Mac Address Based VLAN Project -- Success!
-
J24 thank you for the layout. I am attempting to replicate with an orbi (RBR50) in access point mode and by happenstance the same network switch. Trying to keep it basic, I took an old wired windows laptop and put it on the vlan segment 10 via mac binding as you suggested.
Router -> Switch -> Laptop
When I take the same laptop but hard wire it through the orbi, I lose the ip address.
Orbi is on vlan1. When I put Orbi via the lan port on the vlan 10, orbi will not pick up an ip address either.At this time none of the ports have a pvid turned on.
Do you know why this isn't working? I seems like it should.
Thank you -
It sounds like you might be talking about Shortest Path Bridging, which uses MAC in MAC to provide a better switching fabric than with Spanning Tree Protocol.
-
Ok thank you. I read about the protocols
Still struggling however. My ultimate goal is isolating IOT via MAC and the consumer grade mesh systems do not support vlan over ssid as you point out.
My problem is replicating your setup as the packets don't seem to get to the IOT device through the access point. I think it is my switch setup for the access point and If you could further explain your setup for the access point that would help me.
In your project above you state
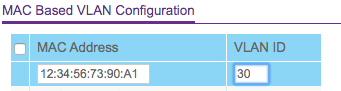
"VLAN 10 -- is trusted devices... wifi devices have their mac address associated with the VLAN tag. It is a mix of wired and wifi devices.
VLAN 30 -- is IoT and those I have to enter the Mac addresses for. All wifi devices."
So my question is how did you configure the switch to allow the vlan traffic to get through the access point?
1- did you set up orbi as an approved mac address to for vlan 10 and 30. This doesn't seem to work for me?
2- did you use pvid for vlan 10 and 30 and plug orbi into that port? I was going to try this next.Appreciate your thoughts.
-
@n70 Did you get this worked out? I think I'm having the same issue. When I connect a machine directly to the switch I have success passing the tag, however, when I run through the access point the switch registers the device in the address table, assigns the tag, but the machine can't get on the network.
-
APs use the VLAN tag to select the SSID to be used. I don't know that they'll pass a VLAN tag, at least not without QinQ.
-
Hello.. My issue was the PVID setup was incorrect. Don't focus on MAC address assigning a VLAN until the PVID is configured correctly. Lets say the router to the switch plugs into port 1 and the switch to the AP leaves from port 8 (on the switch).
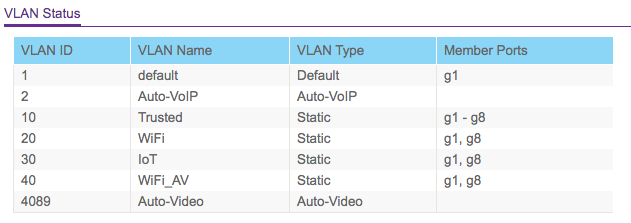
lets use Vlan 1 and 10 from the images above where 1 is default and 10 is trusted; lets put the AP on Vlan 10
Vlan 1 for the router and switch needs to be untagged on the switch side (port 1). Configure the PVID for port 8 to be vlan 10. Finally on Vlan 10 set port 1 tagged and port 8 untagged.
After you can get the PVID setup you can then move onto assign MAC addresses in the switch to assign a different downstream Vlan.
Hope this helps.
-
Does that gs308T support mac wildcards?
-
Replying to myself.
I got the switch and finished setting up. It does not appear to support mac wildcards for mac based vlan. I tried 00, and FF as the wild card characters. Rejects * as well. So each unique mac must be manually entered.
I suppose if there's a long list, one could make a backup which is text based, then following the existing format, paste additional macs in there, restore.
Functionality; My set up at this time is using sophos utm. Each vlan has its own dhcp server assigned along with various firewall and masq rules. The setup does appear to work.
I'll need to use a linux client to do some probing to see if I can see what leaks over on the wifi side from clients on different vlans.
What is missing from the initial steps is the pvid screen, which proved quite important. It is important to assign all pertinent vlans as UNTAGGED in the configuration. In the example below, physical port 8 is the one feeding the orbi device.
For now it's configured with 2 vlans, 4 and 5. Proper connectivity would not happen until vlan 4 and 5 were configured as untagged. PVID of 4 means any undefined (no mac vbased vlan entry exists) mac will be defaulted to vlan4.
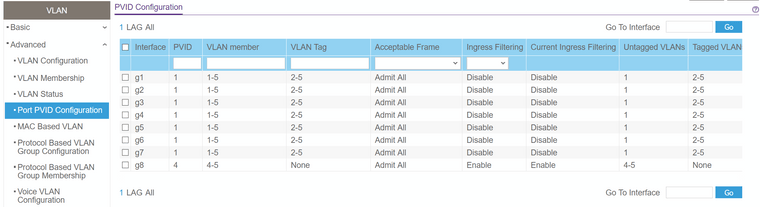
The rest of the lan operates on vlan1, which is not assigned to that port at all. I may make special routing rules later for a few things (like WOL using app on phone). For the most part, I don't want anything wifi having access to the main network.
The switch cost me about $50, the orbi's cost nothing. I am hopeful sometime in the near future someone figures out how to gain console access so the whole vlan mess can be untangled and defined properly. It's a bit odd having the same ssid/wifi password for the guest network as other networks.
-
Yeah it works and hopefully your clarification will help others. Agree its a bit odd that the main and guest networks have the same VLAN,
You can have both the guest and main networks with different passwords in the AP settings for Orbi but it all defaults to the one vlan.
I debated trying to separate the main and guest networks by assign Vlans by the various Mac addresses for the orbi radio frequencies.
you can log into the Orbi router and satellites- at http://192.168.1.1/hidden_info.htm
you will see the there are 2g and 5g mac addresses which i think (unverified) map to
2g main
5g main
2g guest
5g guestUltimately I didn't want to spend the energy, since i figured i would need to do it for the main AP as well as the satellites. I thought it was good enough. If you decide to try this approach and can make it work please report back.
Thanks
-
The problem is this POS is blocked/locked from shell/console access. Both 2.4 and 5ghz bands share the same ssid and can't be divorced. Otherwise I'm sure it'd be simple enough to create several ssid's, each bound to a vlan.
Netgear charges an arm and a leg for this (rbk763s), around $500USD but the functionality is about as dumbed down as wrt54g from 2001.
-
Hi.. do you mean you want to do this?
https://www.tech21century.com/separate-ssid-for-2-4-and-5-ghz-on-orbi/
of course I haven't tried it and didn't want to risk bricking the AP
thanks -
@j24 A bit late to this party, can are you able to share a screenshot of the Switching > VLAN > Advanced > VLAN Membership, for one of your static VLAN groups? I'm trying to see where I'm going wrong with the tagged/untagged options.