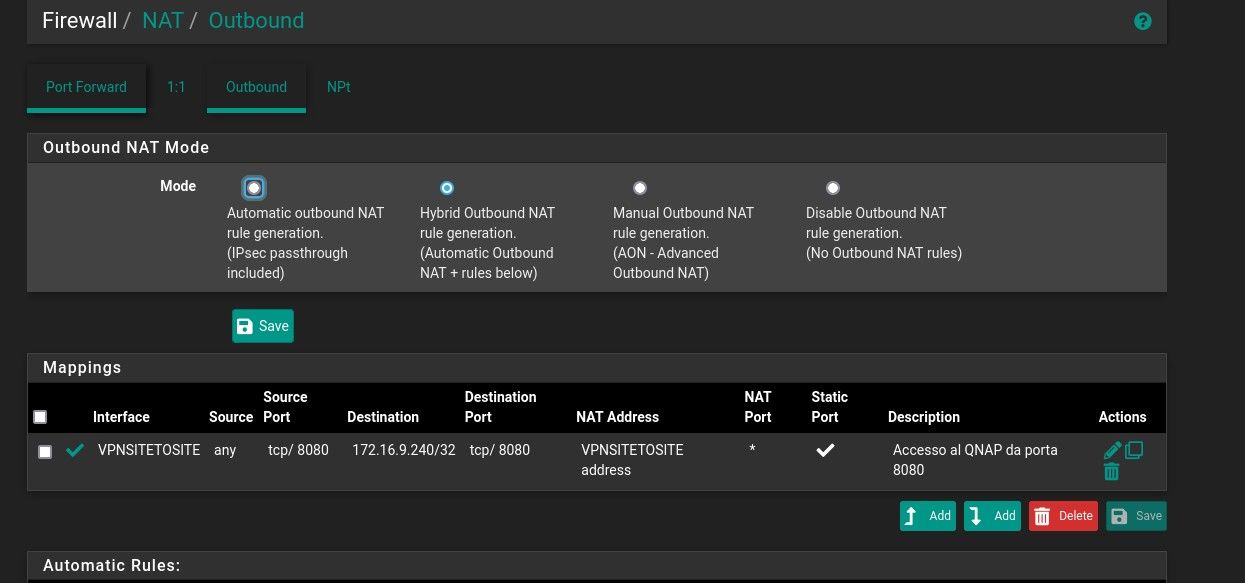
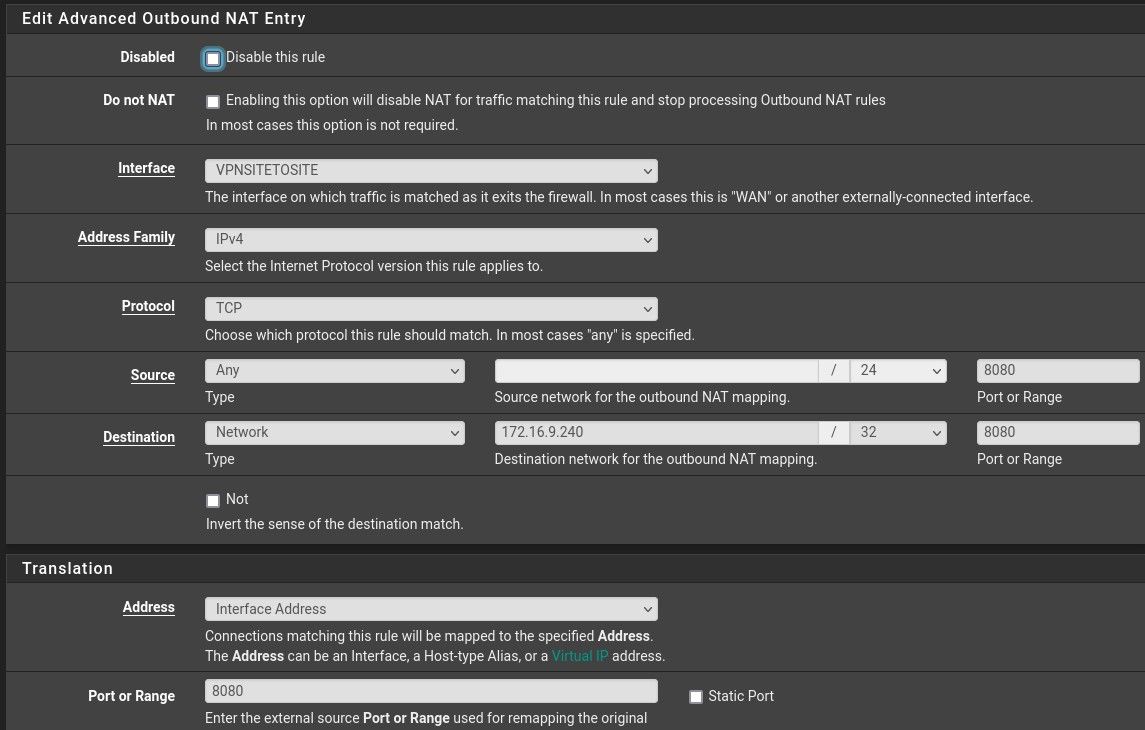
I disable the nat rule in the wan but if enable it the problem is the same.
When I connect by the oepnvpn client at the server " A " I have't any problem and I can reach the 172.16.9.240:8080
Thanks
Andrea
-
@charneval
The source port in the Outbound NAT rule has to be any (according to the port forwarding rule). The source port is dynamic, not static. -
If you have a VPN between the sites, there's no need to port forward anything. Just set the appropriate rules.
Or maybe I'm missing something? -
@jarhead
Seems so.
We are talking here about forwarding requests from public internet sources to a device at the other site. -
Hello.
i can't figure out where the error is and i would like to trace packets to see where they are blocked.
I try to enter on port 8080 (https://89.189.48.194:8080) which should send me back to the web server of the nas (172.16.9.240) behind the firewall 172.16.9.254 of the remote office (this is the site to site vpn client) .
Is nat's rule correct in your opinion?in the remote firewall (client of the vpn) I don't have to do anything right?
He knows where to reroute the packet that should come to him from the VPN interface.Thanks.
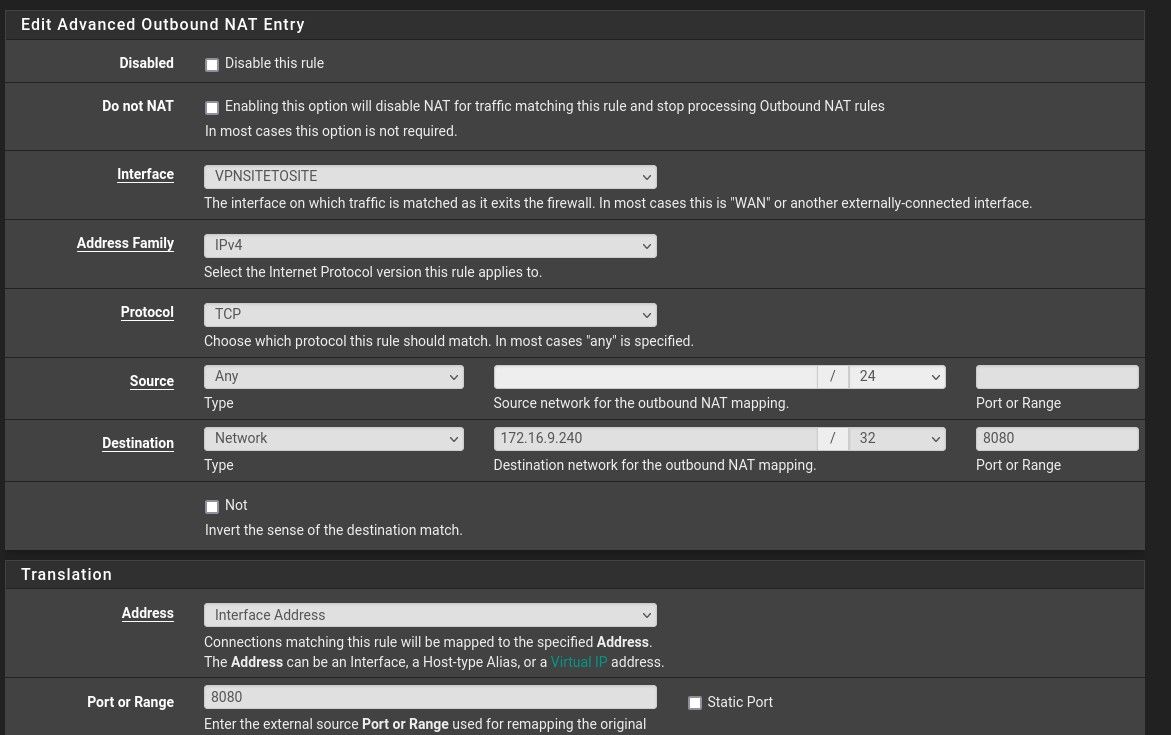
-
@charneval
Also the port translation box must be empty. However, basically it should work anyway.Did you enable the port forwarding to 172.16.9.240:8080?
On the remote site you need you need to allow the incoming packets, either on the interface you've assigned to the VPN if any or on the OpenVPN tab.
which should send me back to the web server of the nas (172.16.9.240)
Is it a web server running as VM on the NAS or the web interface of the NAS itself?
A NAS typically blocks access from outside of it own subnet by default.He knows where to reroute the packet that should come to him from the VPN interface.
The outbound NAT rule translates the source address of packets destined to the remote web server into the virtual IP of the OpenVPN server (or client, doesn't matter. btw. you didn't show the interface assignment. Is it the correct network port if you have multiple VPNs). So this is the IP the web server will see. That responses come back to the remote pfSense requires the it's the default gateway of course. Since the remote pfSense has a VPN with the servers IP it should route responses back properly.
-
Thanks to this fantastic forum I was able to solve my problem.
Thanks a lot to everyone and especially to @ viragomann