VLAN on D-link
-
@fireix Just do what I suggested. You're over thinking it.
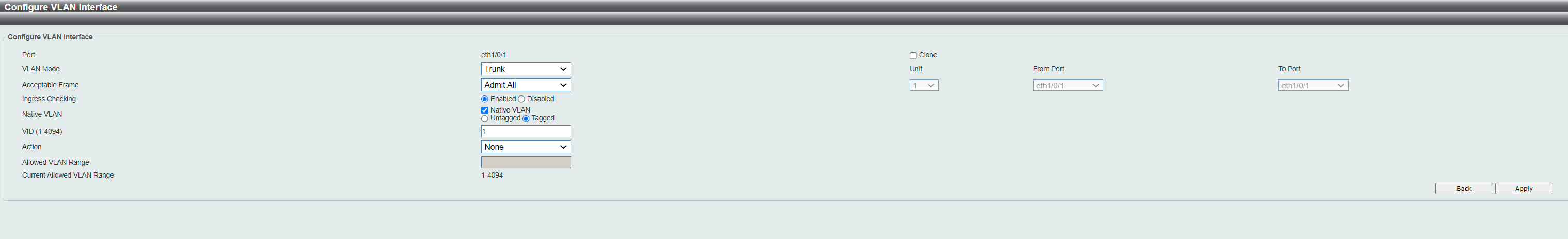
Going by that picture, the "native VLAN" line goes across and you can select native vlan or unselect it. with it selected it means the native vlan is allowed on that port.
Then you have vid, enter 40.
Then you have action, select add. this will add the vlan to that port.
add mode, tagged.
then you should see the allowed vlan range show which vlans are on the port.
Try it.Why not just use the CLI if the gui is too confusing for you?
If the above doesn't work, leave vid 1 in the vid box and try 40 in the allowed box.
-
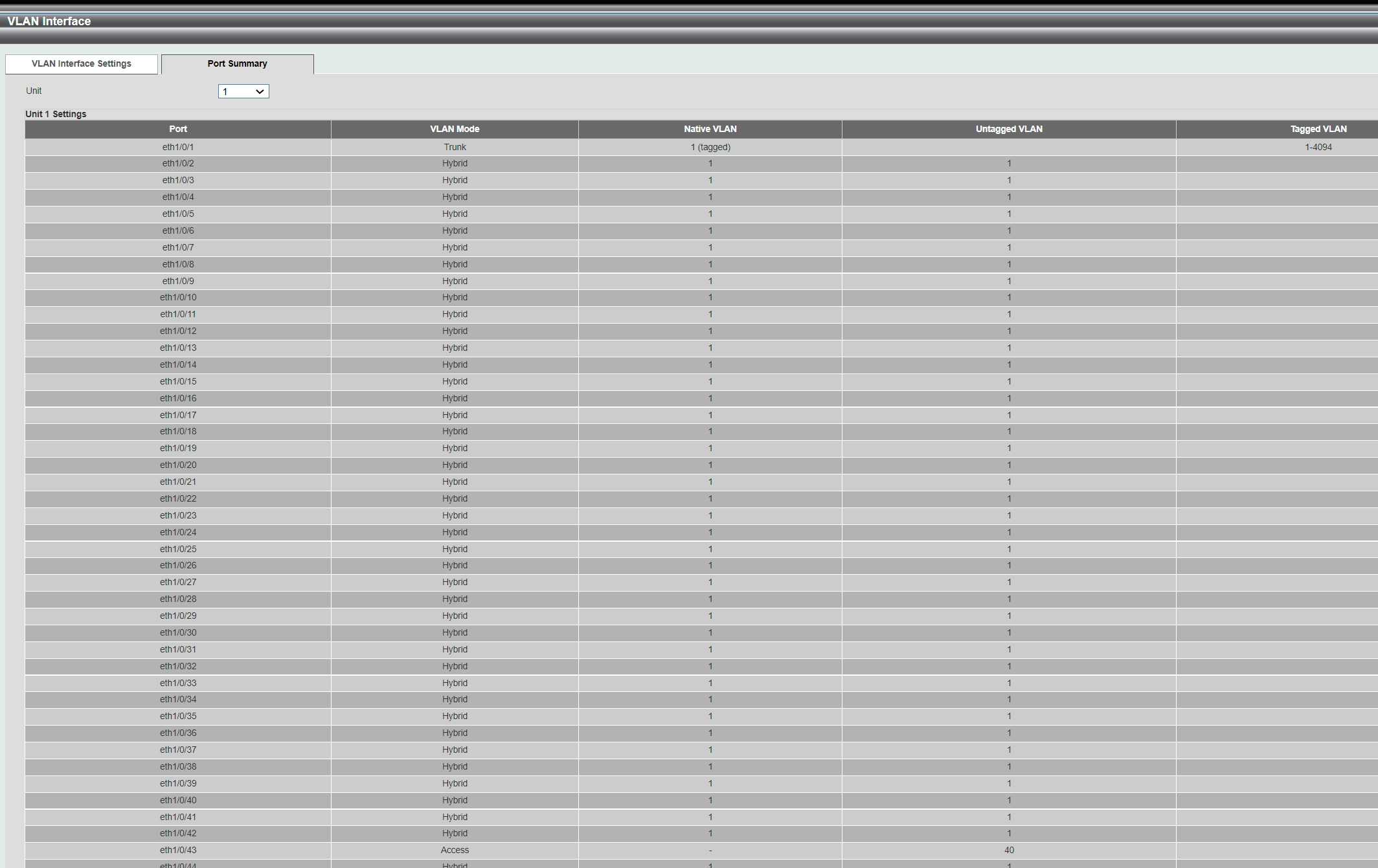
In the dropdown menu, I have "Add, Remove, Tagged, Untagged". It is under the VID-box. This is the Port 1 interface.
When I did as you said, just entered 40 in the VID-box, choose "Add" and choosed "Apply", the Current Hybrid untaggd/tagged VLAN-range list became empty (because the text-box with Allowed VLAN Range was empty and it is my understanding that the dropdown is only for the selected port values under it - so when I had no values in it, it deleted the values displayed at the bottom).
The VID DO change for Port 1, as I shown in previous listing/summary. But I assume that box is only for having a default VLAN in case no traffic is tagged arriving on that port. That makes sense, I would think it was smarter to have it to 1. Since it is port 1 that is a trunk port for many VLANs, not only one. If I enter 43, Port 1 can only communicate with port 43 on VLAN40 (If my understanding is correct).
-
@fireix Read the last line of my previous post.
try that. -
@jarhead said in VLAN on D-link:
@fireix Read the last line of my previous post.
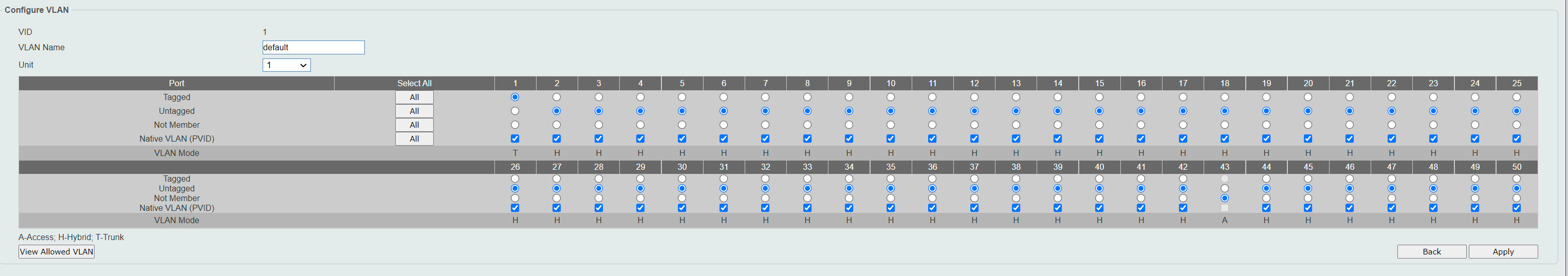
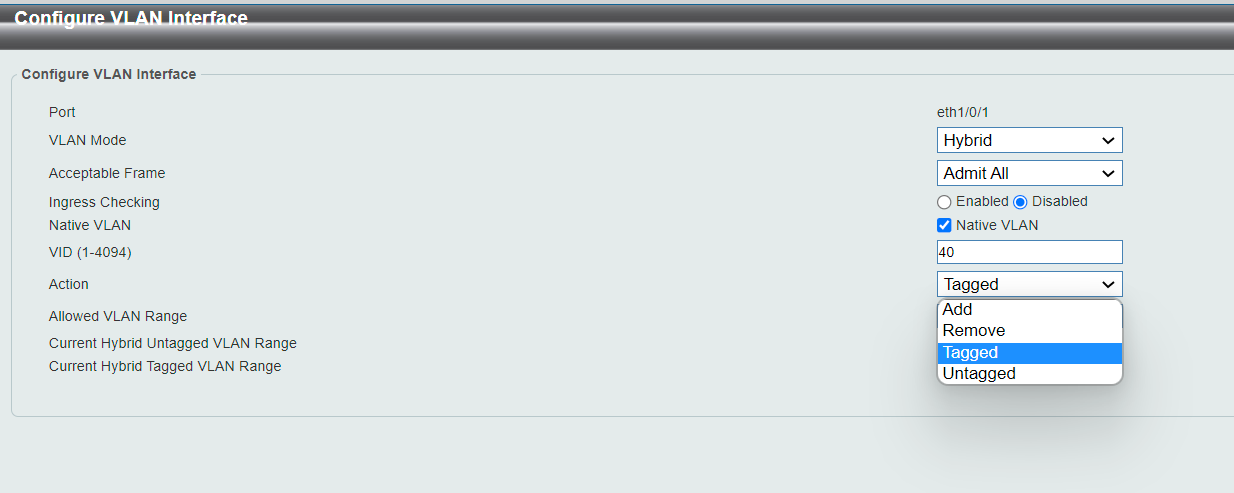
try that.I think that "Allowed"-box is actually port numbers. The reason is that when I select "tagged" or "non-tagged" in the radio box, it changes the number below it. See the screenshot here, this is righ after I entered "40" in the Allowed VLAN Range, selected "Tagged" and choosed "Apply":
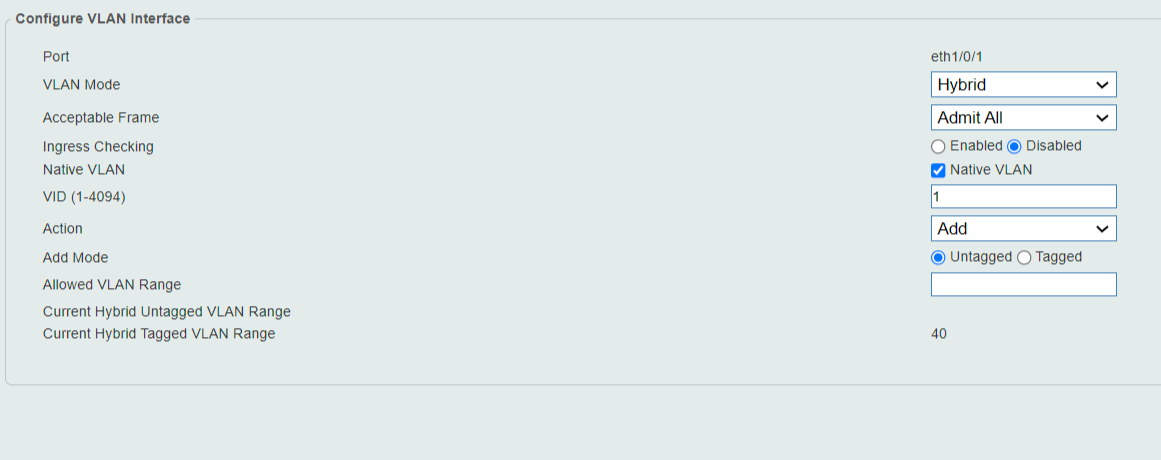
I can even add like "1-43" or "1,43". I was hoping that if I spesified enough ports here, I could "team up" the VLAN in the other list with ports so I could choose Port 1 and Port 43 as member under VLAN40.
-
Here you can see I also put the number "1" and "Untagged". It got added to that list of "Current Hybrid untagged vlan", just like 40. Having an antire VLAN-tagged or untagged doesn't make any sense I think?
-
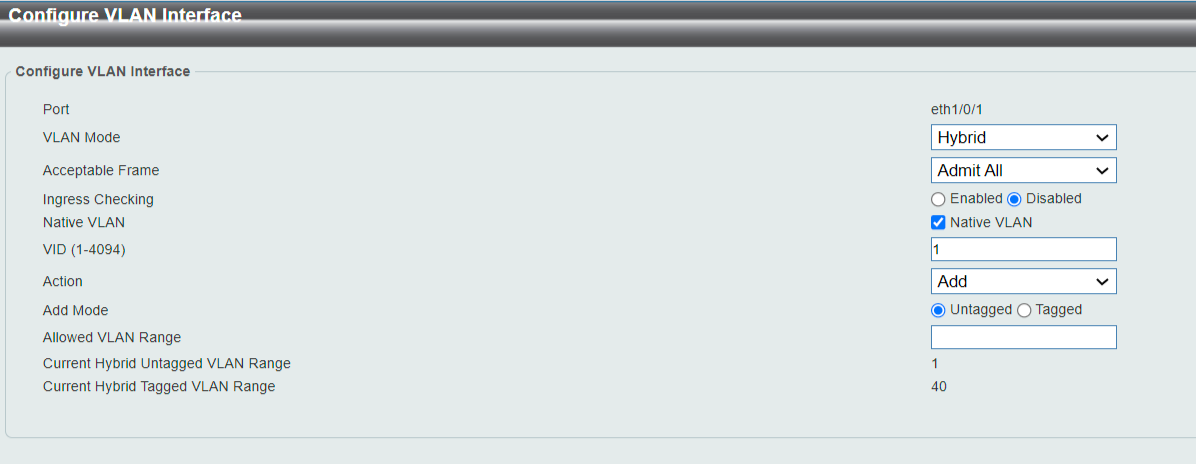
@fireix So that worked then. Good.
-
And here you see another indication that I'm actually adjusting port numbers. After doing what I showed above, the vlan summary looks like this (notice the heading of the columns and you will find the value 1 and 40 again):
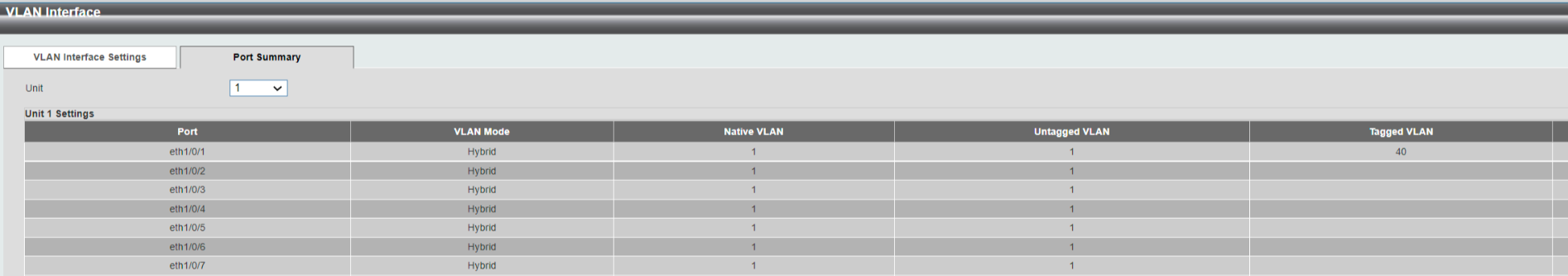
-
@jarhead I don't see I have come an inch longer than before ;) Do you agree with me that it is ports I'm actually editing here - and what should I enter for Current Hybrid untagged VLAN range and Current Hybrid tagged VLAN?
-
@fireix I don't understand what you're saying. It's done. You have vlan 40 tagged on port 1. That's what you want
-
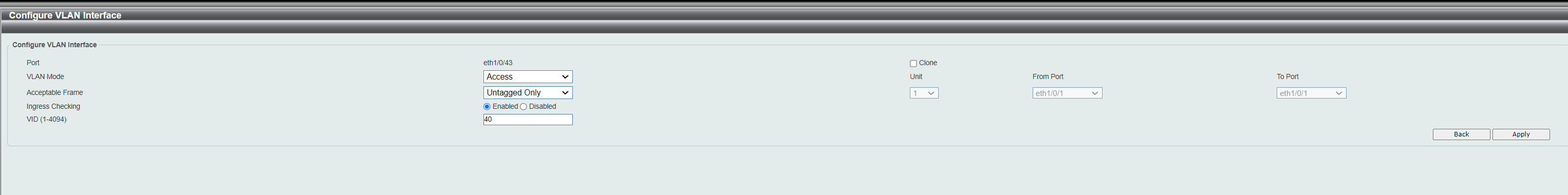
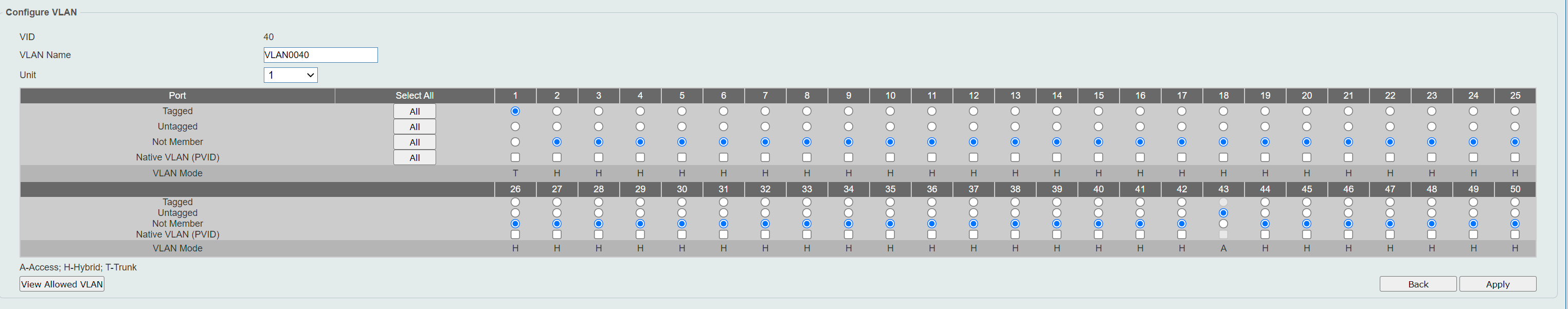
I have no clue why it refuse to set port 1 as Tagged in this interface. In evey other GUI for other vendors, it would allow me to set port 1 as tagged member of VLAN40. It just jumps back to "Not Member" after pushing Save.
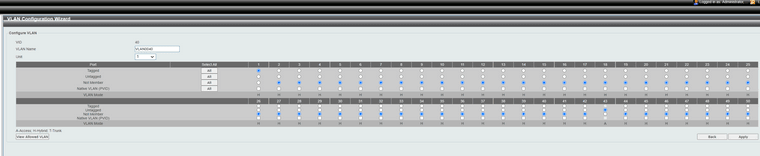
-
@fireix It is tagged. I don't know what you're saying. It's done.
-
@jarhead Is there any term called "VLAN untagged" or "VLAN tagged"? I have heard of ports that are tagged or untagged - but never VLAN itself as it can have any combination of untagged and tagged members. So it sounds wrong in my ears ;) (and the server in port 43 doesn't get any IP from pfSense, so I know it doesn't work).
All my intuition says that the "VLAN 40" to the rigth in that list is actually Port 40. Based on several things, but specially that above.
I'll continue trying tomorrow, thanks for trying to help :)
-
Or maybe I'm wrong.. to tired, time to find bed and look at it with fresh eyes tomorrow ;)
-
Trunk on a D-Link means "Port-Channel in Cisco language"
I don't recommend to fiddle with multi IF trunking, for starters.A port can have one of three "vlan membership states"
Untagged
Tagged
Not Member.Only one of them can be active.
On any port:
Untagged - can only be active on ONE vlan.
Tagged - can be active on many vlans.
Not Member - can be active on many vlans.I have never seen hybrid mode on my switches (not 15xx series) , but sounds like not for starters.
My advice is to :
1:
Decide for a management vlan (could be vlan1 .. if you insist) , make the "last port" an untagged member of that vlan. Move your PC to the newly made mgmt port.2:
Make ALL other ports NOT member of Vlan1 (Usually the default) , to start with a clean membership database.3:
Make & Name the vlans you want to use.4:
Go to the desired vlan , and set the desired port to Tagged/Untagged/Not-Member.
Repeat for all Vlans in use.Done.
Remember a port can only be untagged in ONE vlan.
/Bingo
-
@bingo600 said in VLAN on D-link:
Go to the desired vlan , and set the desired port to Tagged/Untagged/Not-Member.
Repeat for all Vlans in use.I haven't made it work, the GUI is so super confusing and considering just upgrade the switch so I can understand it..
Just a quick stupid question: Is it in easy/possible to have a "dumb" switch (I assume VLAN-tags are just passed on in most cases) and just configure the actual server/PC in a normal port to be on the same VLAN as configured in pfSense?
I see that some windows-server lets you set the network card to a spesific VLAN (under hardware-settings on the network card). So that could be a quicker way for me. The server will run free hypver-v, so I think it would be little administration on it even? Or will it be super complicated? The idea is limit the access/noise to this single server.
-
Where is your issue ??
Vlans on the pfSense ?
Se here
https://forum.netgate.com/post/944383or
Vlans on the D-Link ?
Do as i described above ...or
Both ?
Don't give up ....
We have "talked a lot of people through this"Ohh ... Please tell me you have a pysical pfSense Box , and not a Virtual one.
That's another layer of troubles .... -
@bingo600 Vlans on pfSense Supermicro-server with 4 ports (physical yes) was easy and no problems at all. Followed tutorial to the letter and it looks just fine. Connection from a LAN-port (that has 3 VLANs I set up on it) directly to D-Link port 1.
The problem is D-Link. switch and to do the thing you describe under 4. (choosing tagged, non-tagged, non-member) in the interface. I understand your instructions , but the GUI simply doesn't let me to do it easy as I can see all other GUIs let you do (even on cheaper switches). It is at least 4-5 different places and it isn't always clear what each setting will do. What I can do in the "Member" interface depens on all those 4-5 other places and even then it doesn't let me to do a tag 1 port and untagged 43 port (it refuse to let me have port 1 tagged/member, even thougth the option is active).
The easy part is to create the VLANs and their naming, that was super easy everywhere.
Not giving up yet, just taking a break.. maybe try to read up on how to do it from terminal/shell instead. But requires som learning of dlink syntax.
I will create a small lab at home just to see if I can do it on other switches.
-
Did you remember to select vlan1 , and make all ports except the one you use right now on PC for manage , NOT MEMBER.
That bit me more than once , that D-Link defaults all ports to be untagged in Vlan1. Then you're locked with a lot of other selections.
I have 1100 & 1210 series.
What model do you have ?
If you have a 15xx then it seems like Trunk is like "Cisco Trunk" , and not Port-Channel"
https://eu.dlink.com/uk/en/support/faq/switches/layer-2-gigabit/dgs-series/es_dgs_1510_escenario_config_vlan_por_gui_y_cliThere seems to be an error in the D-Link example
http://forums.dlink.com/index.php?topic=73651.0Makes sense ...
A switchport would not be able to do both tagged & untagged VlanX (here 2)
So the range 1-3 should be 1,3 , as 2 is untagged.I do agree it looks rather confusing , with :
Access
Hybrid
TrunkTo me it seems like :
Access is "access" single untagged vlan membership .
Hybrid can have one Native/Untagged Vlan , and multiple tagged vlans.
Trunk seems to be for just "tagged" vlans.I would use a Tagged port towards the pfS interface.
But on my D-Links where i have no ingress control, i use what they call hybrid.
I made a Vlan XXX as a Dummy Native Vlan , and set all my Native Vlans on my "Trunk ports" to Vlan XXX , to "blackhole" untagged traffic on my trunkports.
I have NO untagged Vlan on my pfS trunk interfaces.As i see it Trunk is "Hybrid" with untagged frames filtered away in ingress (entry).
/Bingo
-
@bingo600 DGS1510 52X is the switch I have.
I agree that port 1 should be tagged (pfSense). I assume setting Trunk would mostly do the same. I wanted to keep vlan1 for all current traffic except the port of the server I want on the different vlan. That port should be untagged. Here I assume Access-port do the work automatically and removes some options. But a bit complicated to know the difference.
But is there something called "untagged VLAN" and "tagged vlan"? I know untagged/tagged ports in a VLAN, but actually hole vlans?
-
@fireix said in VLAN on D-link:
But is there something called "untagged VLAN" and "tagged vlan"? I know untagged/tagged ports in a VLAN, but actually hole vlans?
A Port cant be tagged or untagged , only a Vlan can (tags belongs to Vlans).
A Port can be :Member of (Carry traffic for) one or more Vlans (tagged), One Port can only carry untagged traffic for ONE vlan.
If a port is member of "Untagged Vlan X" , then it can't also be member of "tagged Vlan X".
Untagged ports are usually used for "normal devices" PC's , APPLE-TV's etc , that has a "Normal networkcard setup" .
Tagged traffic is used between devices that carry traffic containing several vlans.
pfSense to switches , switches to switches , Hypervisors to switches , and is also often used to connect to accesspoints that runs several ssid's.You would 95% of time make a standard PC switchport , an untagged member of VlanX
When a port is "Untagged member of VlanX" , it just refers to the frames sent between the "device ie. PC" and the port , here untagged means the port communicates with the end device , with normal ethernet frames, plain network card setup.
The traffic received on that untagged (Vlan X) port , will be tagged (with Vlan X id) and sent to all other ports that are tagged members of VlanX , that's how ie. pfSense sees the data from an untagged port , via the tagged connection from the switch to the pfSense.The traffic received on that untagged (Vlan X) port , will also be replicated to all Ports that are "Untagged members of VlanX" , here it will be sent put as "untagged" aka. normal ethernet frames.
Edit:
You should really read the post i made here , about tagging (envelopes)
https://forum.netgate.com/post/944383/Bingo