Suricata dont block Torrents
-
Hello together,
I'm having a real hard time to understand why Suricata isn't blocking Torrents.
Correct me if I'm wrong but if you make a download via Torrent you download this torrent file and this Torrent File tells your torrent client on which P2P Members the small files are which I need to get to combine all files to one big file. So installed the Snort Registered User Ruleset, the emergingthreats.net Rulesets and the ABUSE.ch SSL Blacklist ruleset. I activate every single of this P2P rules and don't get an Alert if I'm starting a Torrent via uTorrent or BitTorrent. The Background is that I have a Firewall at a costumer site and I get kazaa P2P Alerts, so before I change it to blocking mode on their site I wanted to test the blocking mode on my site to see if it blocks things that are in my Mind like TOR or Torrents. I configure my Suricata as same as the costumer site, but the Suricata on the Costumer Site detects P2P Traffic for Kazaa and on my Site it don't detect that kind of traffic.
I run Suricata 6.0.4_1 and pfsense on Version 2.5.2.
Thanks for the Help!
-
@suricata_cap said in Suricata dont block Torrents:
I configure my Suricata as same as the costumer site
If the software and settings are the same, then there is just one thing left that will be different : the P2P-user at the customers site is not doing the same thing as you do (uses other links, other sofware, etc).
@suricata_cap said in Suricata dont block Torrents:
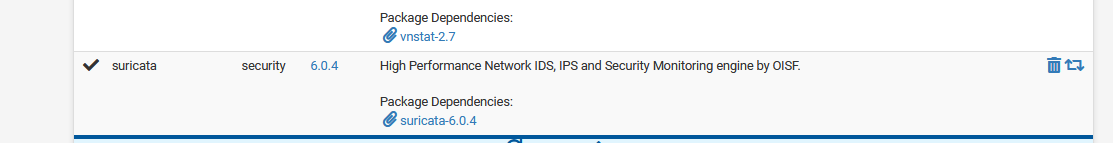
I run Suricata 6.0.4_1
Your not using the latests version :
but this probably a minor issue.
I'm not a Suricata user.Far 'worse' is :
@suricata_cap said in Suricata dont block Torrents:
pfsense on Version 2.5.2.
which is ancient.
Be ware : do not install or update pfSense packages if you are not using the latest pfSEnse version, that is 2.6.0 or 22.05 today.
-
Hello Gertjan, thanks for your answer.
You are right, thats really a problem, I will bring the pfsense to the highes version, hope this will fix it, I will post the result of this in here.Have a nice day!
-
@suricata_cap said in Suricata dont block Torrents:
like TOR
FYI, pfBlockerNG-devel has a feed for TOR exit nodes. So, one can just block with a firewall rule and not packet inspection.
re: package versions, see my sig.
-
Hi Steve,
I allreay read somewhere about that, I never use the pfBlocker before but I think its a try worth.
Thanks you! ^^
-
@suricata_cap said in Suricata dont block Torrents:
I'm having a real hard time to understand why Suricata isn't blocking Torrents.
I configure my Suricata as same as the costumer site, but the Suricata on the Costumer Site detects P2P Traffic for Kazaa and on my Site it don't detect that kind of traffic.
Is one of the clients using encryption and the other not using encryption? Suricata cannot examine encrypted traffic. I am not a torrent user, but I believe most of the clients offer optional encryption and obfuscation of their traffic these days.
-
@gertjan said in Suricata dont block Torrents:
@suricata_cap said in Suricata dont block Torrents:
I run Suricata 6.0.4_1
Your not using the latests version :

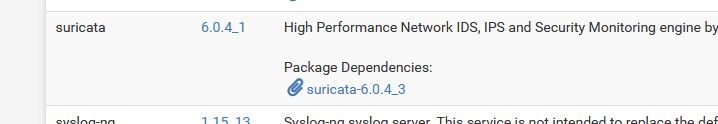
I noticed in your screen shot that suricata Package Dependencies shows suricata-6.0.4_3 but on my system running Suricata 6.0.4_1 on pfsense 2.6.0 CE package manager shows dependencies as suricata-6.0.4,
Am I missing something or is my system corrupted?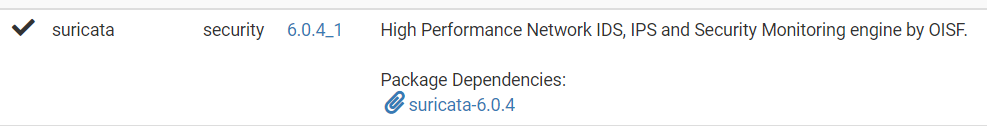
-
@jdeloach said in Suricata dont block Torrents:
Am I missing something or is my system corrupted?
My screen shot was taken on a 22.05 (pfSense+) which is very close to 2.6.0.
This might explain the difference.
@bmeeks would know more about this ;) -
-
Those minor sub-version updates of the binary (the _x values) are coming from changes in dependencies in the FreeBSD Ports tree. For example, Rust is getting frequent updates, and Rust is a dependency of the Suricata binary. So, whenever Rust is updated the Suricata binary has to be recompiled against the new Rust version.
There is really no change to the binary functionality itself, though. The only exception would be if the Rust update was correcting some major flaw. But even there, the use of Rust within Suricata is still somewhat limited to only the newly added protocol decoders.
There are two parts of the IDS/IPS packages. One is the PHP GUI component and the other is the underlying binary component that does the actual work of inspecting traffic and generating alerts and blocks. The sub-version increments for the GUI component do mean PHP code changes. For Suricata, I keep the first part of the package version matching the underlying binary. So if the pfSense Package Manager GUI shows the package as 6.0.4_1, that means the associated binary version is 6.0.4, but the 6.0.4_1 indicates at least one code revision in the PHP has happened since the initial release of the base version (initially the PHP package version would have been 6.0.4 to match the binary).
To help clarify what you are seeing in the screenshots above, the main display row with the checkmark, the word "suricata", then "security", and a version is showing the PHP GUI package version. That is the actual package pfSense is tracking. Underneath that row, in the "Package Dependencies" section, it is showing any associated binary parts and pieces that get installed along with the PHP GUI portion.
-
@bmeeks But I dont see options to update to newer revisions like _4
-
@cool_corona said in Suricata dont block Torrents:
@bmeeks But I dont see options to update to newer revisions like _4
You stated you are running pfSense 2.5.2. As has been stated here on the forums many times, once pfSense is updated, the package tree for the former version is frozen and receives no further updates. So 2.5.2 pfSense will never receive any of the Suricata updates that 2.6.0 CE and 22.05 pfSense Plus will get (until they are no longer the current release). And once 2.6.0 is updated by a newer release, then its package tree will also be frozen at whatever version it has on the day of the update.
There is a separate directory of packages for each pfSense version. But only the current pfSense version tree is updated and recompiled against the new baseline pfSense version. Any older versions are frozen and get no further updates.
And you can't install packages compiled for the newer (current) pfSense version on an older version as that is highly likely to break your installation due to the dependent library versions being different.
So while you may have a reason for staying on pfSense 2.5.2, the downside that comes with that choice is you can't see- nor install- any of the updated packages in the Ports tree.