Is it possible?
-
Curious but what would it take to get payload detail into the output of an alert
Reviewing another open-source firewall i did notice that payload viewing is possible within the alert as seen below Curious as to how much work would be involved. If anything i would like to be involved in the project if its already in the works for future releases.
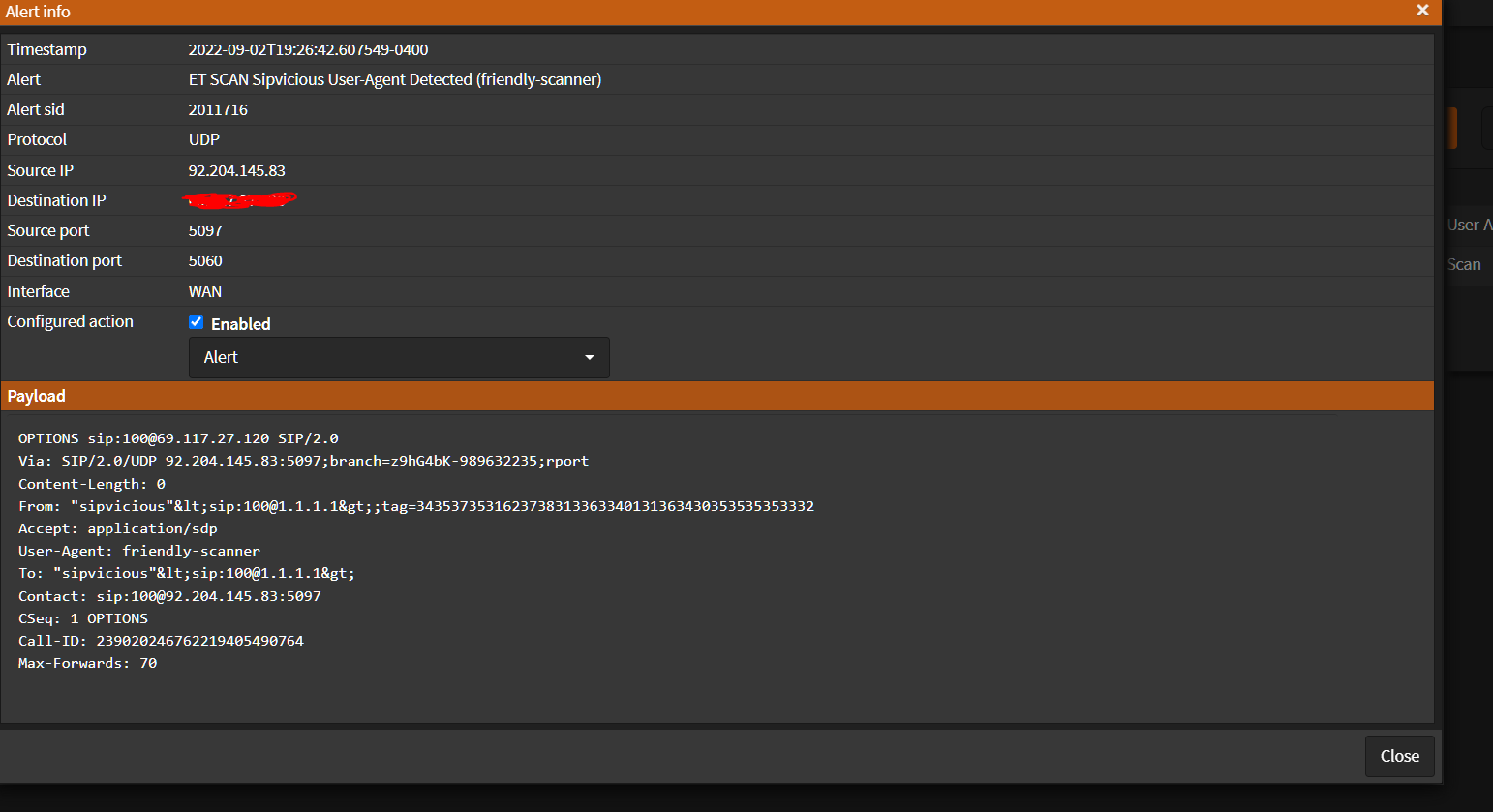
-
There is an option to enable packet payload logging in the EVE LOG parameters on the INTERFACE SETTINGS tab in Suricata. That will write the payload as Base64-encoded text to the EVE JSON log.
But the ALERTS tab in Suricata currently does not parse the EVE JSON log. It parses and displays alerts from a separate fast text log. So in order to display payload data all of the ALERTS tab code would have to be rewritten to reference and decode the EVE JSON log files instead of the fast text log. One problem with those JSON files is they get very large very fast and are thus frequently rotated. That means displaying a longer history of alerts would require unpacking and searching through previously rotated JSON logs.
None of the above is an impossible task, but could be somewhat resource intensive on more marginal hardware. The general opinion for IDS/IPS logging on pfSense is that you export the EVE JSON logs to a separate server for analysis. Something like an ELK stack or equivalent. I believe some users here previously have done something similar by installing the filebeat package from FreeBSD Ports and using it to export to another log analysis server.
There are also several other options as discussed in this thread from 2020 on the Redis forum: https://discuss.elastic.co/t/suricata-redis-elk-stack-mapping-help-please/250860. And the Suricata package on pfSense now has a Redis output option (on the INTERFACE SETTINGS tab for each interface).
-
@bmeeks I can definitely attest to the fact that those JSON logs rack up very quickly. Bzip2 was the top running process on my box for some time.
So instead of logging locally, it might just be better to SPAN the port and send to my security onion or graylog - basically something that can make sense of the data.Thanks for your input on this. I was really curious if the function could be written but not right now.