Providing isolation between Vlans!
-
@enesas By default there are no firewall rules when you create a vlan, therefore nothing can talk outside its subnet.
If you want vlans to only talk to the internet create an alias with all the rfc1918 address space, use it to create a block rule and drag it above the allow rule that I guess that you’ve added.
-
From LAN (default in the setup) to other VLANs is allowed by the default 'any to any' rule. VLANs you create are isolated as there are no rules allowing traffic out. Or at least that has been my experience.
-
@enesas said in Providing isolation between Vlans!:
this means big business
Well managing and setting up a firewall with proper rules does take a bit of work yes ;) Especially when you have multiple network segments and want to filter between them.
While you could use floating tab to assign some rules to all interfaces, I believe its a better idea to put specific rules on each interface directly - as this allow for ease of reading rules later, and or editing specific interfaces with different rules at some future point in time.
An alias with all of rfc1918 space in it can be quite useful in blocking all your other vlans, etc. But you still need to assign rules to allow or block specifically for each interface. For example allowing dns to pfsense IP on that interface, etc.
While you might think it a PITA, yes setting up a firewall properly does take some effort ;)
-
@johnpoz
While researching, Perry suggested the following method and I applied it. only DNS pass rule should be defined on top of this rule, otherwise it will not go to the internet. (or you need to give manual dns)
" Instead of creating alias with subnet i use CIDR in rules
Block Lan3 net to 192.168.0.0/16 Default block all local subnets" -
@enesas said in Providing isolation between Vlans!:
Instead of creating alias with subnet i use CIDR in rules
Sure you can do that if easier for you or you like to see the cidr.. But when we say create an alias with all rfc1918 we mean all of them.
10/8
192.168/16
172.16/12This way if you decide to use some 10 address or 172.16-31 address space in the future you don't need to edit any rules since those are also blocked, even if not currently using that part of the rfc1918 space.
Notice my alias is from 2015 ;)
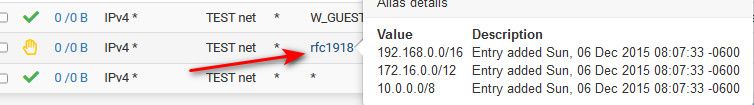
But sure a cidr works just the same.
-
@johnpoz thenk you
-
Here is what I have on my guest WiFi VLAN. It allows no contact at all with my LAN or router, other than pinging the interface it's connected to.
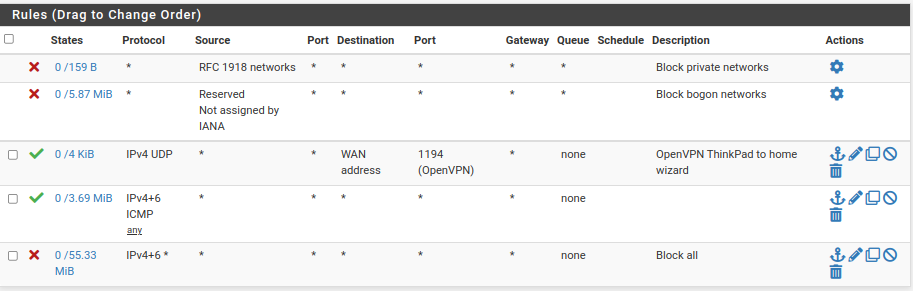
-
@jknott I don't know what you think those rules are going to allow, your first rule there is block rfc1918 source.. Which is before icmp, so only thing that would work is IPv6 ping.
So unless you have some floating those rules make no sense. How is bogon going to be source to your wifi vlan interface?
-
Ooops! I copied the wrong rules. Here's what I meant to post. The other one is my WAN rules.
These are my guest WiFi rules.
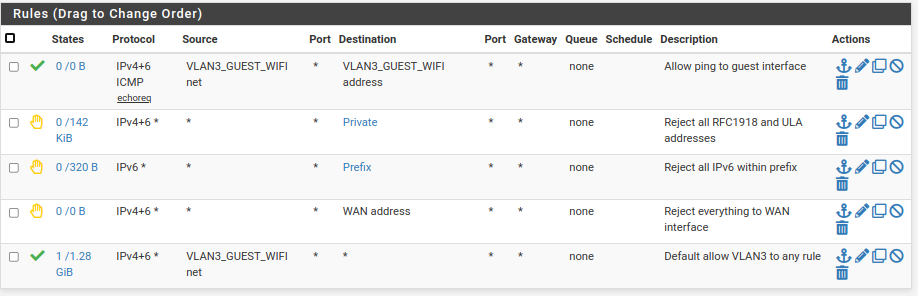
-
@jknott haha - ok that makes more sense ;)
-
@jknott What's the point of the "Block All"?
That's already there without adding that rule. -
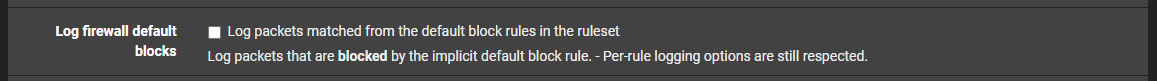
@jarhead that rule is set to not log.. So if he was logging default deny (which is default to do).. He would not log any traffic hitting that block before the default deny which would log.
Common practice to put in rule like that so you don't log a lot of noise, I have my default log off, and just have a block rule at the end of my wan that logs only "SYN" hits.. And common UDP ports for example.
-
@johnpoz Ok, gotcha. Makes sense but I would rather log blocks. Guess I won't be adding a Block All rule.

-
@jarhead you can log what you want, here are my 2 rules on wan that log stuff I block, and also log some of the stuff I allow.
Notice the little log icons, and the gear which says I did something special with the rule - in my case I only log syn only packets, if its something other like a SA or other out of state traffic that might hit my wan I don't really care to see it.
And UDP - while I don't want to see all the random off the wall upd noise - I do like to see interesting UDP ports and where I am being hit from, etc.
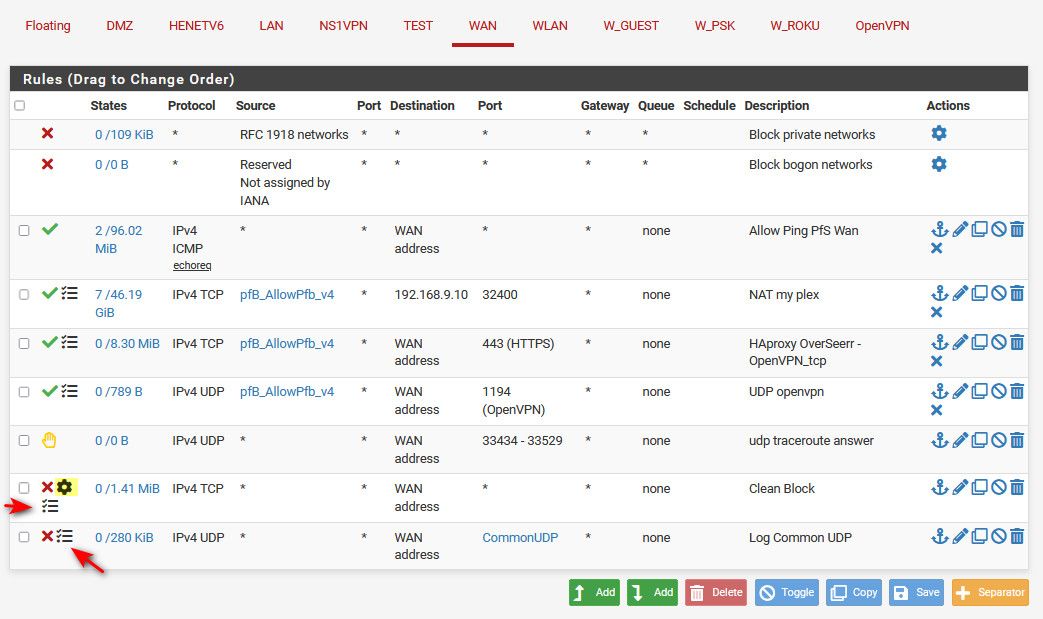
Anything I do not allow still hits the default deny, just not logged because I turned off the option to log default deny rule.
-
@johnpoz Yeah, I got that, was just making a joke because I see no reason to add a Block All rule even if just for logging since you can just turn logging off. Yours I can see because you're logging specific things, but Block All makes no sense to me.
-
@jarhead only problem is - maybe he wants to see default logs on is lan side interfaces, but not on his wan.
You can't just turn off not log default for specific interfaces - its all or nothing ;) So if he wants to see those logs, but not all the noise on is wan, creating your own catch all block that would be hit before the default that does not log, would accomplish that.
I wouldn't do it the way he is doing it either ;) But hey there are multiple ways to skin a cat..
-
I use block on the WAN side, instead of reject, as it makes it appear as nothing is there. A reject will tell incoming traffic it's not allowed, revealing the presence of some device. I'm not sure if the default rule is reject or block.
On internal rules, I use reject, not block.
-
@jknott It's block.
-
@jknott said in Providing isolation between Vlans!:

This is an interesting one: Reject "Prefix".
If your prefix is dynamic, like for most of us who at home get IPv6 from their ISP, it would be nice to have this feature, but not much interest so far it seems.
But I know, jknott will keep his prefix stable by all means and john doesn't care for IPv6 to much.

-
@bob-dig said in Providing isolation between Vlans!:
and john doesn't care for IPv6 to much
Haha - not that I don't care for it, I just don't see it as actually needed as of yet. I agree its the future for sure, and its got some slick stuff going for it.. But its not something you actually need. My isp doesn't even have it ;) I play with it via HE tunnel.. Which to be honest has some huge advantages over many an isp IPv6 so called deployments..
Its something that everyone should play with, but if you don't have time or desire to learn its differences - sure simple solution is not worry about it.
When someone here actually names one resource that requires I have IPv6 that I would care to visit ;) Then sure I will turn it on for all my networks, other then my play vlans, and my pc which I just toggle it on or off if I am playing with something IPv6 related.
For the time being and many years into the future, its just not something a user actually needs to worry about. If they are having issues with it, it simpler to just not use it.. Nothing say you have to.
Here something I keep meaning to look into for example, site I use pretty often tvmaze, just doesn't work with IPv6.. It has an IPv6 address (i can ping it on IPv6), I just can get to it when I enable IPv6 on my pc. It never fails back to IPv4. Its on my list of things to investigate why ;)