pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue
-
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
Correct, I could communicate only via IP with pfSense. Only that worked.
If you were not getting arp replies then wouldn't work even with IP..
-
@johnpoz said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
Correct, I could communicate only via IP with pfSense. Only that worked.
If you were not getting arp replies then wouldn't work even with IP..
If you say so
-
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
If you say so
Not something making up dude - if you can not arp for the mac of something, it is impossible to talk to it even with an IP.
Mac is what is used to talk to something on a network.. Just not possible if you do not have the mac to talk to.
As Steve mentioned
We see no ARP replies to pfSense's queries and it looks like one way traffic from the clients.
Look at your arp table on your client, arp -a will show you the full table.. If there is no mac for an IP then your not going to talk to it.
-
@johnpoz said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
If you say so
Not something making up dude - if you can not arp for the mac of something, it is impossible to talk to it even with an IP.
Mac is what is used to talk to something on a network.. Just not possible if you do not have the mac to talk to.
As Steve mentioned
We see no ARP replies to pfSense's queries and it looks like one way traffic from the clients.
Look at your arp table on your client, arp -a will show you the full table.. If there is no mac for an IP then your not going to talk to it.
The host, the switch and pfSense have static IP. If it did not work, how I could provide the tcpdump?
As you can see the tcpdump is from ix2 interface,from pfSense, you can see that priority 3 set from pfSense.
Is this discussion productive, in any way ? Do you think I'm lying ? -
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
The host, the switch and pfSense have static IP. If it did not work
Then there must be an mac listed in the arp table.. Keep in mind that connecting to pfsense on its lan interface, and then sniffing on a different interface has little to do with if the clients on that other interface or vlan can arp for stuff..
You might see the arp request go out, or come in, but if you do not see replies then those devices that are arping for each other are not going to be able to talk to each other - period.
Don't think anyone is lying - just trying to understand all the pieces to the puzzle. I do recall looking at some of the sniffs and while I saw arp request, I don't recall ever seeing any answers.
-
So I did like that:
- I was connected via ssh to pfSense
- Set the priority to 3 from pfSense from GUI
- Set the priority from the switch
- After that all the hosts lost communication besides pfSense and the host I was running the test
- I performed a tcpdump on pfsense LAN interface ix2
- I could also connect to pfSense GUI via it's LAN IP, but not with it's domain name.
Other technicalities I don't know how to explain. If the test wasn't good, then this is how I understood to reproduce it, following what Steve has told me.
-
Right but the LAN interface here is ix2 unatgged, no VLAN right?
The pcap only captured VLAN tagged traffic, the GUEST interface, and it looked like that was failing?
It appeared as though the priority setting in the switch was in fact filtering the traffic in some way rather than applying tags. Which might well be what it's supposed to be doing in that mode.
Are you able to test that on your switch @johnpoz? -
@stephenw10 yeah my switch is still up, I could setup some vlans to go through it.
What exactly would you like me to test, doing port based qos? vs the 802.1p
Let me add the vlans to the switch, so I can just connect my AP to it, it has 1 untagged vlan and 3 other tagged vlans. 2 of which are tagged all the way to pfsense, and another that has its own uplink to pfsense that is untagged.
-
Yeah any test you can do there to see what those QoS settings it has do.
I expected it to apply tags but I have no idea if that's inbound or outbound on the ports.
However it looks more like it's filtering based on the tags from those last pcaps. No ARP replies to queries sent as
p 3. -
@stephenw10 said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
Right but the LAN interface here is ix2 unatgged, no VLAN right?
On the switch it looks like this, port 15, is ix2 and it is a member of all 3:
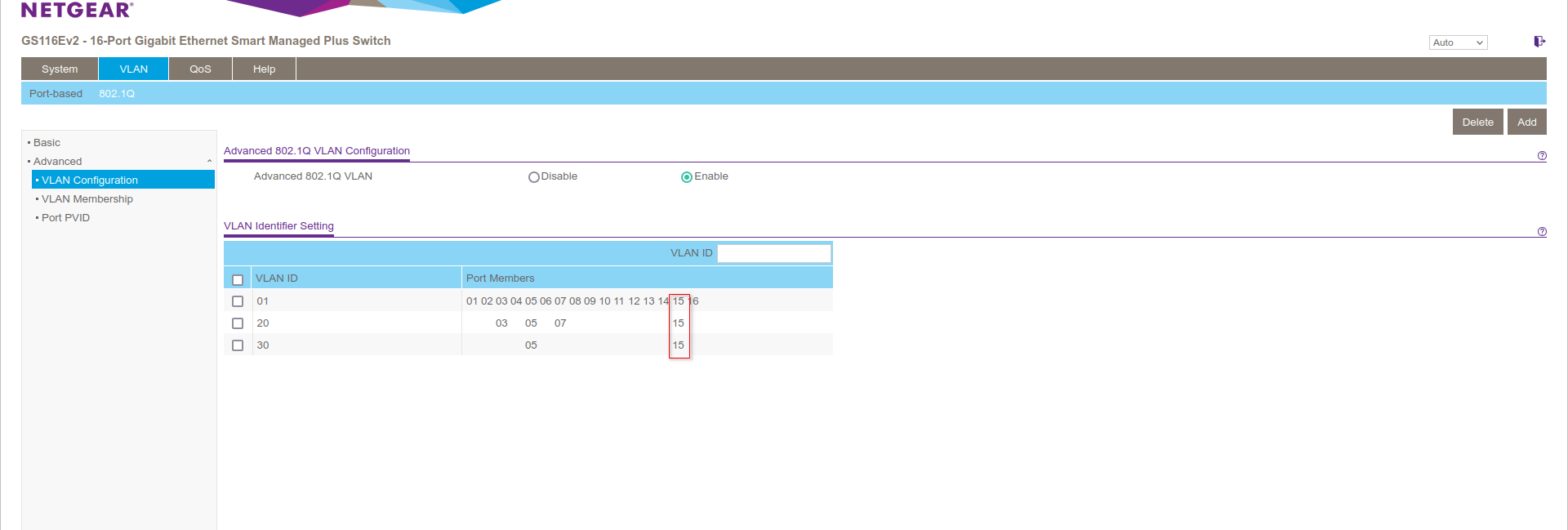
01 is VLAN1 which is untagged
20 is VLAN 20 tagged
30 is VLAN 30 taggedThe pcap only captured VLAN tagged traffic, the GUEST interface, and it looked like that was failing?
It appeared as though the priority setting in the switch was in fact filtering the traffic in some way rather than applying tags. Which might well be what it's supposed to be doing in that mode.
Are you able to test that on your switch @johnpoz?I run it like this:
tcpdump -e -i ix2 vlanMaybe that's why it captured only VLANs traffic. Should I redo the tests ?
-
No, that's fine we only want to see the VLAN tagged traffic there since that's what is failing.
The traffic on LAN (untagged in pfSense) still worked fine in 22.05.
-
@stephenw10 said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
No, that's fine we only want to see the VLAN tagged traffic there since that's what is failing.
The traffic on LAN (untagged in pfSense) still worked fine in 22.05.
Yes it worked fine, only VLANs traffic are the problem on 22.05.
-
@stephenw10 let me find that flexHD ap I have laying around... I can then setup its own ssids so sure connected to it on different vlans.. So I don't have to disrupt my current network at all.
Been meaning to fire it up for updating its firmware and testing it anyway - use to be over at my sons house.. Think its in the garage ;)
-
I suspect the high priority setting you applied to port 15 in the switch filtered the
p 3tagged traffic coming into it so the clients never saw the ARP requests.You could repeat it with port 15 set to low and see if ARP replies then come back.
-
@stephenw10 said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
I suspect the high priority setting you applied to port 15 in the switch filtered the
p 3tagged traffic coming into it so the clients never saw the ARP requests.You could repeat it with port 15 set to low and see if ARP replies then come back.
Do you want me to set any priorities to other ports like port 5 where the AP gets connected?
Also should I set VLAN 20 priority to 3 in pfSense, or should I work only with the switch now ? -
Well you could do either, or both.

But I would do one thing at a time and see what changes.Of course even after we understand what the switch is doing that doesn't really help us know why it fails in 22.05 since the mirror port didn't show VLAN0 tagged traffic.
-
@stephenw10 said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
Of course even after we understand what the switch is doing that doesn't really help us know why it fails in 22.05 sinc
At least you and @johnpoz are trying to help. I appreciate that.
I will redo the test as you suggested, only that the low setting was the default one. -
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
I will redo the test as you suggested, only that the low setting was the default one.
Ah, interesting. Well an alternative might be to leave the switch port 15 set as 'high' and set the prio tag in pfSense to 7. I would expect that to then pass.
-
@stephenw10
First test, only set the low priority only on the switch(the default one), on port 15. I did not touch pfSense.I got this:
low_priority_on_switch_only.txtSecond test:
- Set VLAN20 priority to 3 on pfSense
- Set low priority on the switch to port 15
I saw p3 and p0 now.
pfsense_and_switch_set priorities.txt -
@stephenw10 said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
I will redo the test as you suggested, only that the low setting was the default one.
Ah, interesting. Well an alternative might be to leave the switch port 15 set as 'high' and set the prio tag in pfSense to 7. I would expect that to then pass.
This is what I got with VLAN 20 priority set to 7 in pfSense and High priority set to port 15 in the switch.
high_priority.txt