Pi-Hole + Unbound vs. pfBlockerNG
-
I used to use a Raspberry Pi running Pi-Hole with Unbound. I set that up as per: https://www.youtube.com/watch?v=FnFtWsZ8IP0
I had to make a few whitelist exceptions, but it has worked without any additional effort.
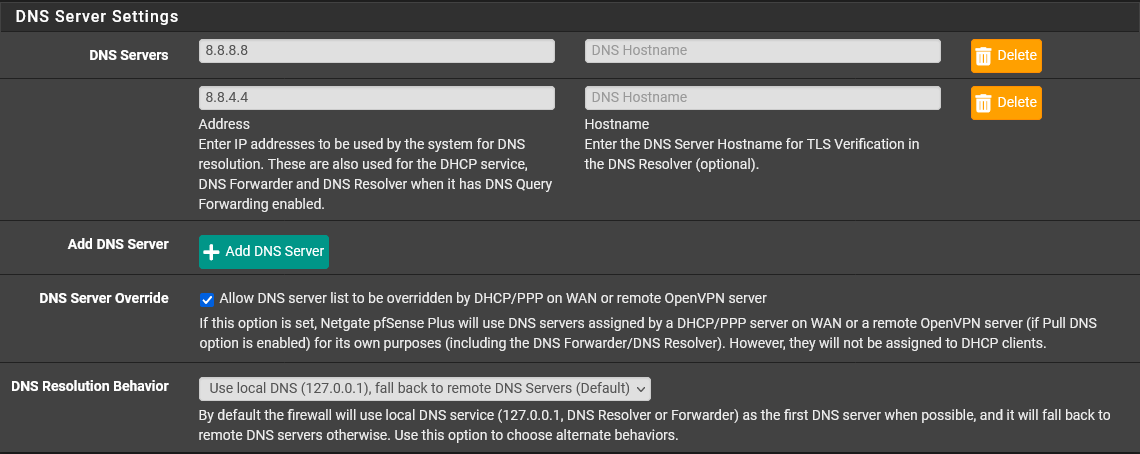
I just installed a Netgate 4100 and installed pfBlockerNG-devel 3.1.0_4. During the setup wizard, I entered the Google DNS servers (8.8.8.8 and 8.8.4.4).
The default block list is the same one used by Pi-Hole and I believe it uses unbound for DNS, too. The only thing I had to do is add my custom whitelist from Pi-Hole to pfBlockerNG. I added the entries to the DNSBL Whitelist, forced an update, and my known websites that were broken by the default adblocking now worked.
Question: The DNSBL Whitelist is populated with 46 entries by default. Where do these entries come from? Is it a default of pfBlockerNG? Now that I added additional entries to the list, will that list update when pfBlockerNG upgrades/updates? If it upgrades/updates, will I lose my entries and have to add them again?
On my status page, I see the following under DNS server(s):
127.0.0.1
68.237.161.12
71.243.0.12
8.8.8.8
8.8.4.4The Google DNS servers are there and my ISP DNS servers are there (even though I never entered them).
Question: I assume since I have pfBlockerNG installed, those DNS servers aren't being used. Is there a way I can test this?
Question: If someone DIDN'T want to block IP addresses, but just wanted Unbound to avoid DNS providers knowing their browsing habits, could you install pfBlockerNG, and disable the adblocking list?
EDIT: It looks like Unbound is working. I tried this from a computer running fedora:
[XXXXXX@fedora ~]$ drill -T facebook.com . 518400 IN NS a.root-servers.net. . 518400 IN NS b.root-servers.net. . 518400 IN NS c.root-servers.net. . 518400 IN NS d.root-servers.net. . 518400 IN NS e.root-servers.net. . 518400 IN NS f.root-servers.net. . 518400 IN NS g.root-servers.net. . 518400 IN NS h.root-servers.net. . 518400 IN NS i.root-servers.net. . 518400 IN NS j.root-servers.net. . 518400 IN NS k.root-servers.net. . 518400 IN NS l.root-servers.net. . 518400 IN NS m.root-servers.net. com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. facebook.com. 172800 IN NS a.ns.facebook.com. facebook.com. 172800 IN NS b.ns.facebook.com. facebook.com. 172800 IN NS c.ns.facebook.com. facebook.com. 172800 IN NS d.ns.facebook.com. facebook.com. 300 IN A 31.13.71.36 -
Hey there,
I used Pihole with unbound on RaspberryPi for some years, quite happy with it.
Then I got to pfsense and since then, unbound is running on pfsense with pfb_dev. Works so far.So, you might want to think twice about using google dns...why not using unbound for dns queries to the authorative dns servers?
To your question: here all lists are safe, even after upgrades...
-
@the-other I don't want to use Google DNS. I believe that I'm currently using unbound for DNS. Is there something else I should do to verify?
-
@gpinzone Hey,
not using fedora here.
With a
nslookup xyz | grep server my ubuntu shows the actual dns server...my pfsenseI don't know why you have all those other dns server IPs in your system...if you do not use them you can go ahead and delete them.
So, what are your settings under System > General Setup?
Is unbound running under Services > DNS resolver?
Is it running in forwarder mode?
:) -
-
@gpinzone so, in case you do not want to use google as dns you could enter something less curious...or get rid of that and change to use only this server (no fall back to remote) and delete google dns.
Here, no entries under general settings...personal decision. -
@the-other I made two changes. I removed the google DNS servers (I had assumed I couldn't get rid of them both, but I just had to clear out the field of the remaining one.)
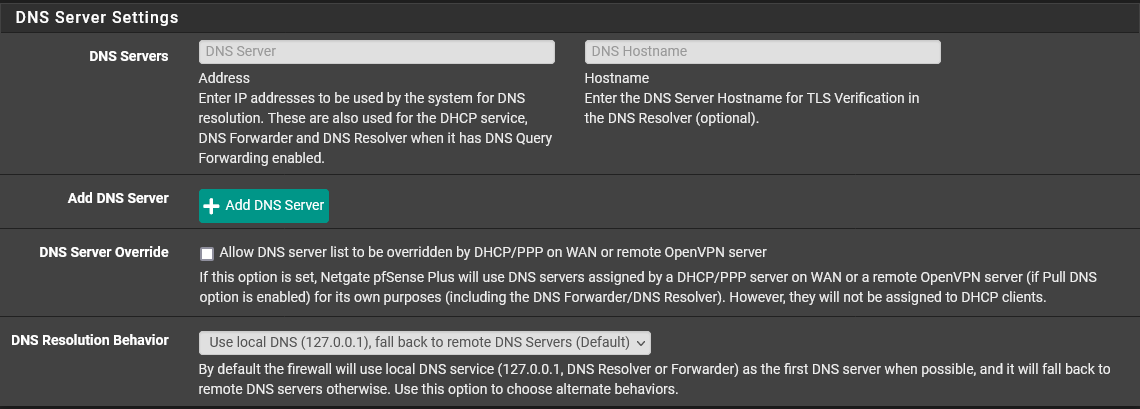
I also unchecked the DNS Server Override option and that got rid of my ISP's DNS servers from appearing on the status page.
DNS server(s) 127.0.0.1
I don't think this changed anything significant since I'm almost positive unbound/pfBlockerNG was supplying the DNS requests even with those entries in place.
-
@gpinzone
Yeah, but now you removed data hungry Google from your setting.
With the right firewall setting, you can make sure everything in your lan uses unbound, no other dns query targets allowed. -
I woke up this morning and I appeared to lose Internet on every device except for a laptop that is connected using a VPN (locally configured on that laptop). I could still ping IP addresses. It appeared to be a system-wide DNS failure. The pfBlockerNG logs showed failures trying to resolve the hostnames to download the blocking information. I restored the checkbox to allow the DNS server list to be overridden by DHCP/PPP on WAN. That didn't seem to make a difference. Perhaps I didn't wait long enough? I rebooted the Netgate 4100 and DNS was restored. I do see the ISP's DNS servers on the status page, but I can verify my LAN isn't using them.
I'm not sure what happened. I assume the DNS cache expired. Without any external DNS servers configured, the system can't bootstrap itself to get unbound working. Am I correct?
-
@gpinzone unbound uses a list of authorative dns servers...
As mentioned, i have no extra entry fordns servers in my system...still working. -
@the-other Thank you. I wonder why I had a failure?
-
@gpinzone
There are known issues when unbound is running and under Services > DNS Resolver are the followin settings active
...DHCP Registration
...no / wrong listening listening interfacesTry search in this forum for "unbound dns fail", during the last few weeks, many users experienced some problems. You might find a solution there.
Are you using IPv6? PfblockerNG_dev? Any firewall rules regarding Port 53 (typically dns)?
-
@the-other
silly me...of course you are using pfblocker...*double facepalm :)Well, do you have under services > DNS Resolver the Python script active?
Also...any restrictions (IP Block outgoing i.e.) so that your dns might not reach the needed servers?As mentioned, problems with unbound and pfblocker_ng are a quite common topic here, so a short search could help...
-
@the-other I'm using the latest development version, not using Python, no IPv6 (my ISP doesn't support it), and I'm not blocking port 53. I know there's a way to redirect all DNS traffic to your DNS server and I have not done that.
I did read something about unbound used by pfBlockerNG isn't the latest. I guess we'll just have to wait.
If it fails again, I assume a complete reboot isn't necessary. I'll see if there's a way just to restart unbound.
-
@gpinzone
Sure there is a way:
First, log on to pfsense
Then go to your status page (it might sho you the status of all services, otherwise check at Status > Services)
There you will see, if unbound is not running...in that case hit Restart Service button and...taDAAA...should restart without rebooting your pfsense in general.
:) -
@the-other Thank you. Added service status to my dashboard.