Parent Interface Config for VLANs
-
Apologies for this newbie question, but hopefully a simple one to answer!
When setting up VLANs on a parent interface, does the parent interface require an IP address itself? My assumption is no unless you are / need to address it directly.
Also, does it require any firewall rules to allow traffic to pass through it? Again my assumption would be no unless you are passing traffic through it.
So I think that the parent interface has neither an IP address assigned nor firewall rules created for it if it is only used to "host" the VLAN's required, and that Interfacer IP addresses are created for the VLAN's as well as the firewall rules.
Is my understanding correct?
Thanks in advance for any and all help and advice!
-
@lees
Your assumptions are correct.
I have not even assigned a pfSense IF , to my VLAN parent IF'sParent IF "could" also be known as the "Untagged or Native IF"
As it would be the IF that receives "Untagged frames" on that "wire"./Bingo
-
@bingo600, I know this is a little old, but your answer gets very close to what I'm wondering...
I have pfsense configured with several VLANs and I too am wondering what to do about the parent interface.
Currently, I have all my devices attached to various VLANs and everything seems to be working as I'd hope. However, I continue to see activity in my firewall and other logs indicating that the interface is still involved somehow. In particular, in my firewall logs, it claims to be blocking connections on LAN between two nodes that are on different VLANs. This doesn't seem to matter, but it clutters the logs and makes me think I still don't have this configured correctly.
I've not given the base interface (LAN) any IPv4/6 configuration. I tried disabling it, but that turned off all the VLANs associated with it (which is ALL my internal network).
You indicated that you haven't even assigned it a pfSense IF... You mean in the Interfaces -> Assignments page, there is no "Network Port" assignment for the parent interface? Do you have VLANs associated with that physical interface? Removing (or never creating) the pfSense IF assignment doesn't affect the associated VLANs?
Not sure if this matters, but when I initially deployed my pfSense router, everything was on the LAN interface. I created VLANs and moved devices around to place them on the correct VLANs/subnets. Now, I'm just trying to make sure I've gotten everything buttoned up appropriately.
Thanks for any insight you can provide. Based on your remark, I may just try deleting the IF assignment and see how it goes. Hopefully, the backup/restore from the console thing will save me again if it doesn't work.
Thanks
Marty
Gloucester, Virginia, USA -
@martywise said in Parent Interface Config for VLANs:
However, I continue to see activity in my firewall and other logs indicating that the interface is still involved somehow.
Could you post screenshot of this, an example of what your seeing.
Just because you don't have IP assigned to the interface, doesn't mean the interface can not see traffic. If untagged traffic comes in that interface,
-
@johnpoz -- Entries like these...
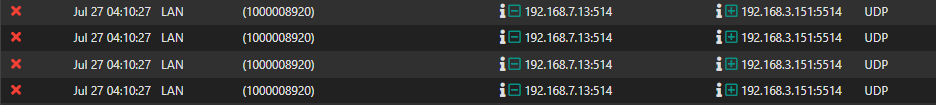
My 192.168.7.0/24 is my management VLAN, and 192.168.3.0/24 is my internal servers VLAN. These devices are communicating with one another just fine, but I'm seeing these log entries. And, the only FW rules I have on the LAN interface is the "anti-lockout" rule applied by pfSense.
Thanks for your speedy response!
Marty -
@martywise So vlan 7 and 3 lets call them are tagged.
If traffic comes into the lan interface and is untagged then yes it would show like that.
If the traffic was tagged then it would show your vlan7 or 3 interface as the interface it was hitting.
You need to figure out how untagged traffic is going to your lan interface..
edit: what switch are you using? If tplink could be leaking vlan 1 traffic - they use to have an issue where they would not allow you to remove vlan 1 from an interface.
The port on your switch your lan interface of pfsense is connected to should only allow tagged vlan 7 and 3 traffic (and any other vlans you might have setup).
How are these 7.13 and 3.151 boxes connected to the network? Wired, wireless?
-
@johnpoz
Aah.. OK. Well, the 7.13 node is one of my access points. So, it has "all" vlans going to it. But, its management interface is on the 7.x vlan. The other node is a VM running in hyper-v that is running my unifi network application. The hardware is ubiquiti -- 2, 16 port switches and 2 APs. One switch connects directly to the LAN interface on my pfSense box and is configured for "all" vlans. The AP is connected directly to that switch. The VM is on a Windows box that runs my NVR software. Hyper-V has a dedicated interface I use for the VM that is VLAN aware, and the VM is assigned to the single VLAN. The main interface to the NVR is separate.When I started writing this, I thought I was beginning to see what was going on. But, by the time I was finished, I had lost it. lol.
Thanks a ton for your help.
Marty -
@martywise said in Parent Interface Config for VLANs:
Well, the 7.13 node is one of my access points. So, it has "all" vlans going to it. But, its management interface is on the 7.x vlan
And what AP is that? The unifi ones for example love management to be untagged.
is configured for "all" vlans
What does that mean exactly? Again untagged traffic is going to show as hitting the lan interface be it you have a network setup on it or not... Untagged traffic is the native parent interface, tagged traffic is the vlan interface. If there is no tag on the traffic then it will be hitting your LAN..
If your not wanting to use a network on the parent native interface then you have a issue with your setup because untagged traffic is hitting your interface..
-
@johnpoz wow. I'm definitely confused.
Here are a few more details... So, my access points are both Ubiquiti U6-Lite. I also have 2, 16 port Ubiquiti USW-Lite-16-POE switches.The first switch is connected directly to the LAN interface on pfSense. On this switch, this uplink port is configured with a port profile of "All". The port profile allows me to select between All, None, or any of the VLANs I have defined. It will not allow me to select multiple VLANs other than to select "All".
The access point in question is connected to the same switch (with POE) and the port to which it is connected is also configured with the "All" port profile.
On both of these devices, their "Management VLAN" is set to my management VLAN (the 192.168.7.xxx addresses).
The AP has 4 SSIDs configured on it, each connecting to a different VLAN (guest, general purpose, security cams, IoT, etc.). This AP has the 192.168.7.13 IP.
My understanding is that these ports that are configured for "All" basically just ignore the VLAN tags and forward everything, assuming something downstream is going to use the tags to split the traffic. In the case of the AP, it applies tags to traffic connecting over any of the 4 SSIDs to the configured VALN for each.
And, other ports on the switch are configured for individual VLANs depending on what is connected to them. This includes a pair of rPis that run my DHCP and DNS Services, one that runs my monitoring system, syslog, etc., HASS, SmartThings hub, etc. And... a couple of ports that connect to downstream switches are also configured for "All" and so those ports ignore the tags and pass all the traffic. Again, so that a downstream switch or AP or whatever can apply the tags appropriately.
In the case of the VM running on the 192.168.3.151 IP, the port to which the PC is connected is also configured for All. This port is dedicated to a virtual switch on the PC in Hyper-V that lets me place individual VMs onto that vSwitch, specifying a VLAN tag to be used for each VM. In this way, I can put VMs on whichever VLAN I need to.
Since the LAN interface on my pfSense box is connected to an uplink port on the switch configured for "All", I would guess I would expect to see all traffic on the LAN interface, even though it has no specific IP or VLAN association itself. Then, in pfSense, it splits the traffic up by VLAN, onto each of the virtual networks I've defined.
But, clearly my understanding is wrong. From your comment, I'm guessing that pfSense really does get all the traffic as I'm describing (it has to, right?), it just shouldn't be treating any of it as "belonging to" that interface since it's tagged, so it shouldn't be turning up in Firewall rules for that LAN interface. Does that sound about right?
I ran a packet capture on the LAN interface and if I look at it in Wireshark and filter by "!vlan", it shows me about 0.1% of the traffic. Most of it seems to be layer 2 XID and STP traffic which I guess I would expect? But, there are a few packets with IP addresses between the two nodes I mentioned (as well as the other AP on the network) that seems to be udp syslog traffic from the APs back to the Unifi controller on that VM.
So, it seems these APs are not tagging their syslog traffic for some reason (I do not see any VLAN tags in the packets), and that's what's leaking onto the LAN interface?
I'll check on those APs... maybe reboot them. I am pretty sure they're up to date. After a reboot, I can use the packet capture again to see if anything has changed/improved.
So.. back to the original question... I was wondering what to do with the parent interface in pfSense... It should be left on/enabled, but with no IP/IPv6 config on it as I have done? The traffic I am seeing that made me ask is actually due to a different problem. But, my basic config of pfSense is correct?
I did a lot of networking back when we did it with coax and bridges and used the term "subnet". This exercise with pfSense has been extremely interesting. Thanks so much for taking the time to assist.
PS -- No change after rebooting the APs.
I hope you have a great day.
Marty Wise
Gloucester, Virgina, USA -
@martywise have you tried to reconfigure the native lan for the port connected to your pfsense box. You could make the native lan of the switch trunk port different than the rest of the switch so it doesn't pass data other ports having same native vlan