Wireguard suddenly refuses to handshake
-
@robearded Yep, I know. Actually I used the older version before, however did not work in my case. As mentioned, it worked when enabling "Disable Gateway Monitoring Action" in the gateway. Thanks anyways!
-
@sly1337 said in Wireguard suddenly refuses to handshake:
I checked further and found a message in the logs basically saying that the route for my S2S Gateway was changed.
/usr/local/pkg/wireguard/includes/wg_service.inc: Removing static route for monitor 8.8.8.8 and adding a new route through 10.1.1.110.1.1.1 is another gateway (LTE), not the primary (should be the gateway group..)
I checked the gateway and activated the "Disable Gateway Monitoring Action" checkmark. And now its working again... but does this make any sense? In any case, just wanted to let you know, so maybe someone faces the same issue.
I just tried that and it made no difference to my setup.
Before that (but after the problem appeared) I did a reboot of both my ESXi host (and updated it) and of the PfSesnse server. Since then the OpenVPN tunnel and one of the WG tunnels came back up exactly as they were before. The other is permanently down and has never come back up. I'm hoping @cmcdonald will be able to get me to do any troubleshooting while it's in this state as having 1 WG tunnel down and the other up and working fine seems like a fairly good opportunity to test things.
Ultimately though this is happening enough to be an "issue" and it's not an issue I have with any of the VPN vendors own WG stacks on my mobile or my desktop. I do need to find the time to set up FreeBSD but I'm not convinced that's really going to help as I can't actually replicate when, or if, it's going to happen.
-
After I had to restart my modem (so the WAN went down for some minutes on the pfsense) this problem happened to me again. I can't seem to be able to initiate the handshake whatever I do. I also checked "Disable Gateway Monitoring Action" checkbox for the wireguard gateway, however it's still not working
-
@robearded So as of 3h ago my other WG connection has gone down for no reason again and now I can't get either of the tunnels up.
This is so infuriating :(
I can't believe it's just a handful of us.
G
-
Hey all,
Sorry you guys are having issues with handshakes.
I do have an idea that might help illuminate where the problem lies, basically creating the tunnel from barebones at the shell and bypassing the GUI.
Here are the steps (adjust addresses, names, etc. as necessary for your situation):
- Disable "WireGuard" in WireGuard > Settings. This keeps the daemon from starting. This is important because we are going to build the tunnel up manually at the shell. Though you can still create your tunnel and peer config as normal, just don't start the service.
- Login to pfSense shell via SSH or console cable.
- Use these commands to create the interface, assign addresses, add to interface group (if necessary) and sync WireGuard conf:
This command creates a interface of type
wgwith nametun_wg0:$ ifconfig wg create name tun_wg0
This command assigns an IPv4
inetaddress of10.11.12.1/24ontun_wg0:$ ifconfig tun_wg0 inet 10.11.12.1/24
This command assigns
tun_wg0to interface groupWireGuard:$ ifconfig tun_wg0 group WireGuard
This command syncs
tun_wg0configuration using WireGuard userland toolswg:$ wg syncconf tun_wg0 /usr/local/etc/wireguard/tun_wg0.confNote:
/usr/local/etc/wireguard/tun_wg0.confcan be generated by the package, just keep the service disabled for the time-being.
This command brings up
tun_wg0administratively:$ ifconfig tun_wg0 up
At this point you should have a WireGuard tunnel interface built manually. You can now proceed with assigning it to pfSense, etc.
This test is useful because it bypasses all WireGuard package semantics and only uses pfSense core logic...useful for isolating potential issues.
-
This video walks through several scenarios that should be applicable here, hopefully this helps!
This video is more aimed at discussing the various ways I test and live with WireGuard on a daily basis, but I walk through the setup and configuration of each scenario.
-
@robearded said in Wireguard suddenly refuses to handshake:
After I had to restart my modem (so the WAN went down for some minutes on the pfsense) this problem happened to me again. I can't seem to be able to initiate the handshake whatever I do. I also checked "Disable Gateway Monitoring Action" checkbox for the wireguard gateway, however it's still not working
It turns out this happened because of a change I did on the wireguard server without realizing it will break stuff. I'm not however sure if I did this change before the first occurrence of this problem, from what I remember it is after, but it is definitely possible to be before.
I had some DNAT iptables rules in the PostUp and PostDown config of wireguard to forward some ports to pfsense, so I can use the public IP of the wg server as a public IP for the server running pfsense. I figured out that it would be easier to DNAT all ports (except SSH) and just do the firewalling inside pfsense, so I don't have to log in to the wg server everything I want to forward another port, and I can do it all from pfsense. Well, the problem is, that I didn't realized I also forwarded the port WG was listening on. -
Hello,
i'm facing the same problem with the error status of
/usr/local/pkg/wireguard/includes/wg_service.inc: Static Routes: Gateway IP could not be found ...No handshake seems to happen anymore. Reinstalled the wireguard package several times, and also tried a new version of the kmod implementation. No success.
-
@woodsomeister Post pictures of your wireguard tunnel, peers, interface and routes/gateway.
-
This post is deleted! -
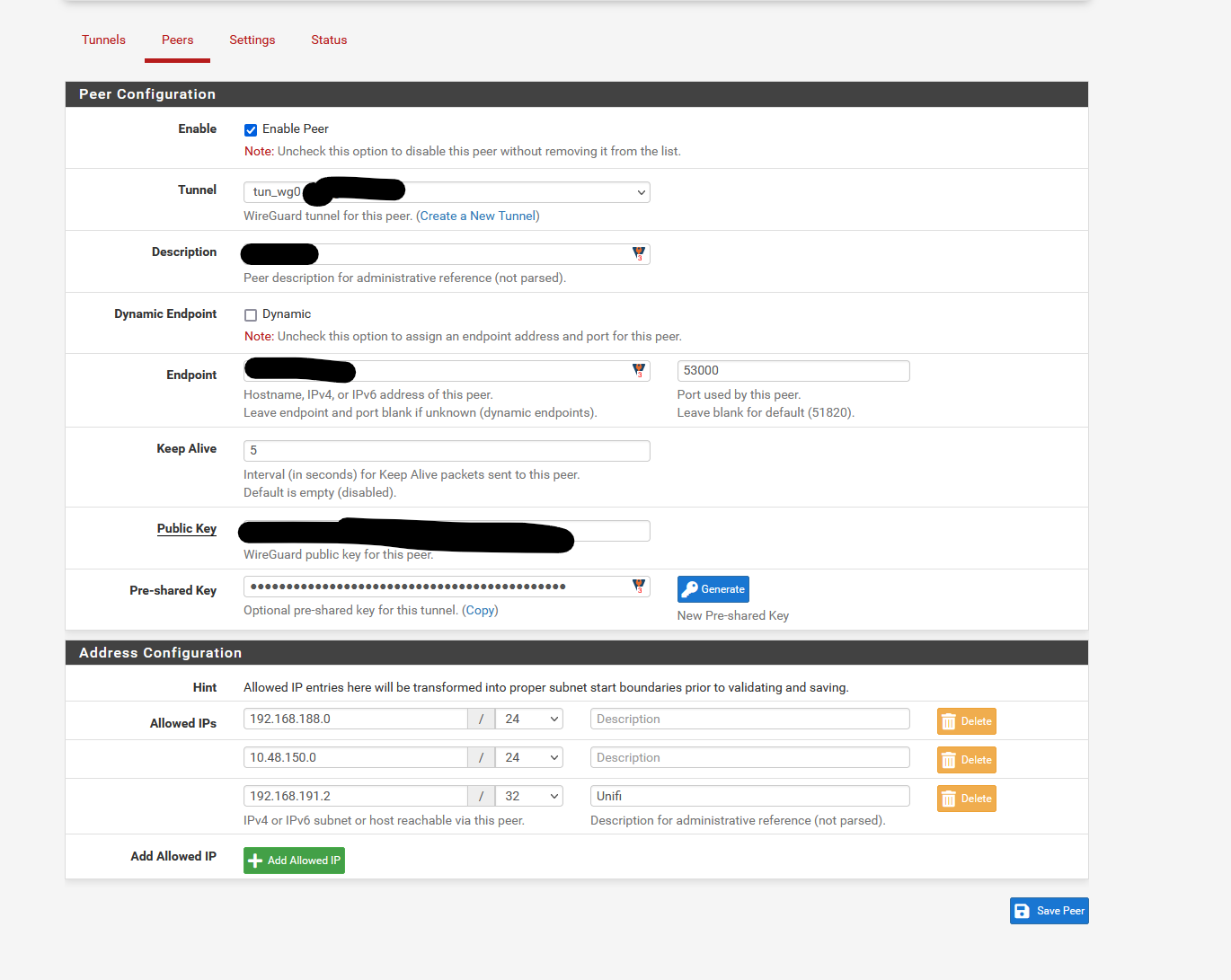
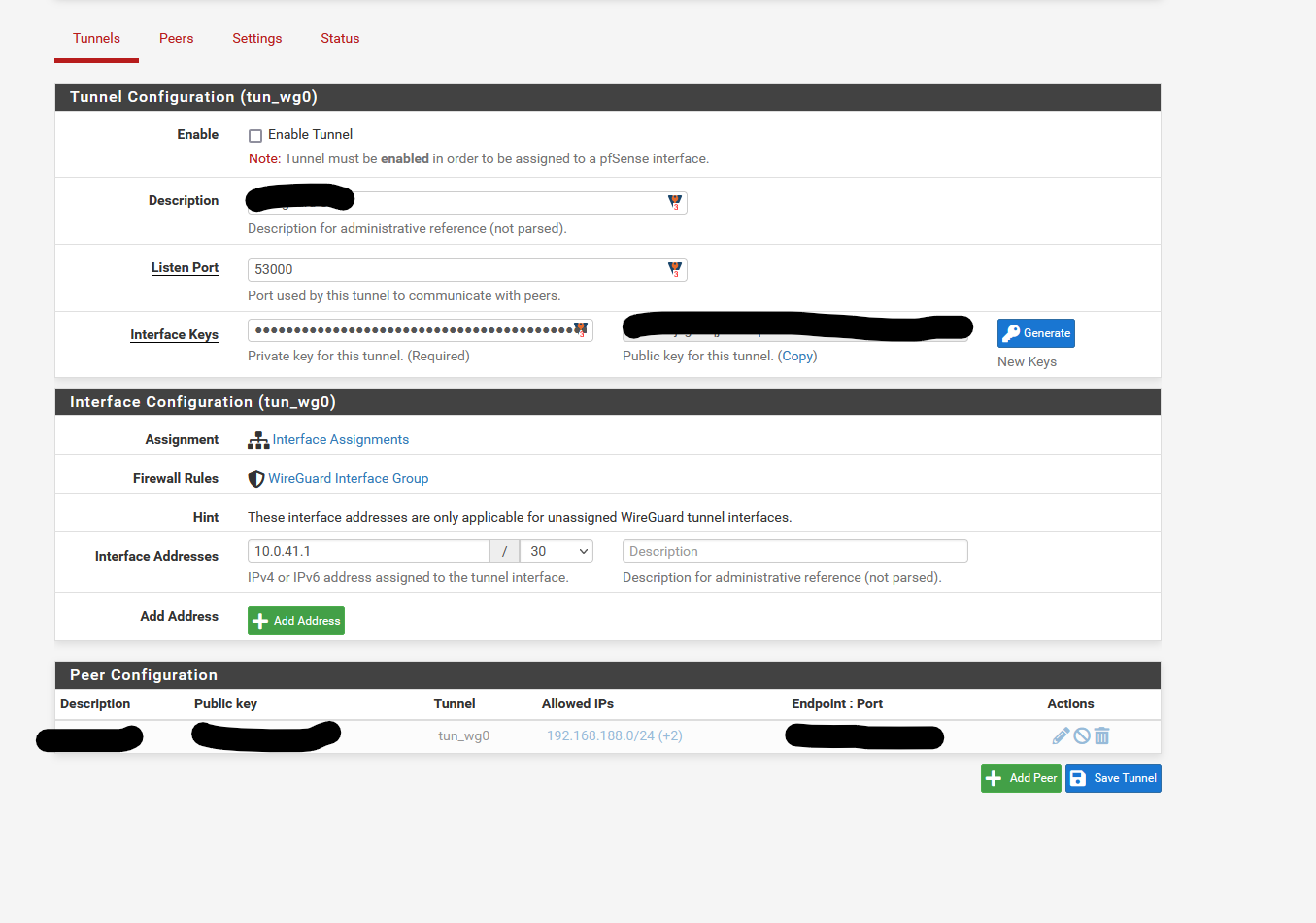
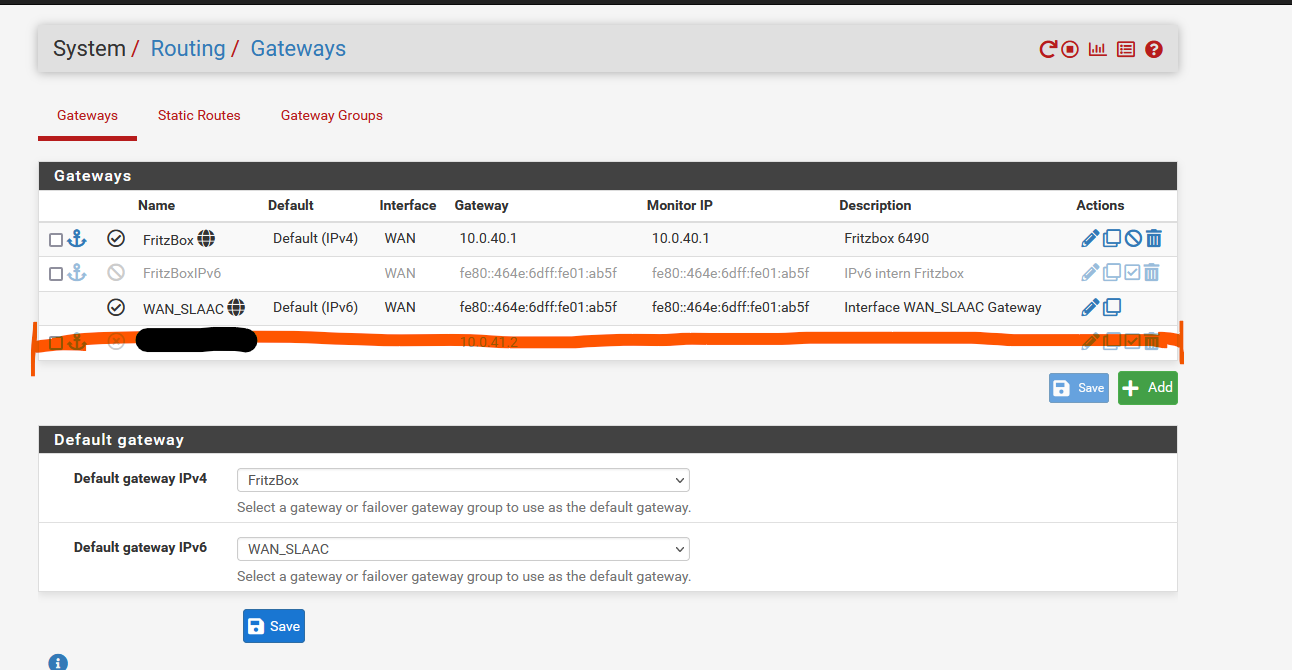
Routes were added for the marked Wireguard interface and i also configured the interface using the right IPv4 static IP (10.0.41.1, peer is 10.0.41.2). (no screenshot)
Unfortunatly i had to switched back to IPSec, so that's why everything is deactivated. -
@woodsomeister You have to add the tunnel as an allowed IP.
Did this ever work? -
@jarhead For several weeks. In the other side is also a Opnsense under my control. Everything was working as expected, but after a restart some days ago i went into this problem.
-
@xxgbhxx I tried the version 0.0.20210606_1 solution and now wireguard crashes and I get crash reports. I tried uninstalling wireguard and installing but now the WG service won't stay running.
What's my next step? -
DO NOT DO THIS.
Changing the wireguard-kmod package will cause kernel panics and take down your pfSense box.
I have the same problem with WireGuard not handshaking, but this solution DOES NOT fix it. FYI.
-
@itheadquarters Same thing happened to me. You need to SSH into your box, run 'pkg install wireguard-kmod'. This will put your package back to wireguard-kmod-0.0.20211105. This doesn't fix the handshake problem, but it will stop the kernel panics.
You can check your version numbers with 'pkg info -l wireguard-kmod'
-
@itheadquarters Sorry no notifications you'd replied to me. That wasn't my suggestion by the way.
I've given up with pfSense' implementation of Wireguard. I find it unstable and flakey as hell.
I purposely don't touch it once it's working and pray it's going to keep working. I've had a few unexplained random drops since I posted this and I just bypass the vpn until it comes back up which might be minutes, hours or days.
To illustrate this I have relatively recently set up a new connection to one of the VPN providers I've set the connection up to before. The settings are identical (obviously not they key's). Everything I can see is set up exactly the same as the working one and it has NEVER worked.
I've deleted and re-built that VPN 10+ times and it will never connect. In anger I set up and configured a brand new Opnsense VM using the exact same keys and settings and it worked instantly first time. It's never dropped. Not even once.
I can only go by what I find. If you're lucky, you get no issues but I have found, with my setup, Wireguard is just broken.
As soon as I get a few days free I'm going to be converting over to Opnsense full time not elast as its fairly clear to me that Netgate have walked away from the community version of PFSense.
-
@xxgbhxx Does Opnsense have a variant of PFBlockerNG?
-
@xxgbhxx I may have too also. I can't keep wrestling with this. I've wasted endless time trying to find out what's wrong, only to find out it's a bad implementation of the WireGuard package. I was running myself crazy, wondering if it was some problem with my ISP, or some arcane config setting. Unbelievable.
-
@n3ivi0 guess that's why it is marked EXPERIMENTAL :-)