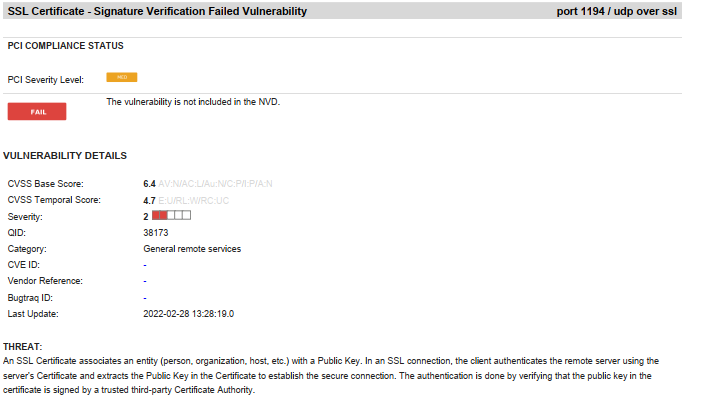
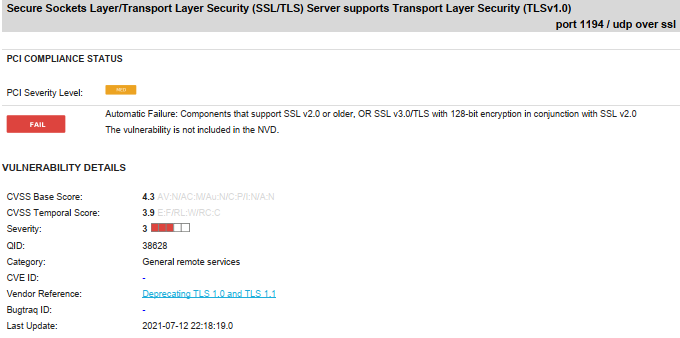
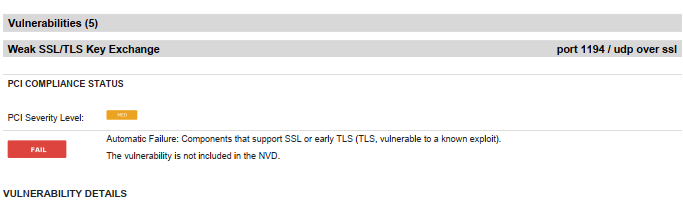
Site-to-Site VPN Tunnel Flagges in PCI Scan
-
@viragomann I can enter that. Would that be through the command prompt, Execute shell command?
And are the two top screen shots about the same TLS 1.0 being active still?
Would this affect other VPN clients that I have with OpenVPN?
Thank you,
-
@parkerask_centuryci said in Site-to-Site VPN Tunnel Flagges in PCI Scan:
I can enter that. Would that be through the command prompt, Execute shell command?
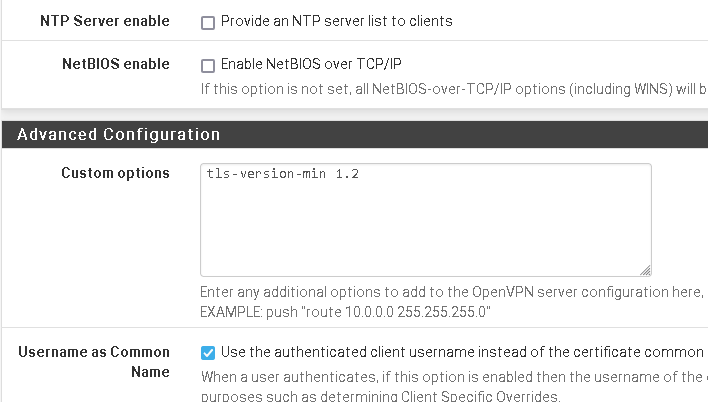
In the OpenVPN server settings.
And are the two top screen shots about the same TLS 1.0 being active still?
About the first one I'm not sure, but think so.
Would this affect other VPN clients that I have with OpenVPN?
No, all clients should support TLS 1.2 nowadays.
But when changing the server settings, the client connections are dropped and they have to reconnect. -
@viragomann That sounds good. I can put that in behind my custom routes.
-
@parkerask_centuryci said in Site-to-Site VPN Tunnel Flagges in PCI Scan:
I can put that in behind my custom routes.
Separated by a semicolon.
-
@viragomann I have saved the line in and the VPN tunnels have reconnected. Is there a way to check what version they are on?
And is there a way to disable TLS 1.0 or did the command do both at once? Still learning the system.
Thank you,
-
@viragomann This morning the VPN tunnels are not up and not connecting. The firewall does a reboot every night. I did check the logs and found that it was exiting with an error now.
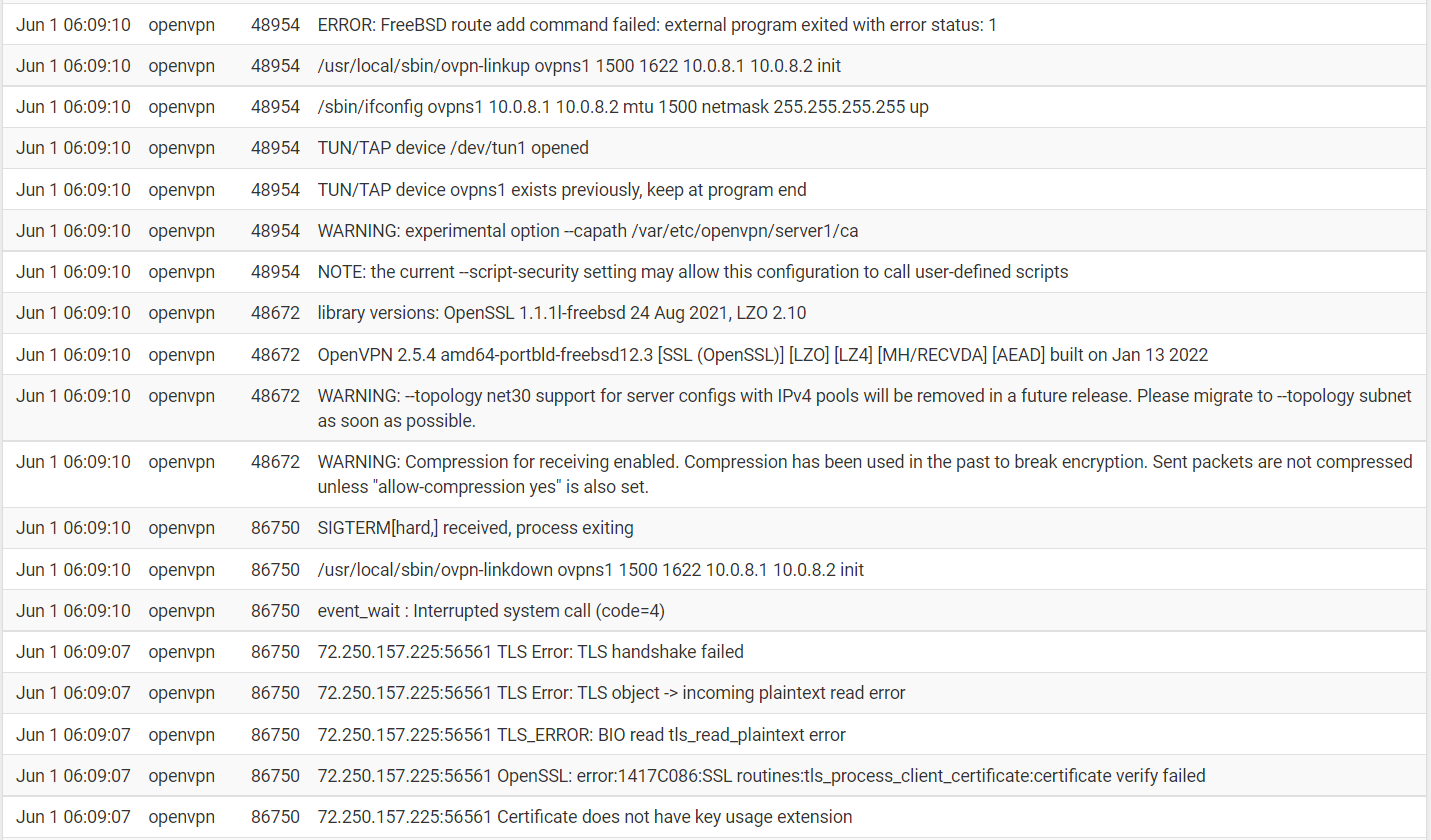
What would be the main problem here? IS it the compression or is a certificate failure?
After a few minutes the tunnels came back up. This is very strange and makes me nervous. The system rebooted at 4:30 am and it took this long to come back? The only thing I did was to remove the tls-version-min 1.2 command. Then I added it back in when the tunnels still did not come back after a few minutes. Both times I saved.
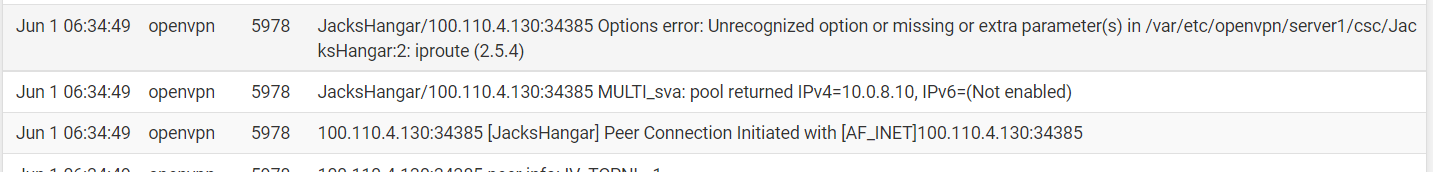
I am wondering if this will happen tomorrow when both firewalls reboot.
-
@viragomann Update: So this morning, I could only get the tunnels to come back after taking out the new tls setting. After a couple of minutes, both tunnels connected. I added in the setting again and it did the reboot. Currently both tunnels are up and working.
Here is a screenshot when they were not working earlier.
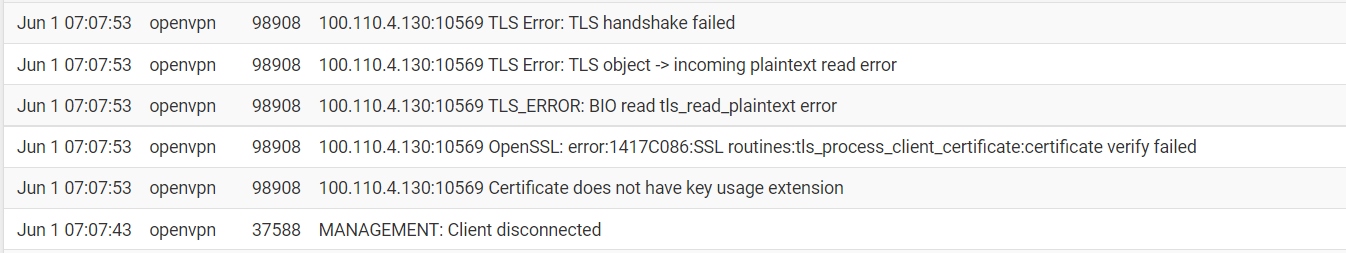
Is this again related to the certificate? Would you like to see my settings for the VPN Server?
-
@parkerask_centuryci said in Site-to-Site VPN Tunnel Flagges in PCI Scan:
So this morning, I could only get the tunnels to come back after taking out the new tls setting.
The log from 6:34 let me assume that there was something wrong with the advanced options.
Are your VPNs both site-to-site? What are the clients?
The other log shows an error thrown at client cert verification. But if the cert really doesn't match, he would never be able to connect. However, as a understand, the connection worked in the past.
-
@viragomann Yes, both of the VPNs under 1194 are Peer to Peer (SSL/TLS).
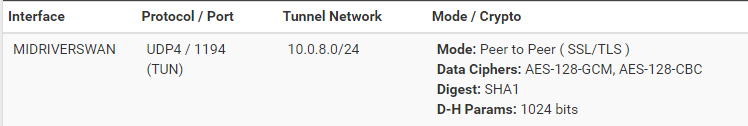
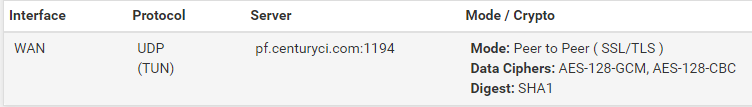
They both have a device mode of: tun - Layer 3 Tunnel ModeYes, they did work before the addition of the TLS min. I would every so often restart the OpenVPN server to reconnect/establish a connection. I have changed no other settings. I do restart both firewalls. The top one starts at 4:30 to reboot. The second one reboots 5 minutes later. I did this to have a fresh connection (and clear cache) each morning. Otherwise I had to restart the VPN service once a day anyway.
-
@parkerask_centuryci I had to remove the line to bring up my secure tunnels again today. Right now I have removed it till we can find a way to have the tunnels come back after the Firewall reboots in the morning. I do not want to have to do an hours work for it to come back for the day.