No traffic between OpenVPN instances....
-
@neogrid
Yes, there is a very good reason for this behavior. If you route all upstream traffic over the VPN (default route points to the VPN gateway), why would you add routes for specific networks additionally? They are part of "all". So there is no need for extra routes. -
@justanotheruser said in No traffic between OpenVPN instances....:
@viragomann "10.1.1.0/24,10.2.1.0/24,10.3.1.0/24"
Tried it... Did not work.
Possibly you did something wrong. Did you also configure the Remote Networks on the remote sites as suggested?
-
@justanotheruser said in No traffic between OpenVPN instances....:
My setup:
10.1.1.0/24 Local LAN1
10.2.1.0/24 Remote LAN1 (OpenVPN Net2Net instance 1)
10.3.1.0/24 Remote LAN1 (OpenVPN N2N instance 2)
10.4.1.0/24 OpenVPN Roadwarrior (my laptop is 10.4.1.2 when connected)The issue is that when I connect my laptop (10.4.1.2) to the router (via OpenVPN), I get:
- internet traffic and LAN1 (10.1.1.0) traffic fine.
I don't get:
- traffic to the other N2N VPN connections (10.2.1.0 & 10.3.1.0)
I have not messed with any gateway settings or "push xxxx yyyy" or anything like that.
Any ideas what I'm doing wrong?
Do you have access to all networks from the local LAN?
In the server config for instance 1 and 2, the local networks should be 10.1.1.0/24, {RW tunnel}On the client sides, the remote networks should be 10.1.01.0/24,10.2.1.0/24,10.3.1.0/24.
The RW local networks should be 10.1.01.0/24,10.2.1.0/24,10.3.1.0/24
-
@viragomann That makes sense. What is the correct way to have a remote user access two remote networks, at the same time (which are themselves both connected via a site to site) ? I know if I enter the networks in the Remote Networks box, it will work, but I would like ALL traffic to be routed via my VPN ?
-
@neogrid
If you have "redirect gateway" checked to route all clients upstream traffic over the VPN, there is no need to state remote networks to be routed over the VPN.
So if the remote networks are 10.0.1.0/24 and 10.10.1.0/24 packets to these are routed over the VPN anyway and the client will be able access them.That means if you want to route all clients upstream traffic over the VPN, check "Redirect gateway", check if the outbound NAT is set properly (if running the wizard) or add a rule manually, but you don't need to care about the particular remote networks.
-
Whew, a lot of stuff to read... I'm not blowing you guys off (I appreciate the help) but, I'm flying out tomorrow.
I'll read all of this and respond in the next day or so.
-
@viragomann Understood. When I am remote I can access all my network and subnets in the 192.168.x.x range at site A. No Problem. While on the same VPN connection I want to also be able to access services at Site B on 10.10.x.x. The two sites have their own VPN connection between them.
So, I don't know how exactly to route my traffic from Remote VPN client to Site A and then to Site B (I'm struggling with this last hop). I can only achieve this if I add remote networks in OpenVPN. However, I want all traffic to go via the VPN, hence that box disappears.
I know I'm missing something simple, just can't quite crack it.
-
@neogrid said in No traffic between OpenVPN instances....:
I can only achieve this if I add remote networks in OpenVPN. However, I want all traffic to go via the VPN, hence that box disappears.
So if I got you correct, your client is connected to an access server at A. In the server settings "Redirect gateway" is checked.
A and B are connected via a OpenVPN P2P. At B you have added the A site's access server tunnel network to the "Remote Networks".But you're not able to access devices on site B from a client connected to A? But if you add the B's LAN to the "Local Networks" in the access server you can?
If that's the case I would suspect that the clients local network is overlapping with site B's LAN.
Run a traceroute on the client to an IP of B to check out where it goes to. -
 file:///home/websurfer/RemoteNetworks.drawio.png
file:///home/websurfer/RemoteNetworks.drawio.pngOk so this is basically my setup

London and Oslo networks are connected over two tunnels with Servers and Clients on each end, so this is my site-to-site connection. When I am in London I can access Oslo and vice versa no problem.
Now say I am in Germany I connect to a third RAS in Oslo or in London, but regardless of the RAS I cannot see the other network.
There isn't an overlap in my numbering.
So if I add my Oslo remote network to my London RAS I see everything, but not all traffic exits the RW VPN (this is split tunnelling I believe).
So I want to be able to connect to London and see Oslo (or vice versa) with all traffic going through the VPN.
This has to be possible, though I must have made a mistake but I just can't see it

-
@neogrid
So what shows the routing table of a client connected to one of the remote access servers?What shows traceroute to a remote IP of the other location.
What is the client OS?
Which kind of VPN are the site-to-site tunnels? Why two? Is it a fail-over group?
Did you really set static routes for the remote site? -
@viragomann said in No traffic between OpenVPN instances....:
So what shows the routing table of a client connected to one of the remote access servers?
This is my phone in the UK connected to my London OpenVPN server:
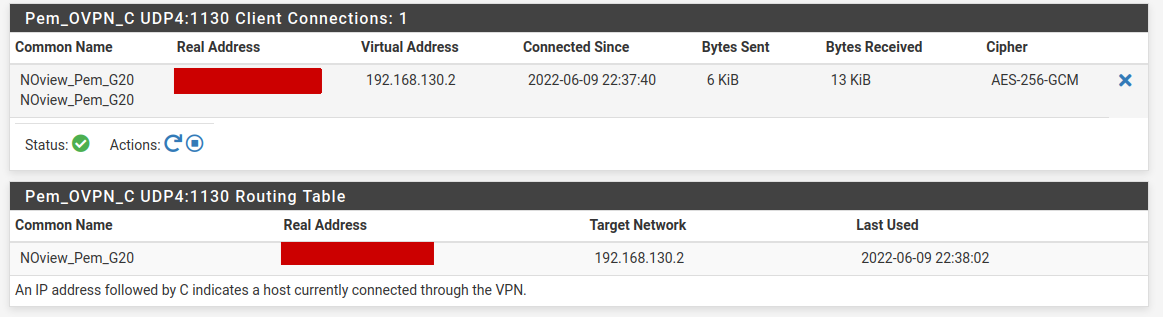
@viragomann said in No traffic between OpenVPN instances....:
What shows traceroute to a remote IP of the other location.
So I'm connecting to my NAS in Oslo from London
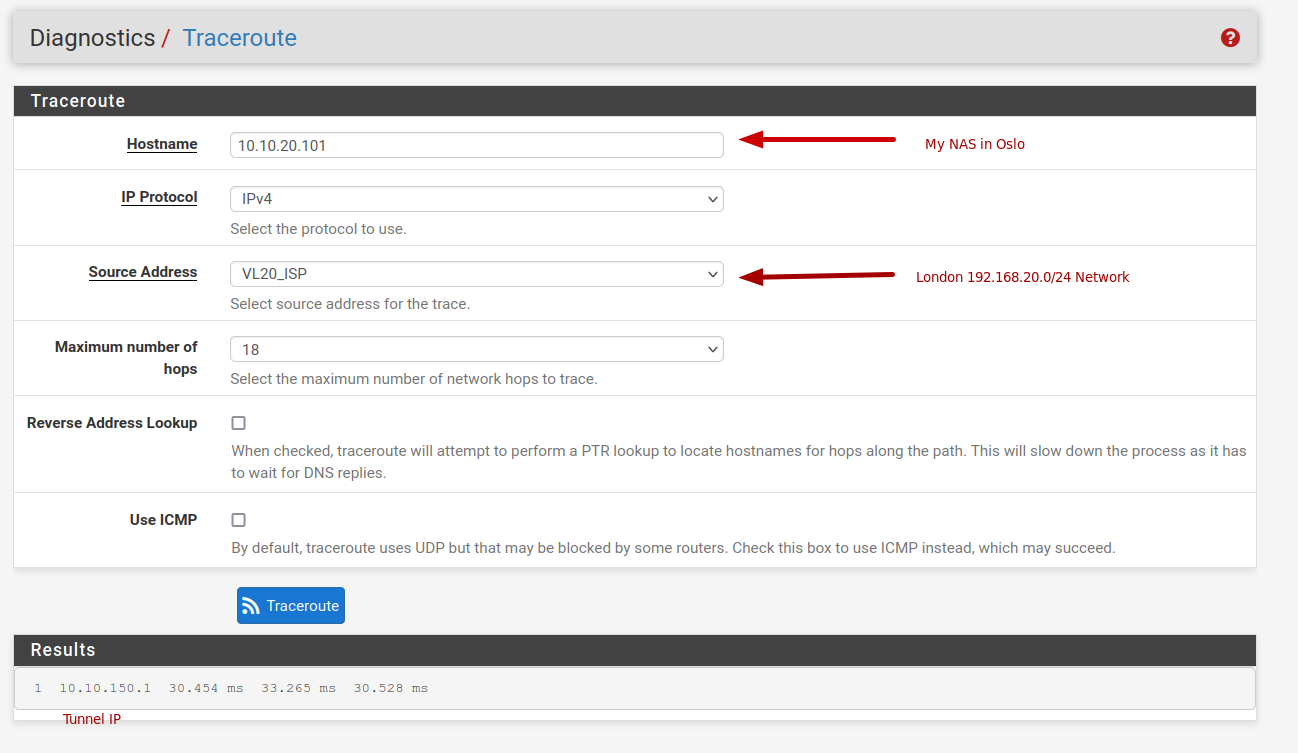
@viragomann said in No traffic between OpenVPN instances....:
What is the client OS?
My phone/tablet runs Android 10/11 or a Laptop running Ubuntu Mate 22.04.
@viragomann said in No traffic between OpenVPN instances....:
Which kind of VPN are the site-to-site tunnels?
All my VPNs are OpenVPN (pfSense 2.5.2. London, pfsense 2.4.5 Oslo)
@viragomann said in No traffic between OpenVPN instances....:
Why two?
My logic was if something went wrong with a single site-to-site tunnel, I have no redundancy. Hence with my setup if one tunnel goes down the other is still up. (It was how I started and kinda ended up here).
@viragomann said in No traffic between OpenVPN instances....:
Is it a fail-over group?
No not at the moment, but I know this is a feature in a later version of OpenVPN but not in pfSense at the moment (at least I could not work out how, with only a single WAN). So to be more accurate, I have several OpenVPN tunnels between my two sites and several RAS servers at both sites for redundancy (because I can) all with unique numbering.
@viragomann said in No traffic between OpenVPN instances....:
Did you really set static routes for the remote site?
These are my routes from London to Oslo, it seems to work ok, and vice versa in Oslo.
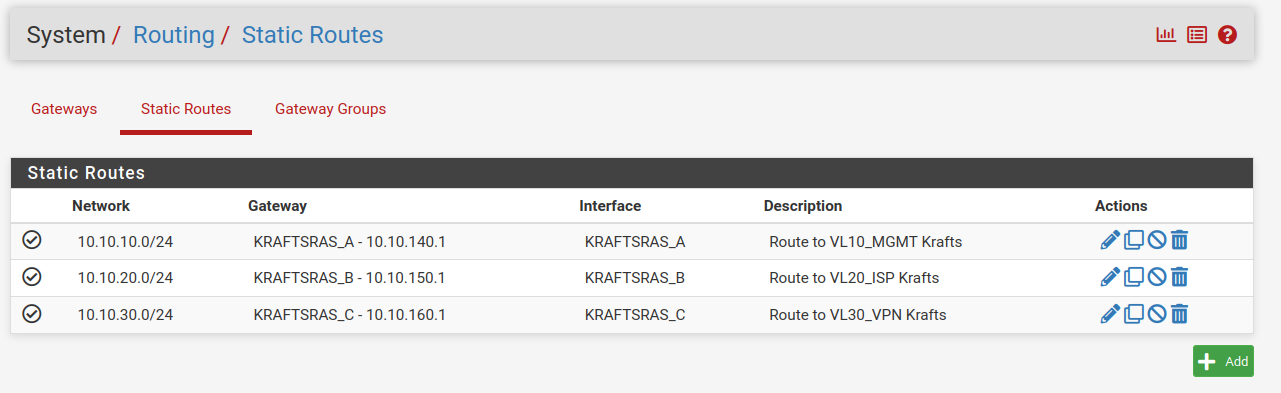
This all works quite ok, just struggling to achieve 2 hops when I connect remotely, I know I have missed something simple ...
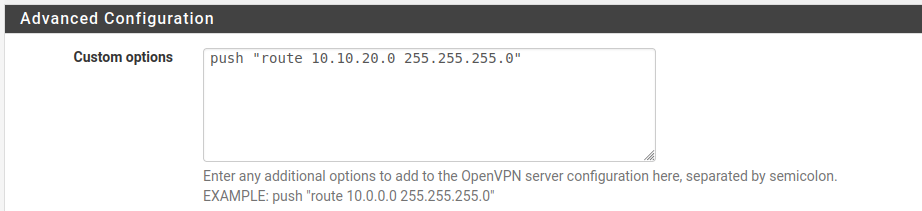
I had thought in the past a possible solution was to add in the Advanced Configuration > Custom options part of the OpenVPN server configuration, - push “route 10.10.20.0 255.255.255.0” - it did not work.
-
@neogrid said in No traffic between OpenVPN instances....:
So what shows the routing table of a client connected to one of the remote access servers?
This is my phone in the UK connected to my London OpenVPN server:
@viragomann said in No traffic between OpenVPN instances....:
What shows traceroute to a remote IP of the other location.
So I'm connecting to my NAS in Oslo from London
The routing table of a client device, which is connected to a RAS would be relevant here, not what pfSense shows at the status page.
As well as a traceroute from one of theses devices directly.Multiple vpn tunnels between the same endpoints should better be configured as a fail-over group for proper routing.
Also it's not a good idea to set static routes for vpn endpoints. For adding routes in OpenVPN, enter the respective networks into the "Remote Networks" field in the settings instead.
But both points might have nothing to do with your actual issue anyway.What is the client OS?
My phone/tablet runs Android 10/11 or a Laptop running Ubuntu Mate 22.04.
I don't know if these devices do the routing as expected, when you push redirect gateway.
If you use the NetworkManager in Ubuntu you can try to add the default route manually, however. There is an option in the settings to add routes.
You may check "ignore server routes" and add your own:
0.0.0.0 0.0.0.0 (no gateway needed, as far as I know)