Source Address is getting translated when transversing tunnel
-
I am having this same problem. Any update on this?
-
@meluvalli Shouldn't happened if you make it this way.
-
@siwatsirichai
If you check your NAT outbound rules you will see ta raffic rule for it to get NAT;ted to the interface of the WG tunnel on your pfsense. Under the WG interface make sure that you do NOT have a gateway selected. Having a gateway present is one of the conditions that pf uses to create automatic outbound NAT rules. If you leave the gateway blank and also have static routes to the WG gateway that you create (you need to create) than the far side will see the Real IP of the client. -
@bob-dig
Thanks! This solved my problem 26 minutes later! HAHA!For those that also have this issue, make sure on the interface, you select "none" as the gateway. This will prevent NATing :)
@bob-dig, great video though!
-
@bob-dig
Update:
While this did solve the problem, it created a new problem :(....I currently have my setup to NAT from Site B to Site A Internal client.
I changed my outbound NAT on Site B to my Site A Network. (It was pointing to my tunnel Network before).
However, this doesn't seem to fix it. The only way I can go from SITE B-WAN to SITE A Client is if I use the upstream gateway. Any idea how to resolve this?
-
@meluvalli I can't follow what you are doing exactly.
-
I actually got it working a while back, I just create a DO NOT NAT entry manually for my internal network
Site A: 192.168.0.0/24
Site B: 10.16.6.0/24Site A DNN Configuration
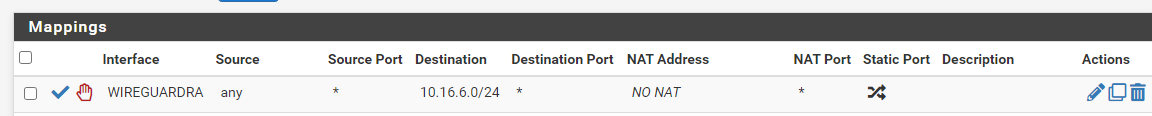
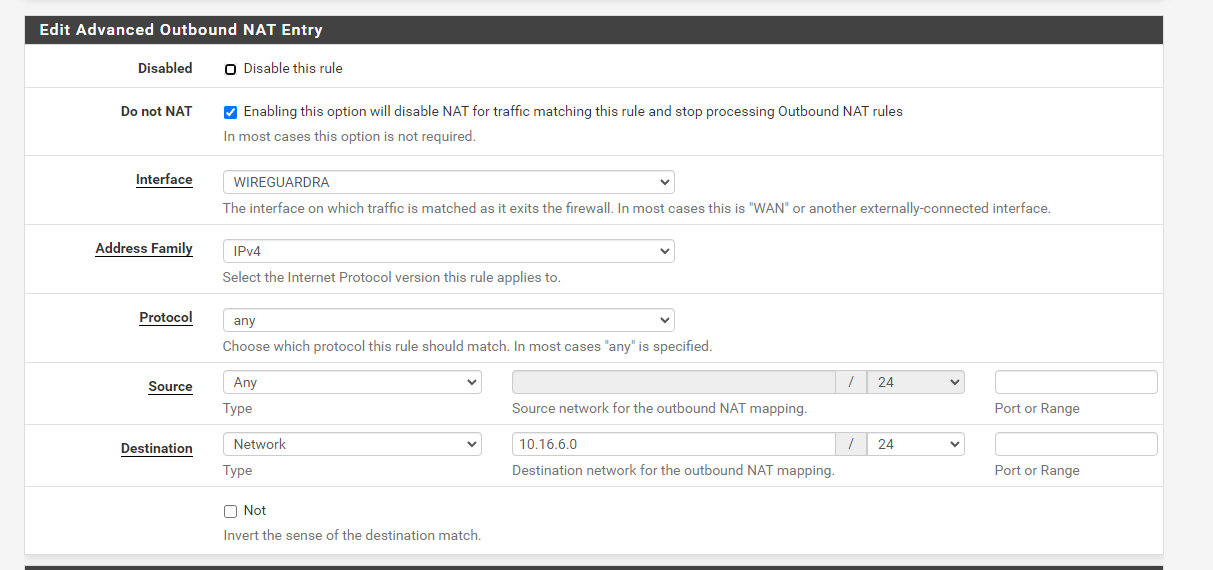
Site B DNN Configuration
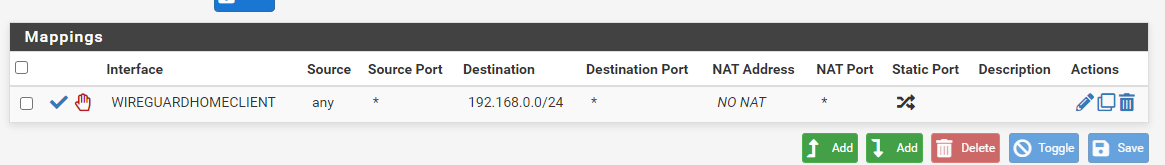
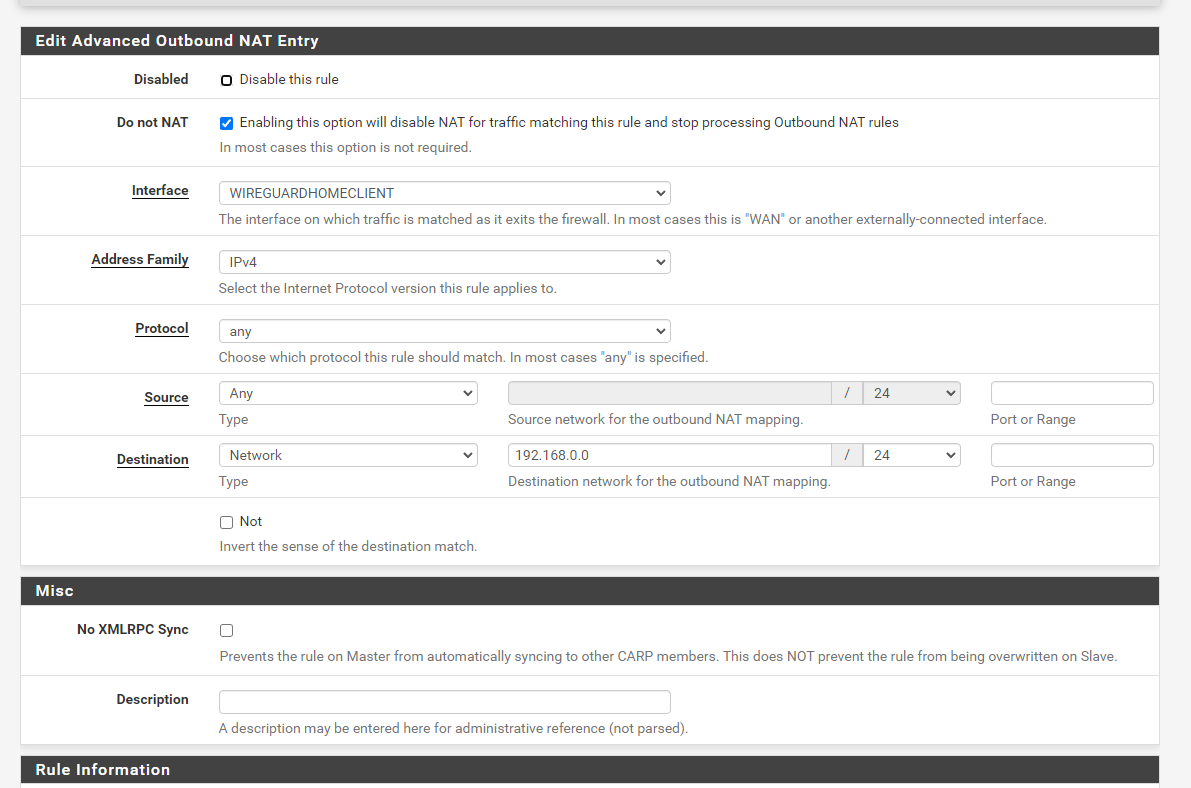
Note that I'm basically saying that any traffic from B that's going to A must not be translate, note that the the configuration will have the destination of the remote network but not the local network because Outbound NAT basically translate traffic that coming out of a specific interface, this is done at the originating router (internal IP to VTI IP). -
@siwatsirichai
So to confirm, you left upstream set on the interface (WIREGUARD Interface) and just added the NONAT rules for outbound? -
@meluvalli
Site A have no gateway, Site B,C,D,… have site A as gateway, as this is a site-to-multisite configuration. -
@siwatsirichai
I think you are handling this wrong but depends on your use case.Site B,C,D will have the real IP of the client natted - Assuming this is what you want.
If this is not what you want, then have no gateway configured for the WireGuard Interface at site B,C,D. You then need to create a gateway at each site and for each site then you utilize static routing.
-
S Sn3akerz referenced this topic on