VLAN suddenly stopped working
-
Thank you for thinking with me.
I connected my Pfsense machine directly to the switch and every port of the switch has been configured like this :
Trunk port / all VLANs allowed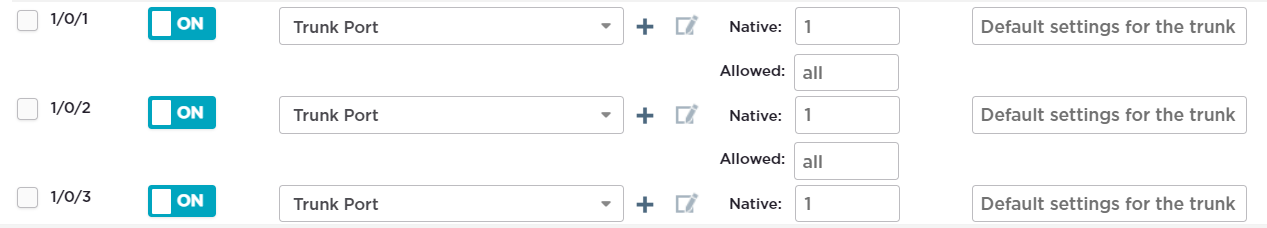
If i change "Native" to 2 of a port connected to my laptop , then i get a IP-address from Pfsense which belongs to VLan 2, if i change it back to 1, then i get an IP-address which belongs to teh private LAN, VLAN1
-
@brian-smit Show me vlan 2 in the switch.
Should be a place to add vlans, you should have vlan 1 and 2 at least.
Why would you allow all vlans on all ports?
Isn't the point of this to separate the guest from the internal?? -
I did it as a test , and it honestly worked like this , where it says "Allowed all" , i can change it to 1,2
-
yes: if you connect to the Guest Wlan , it will use Vlan2 , if you connect to the Private WLAN, it will use Vlan1.
-
@brian-smit Are you connected to pfSense on one interface or two?
If one, layer 2 traffic would never get to the router. If you allow all vlans on every port, you're not separating the networks.
Assuming a trunk port to pfSense (since you didn't answer that), set the trunk to native 1, tagged 2.
Set the port that connects to the guest AP to untagged 2 only.
Set all other ports to 1 only -
@brian-smit said in VLAN suddenly stopped working:
yes: if you connect to the Guest Wlan , it will use Vlan2 , if you connect to the Private WLAN, it will use Vlan1.
How can you say that?? Are the AP's dhcp? If both vlans are going to it, what's to stop it from getting a vlan 1 IP address?
-
yes, this is configured inside the AP , a connecting to the Private SSID sents you to Vlan1, connecting to the guest SSID sents you to Vlan2
-
@brian-smit Ok, so you need a trunk going to the AP as well. Same as pfSense port, native 1, tagged 2.
-
Yes indeed, i will change the settings tomorrow and keep you informed !
Thank you for the help!
-
@brian-smit From the manual: "802.1Q VLAN Trunk Ports for APs
The trunk ports are the ones through which Aerohive APs connect to the wired network. They support 802.1Q tagging and must allow all the VLANs to which the APs assign user traffic, the management VLAN for the APs, and the native (untagged) VLAN. "
You can find more here: https://docs.aerohive.com/330000/docs/guides/Aerohive-Switch-Deployment-Essentials.pdf under "Configuring a Network Policy" section. -
Thank You ! I will go through the steps tomorrow. A small change has been made and that had big consequences (and i am overseeing it)
-
is there someone maybe with tips where to find the problem ?
I wonder if (DHCP) requests are being received by PFsense
-
@brian-smit Did you tag the vlan on the correct port? Do you have the correct vlan untagged on the ports you need?
Post pictures of pfSense and switch configs
-
@jarhead said in VLAN suddenly stopped working:
Did you tag the vlan on the correct port? Do you have the correct vlan untagged on the ports you need?
Yes - i double checked this.
Pictures of my PFsense config:
Interface Assignments:
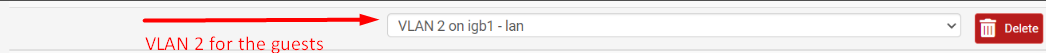
Interfaces - VLANs:
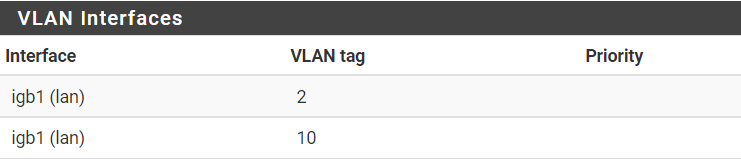
Interfaces - Guests (igb1.2)
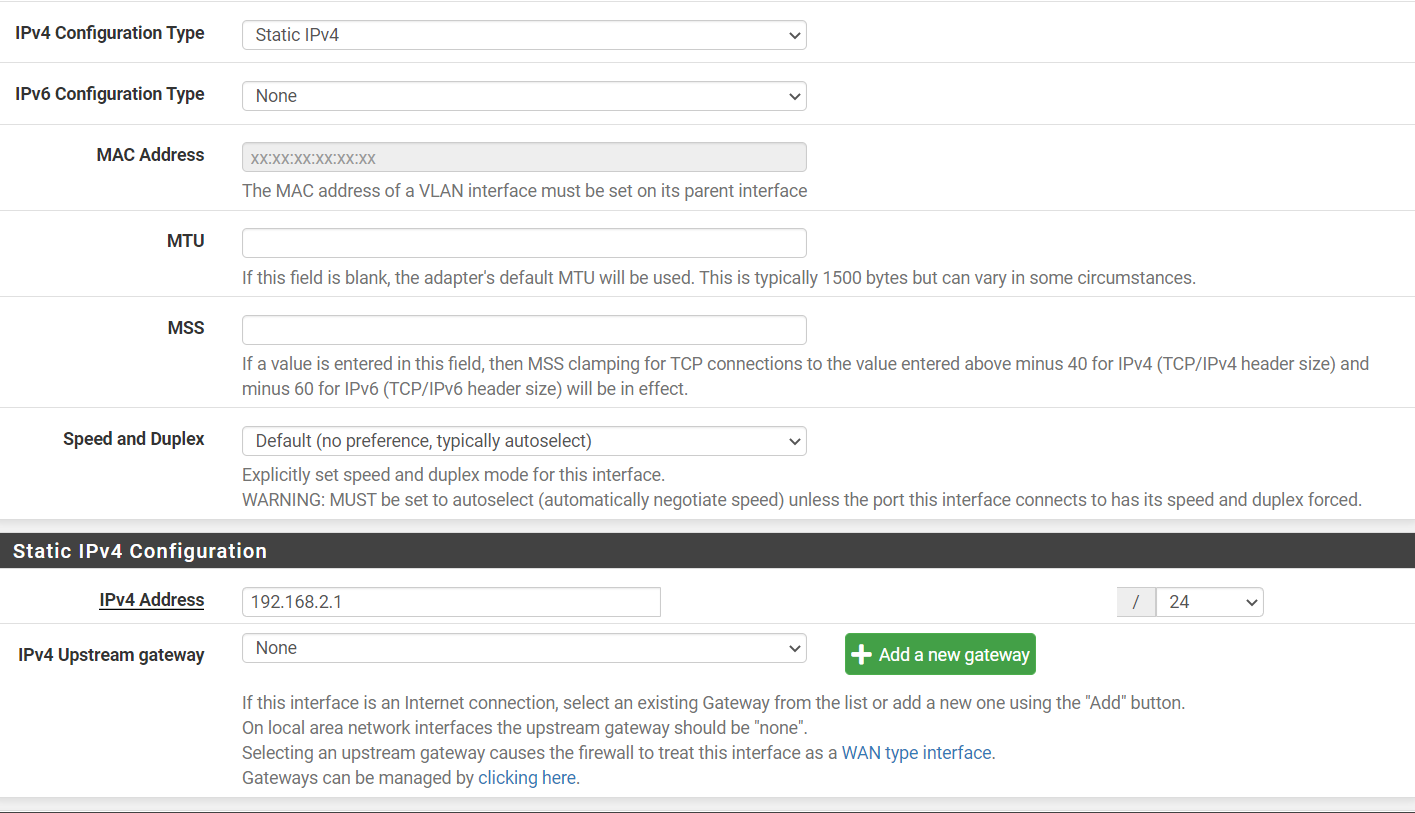
Services - DHCP Server - Guests
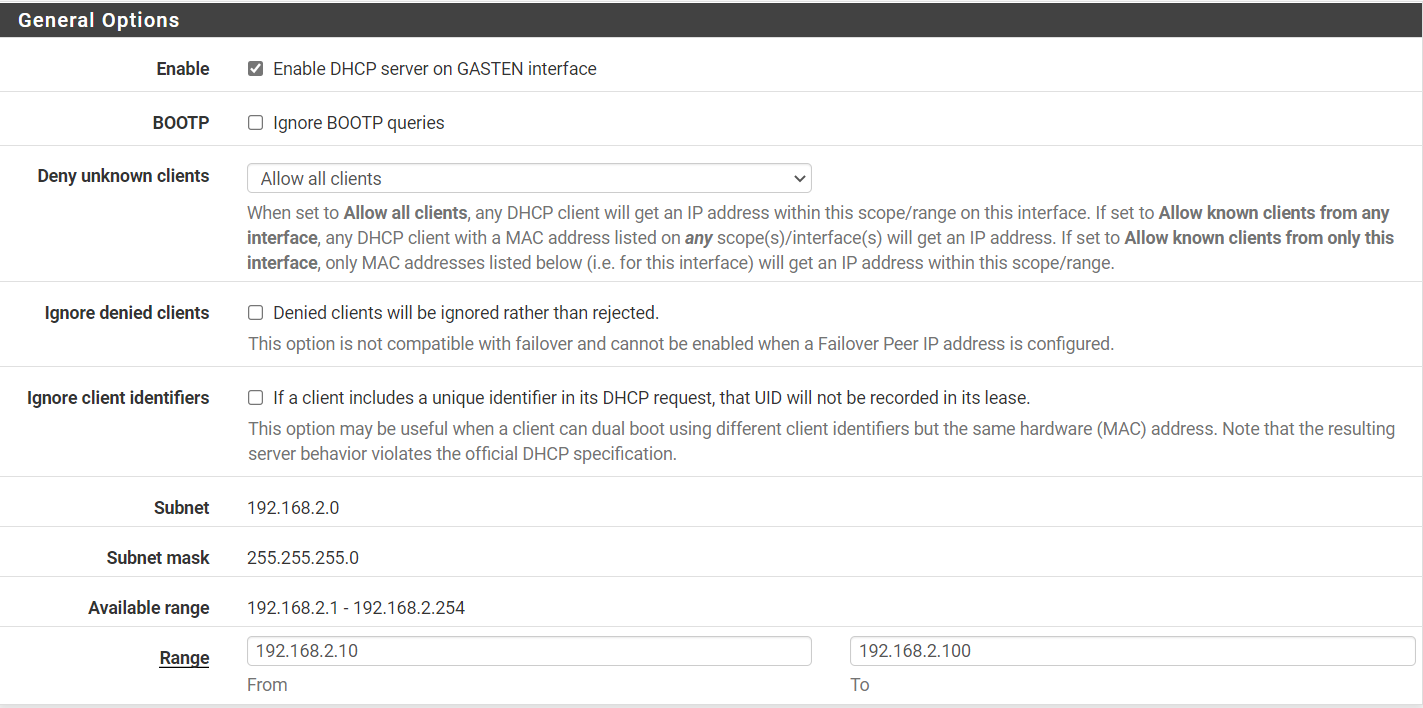
Switch port configuration:
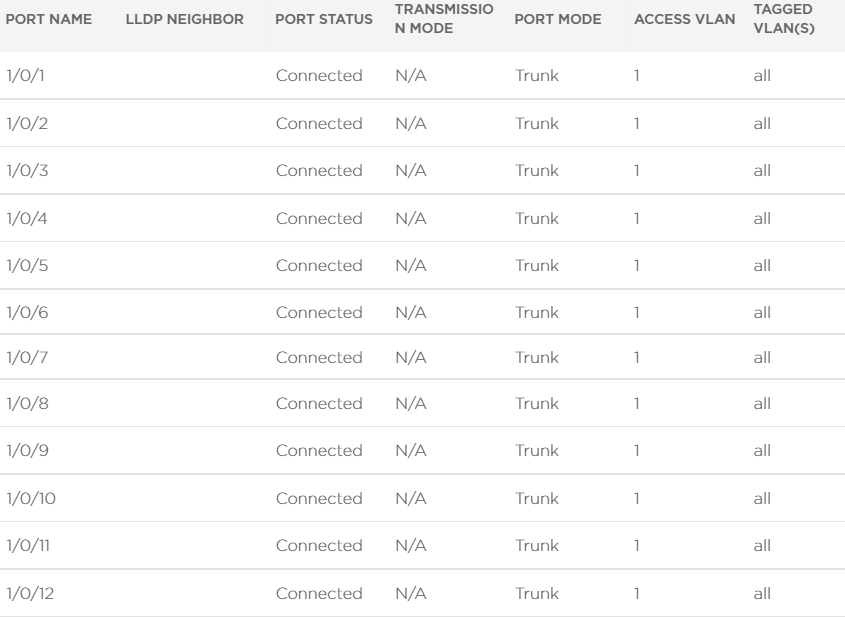
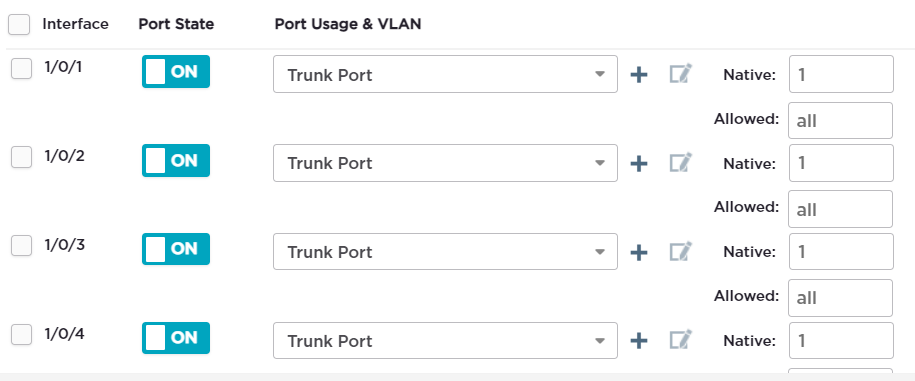
-
@brian-smit So I'll ask again... Why are you allowing all vlans on all ports?
Set it up correctly. All ports do not nned to be trunks, it will still work if correct vlans are on them but not needed.
Set up untagged ports which conect to clients.
Set up tagged ports that connect to pfSense and AP's.
These ports should only allow the vlan's needed on each. -
I'm going to change it and will change the other ports indeed into access ports.
I'll report back :-)
Above switch config could be the whole issue?
-
short update as promised:
Changing the configuration of the switch and only allowing the VLANs that we actually use (in stead of "ALL") solved the problem!