ntopng sshguard
-
I'm running into the situation where ntopng is triggering sshguard on pfsense causing it to ban it's own wan address. This can be resolved by relinquishing and renewing the ip address but a few minutes later sshguard moves to ban the next address. I'm interested in retaining the active device discovery in ntopng, which I think is what's causing this, but I'm uncertain how to configure things so I don't get an allergic reaction out of sshguard. Any suggestions?
Thank you.
-
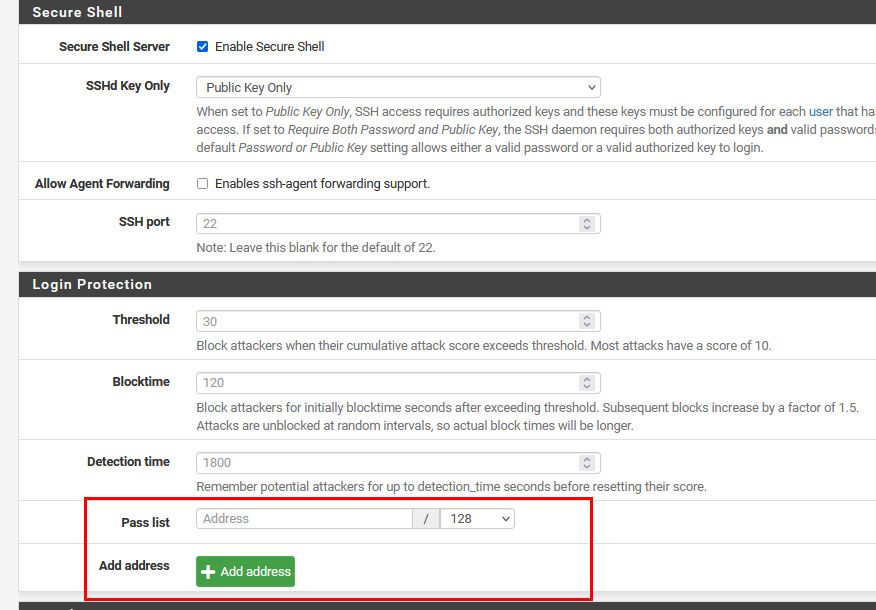
@calvinchu Your talking about pfsense locking out the IP.. You can add IPs to the bypass list so won't lock out on traffic from those IPs
https://docs.netgate.com/pfsense/en/latest/config/advanced-admin.html#login-protection
For example, it may be necessary to add entries for network monitoring systems which probe the SSH port but do not login. Otherwise such systems may be flagged as attackers.
-
@johnpoz If I add the WAN address to the whitelist to prevent pfsense from blocking the wan address when the scanning is coming from pfsense, this suggests that this would cause sshguard to let through all attacks from the WAN and never block legitimate attacks. Is that right?
Thanks.
-
@calvinchu said in ntopng sshguard:
block legitimate attacks. Is that right?
huh? How would a legit attack be coming from your own IP?
Not sure why you would be having ntop using your wan interface anyway.. So your using discovery and checking all IPs on your wan network?
Ntop should really only have lan side interfaces selected.
-
@johnpoz Aha! I think that solves the problem. All interfaces were selected in the ntopng configuration. I excluded the wan interface and I think all is good.
-
@calvinchu hmmm its been a while since I installed and setup ntop, and I only ever turn it on if actually looking for specific data. But I "believe" it defaults to no interfaces selected.. Prob not a good idea if it defaults to "all" interfaces being checked.
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on