(22.09) OpenVPN S-S TLS with /24 tunnel and Client Override
-
Posting in 22.11 section for 22.09 dev build.
This broke in 22.05.
After hours of frustration on the live system I built a lab setup for debugging.Following THIS recipe:
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
following exactly - except one client only and different IP's obvs.Installed on 22.01 - works.
(tested the same setup with a PSK, TLS with a /30, and TLS with /24 and client overrides - as in the example) All successful.Upgraded system to 22.05. - Recipe Fails. Gets:
server:
"AEAD Decrypt error: cipher final failed"
client:
"Authenticate/Decrypt packet error: packet HMAC authentication failed"
in logs.
Nothing I have tried works including diddling with almost every option available. Note: DCO has been OFF entire timeUpgraded system to 22.09. - Recipe Fails. Gets same error.
In 22.05, the same setup with a PSK or TLS with a /30 tunnel work.
As soon as you add the /24 tunnel and client overrides, it gets the log errors as shown and will not connect. -
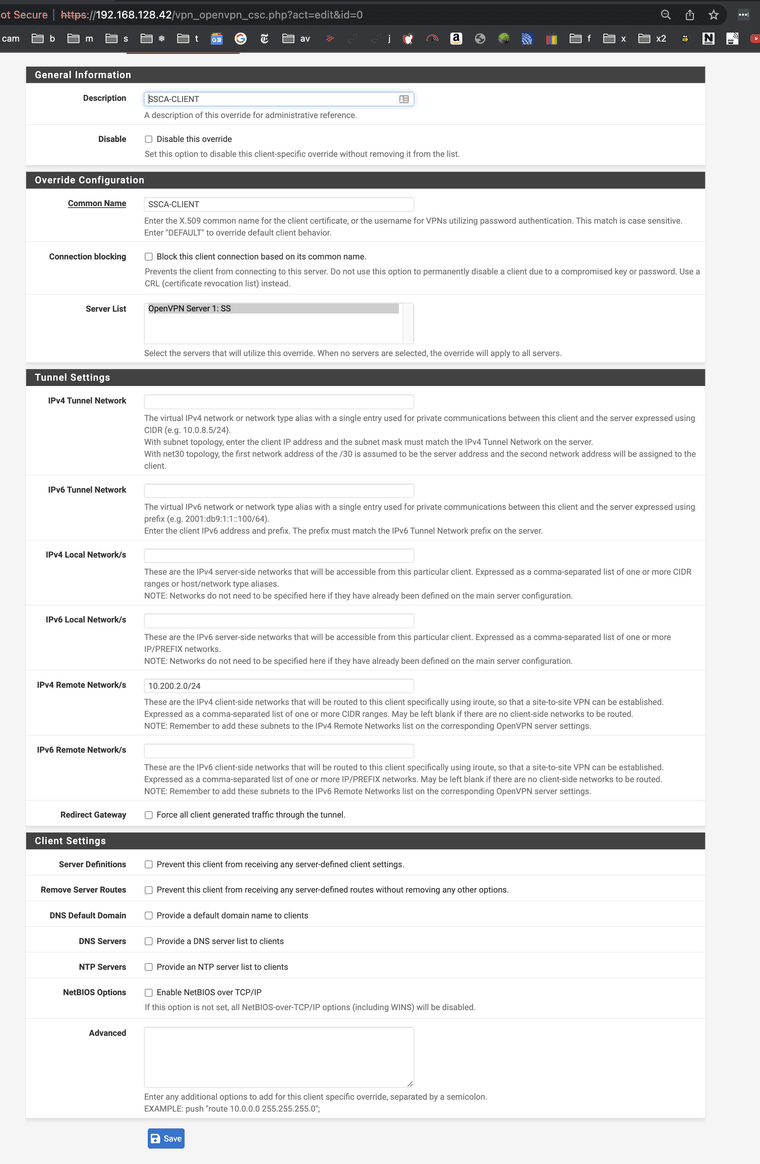
What client override are you setting?
-
@stephenw10 Following the recipe exactly.
In this case only setting the cert CN and the Remote Lan subnet.
-
@swixo FWIW - I am maintaining a reproducible (not production) test environment for this, so if you want me to test any changes...
-
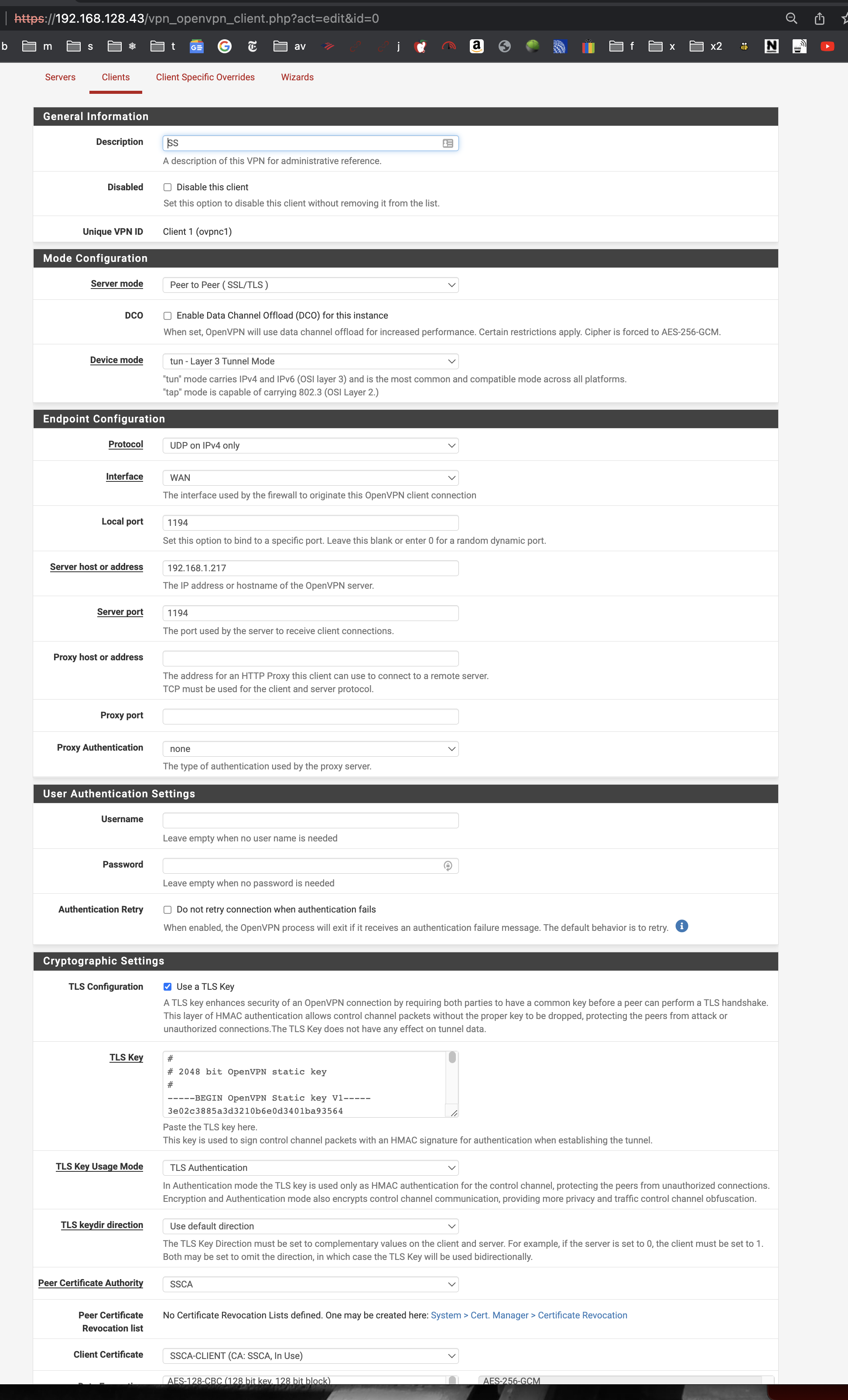
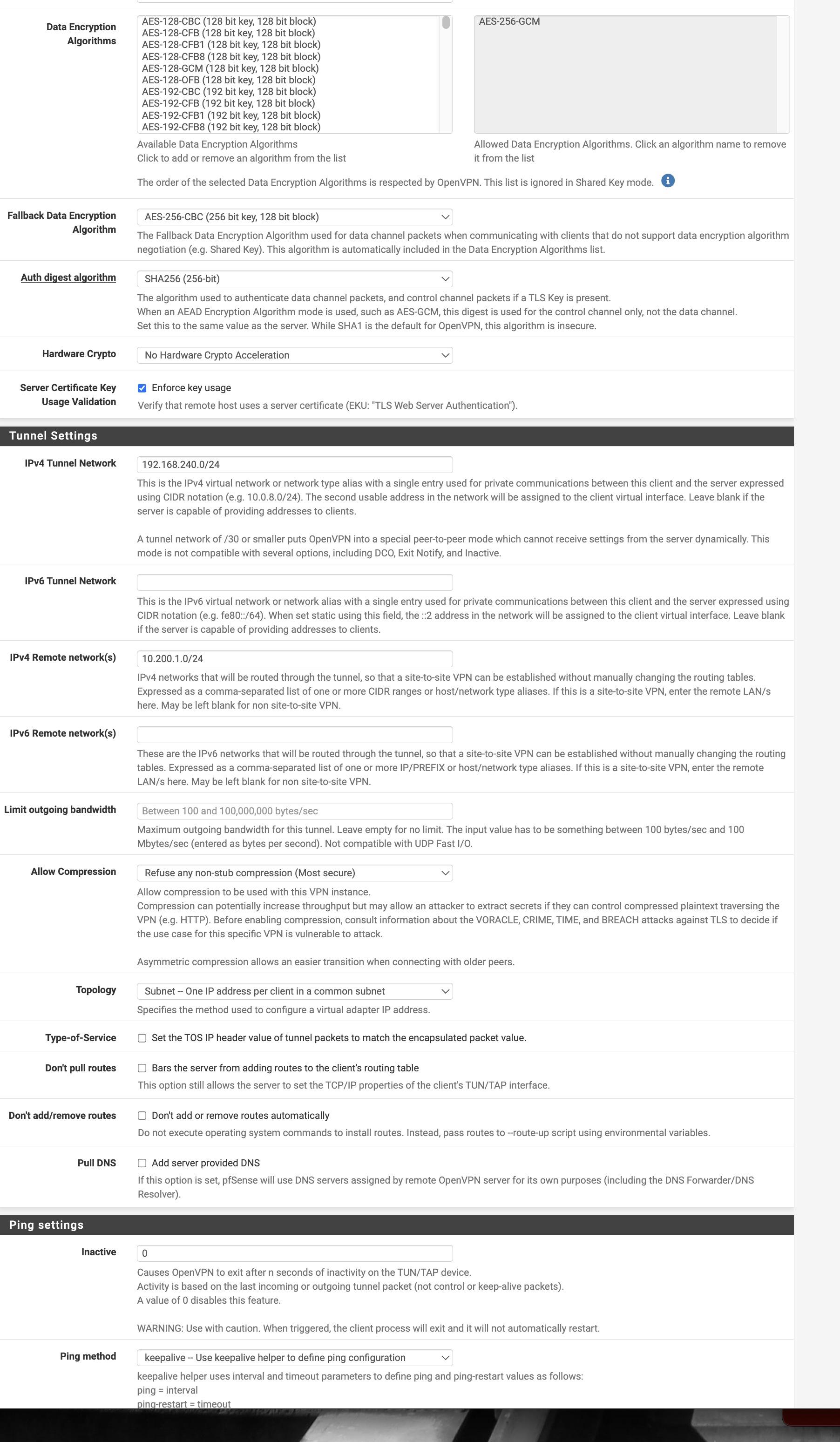
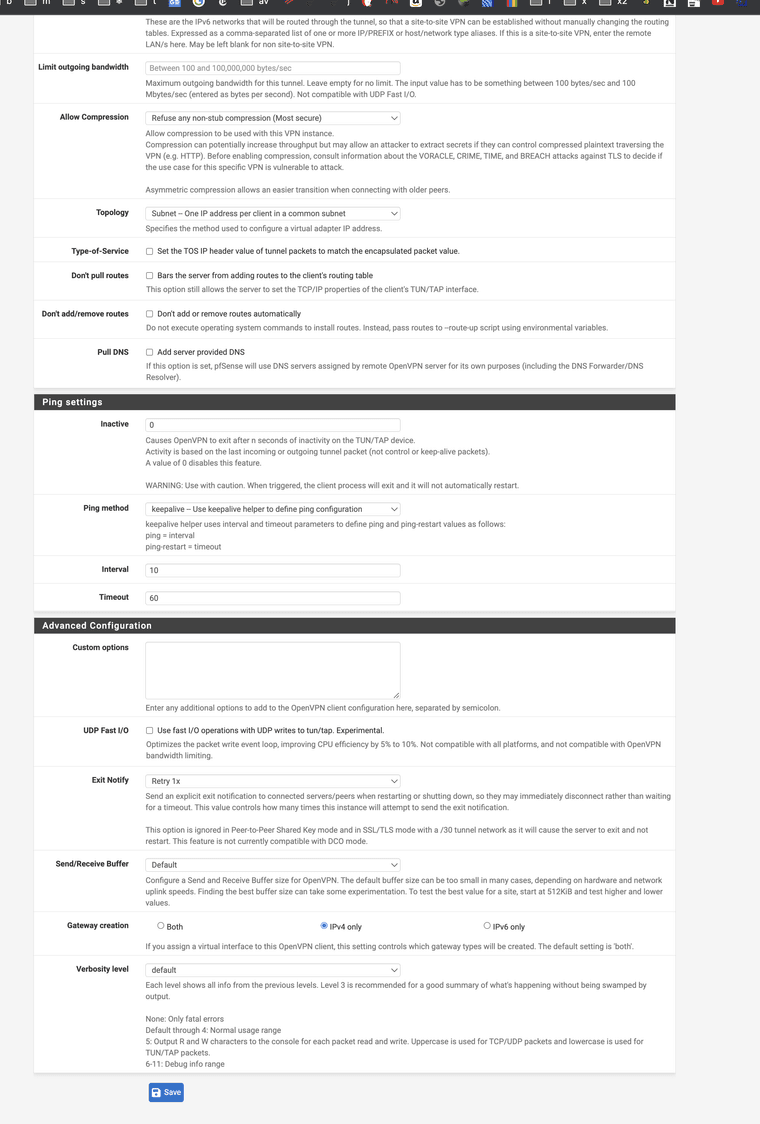
Post screenshots of the server, override, and client config. You can mask out the start of the IP addresses but leave enough to tell what is what.
-
No need to redact. These two instances of PF are running on servers in my lab, and use RFC addresses. We're simulating the arrangement.
The instances are "connecting" just fine - but no data flow, exactly as it was on the production system using actual internet between boxes.
This exact config worked fine in 22.01.
Server:
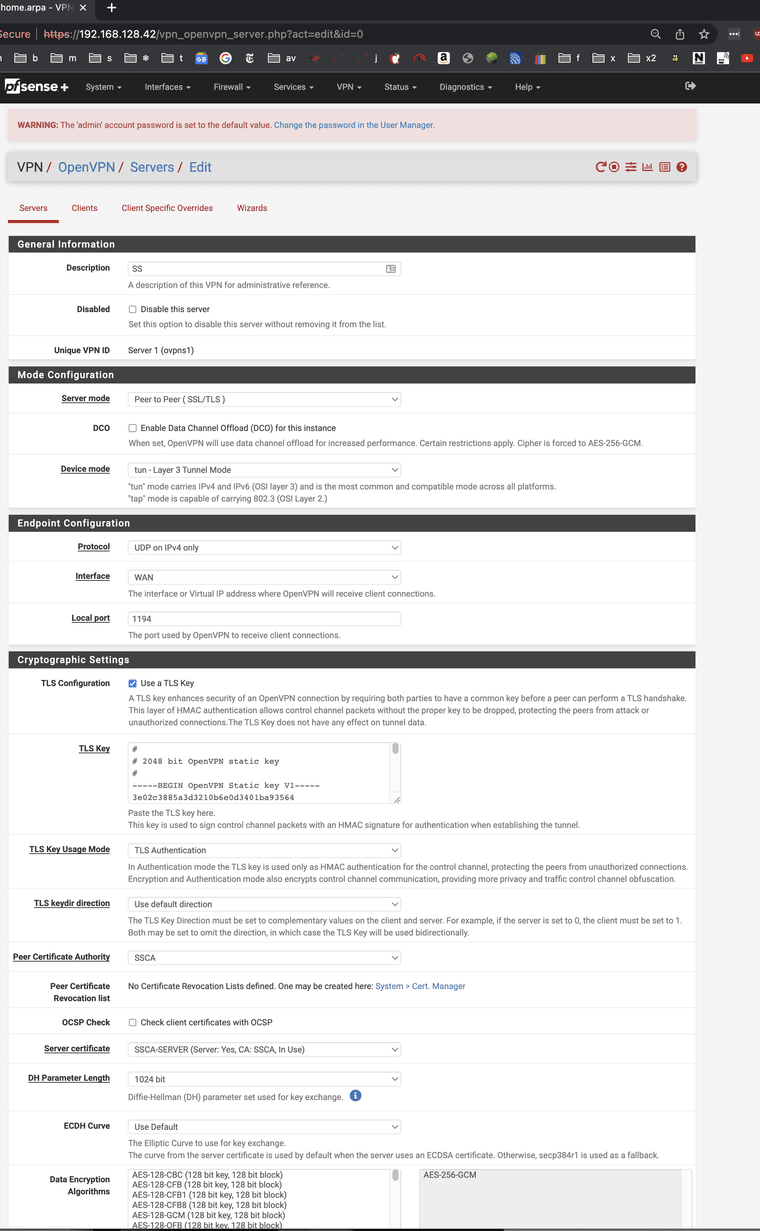
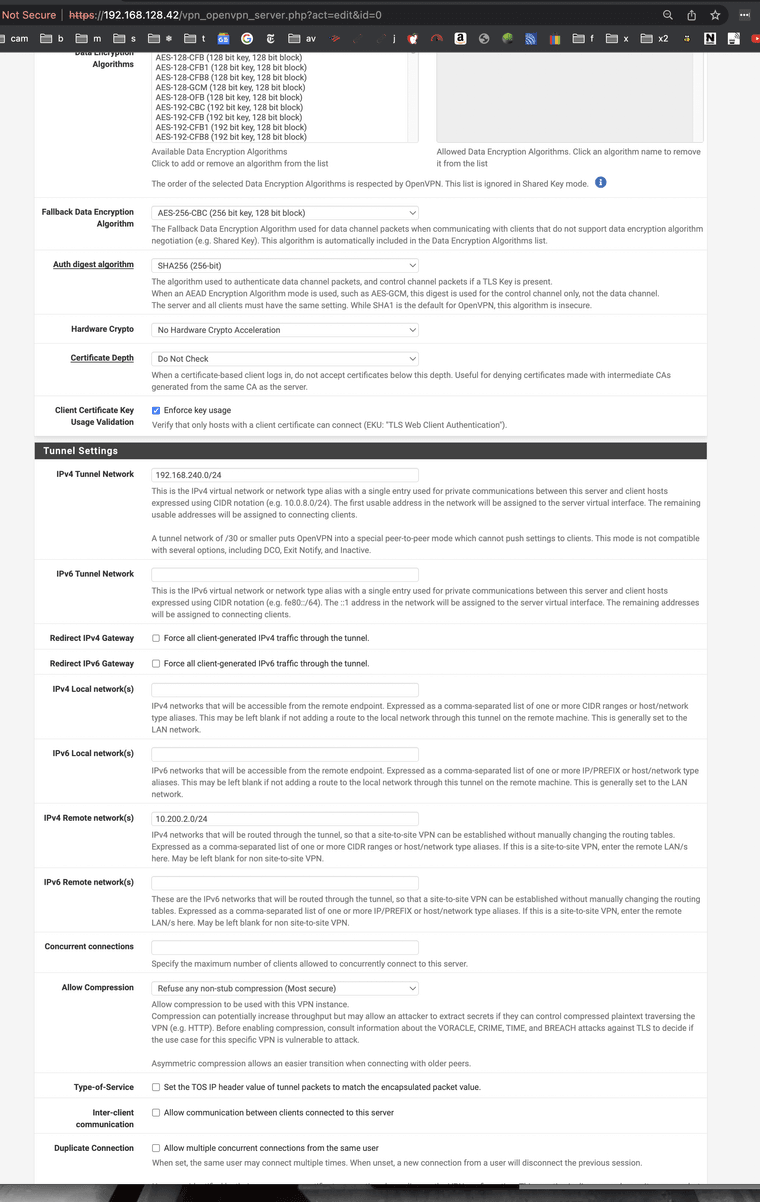
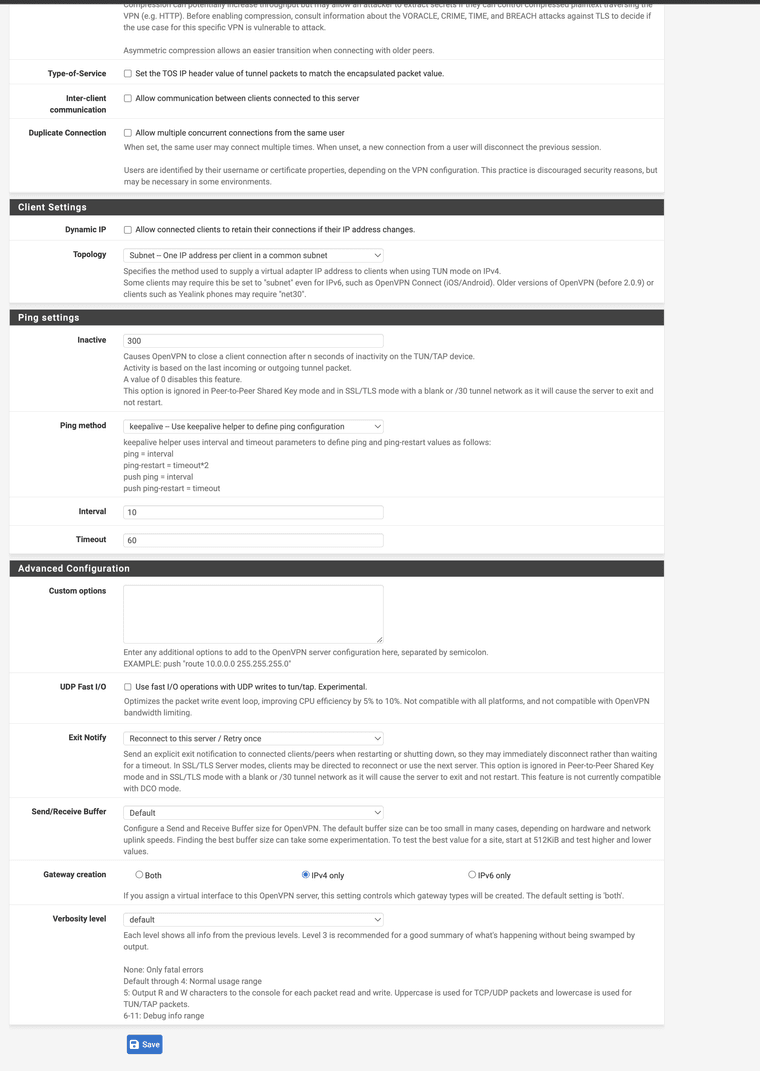
Override:
Client:
-
Remove the tunnel network from the client. It is unnecessary (server will push it) and is a known source of problems.
The recipe you followed doesn't say to set that either.
-
@jimp
Hi Jim - thanks for the update. My only saving grace - it did work before! I probably put that in there on auto-pilot. Thanks