Default deny rule ipV4 for License server traffic
-
Hello,
Firewall state hardware:
We have 2 Netgate appliance in CARP Cluster.Case
We have a Houdini Side FX license server hosted on Linux.
TCP port: 1714 and 1715.
The clients retrieves licenses from the server and each month the IT Admin scheduled a redeem to get back the licenses and clean everything.We also recently applied custom fw rules for each services and we removed the ANY to ANY rules.
Issue
- The licenses server result in an error:
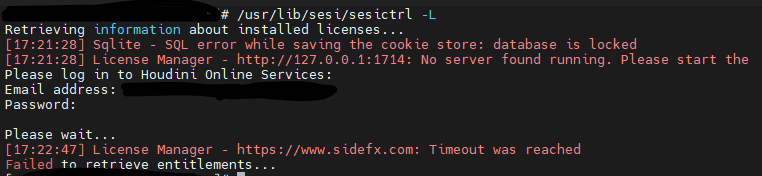
- Despite having firewall rules:
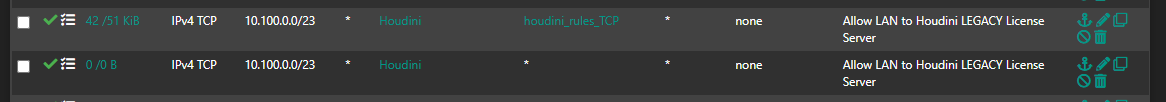
- And on the logs we can see that it is sometime allowed through the rule associated and sometimes blocked with the default deny IPV4
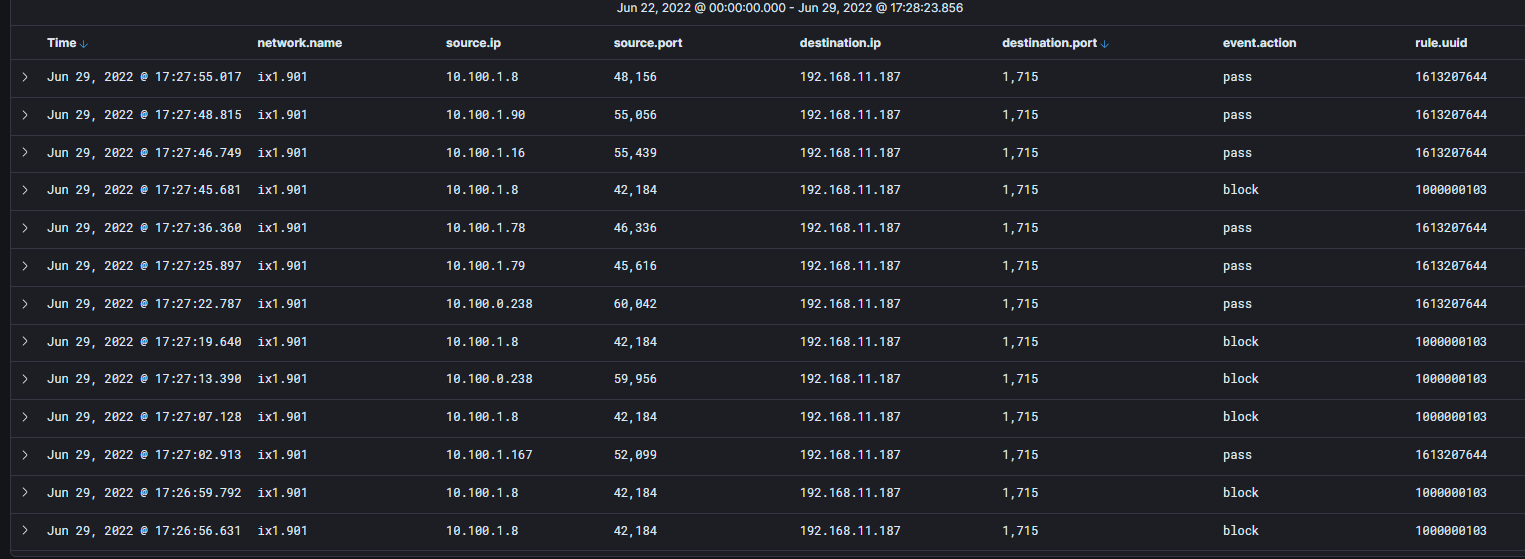 .
.I have read the troubleshooting documentation, but still does not understand why it is happening.
Does anyone have any other information that could lead resolution ?
For the moment I placed a new rule:
ANY to ANY with port 1715 and 1714 on destination target. It work but not when whe specify sources and destination IP.
-
@s0p4l1n www.sidefx.com is 206.223.178.168. Your log shows private IPs for the destination? What is the "Houdini" alias set to?
Basically the rule matches if the source, source port, dest, and dest port match. So one of those doesn't match. Note the source port is typically random.
Per that troubleshooting page, there may be stray packets blocked. "This is likely due to a TCP FIN packet arriving after firewall has removed the connection state. This happens because on occasion a packet will be lost, and the retransmits will be blocked because the firewall has already closed the connection. Another possible reason for the messages is if a packet arrived too slowly and was outside of its expected arrival window. It can also happen when web servers attempt to reuse connections.
In each case, the log entries are harmless and do not indicate a blocked connection. All stateful firewalls do this, though some do not generate log messages for this blocked traffic even if all blocked traffic is logged."
For that scenario, we uncheck the log setting "Log packets matched from the default block rules in the ruleset" which saves a lot of time and eliminates log noise.