Site2Site Not Quite Working
-
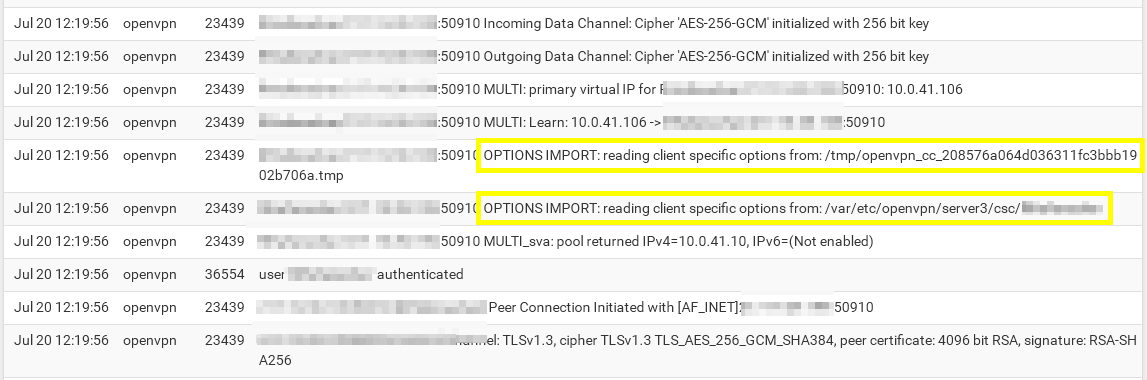
As mentioned, check the OpenVPN log on the server to find out if the CSO is applied properly.
The above mentioned settings were input into CSO, and saved. Not sure what else to do. I don't see anything in the log to confirm CSO is applied
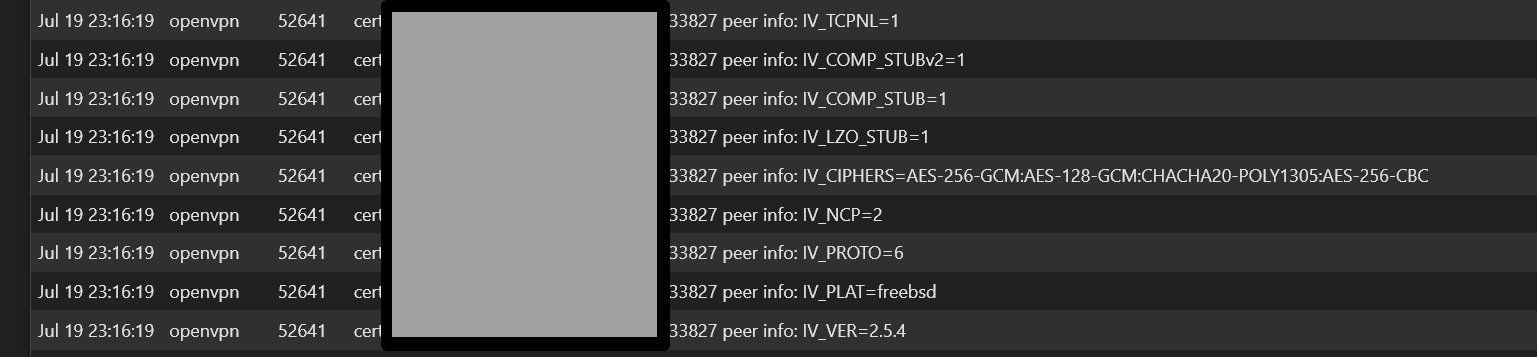
server OpenVPN log shows the following, repeatedly:
Firewall Rules on both server and client for OpenVPN:
Pass IPv4 Source: * Destination: *On server, firewall rules for LAN include:
Pass IPv4 Source: *, Destination 192.168.12.0/24 Port:* Gateway: * -
Some more information on this in the log?
I don't see anymore information regarding this in the log.
-
@ximulate
Okay, even noticed that the CSO part is not logged with default log level.
So I changed the log level in the server setting to 3, then I got the info:
-
@viragomann
Client side OpenVPN log, at verbosity 3:
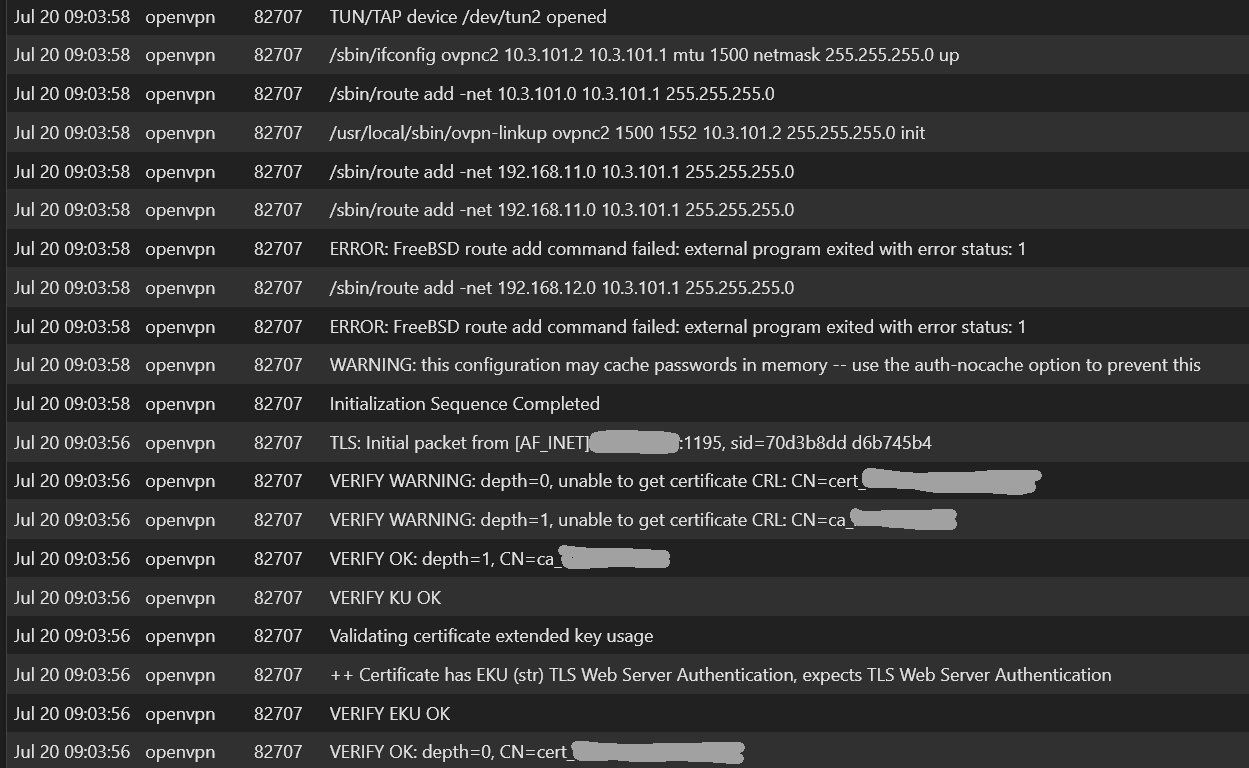
two things stand out to me:
Error: FreeBSD rout add command failedI see this warning on the server side OpenVPN logs also:
Verify Warning: unable to get certificate -
@ximulate said in Site2Site Not Quite Working:
Client side OpenVPN log, at verbosity 3:
The server log is way more of interesting here. The CSO part can only be found in the server log.
Error: FreeBSD rout add command failed
This is due the server is pushing a route for the clients LAN network, which cannot be added naturally.
That's why I don't like this setup method as mentioned above. I'd rather add the remote networks in the client config.
However, it should work anyway.Verify Warning: unable to get certificate
The whole warning says "Verify Warning: unable to get certificate CRL" (Certificate Revocation List).
This is normal. The client complains that he cannot pull the CRL, since it is not provided in the internet. -
@viragomann
One the Server side verbosity 3, I'm now see this:
-
@ximulate
Need to see the section, when the client establishes the connection. -
Server side logs (after reboot of client router)...
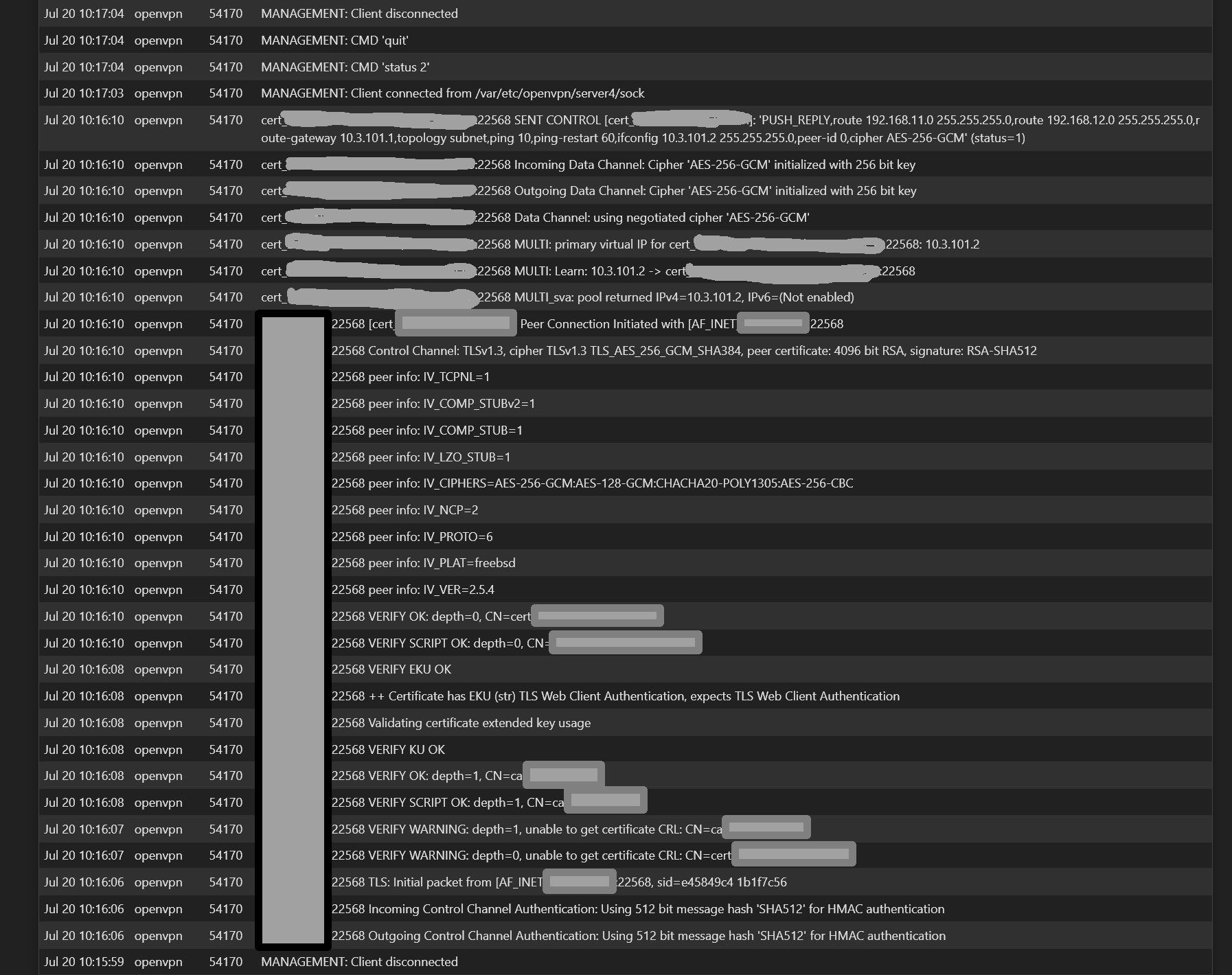
At
Jul 20 10:17:04, MANAGEMENT: .......Those management messages repeat as shown in previous post
-
@ximulate
So there is no note of the CSO in the log. Hence the route within OpenVPN won't work.As mentioned above in post #8 check if the common name in the CSO and server settings are correct.
-
@viragomann
That was it! Its now working. Thank you for your help and patience