VLAN on D-link
-
Two units stack. The interface is showing 4 even if you have 2,3 or 4..
Indeed, Port 2 works just like I want both in the GUI and in the console.
I wish I could just switch it over :) But then I take down all customers while testing, so want to try to avoid it.
Maybe a way to copy all traffic on Port 1 to Port 2.. port mirror?
-
@fireix
Have to leave ... Wife is home
BB in 3..4 hours -
@bingo600 Hmm....
On my pfSense LAN, I have LACP-lag that goes to Port 1 on Switch 1 and Port 48 on Switch 2. I didn't think this mattered, but this migth be the cause.
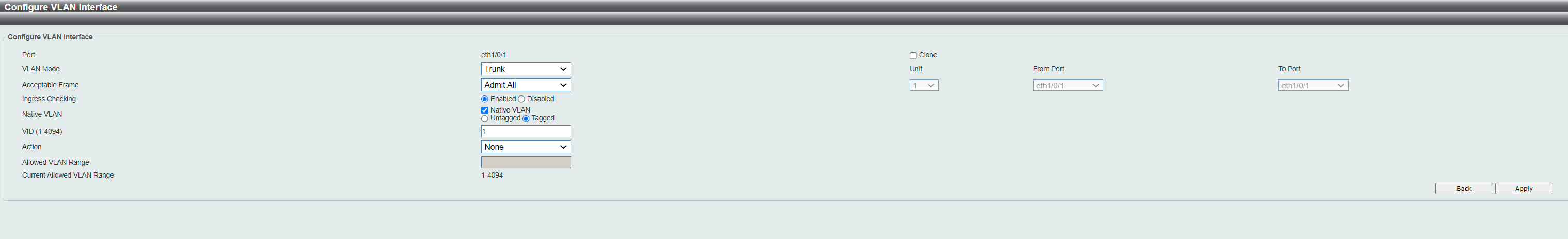
I tried to put port 48 on Switch #2 into tagged-mode. Same symptom: The interface shows it is possible for this port to join VLAN40, but once I choose it and Submit, it is removed. When I did the same on the empty port 47 next to it, it sticked and worked like it should. Either I'm not allowed to put tagged on a live-port that is plugged in - or the switch refuse to put a port in LAG into tagged mode.
I see from a FAQ that VLAN-settings should be set to same on both individual ports that are member of the team, but how can I do that when D-link automatically removes the configuration before I can set it on 2nd unit..
Port definition is exactly the same for port 47 and 48 (like 1 and 2), so I can't see any other reason.
Edit: Using the "Clone port" option I was able to transfer the settings on Port 1 SW1 to port 48 SW2. But no such option for VLAN-membership.
-
I tested tagging port #2 in a VLAN and then let it join in a LACP-bond/channel.. Boom, it removed the tagging setting on port #2.
-
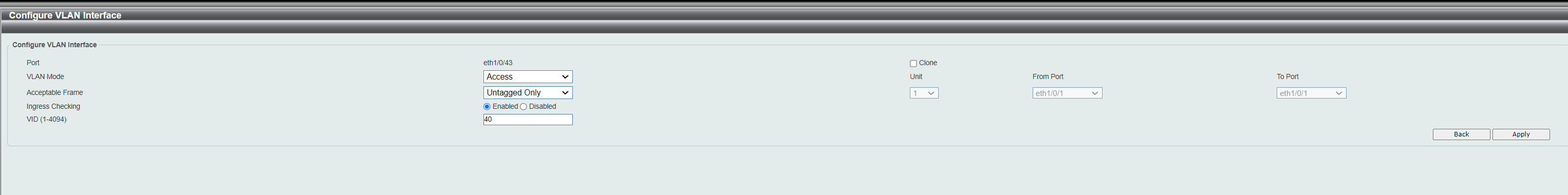
I disabled all LAG/team links and connected pfSense to fresh port #3. As you see. port 3 on VLAN60 is tagged as it should.
The computer in port 34 on VLAN60 is Access port.
No contact between pfSense and the computer on VLAN60.
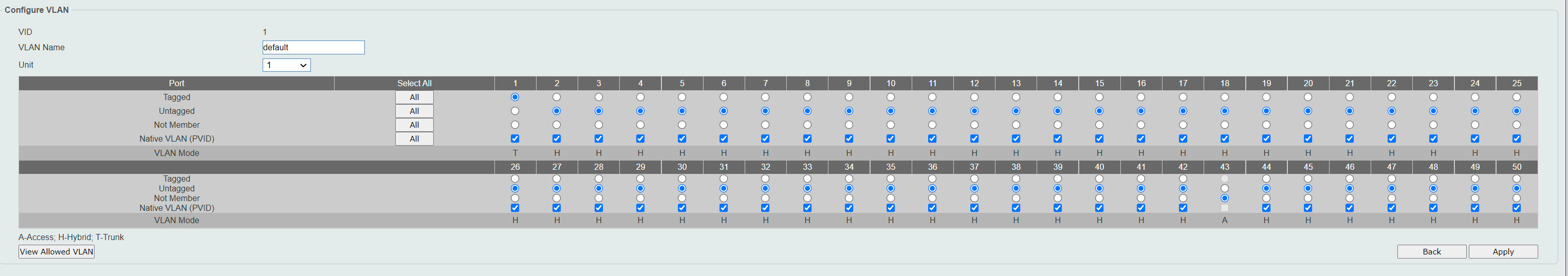
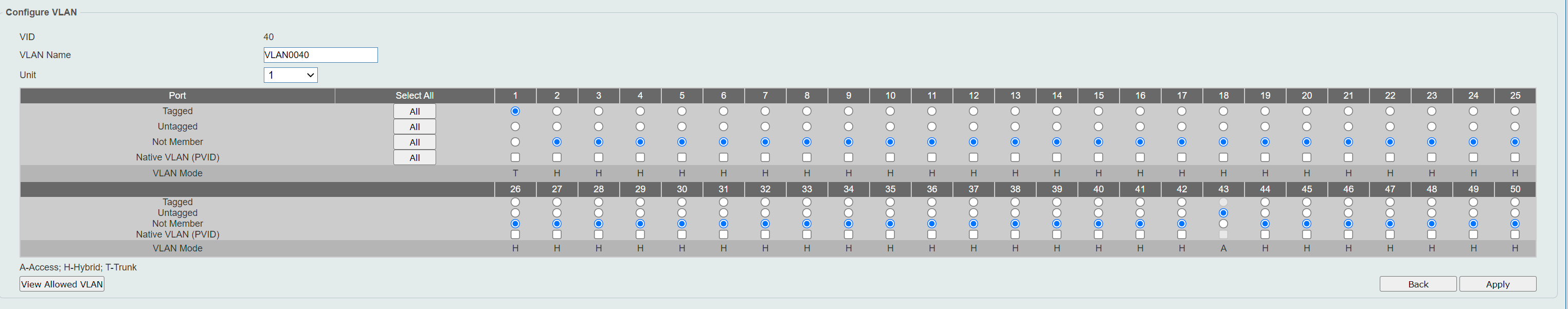
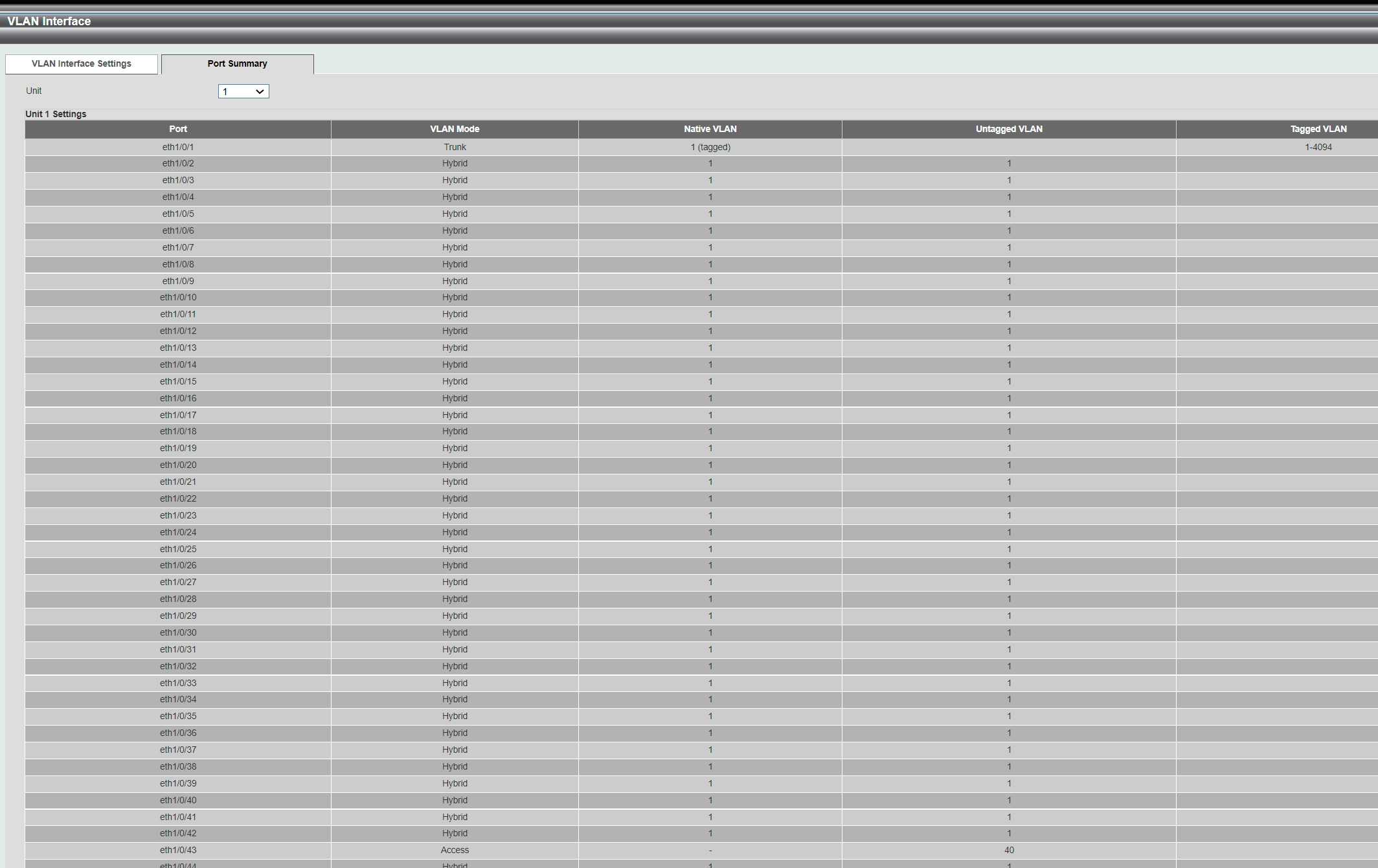
VLAN 1 Name : default Description : Tagged Member Ports : Untagged Member Ports : eth1/0/1-1/0/33,eth1/0/35-1/0/42,eth1/0/44-1/0/50, eth2/0/1-2/0/50,eth3/0/1-3/0/50,eth4/0/1-4/0/50 VLAN 40 Name : VLAN0040 Description : Tagged Member Ports : eth1/0/2,eth1/0/46,eth2/0/47 Untagged Member Ports : eth1/0/43,eth2/0/46 VLAN 60 Name : VLAN0060 Description : Tagged Member Ports : eth1/0/3 Untagged Member Ports : eth1/0/34 -
I have a computer where I can set the VLAN ID on and I put it to 70 on pfSenses LAN port. I got on to correct VLAN and got DHCP for VLAN70 rigth away. So error is 100% in the switch. No idea what more to try.. No way to get the VLAN tag passed through port 3 to any port no matter what I do.
Port 3 shows tagged VLANs 60,70.
-
By defining an IP under meny for Layer 3 LAN interfaces on the switch with an IP in the DHCP-range, I suddenly managed to ping my pfSense (and all other networks). I could however ping everything on the pfSense. Is it supposed to work like that? Seems like I can block it under firewall rules.
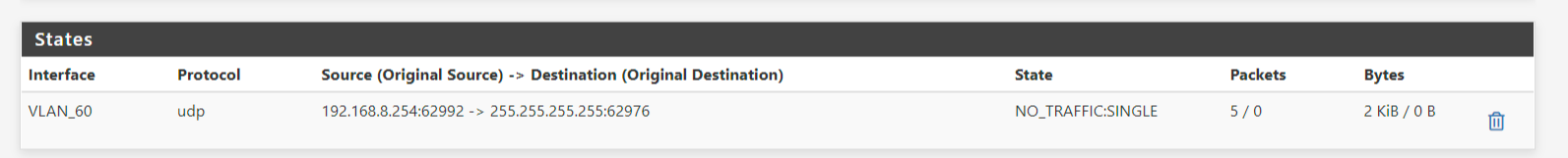
This I found on the pfSense (it is the switch interface address on VLAN60 that has sent out UDP packets).
Still no DHCP though.. Doesn't get assigned.
-
And suddenly I have DHCP also!
Now just have to see that the VLAN seperation actually works, I can ping most stuff, by I assume it all goes through the pfSense and not port-to-port now and then I can at least filter out all traffic I want :)
-
Nice that you are making progress.

But watch out on enabling L3 on the switch , if done "incorrectly" you could easily bypass the pfSense fwall , and route packets between vlans directly on the switch.
-
@bingo600 Do you see any error in the "show vla" command on the console of the switch above? Not sure why it doesn't work without layer 3. Would be so much easier to avoid it, but I get no outside VLAN60 communication whatever I do.
One problem I discovered after enabling layer 3 and still not seeing DHCP, was that the switch had enabled DHCP-protection on most of the ports. Probably done years ago... So that was important discovery at least.
I see that I can control through firewall-rules on pfSense where VLAN60 can go. If I have a server in VLAN1, I can have a rule that by default block all traffic from VLAN60 to not go to servers inside VLAN1. That is a big positive. Doesn't this indicate that correct setup? Or do you think that if I create a layer3 IP on switch for VLAN40, it will allow traffic between VLAN40 and VLAN60 without going through the firewall?
-
@fireix said in VLAN on D-link:
@bingo600 Do you see any error in the "show vla" command on the console of the switch above? Not sure why it doesn't work without layer 3. Would be so much easier to avoid it, but I get no outside VLAN60 communication whatever I do.
I see no immediate errors in the config except i'm not sure what switchport you have connected to the pfSense (or was that P3)
The port connected to the pfSense , should have both VL40 & VL60 as tagged.
If you want the switch to forward packets for both VL40 & 60 down that interface.And offcause you must match the pfSense end , and have both VL 40 & 60 defined on that interface port too.
One problem I discovered after enabling layer 3 and still not seeing DHCP, was that the switch had enabled DHCP-protection on most of the ports. Probably done years ago... So that was important discovery at least.
DHCP Snooping is a usefull feature if setup correctly.
I see that I can control through firewall-rules on pfSense where VLAN60 can go. If I have a server in VLAN1, I can have a rule that by default block all traffic from VLAN60 to not go to servers inside VLAN1. That is a big positive. Doesn't this indicate that correct setup? Or do you think that if I create a layer3 IP on switch for VLAN40, it will allow traffic between VLAN40 and VLAN60 without going through the firewall?
I would expect the switch might be "kind enough" to interroute packages between the vlans with an ip interface.
I can't (wont) say anything with certainty , as this is super switch/firmware dependant , and as i said. I have not even seen a 15xx switch.
-
@bingo600 I ended up putting the pfSense LAN to Port #3 to have a fresh port/start.
VLAN60: Based on the show vla, all traffic arriving on Port 3 is defined as Tagged, so the switch should in theory forward any 60-traffic to Untagged-port at Port 34 and all other access-ports (untagged ports) in VLAN60? At least good to verify that in theory that is how it is supposed to work. If there is an error, I suspect it is on the Port 3 as there is many options for it under VLAN1 at least. With "native VLAN" and how these options can be set, it is hard to know exactly.
I feel it looks a bit weird to me to have all ports in vlan1 untagged. Doesn't this remove the VLAN-tag from the traffic in port 3? Or it is normal, since VLAN60 have port 3 tagged, it should still work.
"I would expect the switch might be "kind enough" to interroute packages between the vlans with an ip interface."
That's what I fear... At least it doesn't for now between VLAN1 and VLAN60, but maybe it will happen with the next VLANs I create with similar config..
-
@fireix said in VLAN on D-link:
@bingo600 I ended up putting the pfSense LAN to Port #3 to have a fresh port/start.
VLAN60: Based on the show vla, all traffic arriving on Port 3 is defined as Tagged, so the switch should in theory forward any 60-traffic to Untagged-port at Port 34 and all other access-ports (untagged ports) in VLAN60?
Correct Vlan60 data should be sent/received tagged on P3 , and also be copied to all untagged port members of VL60.
All untagged traffic sent/received on P3 would (in the switch) belong to Vlan1.What happened to Vlan40 ???
You haven't tagged VL40 one on P3 (the connection from switch to pfSense)At least good to verify that in theory that is how it is supposed to work. If there is an error, I suspect it is on the Port 3 as there is many options for it under VLAN1 at least. With "native VLAN" and how these options can be set, it is hard to know exactly.
Native vlan is a way to tell the switch what Vlan "Untagged packages" belong , on a port that that has no "Untagged Vlan" defined. Ie. a port that only has tagged vlans defined.
If "The other end" decides to send packages untagged to that port , the switch now know what vlan to put those packages in.I have a "Dummy VlanXX" just for native vlan purposes , all my "Pure tagged Vlan switchports" have their native vlan set to XX.
No switch ports are Tagged or Untagged members of that Vlan XX , effectively making it a "Garbage or /dev/null" vlan , where nothing listens , and packages just "die"."I would expect the switch might be "kind enough" to interroute packages between the vlans with an ip interface."
That's what I fear... At least it doesn't for now between VLAN1 and VLAN60, but maybe it will happen with the next VLANs I create with similar config..
I feel it looks a bit weird to me to have all ports in vlan1 untagged. Doesn't this remove the VLAN-tag from the traffic in port 3? Or it is normal, since VLAN60 have port 3 tagged, it should still work.
The untagged definition only affect packaged wo a Vlan tag , VL60 on P3 is defined as tagged , and would not be affected.
But having (almost) all ports untagged menbers of Vlan1 , enables devices in all member ports , to send untagged data like from a normal netcard setup, to eachother.
Well you're the boss , the switch just does as told. -
@bingo600 All servers (on non-vlan/vlan1) fell down once I connected the pfSense to port 2/LAN40 like I had prepared for yesterday. Port 2 was tagged on VLAN40 and port 34 untagged. But total block of all traffic from start. So now the VLAN40 is broken/not-used. Will fix once I'm good with VLAN60, so I can see how traffic goes (or hopefully not goes) between VLAN60 and VLAN40 on the switch.
Ended up resetting everything and using Port 3 instead with fresh vlan-setup.. somehow what seems to be the same setup now works (kind of). I think it changes if you define a port as access-port vs doing it as hybrid and untags it. In theory, it should be similar, but..
-
This post is deleted! -
@bingo600 Thanks for all the help :)
For some reason, once I configured VLAN40 just like VLAN60 now - even without adding the interface ip on Layer #3 on the switch, VLAN40 works. I have no idea how come. But I have tested in details and I can't get to any IP on VLAN40 just like I would hope for (from VLAN60). And DHCP works just great on both VLANs.
I have public IP on the LAN-network and private IPs in the VLAN. This worked just great to do NAT from public static IP to this VLAN IP. Just wonder if there is a simple way to just assign a public IP on the VLAN-side somehow. Since it works on the LAN, I suspect it is just come configuration needed to be able to re-use that public IP (on LAN) also on the VLAN-side. But no idea how.. any ideas? I can use it like it is now, the private IP gets the public static Ip externally, but just a bit administration.
-
I dont think i understand the public ip on the lan part ??
-
@fireix said in VLAN on D-link:
just assign a public IP on the VLAN-side somehow
You can use whatever IP range you want on your local network, rfc1918 or public. But public isn't going to work unless the range is actually routed to you. And just pulling some public IP range out of thin air and natting it to some other public IP is pointless, and could quite likely cause you issues when you can't actually get to the public site that actually owns/uses that IP space
Do you have public space routed to you.. If so you can subnet that out to whatever you want for your local segments as long as you have a large enough cidr routed to you.
-
@johnpoz It is public /24 on the LAN side - my ISP has assigned me transport net /29 on WAN side and also assigned me the /24 I use on the LAN. I have them on my LAN and all of them are reachable on Internet (with NAT).
I can't divide them up in smaller subnets as I have customers using random IPs in the hole /24 range with static settings of mask/gw and so on. To much work to take offline or change them all as IPs are used deep into their applications and it works just fine, it is more like from a better isolation perspective I want this.
Some customers I could have moved on to new settings, but I understand I have to move everyone into different smaller ranges (changing it on their servers) at the same time and can't take just a few of them at a time based on what I'm told.
Since I'm able to "route" the public statics IPs to both private (NAT) and public IPs on my LAN-side (both using the public IP directly on server AND nat to private IPs), it should be possible into the VLAN-side also. But my question is how :) I assume my explanation so far rule out subnetting.
-
@fireix said in VLAN on D-link:
my ISP has assigned me transport net /29 on WAN side and also assigned me the /24 I use on the LAN
Sure that is fine, but you can just break that /24 up in say /29 or /28 or whatever you need for your other segments. Or you could get them to assign you more space routed via your /29
But sure you could assign the IPs from your /29 as vips and nat your other rfc1918 segments to those IPs