VLAN on D-link
-
@fireix said in VLAN on D-link:
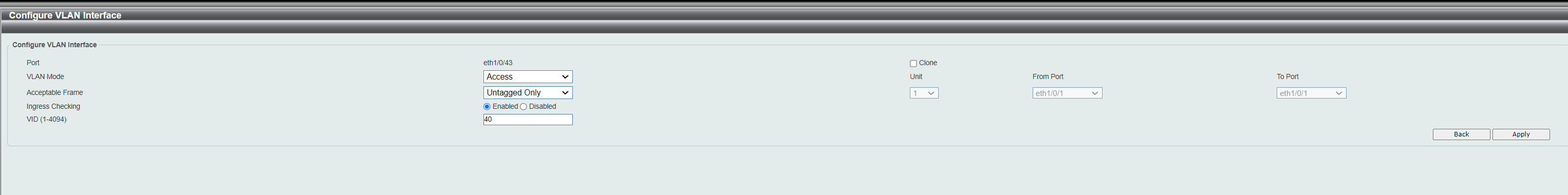
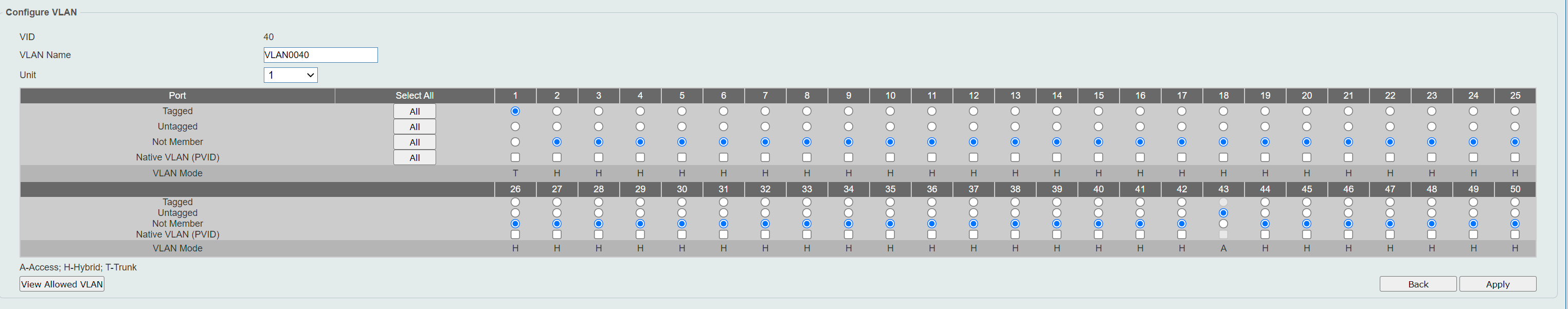
Each time I enable "Untagged member" on the 2nd port I tried (port 43), it removed the VLAN "40" under Tagged VLAN on port 1. So now it looks like this:
Correct because you are now setting this port as that VLAN without a VLAN tag in the ETH packet. This would be expected.
-
@rcoleman-netgate Not sure exactly why that is expected, but do I fix it by adjusting it on the interface afterwards - so that the last screen there looks correct setup?
I have a PC in Port 34 and Port 43, supposed to be in VLAN40 untagged.
pfSense is on Port 1.
No communication with Port 1 at all when member of VLAN40 (I want communication with pfSense...)
-
@fireix On the PF your interface is assigned to the VLAN interface? Mine for comparison:
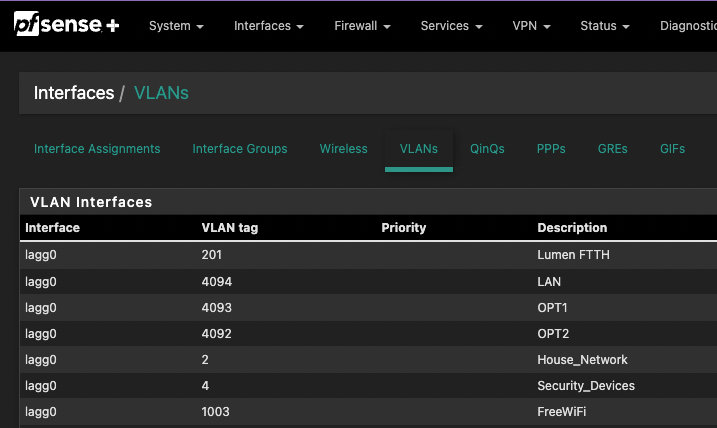
-
@rcoleman-netgate Indeed. Also marked the checkbox to enabled the interface and put firewall-rule in place.
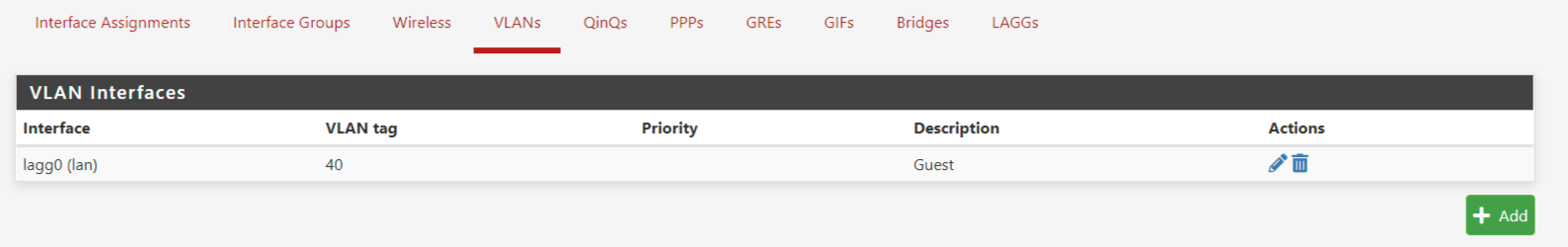
One thing.. I haven't actually defined any VLAN1 on pfSense, as the main mode is non-vlan setup and I don't want to disrupt non-tagged traffic. Could that be the issue? I don't think it should, as I should anyway be able to ping the interfaces IP-address in VLAN40.
-
@fireix Doubtful. VLAN1 = unnumbered, likely your LAN.
Is this a whitebox or one of our devices? What do you see when you run a PCAP on the interface?
-
@rcoleman-netgate said in VLAN on D-link:
PCAP
It is a Supermicro-server with pfSense installed and 4 ports. Haven't really ran an PCAP on it. Do you mean on the entire LAN, is it easy to identify VLAN-id tags in it? I'm only really basic on wireshark-skills, no idea how those packages will look like. I have a ton of non-vlan traffic, so will be a lot of noise.
-
@fireix You can run the PCAP on just the VLAN interface in question.
https://docs.netgate.com/pfsense/en/latest/diagnostics/packetcapture/index.html
-
@fireix said in VLAN on D-link:
I'd do as @rcoleman-netgate says
Try to capture some packets on pfSense , while pinging the pfSense IF.
Both the way where it failed , and the way where you had succeed (Vlan1 ??)Tip: Capture detailed/all , save the file. Then it can be opened in Wireshark.
RE:
But only communication between ports on VLAN40, I can't communicate with Port 1. In my head, it should have been tagged port, but this interface almost looks the oposite of what I find logic... But you are two people saying it looks normal, so I will go with that for now ;)
You could make P1 (or try w P2) a Tagged port.
The only difference as i see it (30 sec glimpse at the Dlink 15xx config example) , is that you can't run Native/untagged data on it.
So you have to TAG Vlan1 data also on the pfSense, aka Tag Vlan1 & Vlan40.This would be my preference anyways (tagged only), i'll always avoid those Hybrid ports when not needed.
UniFI AP's springs to mind , as needs Hybrid ... Well at least in older fw.And i tend to avoid Vlan1 use anywhere in my infrastructure .. Old working habbit.
Btw:
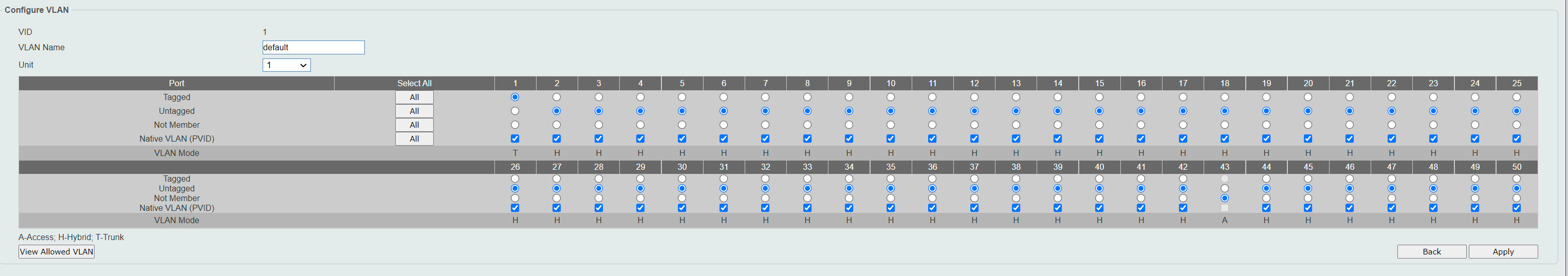
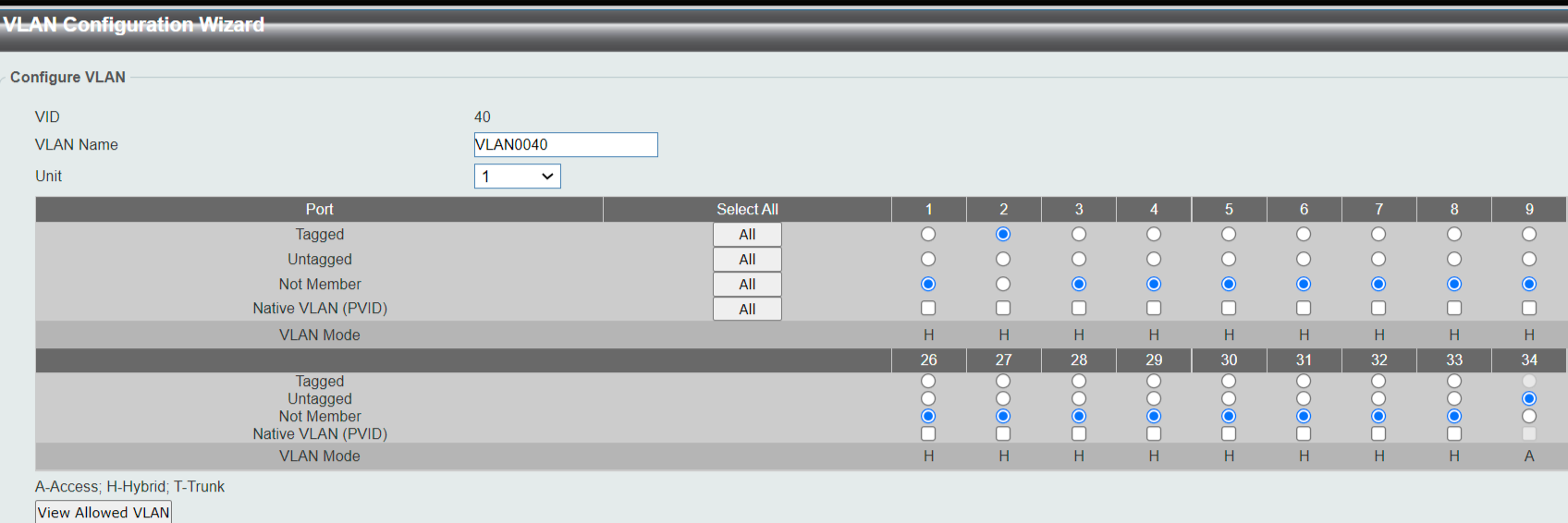
I saw a "View Allowed Vlans Button" on the pict with the Voan40 definition.
Does that give any clue .... Ie. Vlan40 not allowedEdit:
You could also setup a "Monitoring port" on the switch , and connect a PC w. Wireshark to that one.Here's how it's done on a D-Link 1210 , couldn't find anything for a 1510
https://eu.dlink.com/uk/en/support/faq/switches/layer-2-gigabit/dgs-series/es_dgs_1210_como_monitorear_trafico_de_un_puerto_port_mirroring/Bingo
-
@bingo600 said in VLAN on D-link:
I saw a "View Allowed Vlans Button" on the pict with the Voan40 definition.
That's the button I click to get to this screen posten above - to verify the setup:
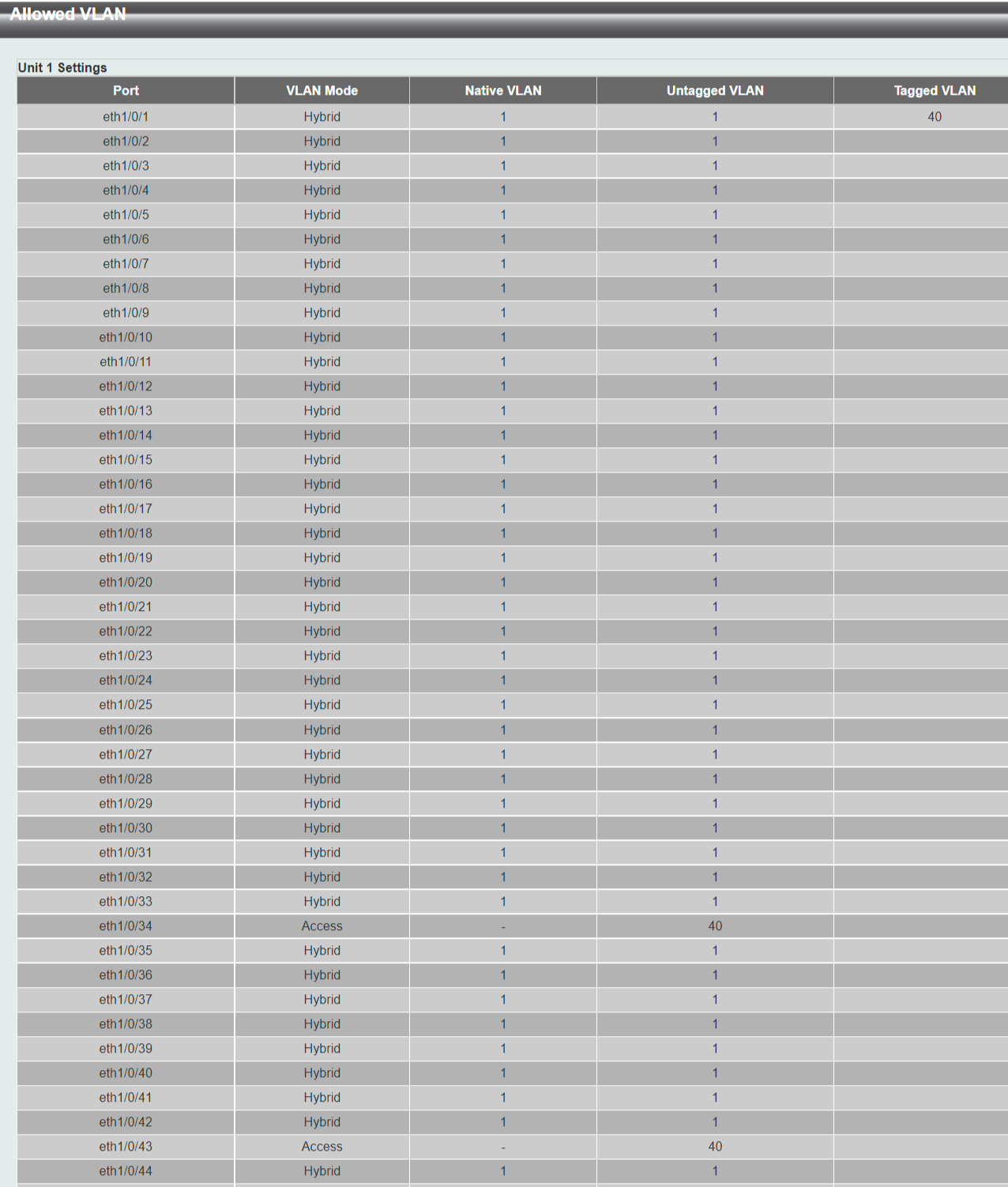
"You could make P1 (or try w P2) a Tagged port."
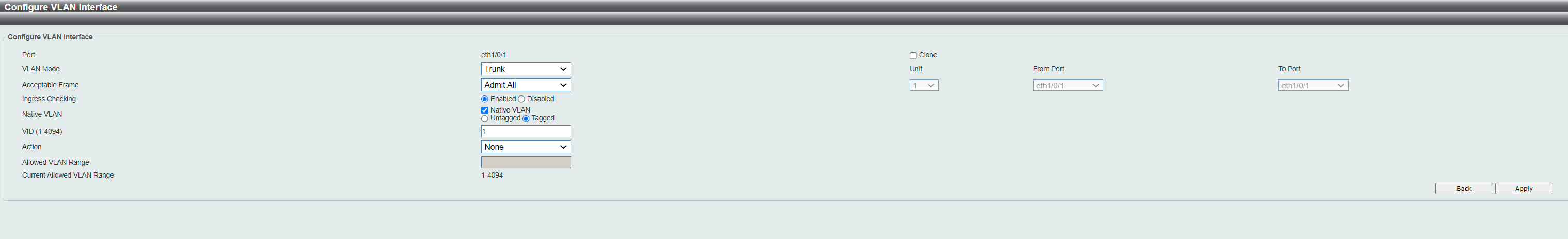
That I have tried for days to do - based on everything I have read, that is the way it is done usually :) Port 1 is the main port to pfSense/Internet and is clearly a "tagged" candidate. But when I edit the VLAN40 and select Port 1 Tagged port in the screen below, it doesn't stick when I click Apply. I tried for port 2 now as you suggested and there it actually sticks/works like I want Port 1 to do. Now, if I just managed to do that with Port 1, I think it would work rigth away :)
I can't see any clear difference on port 1 vs port 2.. they are both Hybrid and both part of VLAN1 (or by default at least). But maybe this gives an important clue... Btw, after I added the Port 2, it automatically did this under Allowed VLAN-page, so config looks similar to Port 1:

Btw: I tried to remove the checkbox for "Native VLAN" on the port 1 (and 2, 3, 4) on the ports inside VLAN1, but it wouldn't stick either. Neither from the port-membership-overview page or the interface for each port. On the port-mebership-overview for VLAN40, I could remove the checkbox for all ports and that is how it is now.
Tagged VLAN40 disappeared from the Allowed VLAN on port 1 when I play around a bit. I have to re-add it manually on the VLAN interface port 1 every timeI do a small edit. I think forcing it doesn't work, it does however sticks on Port 2 as it should no matter what. So that tells me that D-Link doesn't allow it, it will be removed by the system. So even if it looks good on that last picture above, it is probably not respecting the VLAN40-tagged on Port 1.
-
@rcoleman-netgate said in VLAN on D-link:
@fireix You can run the PCAP on just the VLAN interface in question.
https://docs.netgate.com/pfsense/en/latest/diagnostics/packetcapture/index.html
Ah, it is built-into the GUI, nice :)
I ran it both in "Enable promiscuous mode" and without. Tried to ping both from the machine I have setup on VLAN40 (with static IP in DHCP-range) and from pfSense. The data below is from pfSense (I pinged machine 192.168.50.15 with no reply)
12:05:26.303035 ARP, Request who-has 192.168.50.15 tell 192.168.50.1, length 28
12:05:27.303720 ARP, Request who-has 192.168.50.15 tell 192.168.50.1, length 28I think it is is purly a config error in D-Link, port 1 is simply not "connected" on VLAN40 internally.
-
@bingo600 said in VLAN on D-link:
You could make P1 (or try w P2) a Tagged port.
The only difference as i see it (30 sec glimpse at the Dlink 15xx config example) , is that you can't run Native/untagged data on it.T
So you have to TAG Vlan1 data also on the pfSense, aka Tag Vlan1 & Vlan40.Sorry i meant Trunk port above , where i wrote Tagged.
Try to set P2 as Trunk , allowing VL40Something is is spookey with that switch or FW ....
Try to capture on interface , not Vlan40 , that way you should be able to see if it is tagging packets with VL40.
I agree with that D-Link port , not tagging VL40 packets.
We miss a "little important thing" ..... I have no idea what ....
But you might be right in , when the "D-Link gui removes the VL40 tagging" , it might be a hint ....Strange ... It's so easy on a D-Link 1210
I just had another glance at this
https://eu.dlink.com/uk/en/support/faq/switches/layer-2-gigabit/dgs-series/es_dgs_1510_escenario_config_vlan_por_gui_y_cliStrange ... It seems to use a totally different way to GUI configure the ports.
You did say you had success in adding the VL40 tag to P2 , did you try to connect the pfS to that port ??
/Bingo
-
I tried the console on the switch, run the command "show vla" to list all VLANs.
It reports this:
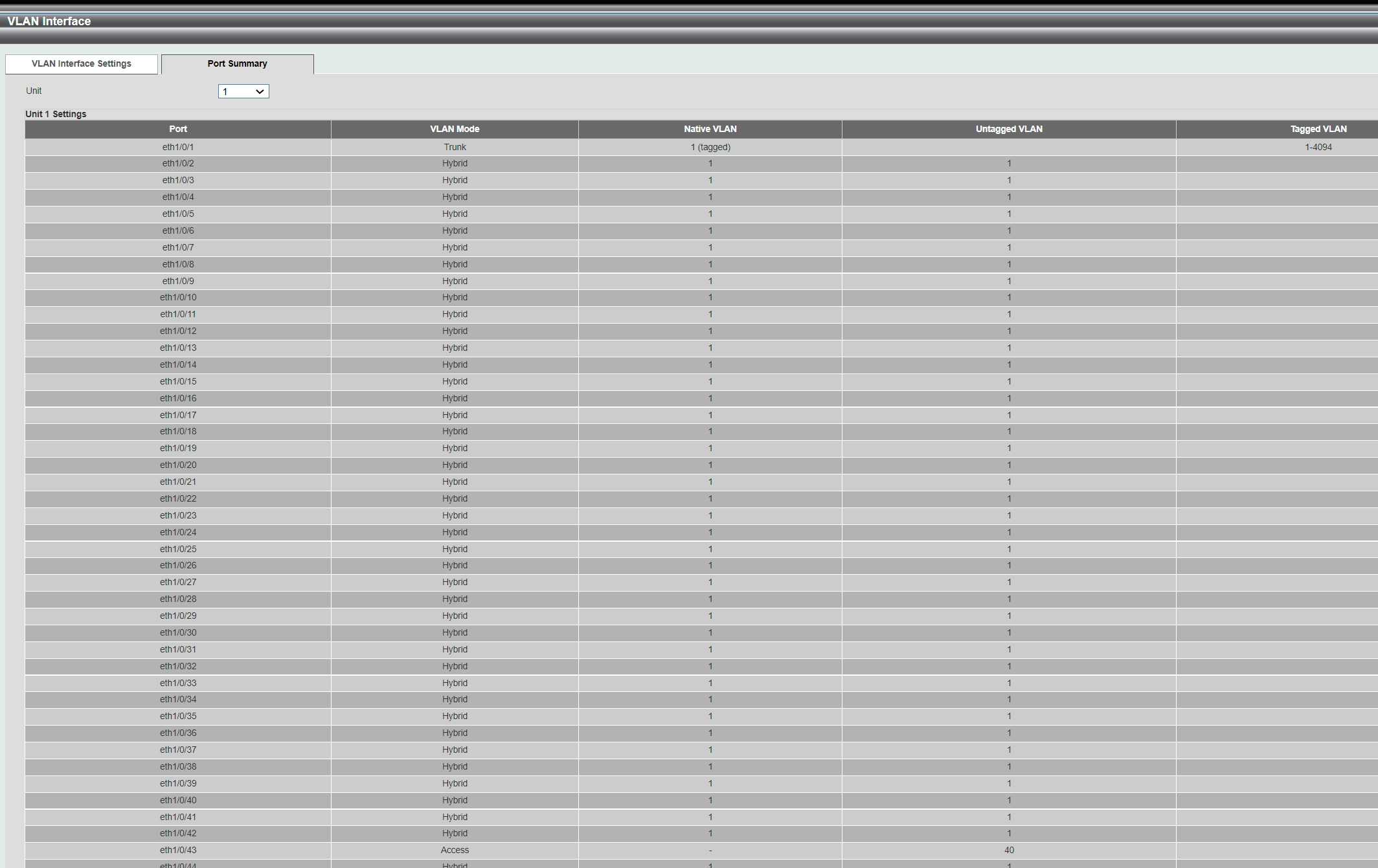
VLAN 1 Name : default Description : Tagged Member Ports : Untagged Member Ports : eth1/0/1-1/0/33,eth1/0/35-1/0/42,eth1/0/44-1/0/50, eth2/0/1-2/0/50,eth3/0/1-3/0/50,eth4/0/1-4/0/50 VLAN 40 Name : VLAN0040 Description : Tagged Member Ports : eth1/0/2 Untagged Member Ports : eth1/0/34,eth1/0/43 Total Entries : 2 -
That seems like it has accepted VL40 tagged on P2
Try to Connect the pFS IF to port2Do you have a 4-Unit Stack ??
What port is your Management PC connected to ?
Sometimes the port where the PC is connected behaves weird , if you want to "kill" the Vlan you're actually Managing via, -
Two units stack. The interface is showing 4 even if you have 2,3 or 4..
Indeed, Port 2 works just like I want both in the GUI and in the console.
I wish I could just switch it over :) But then I take down all customers while testing, so want to try to avoid it.
Maybe a way to copy all traffic on Port 1 to Port 2.. port mirror?
-
@fireix
Have to leave ... Wife is home
BB in 3..4 hours -
@bingo600 Hmm....
On my pfSense LAN, I have LACP-lag that goes to Port 1 on Switch 1 and Port 48 on Switch 2. I didn't think this mattered, but this migth be the cause.
I tried to put port 48 on Switch #2 into tagged-mode. Same symptom: The interface shows it is possible for this port to join VLAN40, but once I choose it and Submit, it is removed. When I did the same on the empty port 47 next to it, it sticked and worked like it should. Either I'm not allowed to put tagged on a live-port that is plugged in - or the switch refuse to put a port in LAG into tagged mode.
I see from a FAQ that VLAN-settings should be set to same on both individual ports that are member of the team, but how can I do that when D-link automatically removes the configuration before I can set it on 2nd unit..
Port definition is exactly the same for port 47 and 48 (like 1 and 2), so I can't see any other reason.
Edit: Using the "Clone port" option I was able to transfer the settings on Port 1 SW1 to port 48 SW2. But no such option for VLAN-membership.
-
I tested tagging port #2 in a VLAN and then let it join in a LACP-bond/channel.. Boom, it removed the tagging setting on port #2.
-
I disabled all LAG/team links and connected pfSense to fresh port #3. As you see. port 3 on VLAN60 is tagged as it should.
The computer in port 34 on VLAN60 is Access port.
No contact between pfSense and the computer on VLAN60.
VLAN 1 Name : default Description : Tagged Member Ports : Untagged Member Ports : eth1/0/1-1/0/33,eth1/0/35-1/0/42,eth1/0/44-1/0/50, eth2/0/1-2/0/50,eth3/0/1-3/0/50,eth4/0/1-4/0/50 VLAN 40 Name : VLAN0040 Description : Tagged Member Ports : eth1/0/2,eth1/0/46,eth2/0/47 Untagged Member Ports : eth1/0/43,eth2/0/46 VLAN 60 Name : VLAN0060 Description : Tagged Member Ports : eth1/0/3 Untagged Member Ports : eth1/0/34 -
I have a computer where I can set the VLAN ID on and I put it to 70 on pfSenses LAN port. I got on to correct VLAN and got DHCP for VLAN70 rigth away. So error is 100% in the switch. No idea what more to try.. No way to get the VLAN tag passed through port 3 to any port no matter what I do.
Port 3 shows tagged VLANs 60,70.
-
By defining an IP under meny for Layer 3 LAN interfaces on the switch with an IP in the DHCP-range, I suddenly managed to ping my pfSense (and all other networks). I could however ping everything on the pfSense. Is it supposed to work like that? Seems like I can block it under firewall rules.
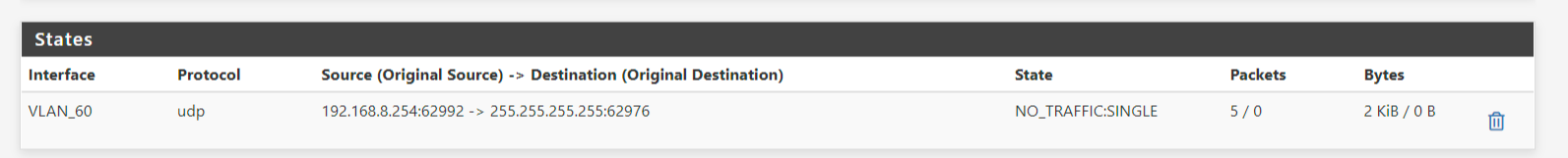
This I found on the pfSense (it is the switch interface address on VLAN60 that has sent out UDP packets).
Still no DHCP though.. Doesn't get assigned.