Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only)
-
Suricata-6.0.6
Look for a new version of the Suricata package to appear for pfSense-2.7.0-DEVEL users in the next few days. This version includes the latest 6.0.6 binary from Suricata upstream and a number of new features and bug fixes.The 6.0.6 version of the Suricata binary includes some fixes to the Radix Tree code used by the pass list logic within the custom Legacy Blocking module used on pfSense. I am cautiously optimistic this updated Radix Tree code along with some additional changes I made in the Legacy Blocking module code will finally correct the sporadic bug reported by a few users that caused IP addresses on a Pass List to still be blocked.
NOTE - This new version will initially be available only in the 2.7.0-DEVEL branch of pfSense for user testing. If no major issues are reported, the update will be merged into the RELEASE branches of pfSense CE and Plus in a few weeks.
New Features:
- Add MQTT and ENIP app-layer-protocol configuration controls on the APP PARSERS tab.
- Improve the configuration options available in the GUI for the Suricata default events rules on the CATEGORIES tab.
- Add the new ssh-events.rules file to the list of default Suricata events rules.
- Add column sorting and improve the functionality of the BLOCKS tab (used for Legacy Blocking Mode). Redmine Feature Request #12748.
Bug Fixes:
- Fix Redmine Issue #12956 - revert the use of preg_quote() to wrap the user-supplied PCRE argument from the SID MGMT tab logic.
- Fix Redmine Issue #13333 - string passed where an array was expected on the CATEGORIES tab when unselecting all categories.
- Auto-enable Live Rule Swap on the GLOBAL SETTINGS tab whenever an interface is configured for Inline IPS operation. This will keep netmap from cycling the physical interface down and back up each time Suricata is restarted during a rules update.
-
@bmeeks Now testing with v.2.7...
-
@nollipfsense said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
@bmeeks Now testing with v.2.7...
Thanks!
-
Perusing the Suricata.io forum today I found mention of a new bug introduced in 6.0.6. The description is here: https://forum.suricata.io/t/behaviour-change-with-fix-to-bug-5403/2662.
There are also two additional bugs introduced in the 6.0.6 binary that were noted previously on the Suricata Redmine site:
https://redmine.openinfosecfoundation.org/issues/5458
https://redmine.openinfosecfoundation.org/issues/5457 -
@bmeeks said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
Perusing the Suricata.io forum today I found mention of a new bug introduced in 6.0.6. The description is here: https://forum.suricata.io/t/behaviour-change-with-fix-to-bug-5403/2662.
There are also two additional bugs introduced in the 6.0.6 binary that were noted previously on the Suricata Redmine site:
https://redmine.openinfosecfoundation.org/issues/5458
https://redmine.openinfosecfoundation.org/issues/5457Even at least one request to pull 6.0.6 due to this defects.
-
@nrgia said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
@bmeeks said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
Perusing the Suricata.io forum today I found mention of a new bug introduced in 6.0.6. The description is here: https://forum.suricata.io/t/behaviour-change-with-fix-to-bug-5403/2662.
There are also two additional bugs introduced in the 6.0.6 binary that were noted previously on the Suricata Redmine site:
https://redmine.openinfosecfoundation.org/issues/5458
https://redmine.openinfosecfoundation.org/issues/5457Even at least one request to pull 6.0.6 due to this defects.
Yes, saw that request as well.
In my opinion Suricata's code is getting quite complicated and intertwined such that a seemingly innocent change in one module now can have a profound unintended impact in another area of the code.
This is true of almost all software these days. The code is developed in higher-level languages that sometimes abstract critical details and make it harder to see potential errors, and the developers are increasingly composed of teams of folks in different parts of the world. That makes collaboration more difficult -- just the difference in time zones makes contact challenging.
-
@bmeeks said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
Yes, saw that request as well.
In my opinion Suricata's code is getting quite complicated and intertwined such that a seemingly innocent change in one module now can have a profound unintended impact in another area of the code.
This is true of almost all software these days. The code is developed in higher-level languages that sometimes abstract critical details and make it harder to see potential errors, and the developers are increasingly composed of teams of folks in different parts of the world. That makes collaboration more difficult -- just the difference in time zones makes contact challenging.
Isn't this model, also the Linux model? They have developers spread all over the globe. Why for the Linux world is working? Or it's just about the programming language used, like you pointed out? AFAIK the Linux kernel is written in "C".
-
@nrgia said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
Isn't this model, also the Linux model? They have developers spread all over the globe. Why for the Linux world is working? Or it's just about the programming language used, like you pointed out? AFAIK the Linux kernel is written in "C".
This is true, but paradoxically something like the Linux kernel is potentially a bit easier to keep together because it does not need so many capabilities. An IDS/IPS has to be programmed to delve into and decode a bunch of different protocols and inspect the protocol's traffic against thousands of rules. An OS kernel does not have to do all that. Now mind you a kernel is still a complicated beast, and it can appear to be total rocket science and magic to an outsider
 .
.Maybe I'm just being a bit too hard on the Suricata folks. They have just a bit of a rough patch of late with some unintended bugs introduced by both refinements of existing features and the introduction of some new features.
-
With this new 6.0.6 version, is there some good news regarding the extra CPU time used by Suricata 6 vs 5?
It's been talked about in topic 166657, which I can't link because the Submit button throws an error.
And some extra talks on this:
https://forum.suricata.io/t/cpu-usage-of-version-6-0-0/706/36
https://redmine.openinfosecfoundation.org/issues/4096
-
@e-1-1 said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
With this new 6.0.6 version, is there some good news regarding the extra CPU time used by Suricata 6 vs 5?
It's been talked about in topic 166657, which I can't link because the Submit button throws an error.
No, there have been no further updates to that flow manager code which is the source of increased CPU utilization on certain types of hardware in Suricata 6.x. I'm really not sure what to expect there as the change improved performance on some big-iron machines while adversely impacting performance on other machines. To be honest, I don't think the Suricata developers really know how they want to approach that issue. Reverting would worsen performance in some setups.
-
@bmeeks had my hopes up, but well, no choice but to run with it. Pretty bummed about that, as a Suricata instance on a almost zero traffic interface takes 8% of CPU on one of my virtualised boxes...
-
@e-1-1 said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
@bmeeks had my hopes up, but well, no choice but to run with it. Pretty bummed about that, as a Suricata instance on a almost zero traffic interface takes 8% of CPU on one of my virtualised boxes...
Just saw this updated pull request on the Suricata Redmine site: https://github.com/OISF/suricata/pull/7743. Might be some glimmer of hope here as the request appears to be essentially rolling back the previous changes in the flow manager code (or at least the ones most likely associated with the increased CPU utilization). Hopefully these make it into Suricata 6.0.7.
-
@bmeeks said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
NOTE - This new version will initially be available only in the 2.7.0-DEVEL branch of pfSense for user testing. If no major issues are reported, the update will be merged into the RELEASE branches of pfSense CE and Plus in a few weeks.
It has been about 5 weeks. Is there any ETA on when this build will be made available in the stable (22.05/2.6.0) branch?
-
@xpxp2002 said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
@bmeeks said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
NOTE - This new version will initially be available only in the 2.7.0-DEVEL branch of pfSense for user testing. If no major issues are reported, the update will be merged into the RELEASE branches of pfSense CE and Plus in a few weeks.
It has been about 5 weeks. Is there any ETA on when this build will be made available in the stable (22.05/2.6.0) branch?
After initially pushing the 6.0.6 version into the DEVEL branch, there were some bug reports posted to the Suricata Redmine site that affected that version. Two of those were sort of bad in my opinion. Those bugs are referenced in a couple of posts earlier in this thread.
Based on those newly reported bugs, I decided to hold off on deploying 6.0.6 to the RELEASE branches of pfSense. I am closely following the upcoming release of Suricata 6.0.7 and hoping it will be a better candidate.
-
Hello Bill, are you aware of this?
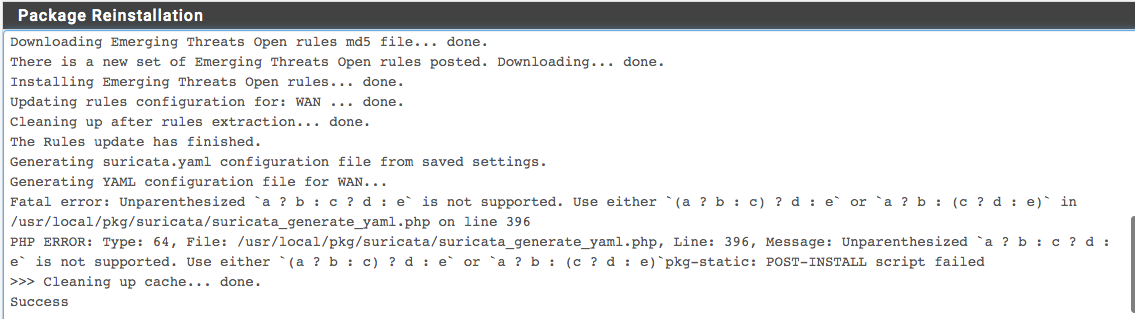
-
@nollipfsense said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
Hello Bill, are you aware of this?

Yep. First read this thread:
https://forum.netgate.com/topic/174915/snort-and-suricata-problems-with-the-new-php-8-1-and-freebsd-main-snapshots.And then you can follow the progress of the fixes here: https://redmine.pfsense.org/issues/13531. Suricata will be pretty badly broken in 2.7.0-DEVEL until my pull request referenced in the ticket and posted here: https://github.com/pfsense/FreeBSD-ports/pull/1192, is merged and a new package is built.
-
Looks like 6.0.9 is out now. Does it address any of the issues that were added with 6.0.6? I'm hoping that it contains a fix for an issue I'm seeing with 6.0.4 and would like to see the pfSense package updated if possible. Thank you for your work on this package.
-
@opoplawski Just checked package manager on v2.7, no Suricata 6.0.9...BTW, the problem is fixed with the current version Suricata 8.0.8_3.
-
@opoplawski said in Suricata-6.0.6 Update Release Notes - (initially for 2.7.0-DEVEL testing only):
Looks like 6.0.9 is out now. Does it address any of the issues that were added with 6.0.6? I'm hoping that it contains a fix for an issue I'm seeing with 6.0.4 and would like to see the pfSense package updated if possible. Thank you for your work on this package.
Suricata 6.0.8 is currently available on the 2.7.0 CE DEVEL branch (and the 23.01 Plus development branch). I'm holding off any changes in the RELEASE branch until I see if the next pfSense release happens in January as hoped. If the next pfSense release misses the anticipated launch date by a wide margin, then I will see about backporting a newer Suricata binary into the current 2.6 and 22.05 branches.
I have been experimenting with 6.0.9, but there is an open Suricata Redmine Issue with netmap that I am monitoring. It was opened by the OPNsense developer and is currently being investigated. I wanted to see how that was resolved before updating Suricata past 6.0.8 in pfSense.