Firewall Rules - Interface
-
@bob-dig many thanks! Makes perfect sense now

-
@lees you understand there are 3 places there are drop downs when you create a rule - it defaults to the interface your on when you click add..
The top one - but there is also source and destination
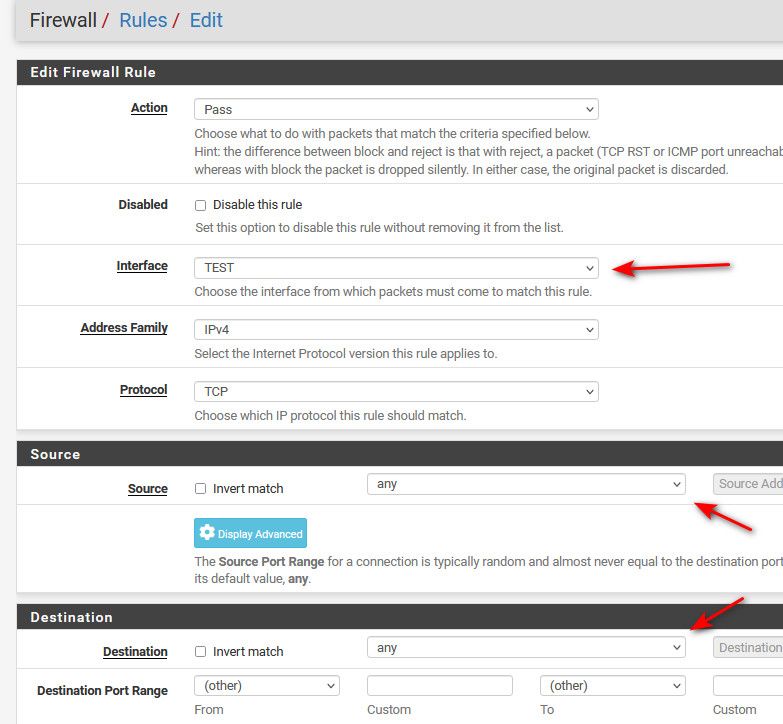
Yes if you change the top one it will put the rule there, because your specifically calling out what interface to put the rule on.
Thought you were talking about the source and destination drop downs.. You can put a rule on optA, but have source be optX - which would almost never be correct.
Thought you wanted to have the drop down filter your source to only be the interface your creating the rule on vs presenting you the full list.
But if was creating an outbound rule in floating you could end up with source different then the interface.
-
@lees Flush the state table after ever firewall rule change while you're getting used to this to completely rule this out. It adds about 10 seconds onto ever tweak you make, but it saves way more than that debugging cached rules (aka. state table). There are ways to flush individual rules too, but it takes longer than 10 seconds to find them :-)
-
It's been a good discussion has this thread and has helped me as I've been talking through it too.
What is clear though is that the UX is poor. By any standard measure of good UX, pfSense fails miserably. But hey, once you know that it's bad UX and not something you're not understanding it all makes sense.
It's like opening an Xmas advent calendar only to find there is no chocolate behind the door. Good UX is simple, don't have a door.
A good book on good usability, while quite old now, still relevant - Don't Make Me Think by Steve Krug - https://www.amazon.co.uk/Dont-Make-Me-Think-Usability/dp/0321344758
The job of any good developer is to make the system fool proof. No-one should have to know what they are doing, they should be guided at every step.
I don't know anything about floating rules yet, but from what I can tell reading the comments that to me, if I was building the pfSense WebGUI would be to have two admin screens, one for Standard Firewall Rules, and another for Floating Firewall Rules.
The reality is networking stuff is complex, and is an extremely difficult topic to understand if people aren't a traditional network admin and/or have been through the usual courses like CCNA and others etc. I'm pretty sure 'certain' big networking vendors make this stuff difficult to understand on purpose to justify the cost of their hardware.
-
@michaelcropper said in Firewall Rules - Interface:
No-one should have to know what they are doing
That is one of the stupidest things I think I have ever heard.
This isn't a ui to a freaking TV.
-
@johnpoz That's where the world is heading in every aspect of tech whether we like it or not.
The future skills are in building the tools to enable this idiot proof tech. Not in configuring tech.
-
@michaelcropper doesn't matter how pretty or easy to use the UI..
Still have to understand what a source port or IP is and destination IP, what protocol.
Sorry you still have to understand what your doing - even if the gui tries to keep you from shooting yourself in the foot.
Sure they could limit the selection to make it harder to shoot yourself.
See it all the time user puts in source port as 443 and destination port as 443.. That is highly unlikely a valid setup.. But it "could" be valid you have no idea what some application might do, etc.
If they prevent me from putting in 443 as the source port, and I actually want that - then the UI sucks.. So again going back to in what scenario is what valid or correct when there are so many variables..
The operator has to understand what the variables mean..
Poor Engineer blames his tools if you ask me.. It gave me too many choices - I didn't know what to put in ;)
As to floating tab - and where should you put rules that could be on multiple interfaces at the same time.. Where should you put rules that are doing outbound vs inbound. Where should you put rules that are suppose to happen before rules you place on the interface for marking traffic on say multiple interfaces at the same time.
So you call it bad design, I call it not understanding what your doing.. Blaming the tool because you don't know how to do something. But the tool should prevent me from shooting myself, and the tool should make it so I don't have to understand anything - it should just know what I meant to do, and not what I told it to do.. While that works on a TV, do you want to see this channel in the guide or not.. It doesn't work for a firewall.
-
@johnpoz I don't disagree with your point.
Good UX is segmenting UI for the average user which accounts for 95% of use cases VS the pro user which accounts for 5% of use cases which requires the ultimately flexibility.
To put this into context in an area that is nothing related to pfSense. A big green 'buy now button' on an ecommerce store can significantly increase sales over a button that is smaller or less obviously placed on the page which results in reduced sales.
Humans have more important things to worry about when using a system. They know what they want to do, the purpose of any system is to make this as easy as possible for the different users to achieve their goal.
This is the basis of good UX and design in any system.
It's not a case of limiting what people can/can't do, merely giving the user a guided experience to ensure they can achieve their goals as easily as possible.
The reality is that in the networking world in general, the UIs have often been so bad and designed in the early 90s in many cases and updated at best annually or with the next hardware firmware upgrade, that it's kind of the normal and people have got so used to bad design. pfSense is awesome in comparison to some of the horrific user interfaces I've seen on networking hardware. Likewise, this is one of the reasons why Ubiquiti / UniFi has become so popular (still a long way to come, but certainly leading the way).
In the world of web tech, it's normal to see upgrades multiple times per day and A/B experiments to use data to justify changes based on actual user experience rather than individual opinions. In reality, no-one is right, other than the users as a whole and it's so simple to track this stuff these days.
I had a bit of a dig into the change process for the pfSense GUI and it seems that this is quite a slow process for any changes to be made.
-
@michaelcropper said in Firewall Rules - Interface:
A big green 'buy now button' on an ecommerce store can significantly increase sales over a button that is smaller or less obviously placed on the page which results in reduced sales.
Your not ordering a sweatshirt on amazon here for gosh sake..
Example of uses clicking shit they don't understand and not reading - but pfsense should "prevent" this in UI
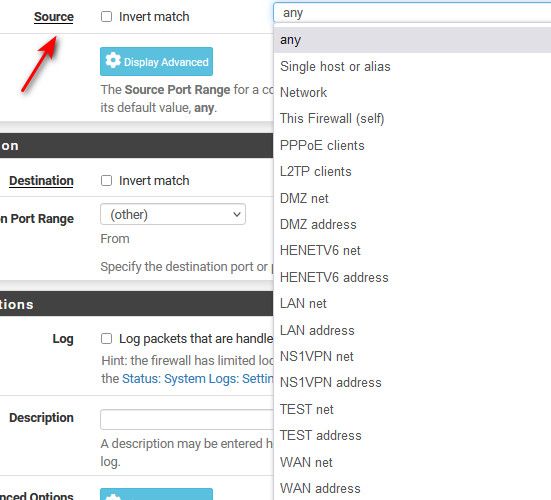
So when you go to create a rule it asks you for source IP or network, range - this is where you have a problem because it lists all the networks on pfsense..
To set a source port on the traffic - you have to clicked the ADVANCED BUTTON, with a warning
"The Source Port Range for a connection is typically random and almost never equal to the destination port. In most cases this setting must remain at its default value, any."
Yes users still seem to open up the advance tab and set the source port from any to the same port as their destination.. my 443 443 example, even though this is a very uncommon setup - it could be possible for that to be a valid configuration.
This this is the UI going out of its way to warn the user - hey you prob don't want to do anything here unless you really know what your doing - still happens... Bad UI, or just bad user?
So again - if you don't know what interface or network you want as source on a rule you are creating - you shouldn't be within 100 feet of the firewall plain an simple.. I didn't know it presented my optX network as source on my Lan network.. That is not UI issue, that is just plain not understanding what your doing or even wanting to do.
They know what they want to do
I would say no they don't know, or they wouldn't be selecting optX network as source into their Lan network, etc. But it happens all the time.. But lets not blame the user of the tool, blame the tool - because the UI should be so easy to use that the user doesn't even know what they are doing ;)
-
@michaelcropper Your right, there is much space for improvement but also pfSense is a firewall appliance for businesses, not a home-router.
-
B Bambos referenced this topic on