Captive Portal breaks policy routing for bypassed MAC addresses after upgrade to 22.05 [fixed]
-
@bitrot Yep. We won't be updating to 22.05 and patching. We'll wait.
-
@bitrot Sorry..
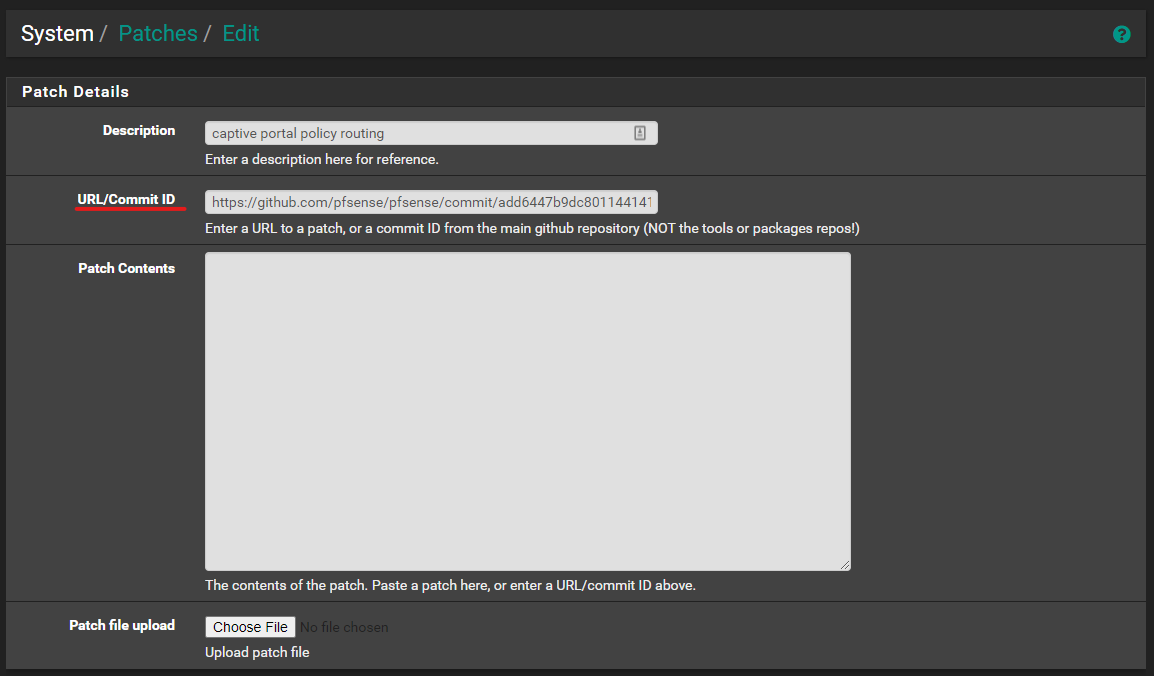
the patch file 13323.patch is different from patch https://github.com/pfsense/pfsense/commit/add6447b9dc801144141bb24f8c264e03a0e7cae
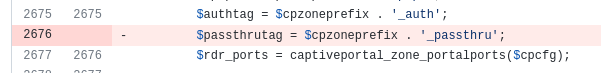
and in the patch file:

Luca
-
-
@bitrot OK applied https://github.com/pfsense/pfsense/commit/add6447b9dc801144141bb24f8c264e03a0e7cae
but before authentication it is not possible to reach the DNS (the firewall itself that acts as a resolver). The same configuration with version 22.01 worked correctly.
In addition, the console displays:
-
@luca-de-andreis
I think your other two issues are unrelated.
Here's the bug report for the dummynet message in your console: Bug 13290 -
@bitrot The criticality is that if the captive portal is active, the client correctly acquires IP, GW and DNS, but does not have DNS resolution, consequently it cannot proceed with authentication via the captive portal.
The same configuration worked perfectly with previous releases, nothing was touched. -
@luca-de-andreis said in Captive Portal breaks policy routing for bypassed MAC addresses after upgrade to 22.05 [fixed]:
but does not have DNS resolution, consequently it cannot proceed with authentication via the captive portal.
The hidden 'pf' captive firewall rules are allowing TCP/UDP incoming traffic on port 53 on its interface. A working DNS is mandatory for a working portal.
What are your GUI firewall rules on the captive portal interface ?
When you connect to the captive portal, without logging in, you should be able to dig, nslookup etc.
When logged in, run the ifconfig or ipconfig /all command and check your IP, mask, gateway and DNS. The last two should be the IP of the captive portal.Also check and double check that the resolver unbound is actually listening on the captive portal's interface. A command on pfSense like :
sockstat -4 | grep ':53'should say :
unbound unbound 18042 3 udp4 *:53 *:* unbound unbound 18042 4 tcp4 *:53 *:*which means unbound is listing on every existing ( == 'All') interface on pfSense.
-
@gertjan Thanks for the detailed explanation ...
Look ... I'm done talking to TOC support now, call code 1006603521.
I am truly speechless.
Yesterday I updated PfSense I tried the captive portal and it worked, shortly after it stopped working and I left it disabled (after restarting the service several times) so that users could still use that network segment.
Now I get TOC support into the system, enable the captive portal and ... IT WORKS.
Tried with disposable code, tried with whitelisted MAC, it works as expected ... and I haven't touched a comma if it doesn't enable / disable.
I left the ticket pending, let's see how it behaves. Really, I have no words, thank you!
-
@luca-de-andreis
I understand you are upset about this problem but why are you hijacking my post with your issue that is completely unrelated instead of creating your own post and/or bug report? -
@bitrot you're right, I thought of doing it, but then for the hurry and thinking about the same problem (at least yesterday) I wrote here, sorry.
-
Wow pfSense! The last working version of pfSense with Captive Portal is still 2.5.2!
This was the fifth time that I tried to upgrade my pfsense, and Captive Portal is still broken.
You should maybe fix it before going enterprise with Netgate payments.Does anyone know if this works on opensense?
It may be time to move on now. -
@pieter_sa said in Captive Portal breaks policy routing for bypassed MAC addresses after upgrade to 22.05 [fixed]:
Wow pfSense! The last working version of pfSense with Captive Portal is still 2.5.2!
What ?
Let me check ...... no, you check me : please visit this link.It works. I was using all the versions up until 2.6.0, and now 22.05.
I can't afford to shut down of have issues with our captive portal, it's used for a hotel, and we have tourists here, not the most patient type of portal users.
True, 2.6.0 had an issue, but was patchable very quickly. It was a two click solution.The issue
Captive Portal breaks policy routing for bypassed MAC addresses after upgrade to 22.05 [fixed]
is marked fixed, I'm not sure if there was even an issue.@pieter_sa said in Captive Portal breaks policy routing for bypassed MAC addresses after upgrade to 22.05 [fixed]:
You should maybe fix it
Can you give more details ? Fix what ? Bug report ?
@pieter_sa said in Captive Portal breaks policy routing for bypassed MAC addresses after upgrade to 22.05 [fixed]:
Does anyone know if this works on opensense?
If you - and me, and others, don't know what the issue is, then no one can tell.
It takes a couple of minutes to find out ... ;) -
@gertjan The frustration with this thing is getting to me.
I am on 22.05 with Captive Portal and Suricata.
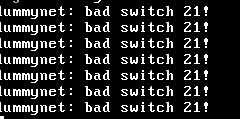
So the moment I enable Captive Portal, the "Dummynet: bad switch 21!" messages start popping up in console.Earlier today my internet connection dropped, with pfsense showing my WAN as down. I checked the router, rebooted it for good measure, problem persists, then I rebooted pfSense, and everything came up again.
The logs showed this:
Jul 26 12:14:05 kernel sonewconn: pcb 0xfffff800b1b20300: Listen queue overflow: 2 already in queue awaiting acceptance (2 occurrences)
And a bunch of:
Jul 26 12:14:47 kernel ovpnc1: link state changed to DOWN
Jul 26 12:14:38 kernel dummynet: bad switch 21!
Jul 26 12:14:29 kernel dummynet: bad switch 21!
Jul 26 12:14:19 kernel dummynet: bad switch 21!Captive Portal sort of works with MAC filtering and vouchers, except that it gives random connection issues on Wifi, and the Interface statistics show "Errors Out" 5 for WIFI.
I get mostly problems with UDP, but I have also seen issues opening a web page over WIFI with Captive Portal enabled.I don't know how to further fault find this issue, and I am again looking at doing a clean install of 2.5.2 to get it working.
-
@pieter_sa The issue with Captive Portal mentioned in this thread has been resolved with a patch you can apply to your system. If you have other issues with Captive Portal I suggest you be much, much more specific and also open a separate thread and maybe create a bug report.
-
@bitrot You marked this as fixed, so others, like me, will also go through the entire journey of registering for pfsense+ and updating all the way up to 22.05 just to see the same old Captive Portal issues.
-
@pieter_sa said in Captive Portal breaks policy routing for bypassed MAC addresses after upgrade to 22.05 [fixed]:
@bitrot You marked this as fixed, so others, like me, will also go through the entire journey of registering for pfsense+ and updating all the way up to 22.05 just to see the same old Captive Portal issues.
No. I found an issue with Captive Portal in 22.05, made a post about it, troubleshot it, and created a bug report about it. Once a patch was available I linked it and marked the issue as fixed.
The other issue you've mentioned is Regression #13290: dummynet. This is a cosmetic issue only that does not affect functionality and is also already fixed.
If you have some other "same old Captive Portal issues" I again suggest you be much, much more specific and also open a separate thread and maybe create a bug report that deals with your specific problems instead of hijacking another thread that is about a different issue that has already been fixed.
-
A adnan97 referenced this topic on
-
A adnan97 referenced this topic on