Configuring Netgate W/ Dedicated Switch
-
Configuring Netgate 6100 to supply firewall to dedicated switch.
Warning Networking Newb
Recently received my Netgate 6100 and deployed it at a data center. Before ordering the design I had in my head was rather simple. Our fiber connection from the data center would plug into the netgate, from the netgate to the dlink switch and from the switch to our servers. The Dlink would serve as a simple firewall. Before you say "Why not just use IPtables.", idk it just seemed like id rather block connections from the top then for every server.
Currently our connections are as follows:
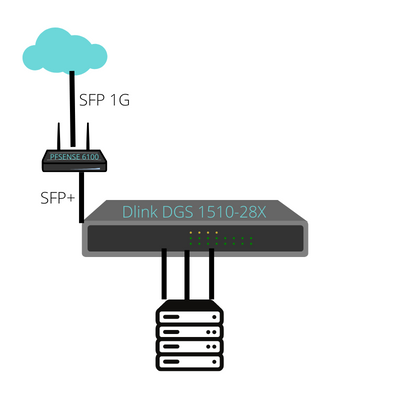
Fiber -> NETGATE 6100 via SFP in WAN 1 (1G) NETGATE 6100 -> DLINK (WAN 4 converted to LAN -- SFP+)We have an IP range from our data center
CIDR .128/28 Gateway .129 IP's .130 - .142Heres a crappy image
Things I've tried :
Converting WAN 4 to a LAN port and connecting to the switch but then I get overlapping errors when trying to assign an different IP and same gateway to both ports.
Do we need to configure a transparent bridge? Is it possible the whole SFP ingress to SFP+ egress situation we have going is causing an issue?
Any tips are much appreciated, please excuse our lack of networking knowledge and apologies in advanced if this is the incorrect forum subject.
-
@chalabi2 What do you mean use the switch as a firewall??
Is the intent to use your IPs on the LAN side of the pfSense? The "normal" way this is done is to have the data center allocate you a WAN IP in a different subnet (can be a /29 if you want to use CARP/HA). Then they route the /28 to the WAN IP. pfSense "knows" to forward those packets to the LAN network. You can then create whatever firewall rules you want to protect the LAN IPs.
If they will only provide one subnet then that usually means using NAT, perhaps 1:1 NAT. Or one can use a bridge.
-
@steveits Thanks for the reply steve, I meant use the netgate as a firewall.
Or one can use a bridge.
I was reading about transparent firewalls/bridges. Seemed like that is the approach that would best suit what we are looking to accomplish. Ive yet to try it but was confused as to why the 6100 doesnt just route the connection without doing all this. Shouldnt it be as simple as connecting fiber to wan of netgate, out of another wan port(converted to lan only calling it wan because its one of the sfp ports) of the netgate to the dlink switch then assigning IPs on the server level.
-
@chalabi2 A router needs to know where to route the packet. If an IP (subnet) is on both WAN and LAN then it gets confused. (To simplify). A bridge tells the router to not route.
-
@chalabi2 routing doc:
https://docs.netgate.com/pfsense/en/latest/recipes/route-public-ip-addresses.html -
@steveits I think im getting close to understanding, so if i dont want Netgate to do any routing I can create a bridge for the WAN & the LAN and just do the port/ip blocking on pfsense firewall while allowing the switch to distribute internet connection via ethernet to my servers? That way I would be utilizing the data centers router and would just have to configure gateway/ip on the Netgate, Dlink Switch & all my servers in the order?
Again, apologies if theres any redundant questions in here and i have a feeling actually trying to configure the transparent bridge would be beneficial to my understanding.
-
@chalabi2 Yes in that case a bridge is necessary. I’ve never had to use one though.
https://docs.netgate.com/pfsense/en/latest/bridges/index.html -
@steveits Thanks for the help Steve! Bridge worked :)