Want to segregate my IoT devices again.
-
I was using a Netgear RAX42 router before I set up my Netgate 4100. I put all my IoT devices (which happen to all be wireless) on my Guest network. The Guest network would prevent any device from seeing any other device on that network. It would just provide access to the Internet.
I reconfigured the router to work in AP mode and connected it to my switch that's on the LAN port of the Netgate 4100. The Guest network works, but there is no way for the router to segregate the devices on that network. I understand why this is the case since the router is no longer "routing."
I assume I need to set up a VLAN for my wireless IoT devices. Unlike hardwired devices, I cannot physically separate the traffic to a different LAN port on the Netgate 4100. I'm assuming I will have to set up a VLAN using a new internal IP range and assign each device to that VLAN based on its MAC address.
Am I on the right track? Is there a guide or YouTube video on this topic? Should I ditch my router and get a different wireless setup?
-
@gpinzone What is your router that you "reconfigured the router to work in AP mode"? Does it support VLANs in the network settings?
If it does, and you don't want to do anything fancy (meaning you don't need a managed switch connected to pfsense to handle VLAN traffic), you can make 1 physical cable run back to your pfsense box from your AP. Then on the AP, configure as many VLANs as possible, and also setup the pfsense box with these VLANs.
You should run VLANs on your wireless AP if you want it to serve multiple wireless roles - management, guest, kids network, smart thermostat or lights, smart TV or streaming boxes, work laptop network, iot, wireless cameras, wireless appliances, etc.
Here's the instructions for setting up VLANs on pfsense:
https://docs.netgate.com/pfsense/en/latest/vlan/configuration.html -
@gpinzone said in Want to segregate my IoT devices again.:
The Guest network works, but there is no way for the router to segregate the devices on that network. I understand why this is the case since the router is no longer "routing."
This can only be done on the AP, even if it's in AP mode.
There should be a setting to prohibit traffic between connected devices.pfSense or any other device can do nothing to segregate wifi devices, since traffic between them won't pass it.
-
@viragomann That option is grayed out.
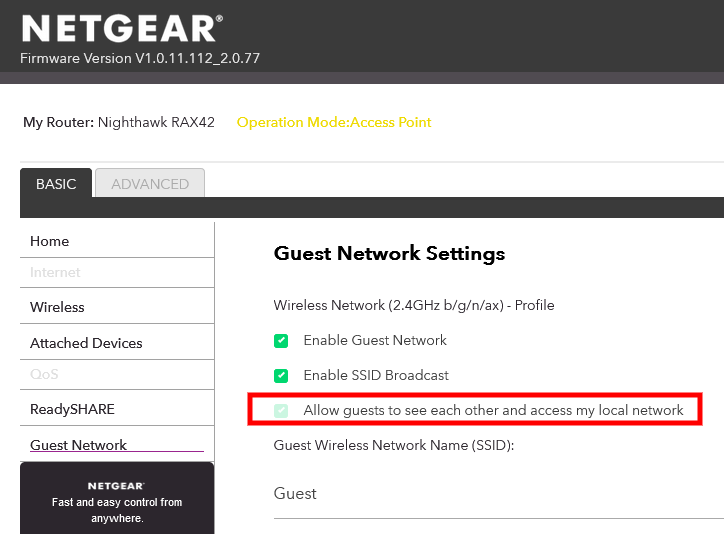
Once the router is put into AP mode, it does not assign IP addresses, QoS, port forwarding, etc.
I suppose I could put the RAX42 on a different LAN port, but then all the wireless devices would be affected, right?
Perhaps VLAN isn't the correct solution. Is there any way to segregate devices based on their MAC address? Or, is there a way to prevent a device from accessing the local network by its MAC address?
-
@gpinzone
You're showing the guest network settings here. There is no guest network in AP mode for sure.You have to look into the wireless settings.
I don't know the Netgear features, but I assume the setting should be there. -
@viragomann Just to clarify: There is a guest network and it works. The only option that doesn't work is isolating the devices connected to the guest network. It's understandable. I suppose I could buy TWO wireless devices and connect them to different LAN ports, but that's silly.
-
@gpinzone most of those wifi router that support AP mode are pretty limited in what they can do. I have yet to see a soho wifi router that can do actual vlans with native firmware. Really need to use ddwrt or openwrt, etc. to actually get vlan support.
But if all you want to stop is clients on ssid from talking to each other. That most likely called AP isolation or Client Isolation or L2 isolation.
If your goal is actual segmentation of your different wifi devices from other stuff on your network - your best bet would be to get an actual AP that supports vlans..
-
I found this video: https://www.youtube.com/watch?v=hhPGN4UJHAM
It sounds like the issue is that most wireless routers in AP mode do NOT have any ability to assign their wireless guest network to a VLAN. Unfortunately, he didn't explain what UniFi controller he was using.
-
@gpinzone
If you want to provide a guest network aside of a trusted ones you should get an AP which supports multiple SSIDs. So you can assign a different VLAN ID to each SSID and control traffic of each on pfSense.
Seems your AP doesn't support this. -
@gpinzone Hey there,
I guess it is the cloudkey controller for unifi devices...
Unifi APs are no reduced routers but just for the purpose of being an AP. You have up to 4 SSIDs, so you can create your vlans on pfsense and then point those to a ssid on your ap...
This way you can use one AP with up to 4 vlans (WLAN Guest, WLAN IoT, WLAN home, WLAN kids...like that).
Add your firewal rules and your IoT can talk to each other but not to the rest of your homenet devices (or the Internet if you restrict that as well).A cloudkey controller can be purchased, it can run on PC, NAS, raspberry...
As always...some light, some shadow... -
@the-other said in Want to segregate my IoT devices again.:
You have up to 4 SSIDs
Actually you can more than, if you turn off monitor link you can get 8. And you can actually setup different ssid on 2.4 than on 5 so in theory you could really do 16.
And actually if you use radius to to assign the vlan you should be able to really have an almost unlimited number of actual vlans.
The soho stuff just doesn't want to support vlans at all. You need an actual AP, that is meant for pro-consumer or smb, business etc..
I have been using the unifi stuff for many years. And have no issues at all with them, pretty happy with what they do, how easy they are to setup and the pricepoint.
If your goal is to segment your network.. Pfsense (you have that already) and then you need vlan capable switch and vlan capable AP(s) and then your cooking with gas ;)
-
@johnpoz
Absolutely with you...I meant just "out of the box" up to 4 ssids...and yes, overall, I am quite happy with unifi so far as well (2 APs and cloudkey)... -
@the-other true - I wouldn't really recommend doing too many ssids ;) because they do come with more overhead with your management frames, etc.
In the big picture in a home setup prob not going to be an issue - but can be seen as a hit and performance hit if you have lots of clients and your trying to squeeze as much performance as possible out of your available bandwidth.. But in a home setup with a few clients, or low requirement clients like iot devices prob not an issue.
I'm currently running 4.. My trusted network where my phone and tablet etc. then a iot segment, a roku segment where all my streaming sticks connect and a guest network for my friends and stuff that come over.
A while back I did play with assigning vlans via radius and that works.. So could be slick and you could even assign vlan based on mac auth.. But while I did get it to work, it was going to be too much effort to switch over all devices to be using that, and just easier to just use different ssid. But it kind of slick setup - just too much extra management for simple home setup.
-
@johnpoz funny, I was planning on radius assigned vlans a while ago...and then buried the idea, cause it is just my home network...so 100 % with you once more...there is a bit more to life than configuring and re-configuring my (working) network...
-
@the-other yeah ;) it was just to see if would work, etc. But then thought about all the extra work to actually move to it, and then future work if adding any extra devices, etc. And was like is it worth it?? Answer to myself was no - heheh
But it was a fun project to prove could be done with just basic home budget level hardware.
I really should move away from the local.lan network using and use home.arpa - but again, I have a bunch of certs being used for like unifi controller, nas, switches gui, etc. And was like - man that is a bit of effort for no real benefit..
My unifi controller software cert expired a while back, and had to remember how to install cert - they make its such a PITA.. And then I forgot to add the home.arpa as SAN.. Should I just redo it, said screw it - I will do it next year ;) heheh
-
@johnpoz and (boooring) again conform with you regarding pita with certs and unifi...really sh...y implementation.
:) -
In case anyone is wondering what's needed to get this to work, a bare minimum configuration is shown here:
https://www.youtube.com/watch?v=DL4vMLgBrYI
The video is 4 years old, but it can be done without a managed switch if you have a suitable WiFi adapter that's VLAN aware.
-
@gpinzone said in Want to segregate my IoT devices again.:
done without a managed switch if you have a suitable WiFi adapter that's VLAN aware.
You mean a wifi adapter installed on pfsense? Yeah that would be the wrong solution for sure - freebsd and wifi is not a good mix at all.. Not pfsense problem its a freebsd problem - just not a good choice for wifi as a AP..
Can it be done - sure.. Is it going to be something you are happy with, if you have really really low expectations maybe.. I would never in a million years set something like that up.. You would be better off getting some 20$ soho wifi router and just using it as AP, if you want vlans then put ddwrt on it.
Me - I would get actual AP, they can be had for under 100$ and have stable wifi network current tech, poe for AP that can be placed correctly for good coverage and support vlans, etc.
The Omada line from tp-link get decent reviews, again a "proper" AP and very low 100 price range right on amazon. AX with OFDMA and mu-mimo, etc.
The U6 lite from unifi is $99 (when they have them).. Are they the lasted and greatest best wifi 6 AP - no.. But they get you wifi 6 and stable, feature packed.. I don't even think you can do AC with freebsd and any wifi card?
-
@gpinzone
Really, not a good config...
Just get a small cheap tp link with 802.1q (vlan) ability, here (germany) around 30 euros.
And a standalone AP...
Enough playground for starts. Pfsense, 5 port Smart managed switch, ap, vlans...simple segregation of iot and guests. -
@the-other exactly..
The AP doc on netgate - sure isn't a doc that that screams use pfsense as your wifi AP ;)
https://docs.netgate.com/pfsense/en/latest/wireless/configuration-ap.html#pfsense-as-an-access-point
Now lets say you were marooned on a desert island and you had xyz gear to use and you had to setup a wifi network to try and get rescued - then ok sure you could make it work ;) hehehe
But even with only a $10 budget, pretty sure you could find some old wifi router on ebay that would make for better AP than a card in pfsense ;)