pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue
-
Hi,
As I previously reported here:
pfSense breaks VLANSpfSense 2.7.0-Devel or pfSense Plus 22.05 breaks VLANS.
The issue manifests that VLAN networks cannot get DHCP, or communicate whatsoever.Between my first reporting and now, I tried installing numerous snapshots of 2.5.0-Devel with no avail.
My VLANs setup are like this:
For a interface named ix2 we have 2 VLANs
ix2.20 and ix2.30
The traffic is passing only for ix2 interface(Native LAN) and not for the VLAN.
The last know snapshot that did not break VLANS was pfSense-CE-memstick-2.7.0-DEVELOPMENT-amd64-20220314-1916 or pfSense 22.01 Stable.Driver information:
dev.ix.0.iflib.driver_version: 4.0.1-k dev.ix.0.%parent: pci5 dev.ix.0.%pnpinfo: vendor=0x8086 device=0x15e4 subvendor=0x8086 subdevice=0x0000 class=0x020000 dev.ix.0.%location: slot=0 function=0 dbsf=pci0:5:0:0 handle=\_SB_.PCI0.VRP0.OBL1 dev.ix.0.%driver: ix dev.ix.0.%desc: Intel(R) X553 (1GbE)I did not know what to report, the rules where fine, but I stumbled upon this defect:
https://redmine.pfsense.org/issues/12821Although comment #16 states it doesn't affect ix interfaces I beg to differ.
I will show bellow the 2 different ifconfig(s) data from pfSense 22.05 and pfSense 22.01:pfSense 22.05
ix0: flags=8802<BROADCAST,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=8138b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_UCAST,WOL_MCAST,WOL_MAGIC,VLAN_HWFILTER> ether ac:1f:6b:45:fa:88 media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix1: flags=8802<BROADCAST,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=8138b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_UCAST,WOL_MCAST,WOL_MAGIC,VLAN_HWFILTER> ether ac:1f:6b:45:fa:89 media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix2: flags=28943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST,PPROMISC> metric 0 mtu 1500 description: LAN options=903828<VLAN_MTU,JUMBO_MTU,WOL_UCAST,WOL_MCAST,WOL_MAGIC,NETMAP> ether ac:1f:6b:45:fa:8a inet6 fe80::ae1f:6bff:fe45:fa8a%ix2 prefixlen 64 scopeid 0x3 inet 172.18.0.12 netmask 0xfffe0000 broadcast 172.19.255.255 media: Ethernet autoselect (1000baseT <full-duplex,rxpause,txpause>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix3: flags=28943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST,PPROMISC> metric 0 mtu 1500 description: WAN options=9138b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_UCAST,WOL_MCAST,WOL_MAGIC,VLAN_HWFILTER,NETMAP> ether ac:1f:6b:45:fa:8b inet6 fe80::ae1f:6bff:fe45:fa8b%ix3 prefixlen 64 scopeid 0x4 inet ******** netmask 0xfffff800 broadcast ********** media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> enc0: flags=0<> metric 0 mtu 1536 groups: enc nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384 options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6> inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x6 inet 127.0.0.1 netmask 0xff000000 groups: lo nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> pfsync0: flags=0<> metric 0 mtu 1500 groups: pfsync pflog0: flags=100<PROMISC> metric 0 mtu 33160 groups: pflog ix2.20: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: IoT ether ac:1f:6b:45:fa:8a inet6 fe80::ae1f:6bff:fe45:fa8a%ix2.20 prefixlen 64 scopeid 0x9 inet 192.168.10.1 netmask 0xffffffc0 broadcast 192.168.10.63 groups: vlan vlan: 20 vlanpcp: 0 parent interface: ix2 media: Ethernet autoselect (1000baseT <full-duplex,rxpause,txpause>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix2.30: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: GuestNetwork ether ac:1f:6b:45:fa:8a inet6 fe80::ae1f:6bff:fe45:fa8a%ix2.30 prefixlen 64 scopeid 0xa inet 192.168.20.1 netmask 0xffffffc0 broadcast 192.168.20.63 groups: vlan vlan: 30 vlanpcp: 0 parent interface: ix2 media: Ethernet autoselect (1000baseT <full-duplex,rxpause,txpause>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ovpns1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::ae1f:6bff:fe45:fa88%ovpns1 prefixlen 64 scopeid 0xb inet 10.0.8.1 --> 10.0.8.2 netmask 0xffffff00 groups: tun openvpn nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> Opened by PID 24016pfSense 22.01
ix0: flags=8802<BROADCAST,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=8138b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_UCAST,WOL_MCAST,WOL_MAGIC,VLAN_HWFILTER> ether ac:1f:6b:45:fa:88 media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix1: flags=8802<BROADCAST,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=8138b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_UCAST,WOL_MCAST,WOL_MAGIC,VLAN_HWFILTER> ether ac:1f:6b:45:fa:89 media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix2: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: LAN options=803828<VLAN_MTU,JUMBO_MTU,WOL_UCAST,WOL_MCAST,WOL_MAGIC> ether ac:1f:6b:45:fa:8a inet6 fe80::ae1f:6bff:fe45:fa8a%ix2 prefixlen 64 scopeid 0x3 inet 172.18.0.12 netmask 0xfffe0000 broadcast 172.19.255.255 media: Ethernet autoselect (1000baseT <full-duplex,rxpause,txpause>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix3: flags=28943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST,PPROMISC> metric 0 mtu 1500 description: WAN options=8138b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_UCAST,WOL_MCAST,WOL_MAGIC,VLAN_HWFILTER> ether ac:1f:6b:45:fa:8b inet6 fe80::ae1f:6bff:fe45:fa8b%ix3 prefixlen 64 scopeid 0x4 inet ******** netmask 0xfffff800 broadcast ********** media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> enc0: flags=0<> metric 0 mtu 1536 groups: enc nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384 options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6> inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x6 inet 127.0.0.1 netmask 0xff000000 groups: lo nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> pflog0: flags=100<PROMISC> metric 0 mtu 33160 groups: pflog pfsync0: flags=0<> metric 0 mtu 1500 groups: pfsync ix2.20: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: IoT ether ac:1f:6b:45:fa:8a inet6 fe80::ae1f:6bff:fe45:fa8a%ix2.20 prefixlen 64 scopeid 0x9 inet 192.168.10.1 netmask 0xffffffc0 broadcast 192.168.10.63 groups: vlan vlan: 20 vlanpcp: 0 parent interface: ix2 media: Ethernet autoselect (1000baseT <full-duplex,rxpause,txpause>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix2.30: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: GuestNetwork ether ac:1f:6b:45:fa:8a inet6 fe80::ae1f:6bff:fe45:fa8a%ix2.30 prefixlen 64 scopeid 0xa inet 192.168.20.1 netmask 0xffffffc0 broadcast 192.168.20.63 groups: vlan vlan: 30 vlanpcp: 0 parent interface: ix2 media: Ethernet autoselect (1000baseT <full-duplex,rxpause,txpause>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ovpns1: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1500 options=80000<LINKSTATE> inet6 fe80::ae1f:6bff:fe45:fa88%ovpns1 prefixlen 64 scopeid 0xb inet 10.0.8.1 --> 10.0.8.2 netmask 0xffffff00 groups: tun openvpn nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> Opened by PID 49373As you can observe the difference between the 2 versions is that the tag "PROMISC" is missing from ix.20 and ix.30 interfaces in pfSense 22.05 and present in pfSense 22.01, as the defect states.
Other packages like pfBlocker and Suricata were disabled.
Please advise.
-
@nrgia you wouldn't need promisc on the vlan interface. I am running 22.05 and my vlans are working just fine.
igb2.4: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: W_PSK options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:08:a2:0c:e6:20 inet6 fe80::208:a2ff:fe0c:e620%igb2.4 prefixlen 64 scopeid 0xb inet 192.168.4.253 netmask 0xffffff00 broadcast 192.168.4.255 groups: vlan vlan: 4 vlanpcp: 0 parent interface: igb2 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb2.6: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: W_Guest options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 00:08:a2:0c:e6:20 inet6 fe80::208:a2ff:fe0c:e620%igb2.6 prefixlen 64 scopeid 0xc inet 192.168.6.253 netmask 0xffffff00 broadcast 192.168.6.255 groups: vlan vlan: 6 vlanpcp: 0 parent interface: igb2 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>They don't have promisc listed.. Here are couple of dhcp logs of devices getting dhcp on the vlans
Jun 30 08:10:21 dhcpd 62588 DHCPACK on 192.168.4.77 to 40:a9:cf:c2:b0:99 via igb2.4 Jun 30 08:10:21 dhcpd 62588 DHCPREQUEST for 192.168.4.77 from 40:a9:cf:c2:b0:99 via igb2.4 Jun 30 11:00:37 dhcpd 62588 DHCPACK on 192.168.6.119 to 6c:24:08:18:72:0b (BE2BP581) via igb2.6 Jun 30 11:00:37 dhcpd 62588 DHCPREQUEST for 192.168.6.119 from 6c:24:08:18:72:0b (BE2BP581) via igb2.6 -
@johnpoz I don't intend to contradict you somehow
That is what I saw missing.
Also why on 22.01 is enabled, and on 22.05 it is not?
Again why restoring 22.01 fixes the issue?
There are no changes in the rules, whatsoever.From the defect: "Maybe it promiscuous mode issues, issues interacting with Netgraph, VLAN 0, I don't know." - maybe it's not the same issue, but this is what picked my attention
Are the igb and ix using the same driver in FreeBSD?
I'm open to sugestions, but please consider that the rules are sound.
Thank you -
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
but please consider that the rules are sound.
If dhcp is enabled then yeah rules would be sound, because when you enable dhcp server it creates hidden rules to allow for dhcp..
It could be something with the different interfaces. But it not related to promisc tag your seeing or not seeing, that I am like 99.99% sure of ;)
I wish I had an answer for you - the point of my post was to just say that I am running 22.05 and and not seeing the problem. So its not like something across the board in 22.05.. And to let you know its not related to promisc setting, atleast 99.99% sure its not - because I don't have that and all working here.
The guy that most likely could help would be @stephenw10
-
Thank you @johnpoz I see that you help a lot of people here on the forums. But in my case, as you saw in the other post, it started a while ago, and I tried everything, changing the rules, disabling packets, I even disabled NUT :) , the only thing that fixes it, is restoring pfSense 22.01.
And yes I agree, I don't get my hopes up, but maybe someone has a solution, if not, maybe after a few months, someone will stumble upon this and drop a solution, or say it happens to me also.
-
@nrgia Steve would be my go to guy on something like this - if he doesn't know about an issue, he will for sure have some stuff to get more info with..
So your seeing the tags hit pfsense? But pfsense just not answering them?
So for example if I do a sniff with -e on from command line with tcpdump - I see traffic with the tag..
When you sniff on the vlan interface via packet capture under diagnostic menu - you see no traffic?
-
@johnpoz unfortunatelly for the moment I reverted back to pfSense 22.01. If you are kind enough to help me investigate, I can upgrade tomorrow and investigate together, or provide the information you asked for.
I can do it via VPN, but I'm afraid that I will lose connection, after that.
Can I ping @stephenw10 directly on private, about this? What is the best practice?
Thanks -
@nrgia I am normally around all day, really all the time ;) Unless I get caught up in a real work thing - Fridays normally pretty light ;) Got a couple meetings on the cal, but cross fingers it will be a light day..
When it comes to hardware related stuff, or stuff that is most likely driver or hardware sort of stuff @stephenw10 is the guy! Now if I could duplicate the problem here I would be all in ;) But have not seen this issue and don't have anything that has that interface to play with even.
But always up for helping figure out a problem..
Lot of smart people around here - sure we can figure out what is going on.. Problem is might not be something that people get involved in - especially if they are not seeing the problem or don't have the hardware to try and duplicate. Steve seems to have everything ever made in his lab ;) heheh
The VLAN_HWTAGGING is a thing I would be interesting in looking into, I saw some stuff on the freebsd mailing list about that actually and the promisc setting.. You could put your interface into promisc mode and see if that corrects the problem - but that shouldn't need to be set as you see on my setup.. But it might be a work around for a driver issue?
I should be around trmw though - and happy to help if I can.. But hardware issues not really my "thing" if you will.. Especially if I don't have the hardware to duplicate it with.
-
I can definitely look into this. I'm not aware of any issue with ix and vlans though.
In fact I have one here and it's working fine:
[22.05-RELEASE][admin@4100.stevew.lan]/root: ifconfig ix3.1001 ix3.1001: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: Guest options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> ether 90:ec:77:1f:8a:5f inet6 fe80::92ec:77ff:fe1f:8a5f%ix3.1001 prefixlen 64 scopeid 0x10 inet 10.101.0.1 netmask 0xffffff00 broadcast 10.101.0.255 groups: vlan vlan: 1001 vlanpcp: 0 parent interface: ix3 media: Ethernet autoselect (1000baseT <full-duplex,rxpause,txpause>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> [22.05-RELEASE][admin@4100.stevew.lan]/root: tcpdump -i ix3.1001 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on ix3.1001, link-type EN10MB (Ethernet), capture size 262144 bytes 01:55:37.636598 IP AP300.stevew.lan.55659 > ntp2.icolo.io.ntp: NTPv4, Client, length 48 01:55:37.773762 IP ntp2.icolo.io.ntp > AP300.stevew.lan.55659: NTPv4, Server, length 48 01:55:41.643175 ARP, Request who-has 10.101.0.1 tell AP300.stevew.lan, length 42 01:55:41.643193 ARP, Reply 10.101.0.1 is-at 90:ec:77:1f:8a:5f (oui Unknown), length 28Steve
-
@stephenw10 and no promisc set either ;)
-
Indeed, and it shouldn't need to be.
Something hardware specific perhaps? That's the SoC NIC in a 4100.
Steve
-
@stephenw10 @johnpoz
I appreciate your time guys.This is the board if it helps
https://www.supermicro.com/en/products/motherboard/A2SDi-4C-HLN4FShould I provide a TCP dump on vlan interface or on the native interface ?
I mean in my case ix2 or ix.20 ? Or both ?
Thank you -
Look on the VLAN. If there's nothing there look on the parent for the tagged traffic. Or just do both anyway!
If you're doing that in the pfSense GUI be aware that you cannot (currently) apply filters when looking for tagged traffic. https://redmine.pfsense.org/issues/13094
-
@stephenw10 I will use your cli command
tcpdump -iI see it spits a lot of info, I will try to paste relevant info like in your example.
-
This all I have:
listening on ix2.20, link-type EN10MB (Ethernet), capture size 262144 bytes 15:22:07.873050 ARP, Request who-has 192.168.10.56 tell 192.168.10.1, length 28 15:22:10.070379 IP 192.168.10.1.mdns > 224.0.0.251.mdns: 0 [2q] PTR (QM)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QM)? _googlecast._tcp.local. (94) 15:22:10.071252 IP 192.168.10.1.mdns > 224.0.0.251.mdns: 0*- [0q] 4/0/0 PTR SHIELD-Android-TV-ee41442d2c14cc09fde82be16f84be32._googlecast._tcp.local., (Cache flush) A 172.18.0.14, (Cache flush) SRV ee41442d-2c14-cc09-fde8-2be16f84be32.local.:8009 0 0, (Cache flush) TXT "id=ee41442d2c14cc09fde82be16f84be32" "cd=3CABD325728E72997BA6735F95651E36" "rm=" "ve=05" "md=SHIELD Android TV" "ic=/setup/icon.png" "fn=SHIELD" "ca=463365" "st=0" "bs=FA8F14F198FB" "nf=1" "rs=" (356) 15:22:10.096988 ARP, Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:22:11.093740 ARP, Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:22:13.091847 ARP, Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:22:30.072687 IP 192.168.10.1.mdns > 224.0.0.251.mdns: 0 [2q] PTR (QM)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QM)? _googlecast._tcp.local. (94) 15:22:30.073588 IP 192.168.10.1.mdns > 224.0.0.251.mdns: 0*- [0q] 4/0/0 PTR SHIELD-Android-TV-ee41442d2c14cc09fde82be16f84be32._googlecast._tcp.local., (Cache flush) A 172.18.0.14, (Cache flush) SRV ee41442d-2c14-cc09-fde8-2be16f84be32.local.:8009 0 0, (Cache flush) TXT "id=ee41442d2c14cc09fde82be16f84be32" "cd=3CABD325728E72997BA6735F95651E36" "rm=" "ve=05" "md=SHIELD Android TV" "ic=/setup/icon.png" "fn=SHIELD" "ca=463365" "st=0" "bs=FA8F14F198FB" "nf=1" "rs=" (356) 15:22:30.093361 ARP, Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:22:31.091257 ARP, Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:22:33.095748 ARP, Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:22:37.097207 ARP, Request who-has 192.168.10.60 tell 192.168.10.1, length 28 -
@nrgia make sure you add -e on tcpdump or it won't spit out vlan tag info
but isn't that 192.168.10 your vlan 20?
-
Yeah, so that looks expected for a dump inside the VLAN. Except there's only outbound traffic.
So run
tcpdump -e -i ix2.20and see if the tagged traffic is arriving. -
Yes 192.168.10.1 is vlan 20
Here you go:
]/root: tcpdump -i ix2.20 -e tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on ix2.20, link-type EN10MB (Ethernet), capture size 262144 bytes 15:40:03.507991 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:40:03.518434 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 136: 192.168.10.1.mdns > 224.0.0.251.mdns: 0 [2q] PTR (QM)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QM)? _googlecast._tcp.local. (94) 15:40:04.505932 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:40:04.508145 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 136: 192.168.10.1.mdns > 224.0.0.251.mdns: 0 [2q] PTR (QM)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QM)? _googlecast._tcp.local. (94) 15:40:04.509221 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 398: 192.168.10.1.mdns > 224.0.0.251.mdns: 0*- [0q] 4/0/0 PTR SHIELD-Android-TV-ee41442d2c14cc09fde82be16f84be32._googlecast._tcp.local., (Cache flush) A 172.18.0.14, (Cache flush) SRV ee41442d-2c14-cc09-fde8-2be16f84be32.local.:8009 0 0, (Cache flush) TXT "id=ee41442d2c14cc09fde82be16f84be32" "cd=3CABD325728E72997BA6735F95651E36" "rm=" "ve=05" "md=SHIELD Android TV" "ic=/setup/icon.png" "fn=SHIELD" "ca=463365" "st=0" "bs=FA8F14F198FB" "nf=1" "rs=" (356) 15:40:05.510287 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 136: 192.168.10.1.mdns > 224.0.0.251.mdns: 0 [2q] PTR (QM)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QM)? _googlecast._tcp.local. (94) 15:40:05.511240 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 398: 192.168.10.1.mdns > 224.0.0.251.mdns: 0*- [0q] 4/0/0 PTR SHIELD-Android-TV-ee41442d2c14cc09fde82be16f84be32._googlecast._tcp.local., (Cache flush) A 172.18.0.14, (Cache flush) SRV ee41442d-2c14-cc09-fde8-2be16f84be32.local.:8009 0 0, (Cache flush) TXT "id=ee41442d2c14cc09fde82be16f84be32" "cd=3CABD325728E72997BA6735F95651E36" "rm=" "ve=05" "md=SHIELD Android TV" "ic=/setup/icon.png" "fn=SHIELD" "ca=463365" "st=0" "bs=FA8F14F198FB" "nf=1" "rs=" (356) 15:40:05.526062 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:40:06.506694 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:40:07.530222 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:40:10.516671 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 ^C 11 packets captured 11 packets received by filter 0 packets dropped by kernel -
And with tcpdump -e -i ix2.20
]/root: tcpdump -e -i ix2.20 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on ix2.20, link-type EN10MB (Ethernet), capture size 262144 bytes 15:45:48.622767 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:46:05.588374 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 136: 192.168.10.1.mdns > 224.0.0.251.mdns: 0 [2q] PTR (QM)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QM)? _googlecast._tcp.local. (94) 15:46:05.589317 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 398: 192.168.10.1.mdns > 224.0.0.251.mdns: 0*- [0q] 4/0/0 PTR SHIELD-Android-TV-ee41442d2c14cc09fde82be16f84be32._googlecast._tcp.local., (Cache flush) A 172.18.0.14, (Cache flush) SRV ee41442d-2c14-cc09-fde8-2be16f84be32.local.:8009 0 0, (Cache flush) TXT "id=ee41442d2c14cc09fde82be16f84be32" "cd=3CABD325728E72997BA6735F95651E36" "rm=" "ve=05" "md=SHIELD Android TV" "ic=/setup/icon.png" "fn=SHIELD" "ca=463365" "st=0" "bs=FA8F14F198FB" "nf=1" "rs=" (356) 15:46:05.619590 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:46:06.623982 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:46:08.616921 ac:1f:6b:45:fa:8a (oui Unknown) > Broadcast, ethertype ARP (0x0806), length 42: Request who-has 192.168.10.60 tell 192.168.10.1, length 28 15:46:18.970438 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 82: 192.168.10.1.mdns > 224.0.0.251.mdns: 0 PTR (QM)? _googlezone._tcp.local. (40) 15:46:18.970617 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 119: 192.168.10.1.mdns > 224.0.0.251.mdns: 0 SRV (QM)? ee41442d-2c14-cc09-fde8-2be16f84be32._googlezone._tcp.local. (77) 15:46:18.970973 ac:1f:6b:45:fa:8a (oui Unknown) > 01:00:5e:00:00:fb (oui Unknown), ethertype IPv4 (0x0800), length 252: 192.168.10.1.mdns > 224.0.0.251.mdns: 0*- [0q] 4/0/0 PTR ee41442d-2c14-cc09-fde8-2be16f84be32._googlezone._tcp.local., (Cache flush) A 172.18.0.14, (Cache flush) SRV ee41442d-2c14-cc09-fde8-2be16f84be32.local.:10001 1100 0, (Cache flush) TXT "id=3CABD325728E72997BA6735F95651E36" "UDS" (210) ^C 9 packets captured 9 packets received by filter 0 packets dropped by kernel -
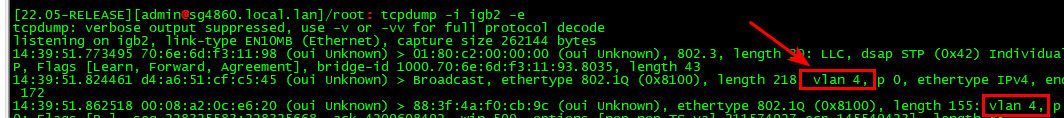
Sorry I meant:
tcpdump -e -i ix2On the parent interface dircetly