HAProxy and X.509 certificates no longer working after reboot?
-
Hello, I am scratching my head here!
I rebooted my pfsense box that was working and my x.509 certificates are no longer working?
I have tried renewing them, etc. but no luck.
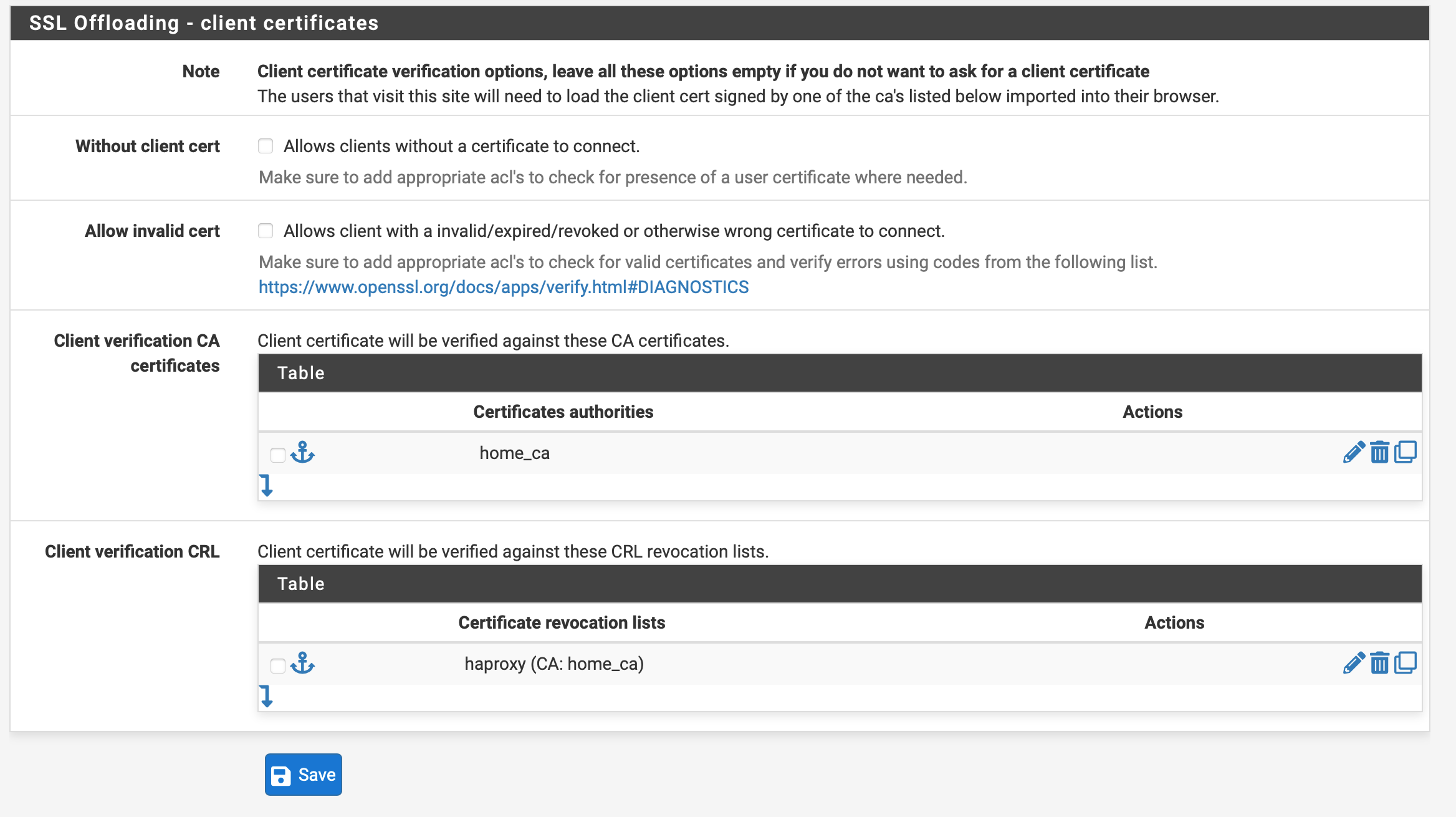
My HAProxy services that are not limited to client certificates are still functioning and if I remove the client certificate configuration for those broken frontends, they work without certificates...
Can anyone help me to troubleshoot this? I am a bit lost.
Running HAProxy 2.4.9-f8dcd9f on pfsense 2.6.0-RELEASE
I have a self-signed CA in pfsense that I create certificates for and then download the p12 files and import them to macOS keychain.
It worked great before, for the two machines I used, but both of them stopped working after the reboot...
The domain has a wildcard certificate from cloudflare.
➜ ~ curl -Iv https://sub.valid.domain * Trying XX.XX.XX.XX:443... * Connected to sub.valid.domain (XX.XX.XX.XX) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * successfully set certificate verify locations: * CAfile: /etc/ssl/cert.pem * CApath: none * (304) (OUT), TLS handshake, Client hello (1): * (304) (IN), TLS handshake, Server hello (2): * (304) (IN), TLS handshake, Unknown (8): * (304) (IN), TLS handshake, Request CERT (13): * (304) (IN), TLS handshake, Certificate (11): * (304) (IN), TLS handshake, CERT verify (15): * (304) (IN), TLS handshake, Finished (20): * (304) (OUT), TLS handshake, Certificate (11): * (304) (OUT), TLS handshake, Finished (20): * SSL connection using TLSv1.3 / AEAD-AES256-GCM-SHA384 * ALPN, server did not agree to a protocol * Server certificate: * subject: CN=*.valid.domain * start date: Aug 1 00:17:06 2022 GMT * expire date: Oct 30 00:17:05 2022 GMT * subjectAltName: host "sub.valid.domain" matched cert's "*.valid.domain" * issuer: C=US; O=Let's Encrypt; CN=R3 * SSL certificate verify ok. > HEAD / HTTP/1.1 > Host: sub.valid.domain > User-Agent: curl/7.79.1 > Accept: */* > * LibreSSL SSL_read: error:1404C45C:SSL routines:ST_OK:reason(1116), errno 0 * Closing connection 0 curl: (56) LibreSSL SSL_read: error:1404C45C:SSL routines:ST_OK:reason(1116), errno 0
-
huh, removing the certificate revocation and creating new certificates makes it work again, but adding the revocation list back makes it stop working.
The revocation list is empty:
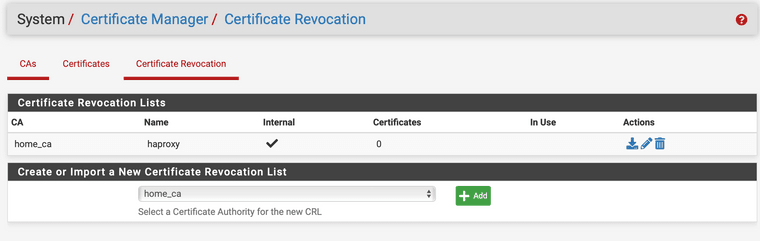
If I delete that revocation list and create a new one, also empty, the same thing happens.
from log:
Aug 18 19:46:39 localhost haproxy[7636]: XX:25674 [18/Aug/2022:19:46:39.114] https_shared-merged/192.168.2.2:443: SSL client certificate not trustedAny idea what is going on here?
I guess I don't need the revocation list function right now but... I might in the future
-
Ok, so after checking the CRL with openssl, and finding it was set to new in 1950 I found this thread: https://forum.netgate.com/topic/172870/crl-has-expired
So I guess that patch would fix this?
Anyway, I just created a new CRL with only 7000 days and it is working again.
-
S slu referenced this topic on
-
S slu referenced this topic on