OpenVPN clients can't resolve local server names
-
@dansci what version of pfsense are you using. You need to make sure that your tunnel networks are in the unbound acl.
what is in
cat /var/unbound/access_lists.conf -
@johnpoz This is the output:
access-control: 127.0.0.1/32 allow_snoop access-control: ::1 allow_snoop access-control: 127.0.0.0/8 allow access-control: 192.168.10.0/24 allow access-control: 192.168.11.0/24 allow access-control: 192.168.20.0/24 allow access-control: 192.168.20.1/24 allow access-control: 192.168.30.0/24 allow access-control: 192.168.40.0/24 allow access-control: 192.168.50.0/24 allow access-control: 192.168.70.0/24 allow access-control: 192.168.71.0/24 allow access-control: 192.168.80.0/24 allow access-control: 192.168.99.0/24 allow access-control: ::1/128 allow #DNS access access-control: 192.168.11.0/24 allowSo the last line seems to be what I've added into the Servies->DNS Resolver->Access Lists
-
@dansci well its in there.
So from a vpn client, do a dns query to unbound.. Do you time out, do you get say a refused or NX answer?
use your fav dns client, dig, host or even nslookup.
If you get timeout - sniff on pfsense via packet capture is pfsense seeing the query?
-
@johnpoz I do nslookup and I get
Server: 127.0.0.53 Address: 127.0.0.53#53 ** server can't find <my_server_name>.<my_domain>: NXDOMAIN -
@dansci Well 127.0.0.53 is not pfsense, that is some local dns client on the machine, that prob forwards to where??? My guess is the dns the client got from its local dhcp server.
So now change the server you talk to so you directly ask pfsense IP you want to use.
dig its as simple as @ipaddress in your query
with nslookup you need to set server.. like this.
$ nslookup Default Server: pi.hole Address: 192.168.3.10 > server 192.168.9.253 Default Server: sg4860.local.lan Address: 192.168.9.253then do your query for example.
-
@johnpoz hmm, I have no idea why the VPN doesn't set up a server like I would need, which is 192.168.11.1.
When I set it that way in nslookup I get a connection timeout:
> server 192.168.11.1 Default server: 192.168.11.1 Address: 192.168.11.1#53 > google.pl ;; connection timed out; no servers could be reachedOn the pfSense side I see:
15:00:44.169763 AF IPv4 (2), length 59: (tos 0x0, ttl 64, id 41007, offset 0, flags [none], proto UDP (17), length 55) 192.168.11.2.48282 > 192.168.11.1.53: [udp sum ok] 11595+ A? google.pl. (27) 15:00:44.173324 AF IPv4 (2), length 59: (tos 0x0, ttl 64, id 241, offset 0, flags [none], proto UDP (17), length 55) 192.168.11.2.50416 > 192.168.11.1.53: [udp sum ok] 11595+ A? google.pl. (27) 15:00:49.183350 AF IPv4 (2), length 59: (tos 0x0, ttl 64, id 23552, offset 0, flags [none], proto UDP (17), length 55) 192.168.11.2.50058 > 192.168.11.1.53: [udp sum ok] 11595+ A? google.pl. (27) -
@dansci well good that you get timeout, firewall rule blocking.. Because if unbound was actually seeing it, but client was not in the acl, you would get a refused vs timeout.
-
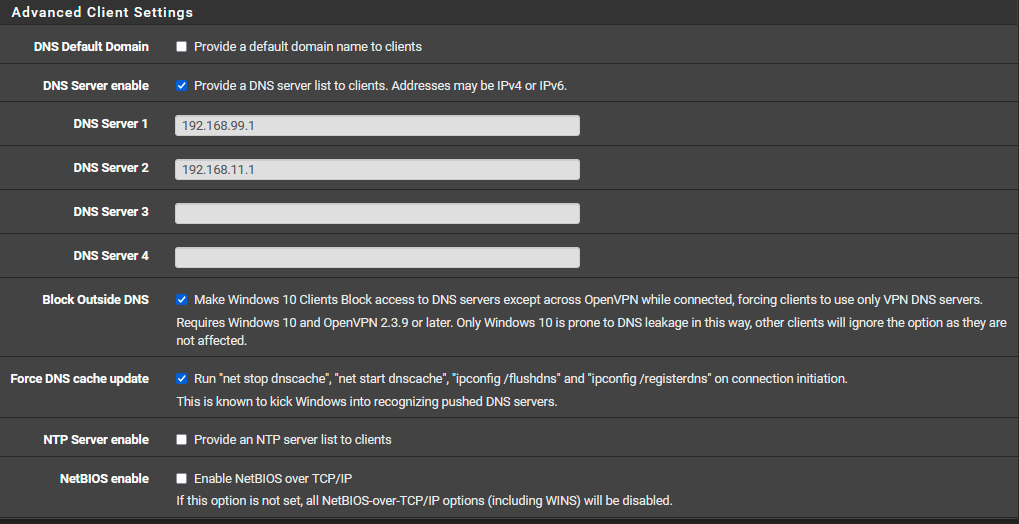
@johnpoz Even now I changed the server to 192.168.99.1 which is the address of the main VLAN of mine (previously I used 192.168.11.1 - the first address from the address pool for the VPN tunnel). Now nslookup was able to find the name of my local server :)
So the question remains what to do to make the VPN clients know that 192.168.99.1 is the DNS server...
-
@dansci you hand it out to them, but there is nothing saying they will use it.
That 127.0.0.53 address you show points to the client using systemd-resolved.. That is a whole ball of wax on its own ;)
You would need to look in how to configure that how you want, pretty sure it does allow for split dns, etc. Not a fan of it on my own linux boxes, I always just turn it off ;) And allows me to set specific dns I want to use with the old resolv.conf method.
-
@johnpoz I found somewhere on the web that it is useful to install the 'openresolv' package. This helped :)
Thank you for your activity on the forum and quick support on any issue :)