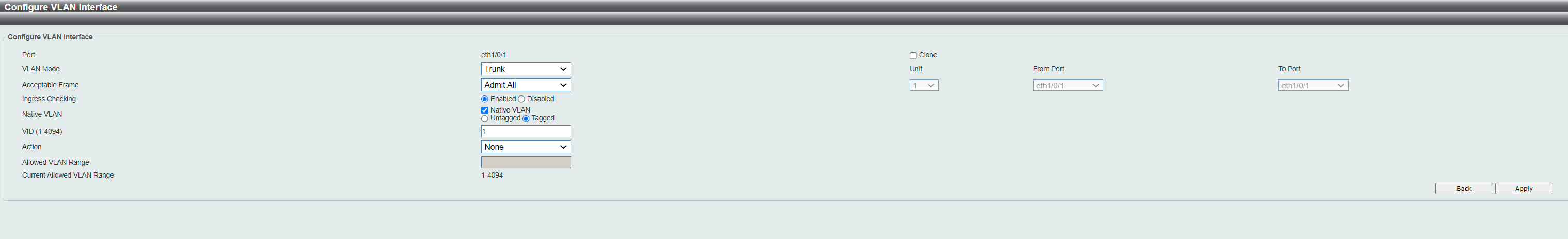
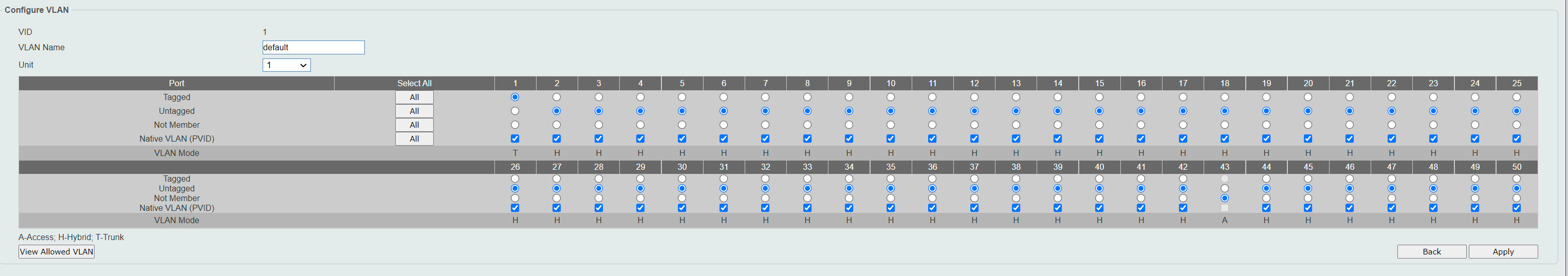
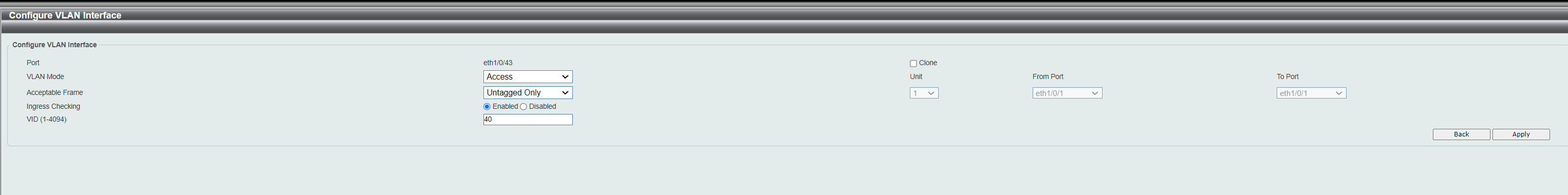
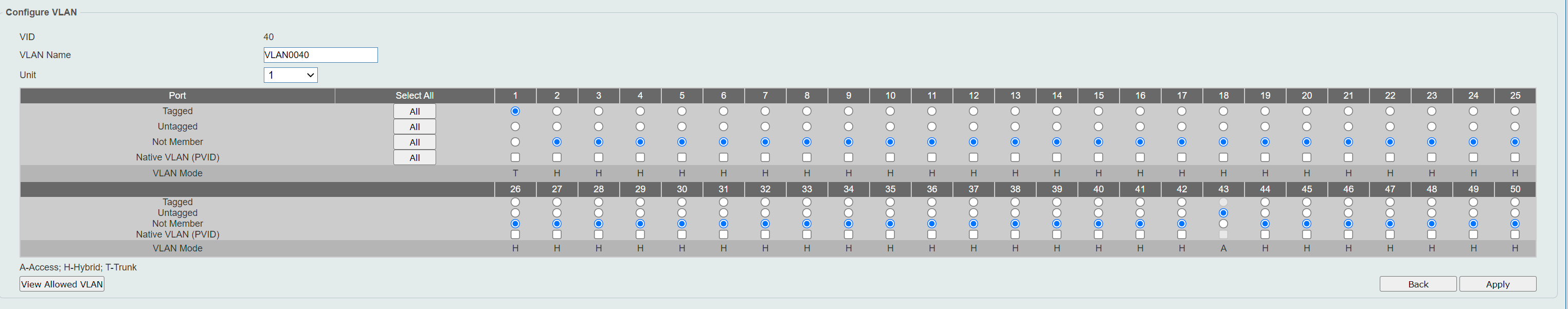
VLAN on D-link
-
@johnpoz Not so much how to subnet, more practical on how to implement it. The reason for doing subnetting (in my head), is to group some customers into their own "network". Bit due to security and bit because customers of data centers (all the ones I have been customer of) are used to beeing handed out a small or big public IP subnet to their customer. Customer can just plug in their server, assign it a public static IP in the range I have set up to them and be online in a minute without having to use private IPs. And less risk that they by accident take an IP I already use - less broadcasting inside a /28 than a /24. I use like 70 IPs out of 256 today, but not super heavy traffic here.
Now, I understand the theory of subnetting (subnet-calculators can help me divide to find the allowed IPs and broadcast domains), but how it is implemented in pfSense is my biggest question. How to you set up the subnets when only one subnet is allowed on the pfSense LAN side?
I'm missing something fundamently. Since I have been struggeling with VLANs, and finally know how to set them up, I do see that I can create an interface for the VLAN and I can enter private IP-range there just like on the LAN-interface. So I think somewhat of a solution is to enter the public static IP-ranges (for instance /28s). But then I need to first remove the /24 and then add each subnet again - to each vlan. This way, no overlapping and I will both have subnetting and more isolated traffic.
However: Is there a way to add interfaces (like several subnets) to the pfSense LAN (remove the /24 assignment first) WITHOUT using vlans and interfaces from there is basically something I wonder I think.. Without introducing seperate router/extra switches. Having a seperate VLAN for each customer I suspect will be hard to manage in the GUI after a while.
-
@fireix said in VLAN on D-link:
How to you set up the subnets when only one subnet is allowed on the pfSense LAN side?
Huh, who says only 1 subnet is allowed on the lan side.. I have 8 different networks on the lan side all using different address space. Currently they are all /24 but that has nothing do with anything they could be /22s they could be /29s, etc.
How many networks are you wanting to created - a /24 isn't going to support many customers if you break those up into /28s
-
@johnpoz 8? That's child's play... my new network has 15.
Of course 5 of them are for testing pfSense releases...
-
@rcoleman-netgate hhehee but I thinks his point it might be cumbersome to manage 2000 some networks off of pfsense.. Yeah it would, not really something I would think you would be doing ;)
Out of your 24 you could create 16 /28s - that should be easy enough to manage, or even /29s wouldn't be something you couldn't do pretty easy.
But yeah you start getting into the 100s of interfaces it might be a bit cumbersome
-
@johnpoz Hmm.. maybe I was thinking it was more complicated ;) I was thinking it was special since I have public static IPs on the non-wan side of the firewall and stuff, but maybe not..
But what would you choose on the LAN-interface from start? Would I just choose one random subnet of the (for instance) /28s out of all I want and then just start using the rest on servers?
I set up at /28 (for example) on the VIP (lan), one for each subnet - or isn't that needed either - to use as gw for each subnet?
-
@fireix said in VLAN on D-link:
) on the VIP (lan), one for each subnet
What? VIP?
Why would you do vips? This isn't difficult, using public behind pfsense is just as using rfc1918, you just don't nat it.. Its that simple.
-
@johnpoz So no setup at pfSense at all except firewall rules?
-
@fireix you have to setup the interfaces or vlan on an interface. But there is nothing special to do other than disable the nat..
The only difference in running 192.168.0/24 vs 42.15.16.0/28 for example would be you don't nat that network to some public interface, because the whole 42.15.16/24 is routed to you.
So there is not port forwarding required, etc. Just firewall rules that you allow or block traffic with.
-
@johnpoz That sounds great :) But when you say "interfaces"... Can I put more than one network on one interface - assume I have one LAN-port on my pfSense. I suspect not. Now I have the entire /24 on LAN-port. So let say I have one port for WAN and one for LAN.
I don't get it ;)
-
@fireix they are called vlans - the exact subject of your thread.. Yes you can put more than one network on a physical interface - via vlans!
-
@johnpoz So what I suggested before was the solution.. Your answer that it was possible with more than 1 subnet per LAN made me believe there was another way WITHOUT VLAN. But of course you meant LAN as a collective thing (with vlans) and not spesific the single LAN-interface. So the way to go is like I suggested here:
Since I have been struggeling with VLANs, and finally know how to set them up, I do see that I can create an interface for the VLAN and I can enter private IP-range there just like on the LAN-interface. So I think somewhat of a solution is to enter the public static IP-ranges (for instance /28s). But then I need to first remove the /24 and then add each subnet again - to each vlan. This way, no overlapping and I will both have subnetting and more isolated traffic.
-
@fireix said in VLAN on D-link:
This way, no overlapping
FWIW pf will not let you do overlapping subnets so that doesn't matter so much. You can migrate your networks over to a new /28 individually as long as it is contained in a different /24 than your other interfaces.
-
This post is deleted!