Packet loss when download and TCP connection error
-
Hi,
It's my first post in this forum.
I have big problems with OpenVPN and NordVPN when any of my devices downloads on my network, the rate of packet loss increase and the gateway monitoring becomes down.
When the download stops, all is immediately good.My pfSense version is 2.6.0 and my OpenVPN Client protocol is UDP.
The MTU is 1500.So I tried to connect with TCP.
The connection is OK, but there is always 100% of packet loss even without download.
The OpenVPN logs in TCP mode :Aug 25 08:30:27 openvpn 39248 event_wait returned 1 Aug 25 08:30:27 openvpn 39248 PO_WAIT[1,0] fd=6 rev=0x00000001 rwflags=0x0001 arg=0x002b6724 Aug 25 08:30:27 openvpn 39248 I/O WAIT TR|Tw|SR|Sw [11/69244] Aug 25 08:30:27 openvpn 39248 PO_CTL rwflags=0x0001 ev=4 arg=0x002b6728 Aug 25 08:30:27 openvpn 39248 PO_CTL rwflags=0x0001 ev=6 arg=0x002b6724 Aug 25 08:30:27 openvpn 39248 PO_CTL rwflags=0x0001 ev=5 arg=0x002b7428 Aug 25 08:30:27 openvpn 39248 STREAM: SET NEXT, buf=[572,0] next=[572,1659] len=-1 maxlen=1659 Aug 25 08:30:27 openvpn 39248 write TCPv4_CLIENT: Permission denied (code=13) Aug 25 08:30:27 openvpn 39248 TCPv4_CLIENT write returned -1 Aug 25 08:30:27 openvpn 39248 STREAM: WRITE 54 offset=500 Aug 25 08:30:27 openvpn 39248 TCPv4_CLIENT WRITE [54] to [AF_INET]138.199.47.175:443: P_DATA_V2 kid=0 DATA 00000000 00009fb9 d7446586 331eead2 5e1b19fb 59012530 499c0428 127c379[more...] Aug 25 08:30:27 openvpn 39248 I/O WAIT status=0x0002There is no blocked traffic on the snort, pfBlocker and firewall logs.
I didn't found solution on the net, so this is the last place where I could find help. -
Can you show all the OpenVPN client log lines ?
From complete stop to running ? -
Here is the log when the server stops (UDP mode) and starts (TCP mode) :
Aug 25 09:43:31 openvpn 68471 write TCPv4_CLIENT: Permission denied (code=13) Aug 25 09:43:30 openvpn 68471 write TCPv4_CLIENT: Permission denied (code=13) Aug 25 09:43:30 openvpn 68471 write TCPv4_CLIENT: Permission denied (code=13) Aug 25 09:43:29 openvpn 68471 write TCPv4_CLIENT: Permission denied (code=13) Aug 25 09:43:29 openvpn 68471 write TCPv4_CLIENT: Permission denied (code=13) Aug 25 09:43:28 openvpn 68471 write TCPv4_CLIENT: Permission denied (code=13) Aug 25 09:42:54 openvpn 68471 Initialization Sequence Completed Aug 25 09:42:54 openvpn 68471 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Aug 25 09:42:54 openvpn 68471 /usr/local/sbin/ovpn-linkup ovpnc5 1500 1586 10.7.2.2 255.255.255.0 init Aug 25 09:42:54 openvpn 68471 /sbin/route add -net 10.7.2.0 10.7.2.1 255.255.255.0 Aug 25 09:42:54 openvpn 68471 /sbin/ifconfig ovpnc5 10.7.2.2 10.7.2.1 mtu 1500 netmask 255.255.255.0 up Aug 25 09:42:54 openvpn 68471 TUN/TAP device /dev/tun5 opened Aug 25 09:42:54 openvpn 68471 TUN/TAP device ovpnc5 exists previously, keep at program end Aug 25 09:42:54 openvpn 68471 ROUTE_GATEWAY 91.XX.XX.XX/255.255.255.0 IFACE=igb0 HWADDR=40:62:31:11:0e:48 Aug 25 09:42:54 openvpn 68471 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 25 09:42:54 openvpn 68471 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 25 09:42:54 openvpn 68471 Data Channel: using negotiated cipher 'AES-256-GCM' Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: data channel crypto options modified Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: adjusting link_mtu to 1658 Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: peer-id set Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: route-related options modified Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: route options modified Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: --ifconfig/up options modified Aug 25 09:42:54 openvpn 68471 Socket Buffers: R=[65700->524288] S=[65700->524288] Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: --sndbuf/--rcvbuf options modified Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: compression parms modified Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: --explicit-exit-notify can only be used with --proto udp Aug 25 09:42:54 openvpn 68471 OPTIONS IMPORT: timers and/or timeouts modified Aug 25 09:42:54 openvpn 68471 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 103.86.96.100,dhcp-option DNS 103.86.99.100,sndbuf 524288,rcvbuf 524288,explicit-exit-notify,comp-lzo no,route-gateway 10.7.2.1,topology subnet,ping 60,ping-restart 180,ifconfig 10.7.2.2 255.255.255.0,peer-id 0,cipher AES-256-GCM' Aug 25 09:42:54 openvpn 68471 SENT CONTROL [fr780.nordvpn.com]: 'PUSH_REQUEST' (status=1) Aug 25 09:42:53 openvpn 68471 [fr780.nordvpn.com] Peer Connection Initiated with [AF_INET]138.199.47.175:443 Aug 25 09:42:53 openvpn 68471 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 4096 bit RSA, signature: RSA-SHA512 Aug 25 09:42:53 openvpn 68471 WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='comp-lzo' Aug 25 09:42:53 openvpn 68471 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1635', remote='link-mtu 1636' Aug 25 09:42:53 openvpn 68471 VERIFY OK: depth=0, CN=fr780.nordvpn.com Aug 25 09:42:53 openvpn 68471 VERIFY EKU OK Aug 25 09:42:53 openvpn 68471 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Aug 25 09:42:53 openvpn 68471 Validating certificate extended key usage Aug 25 09:42:53 openvpn 68471 VERIFY KU OK Aug 25 09:42:53 openvpn 68471 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA7 Aug 25 09:42:53 openvpn 68471 VERIFY OK: depth=2, C=PA, O=NordVPN, CN=NordVPN Root CA Aug 25 09:42:53 openvpn 68471 VERIFY WARNING: depth=2, unable to get certificate CRL: C=PA, O=NordVPN, CN=NordVPN Root CA Aug 25 09:42:53 openvpn 68471 VERIFY WARNING: depth=1, unable to get certificate CRL: C=PA, O=NordVPN, CN=NordVPN CA7 Aug 25 09:42:53 openvpn 68471 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=fr780.nordvpn.com Aug 25 09:42:53 openvpn 68471 TLS: Initial packet from [AF_INET]138.199.47.175:443, sid=43d86a7c 77d9f5a4 Aug 25 09:42:53 openvpn 68471 TCPv4_CLIENT link remote: [AF_INET]138.199.47.175:443 Aug 25 09:42:53 openvpn 68471 TCPv4_CLIENT link local (bound): [AF_INET]91.XX.XX.XX:0 Aug 25 09:42:53 openvpn 68471 TCP connection established with [AF_INET]138.199.47.175:443 Aug 25 09:42:53 openvpn 68471 Attempting to establish TCP connection with [AF_INET]138.199.47.175:443 [nonblock] Aug 25 09:42:53 openvpn 68471 Socket Buffers: R=[65228->65228] S=[65228->65228] Aug 25 09:42:53 openvpn 68471 TCP/UDP: Preserving recently used remote address: [AF_INET]138.199.47.175:443 Aug 25 09:42:53 openvpn 68471 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Aug 25 09:42:53 openvpn 68471 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Aug 25 09:42:53 openvpn 68471 WARNING: experimental option --capath /var/etc/openvpn/client5/ca Aug 25 09:42:53 openvpn 68471 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Aug 25 09:42:53 openvpn 68471 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client5/sock Aug 25 09:42:53 openvpn 68215 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10 Aug 25 09:42:53 openvpn 68215 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022 Aug 25 09:42:53 openvpn 68215 WARNING: file '/var/etc/openvpn/client5/up' is group or others accessible Aug 25 09:42:53 openvpn 17811 SIGTERM[soft,exit-with-notification] received, process exiting Aug 25 09:42:53 openvpn 17811 /usr/local/sbin/ovpn-linkdown ovpnc5 1500 1584 10.8.1.4 255.255.255.0 init Aug 25 09:42:53 openvpn 17811 Closing TUN/TAP interface Aug 25 09:42:52 openvpn 17811 SIGTERM received, sending exit notification to peer Aug 25 09:42:52 openvpn 17811 event_wait : Interrupted system call (code=4) Aug 25 09:42:11 openvpn 17811 MANAGEMENT: Client disconnected Aug 25 09:42:11 openvpn 17811 MANAGEMENT: CMD 'status 2' Aug 25 09:42:11 openvpn 17811 MANAGEMENT: CMD 'state 1' Aug 25 09:42:11 openvpn 17811 MANAGEMENT: Client connected from /var/etc/openvpn/client5/sock Aug 25 09:42:11 openvpn 17811 MANAGEMENT: Client disconnected Aug 25 09:42:11 openvpn 17811 MANAGEMENT: CMD 'status 2' Aug 25 09:42:11 openvpn 17811 MANAGEMENT: CMD 'state 1' Aug 25 09:42:11 openvpn 17811 MANAGEMENT: Client connected from /var/etc/openvpn/client5/sockAnd the same log when the server stops (TCP mode) and starts (UDP mode) :
Aug 25 09:49:41 openvpn 525 Initialization Sequence Completed Aug 25 09:49:41 openvpn 525 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Aug 25 09:49:41 openvpn 525 /usr/local/sbin/ovpn-linkup ovpnc5 1500 1584 10.8.0.2 255.255.255.0 init Aug 25 09:49:41 openvpn 525 /sbin/route add -net 10.8.0.0 10.8.0.1 255.255.255.0 Aug 25 09:49:41 openvpn 525 /sbin/ifconfig ovpnc5 10.8.0.2 10.8.0.1 mtu 1500 netmask 255.255.255.0 up Aug 25 09:49:41 openvpn 525 TUN/TAP device /dev/tun5 opened Aug 25 09:49:41 openvpn 525 TUN/TAP device ovpnc5 exists previously, keep at program end Aug 25 09:49:41 openvpn 525 ROUTE_GATEWAY 91.XX.XX.XX/255.255.255.0 IFACE=igb0 HWADDR=40:62:31:11:0e:48 Aug 25 09:49:41 openvpn 525 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 25 09:49:41 openvpn 525 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 25 09:49:41 openvpn 525 Data Channel: using negotiated cipher 'AES-256-GCM' Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: data channel crypto options modified Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: adjusting link_mtu to 1656 Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: peer-id set Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: route-related options modified Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: route options modified Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: --ifconfig/up options modified Aug 25 09:49:41 openvpn 525 Socket Buffers: R=[42080->524288] S=[57344->524288] Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: --sndbuf/--rcvbuf options modified Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: compression parms modified Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: explicit notify parm(s) modified Aug 25 09:49:41 openvpn 525 OPTIONS IMPORT: timers and/or timeouts modified Aug 25 09:49:41 openvpn 525 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 103.86.96.100,dhcp-option DNS 103.86.99.100,sndbuf 524288,rcvbuf 524288,explicit-exit-notify,comp-lzo no,route-gateway 10.8.0.1,topology subnet,ping 60,ping-restart 180,ifconfig 10.8.0.2 255.255.255.0,peer-id 0,cipher AES-256-GCM' Aug 25 09:49:41 openvpn 525 SENT CONTROL [fr780.nordvpn.com]: 'PUSH_REQUEST' (status=1) Aug 25 09:49:40 openvpn 525 [fr780.nordvpn.com] Peer Connection Initiated with [AF_INET]138.199.47.175:1194 Aug 25 09:49:40 openvpn 525 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 4096 bit RSA, signature: RSA-SHA512 Aug 25 09:49:40 openvpn 525 WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='comp-lzo' Aug 25 09:49:40 openvpn 525 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1633', remote='link-mtu 1634' Aug 25 09:49:40 openvpn 525 VERIFY OK: depth=0, CN=fr780.nordvpn.com Aug 25 09:49:40 openvpn 525 VERIFY EKU OK Aug 25 09:49:40 openvpn 525 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Aug 25 09:49:40 openvpn 525 Validating certificate extended key usage Aug 25 09:49:40 openvpn 525 VERIFY KU OK Aug 25 09:49:40 openvpn 525 VERIFY OK: depth=1, C=PA, O=NordVPN, CN=NordVPN CA7 Aug 25 09:49:40 openvpn 525 VERIFY OK: depth=2, C=PA, O=NordVPN, CN=NordVPN Root CA Aug 25 09:49:40 openvpn 525 VERIFY WARNING: depth=2, unable to get certificate CRL: C=PA, O=NordVPN, CN=NordVPN Root CA Aug 25 09:49:40 openvpn 525 VERIFY WARNING: depth=1, unable to get certificate CRL: C=PA, O=NordVPN, CN=NordVPN CA7 Aug 25 09:49:40 openvpn 525 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=fr780.nordvpn.com Aug 25 09:49:40 openvpn 525 TLS: Initial packet from [AF_INET]138.199.47.175:1194, sid=f09271c1 8086d3bd Aug 25 09:49:40 openvpn 525 UDPv4 link remote: [AF_INET]138.199.47.175:1194 Aug 25 09:49:40 openvpn 525 UDPv4 link local (bound): [AF_INET]91.XX.XX.XX:0 Aug 25 09:49:40 openvpn 525 Socket Buffers: R=[42080->42080] S=[57344->57344] Aug 25 09:49:40 openvpn 525 TCP/UDP: Preserving recently used remote address: [AF_INET]138.199.47.175:1194 Aug 25 09:49:40 openvpn 525 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Aug 25 09:49:40 openvpn 525 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Aug 25 09:49:40 openvpn 525 WARNING: experimental option --capath /var/etc/openvpn/client5/ca Aug 25 09:49:40 openvpn 525 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Aug 25 09:49:40 openvpn 525 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client5/sock Aug 25 09:49:40 openvpn 263 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10 Aug 25 09:49:40 openvpn 263 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022 Aug 25 09:49:40 openvpn 263 WARNING: file '/var/etc/openvpn/client5/up' is group or others accessible Aug 25 09:49:39 openvpn 68471 SIGTERM[hard,] received, process exiting Aug 25 09:49:39 openvpn 68471 /usr/local/sbin/ovpn-linkdown ovpnc5 1500 1587 10.7.3.5 255.255.255.0 init Aug 25 09:49:39 openvpn 68471 Closing TUN/TAP interface Aug 25 09:49:39 openvpn 68471 event_wait : Interrupted system call (code=4) Aug 25 09:49:39 openvpn 68471 write TCPv4_CLIENT: Permission denied (code=13) -
Why alternate between UDP and TCP ?
Why not : make one works.
Then, when done, make the other work (create a new instance)Your logs look fine.
But mtu values bigger then 1500 .... are you sure ?Packets leaving your native WAN interface are probably a bit lower as 1500. So, encapsulated packets like the ones send to a VPN server must be smaller.
General advise : you NordVPN is probably not using OpenVPN 2.5.4, but another version. It could even be the older 2.4.x series.
This means you have to visit the official OpenVPN documentation, and see what you have to chose : "comp-lzo" did change in the newer 2.5.x series. -
I have packets loss with UDP and can't find the solution so I try also in TCP until one of them works.
I didn't set a MTU value bigger than 1500. I set 1500 on the OpenVPN client like the value which is in the document of NordVPN for pfSense 2.4.5.
I set also 1500 directly on the OpenVPN interface.
So I don't understand why there is a MTU of 1656 in the log ?My custom options are :
tls-client; remote-random; tun-mtu 1500; tun-mtu-extra 32; mssfix 1450; persist-key; persist-tun; reneg-sec 0; remote-cert-tls server; -
@mavenhalo said in Packet loss when download and TCP connection error:
tls-client;
When using a VPN 'thing', always double check the settings.
Have a look here /var/etc/openvpn/clientx/ where x can be 1,2, etc.
You find several files, and among them the famous config.opvnOpen the file, and check the content.
You will probably find a first "tls-client", as you are setting up a OpenVPN client so the next tls-client line (is part of your custom config) isn't needed.
While you see the file, check other options for doubles and other awkward stuff.Remember : this is OpenVPN. Using a GUI is nice, but it always boils down to 'a config file'.
Btw : I'm not using Nord, but Express.
My custom settinsg are :remote-random; pull; comp-lzo; verify-x509-name Server name-prefix; remote-cert-tls server; key-direction 1; route-method exe; route-delay 2; tun-mtu 1500; fragment 1300; mssfix 1450;Double check the usage of :
tun-mtu-extra 32; <= never saw this one before
persist-key; <= probably also already included - so remove them from your custom config
persist-tun; <= idem
reneg-sec 0;If the Nord instruction are for a pfSense 2.4.5, then keep in mind that these are valid for an (very) old OpenVPN version, as said, an earlier 2.4.x.
Try finding instructions for a more recent pfSense version (using OpenVPN 2.5.4).I'm a bit perplex about your mtu values. They seem 'not logic' to me.
-
How big is your bandwith and is the download using all of the bandwith??
-
I will check my config file.
My bandwith is about 400Mb/s down and 300Mb/s up.
Through the VPN, I notice a bandwith of 200Mb/s down and 120Mb/s up. -
I have check the config file.
I found only these duplicate lines that I have removed from my custom options :tls-client; persist-key; persist-tun;I tried to remove tun-mtu-extra, same behavior.
Can the problem comes from something else than the OpenVPN configuration ?
-
@mavenhalo said in Packet loss when download and TCP connection error:
Can the problem comes from something else than the OpenVPN configuration ?
The problem is : a conflicting configuration between VPN server (Nord) and the client - pfSense.
As said, I'm not using Nord myself, but I have a working Express ( not sure - read on ) OpenVPN client setup.When I start mine, I can't really use it, as I did not complete the routing part.
But, I can use the active OpenVPN client interface to ping with it :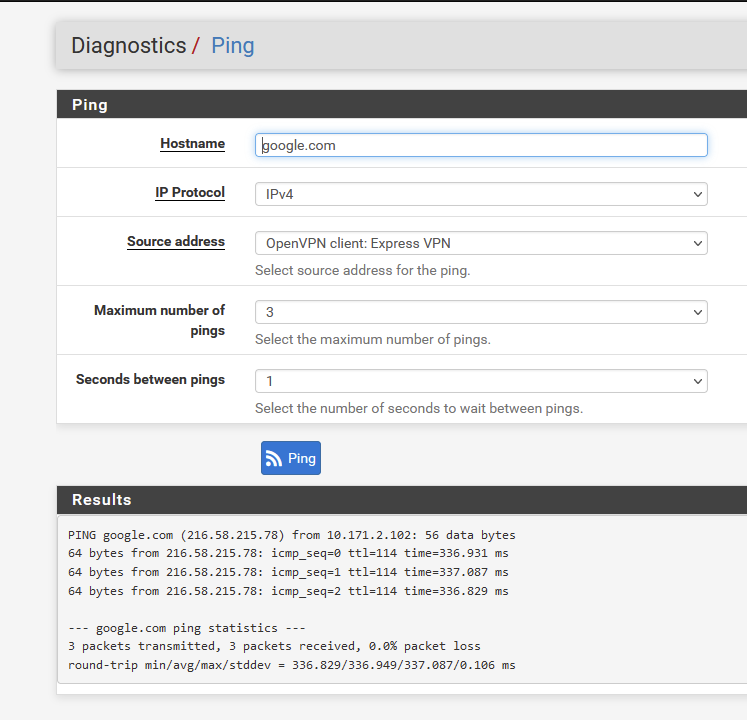
The 330 ms delay is due to the fact that I'm using a VPN server from "usa-sanfrancisco-ca-version-2.expressnetw.com" which is not really in my neighbourhood ;)
edit :
Forget about the links that mention 2.4.5 (ancient, dangerous ....) or even 2.5.0 (also old) or even 2.5.2.
Look for specific pfSense 2.6.0, use no other ones.
[Rambling : start]
If their is no info, then it might be the case that the OpenVPN version that Nord uses isn't the stock OpenVPN ( from here ) as that is the place where pfSEnse got it from.
Nord can have their own 'adapted' build as they only need to make it work with their own 'App', the one you install on your PC or Mac or Phone.
I didn't checked their support sites, but, if you can make it work with your 'router', then great for you. If not, they don't care, as that isn't their goal.
Their goals is are : Make money. Spend less on support. Tell support that they should tell the customers : install the App. For the rest, you are on your own aka non supported.By now you start to understand that you can't chose a VPN by watching a Youtube video, and that there is more then 'price'.
(Your) questions like : "you support my router ," should be number one.[Rambling : stop]
Still, I think OpenVPN is possible.
Btw : Nord supports Wiregaurd ? Never used that one myself, but give it a go, as it is waaaaaay simpler to set up.
Also : you have seen [https://techshielder.com/how-to-setup-and-use-nordvpn-on-pfsense](link url) I presume.
but you already saw that half of this :

is a bit BS.
So, I tend to ask myself : what about the rest ? ;)
Btw : https://techshielder.com/how-to-setup-and-use-nordvpn-on-pfsense looks nice, but there are NO intermediate tests, like : when done this, test this, and it should work.
So you can't know what went wrong where.
And because you and I don't know shit about VPN anyway (I'm pretty for myself), we could also typing pure Chinese characters from a web page, we're lost.Here is one for free :
When you reach step 12, do the ping test first as I've shown above.
You will know if the tunnel is up (not usable for traffic, but up) - see my example.Also : who is 103.86.96.100 ? is it safe ?
Isn't the default resolving not just fine ? Just route all resolver traffic over the VPN connection, and done.
IMHO : Don't mess with DNS, the out of the box DNS works fine, things go often downhill when people start to enter their own DNS choices (and then its pfSense's fault of course).edit : sorry, no mega helpful here.
-
There is something I don't understand.
When I download from my server, I see loss on the VPN gateway in pfSense.
But, is it packets loss from the data I download, or a saturation (bandwith, CPU, etc...) of pfSense with a consequence in the monitoring of the gateway ?How can I know if my transfer of data had lost packets ?
ps : I have a Qotom with a core i5-4210U and 8GB
-
@mavenhalo said in Packet loss when download and TCP connection error:
How can I know if my transfer of data had lost packets ?
When you use your VPN, start a ping like this :
ping www.google.com -tNow, do a download test with a navigator, or start downloading something big, from a source that as 'infinite' output. Try to install the WorldofTanks game from wargaming.
You will most probably see packet and thus ping packet loss.One thing that you can't really test : the output of your VPN server, your VPN ISP, they all say they give you 'a lot'. But they actually share the outgoing bandwidth among all connected clients. And ones the pipe is full, everything gets throttled.
Also : the VPN is most probably UDP, and that traffic can get discared : packets (and pings) get lost. Traffic will retransmitted and re assembled to the correct info of course. -
When you fill your pipe on the VPN with a DL then packetloss will occur.
Everything else is getting throttled.
Also a normal DL on the connection that fills the pipe will see packetloss.
Thats why people tend to use bandwidth limiters for the services so this doesnt occur.