OpenVPN Client working, but other ports & VLANs now offline
-
one more screenshot I forgot to add.
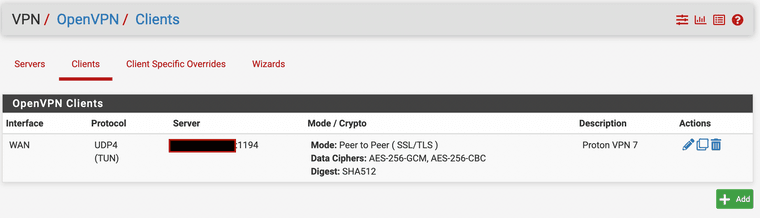
-
@pourts
What's your intention regarding the VPN client?
Routing all upstream traffic over the VPN or only specific sources? -
@viragomann
Only route the traffic plugged into physical LAN port #1 (which is also VLAN 4081, because the netgate 2100 is weird and the ports don't really exist unless they are VLANs).Things plugged into LAN 2 thru 4 (which are VLAN 4082-4084) I want to be routed normally without the VPN client.
-
@pourts
So you probably want to go with policy routing.And 192.168.50.0/24 is your LAN, I guess, since you have an outbound NAT rule for it on the VPN interface?
With that you should at least have internet access from the LAN, don't you?To avoid to change the default route by OpenVPN, you have to check "Don't pull routes" in the client settings.
-
@viragomann thank you for the help so far.
"Don't pull routes" was unselected. When I click that box, now everything outbound is dead. So, I think something is wrong with how my VPN client is setup
My understanding is the following:
192.168.49.1 is the firewall hardware itself
192.168.50.XXX is for anything in VLAN 4081, which is physical port 1.
192.168.100.XXX is for anything in VLAN 4082, which is physical port 2.
192.168.150.XXX is for anything in VLAN 4083, which is physical port 3.
192.168.200.XXX is for anything in VLAN 4084, which is physical port 4.Honestly I don't know the difference between LAN and my 4 VLANs. Do the 4 VLANs all combine into the LAN, then out to WAN?
I'm not trying to do anything very custom or complicated, this is just what was shown in the Netgate 2100 documentation and various Lawrence Systems tutorials on YouTube. Thank you all for helping me learn.
-
@pourts
"Don't pull routes" instructs pfSense to not add routes, when the OpenVPN client connects. So everything should behave as the client was disabled.I'm not familiar with the switch configuration of the Netgate 2100. If you have trouble with it and want to get help, you should open a separate thread.
-
@viragomann
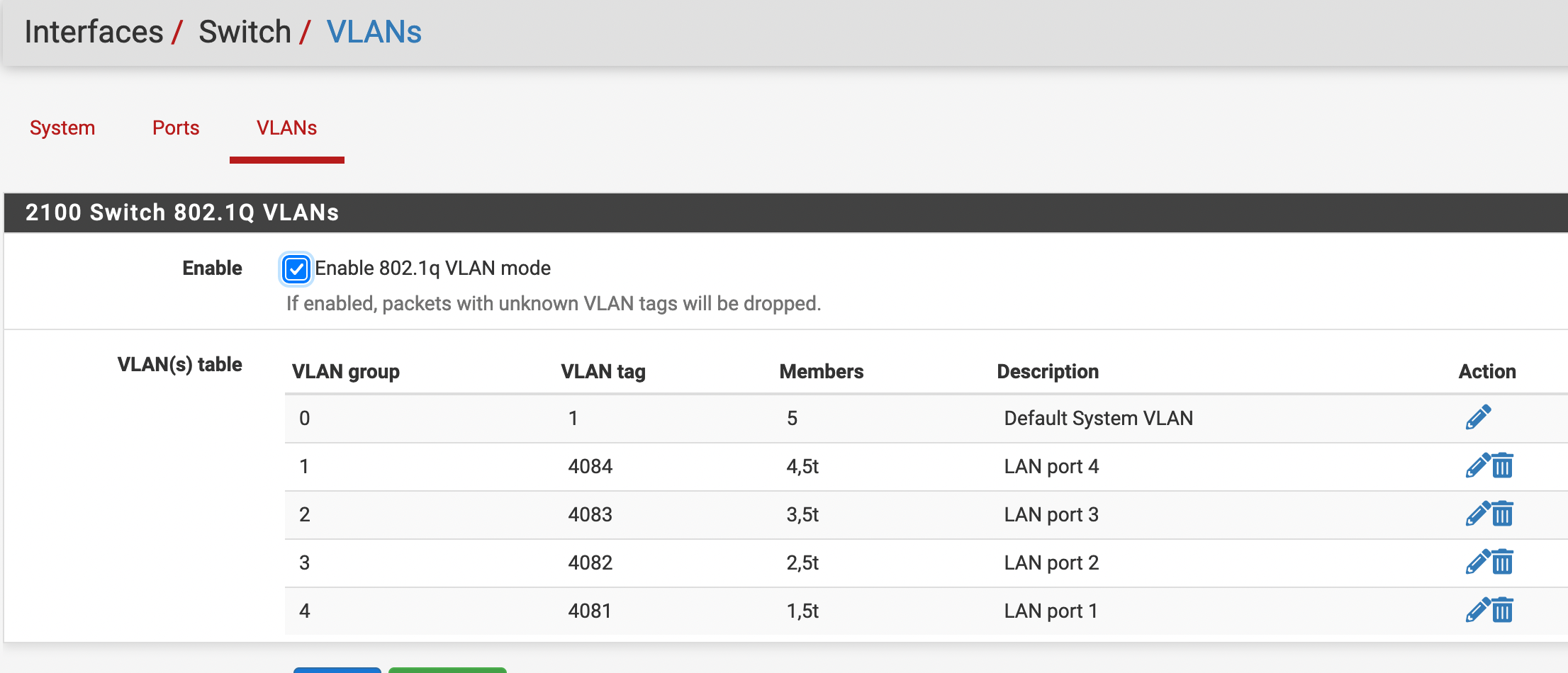
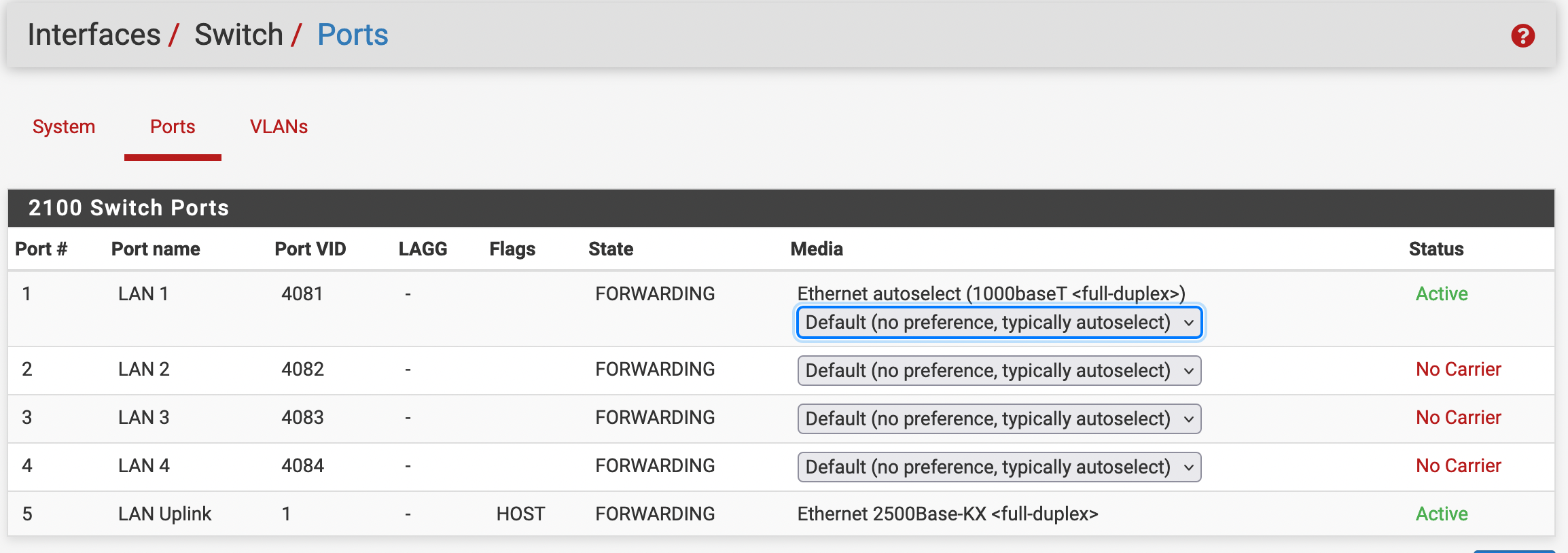
Perhaps I should restate the question:I have a VLAN defined, but it cannot reach the internet. Any ideas what I have wrong? I followed the guide in the Netgate 2100 docs.
I have called it VLAN 4082
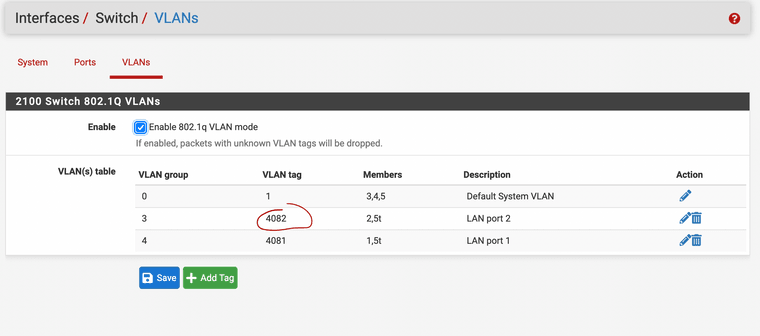
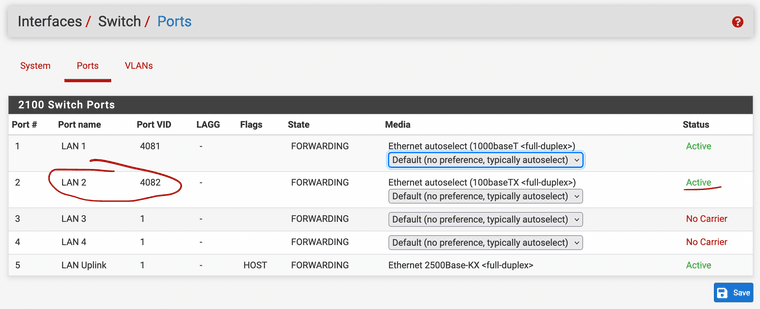
Assigned that VLAN to physical port #2
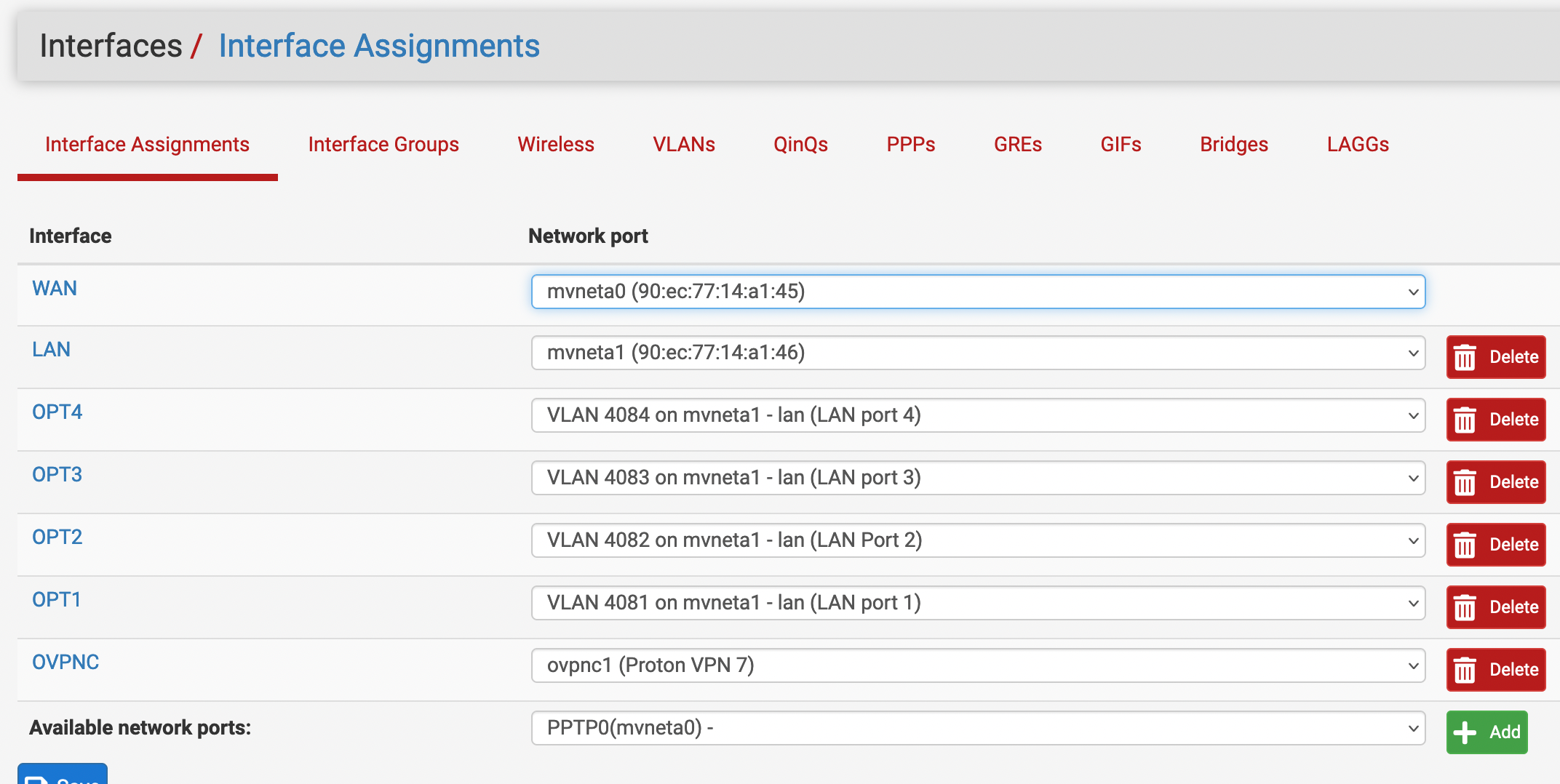
Created the VLAN interface. I have a Netgate 2100, so the only actual switches are mvneta0 (for WAN) and mvneta1 (for everything else.
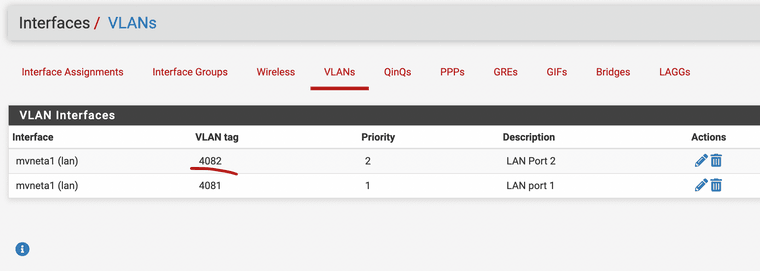
VLAN interface assigned

VLAN interface details:
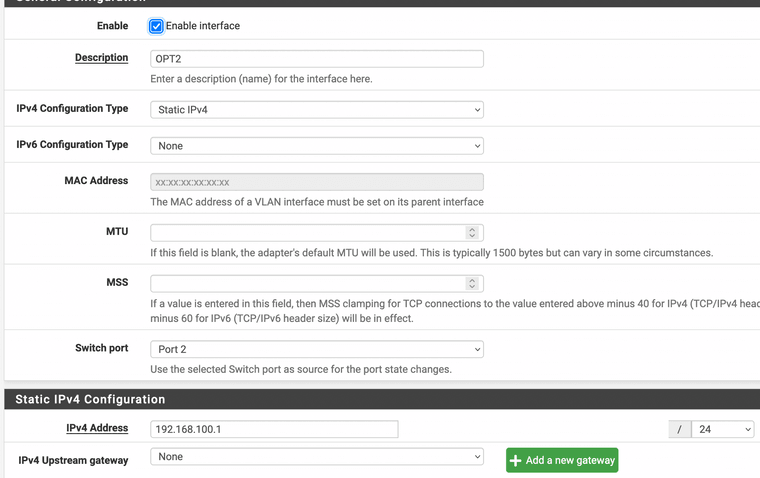
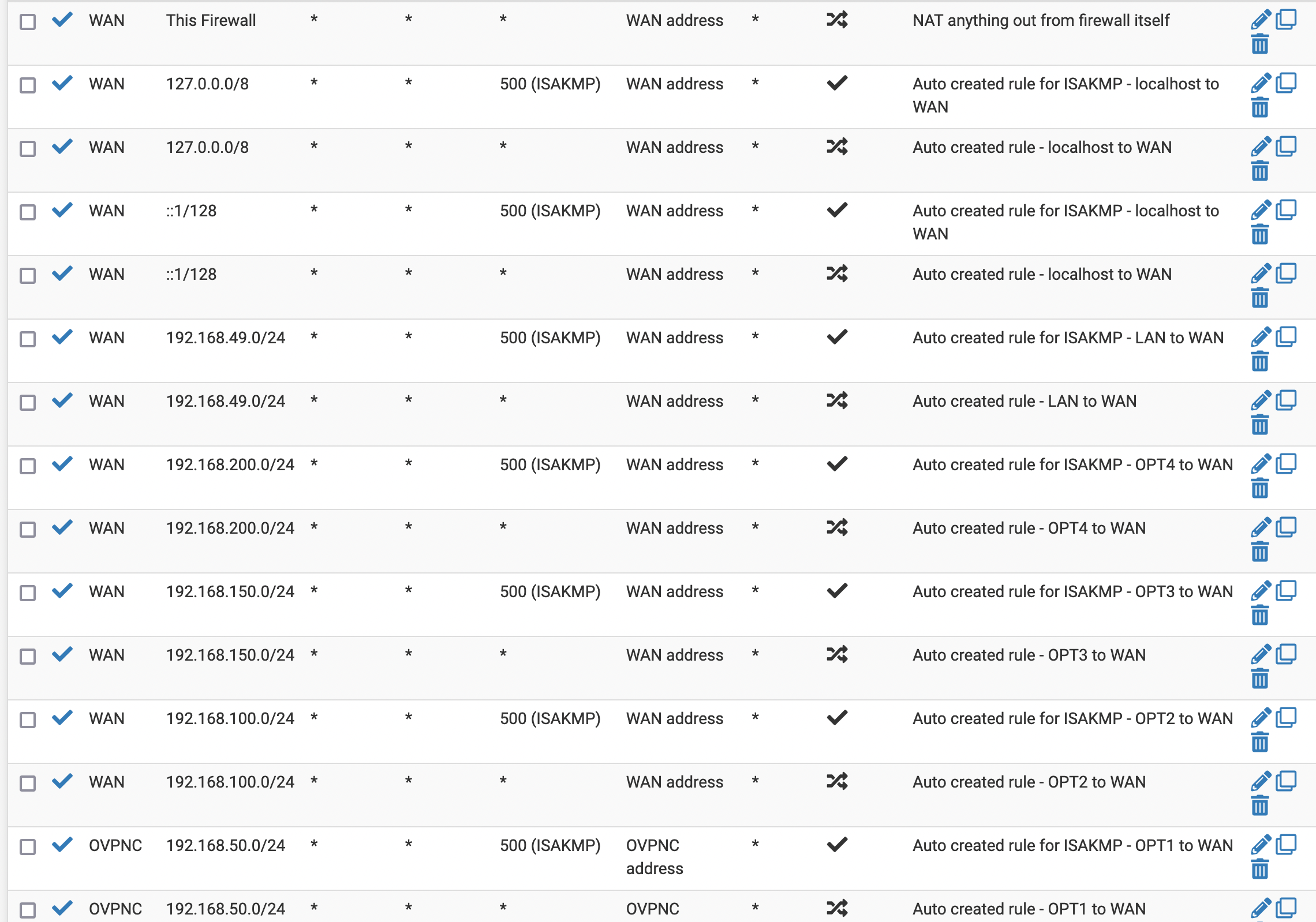
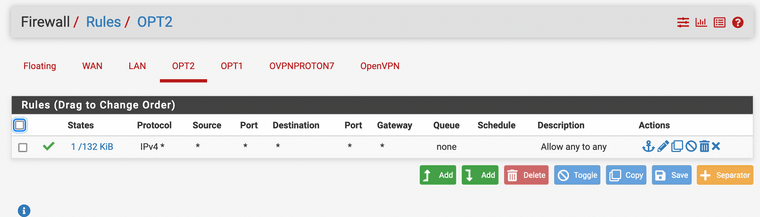
Firewall rules:
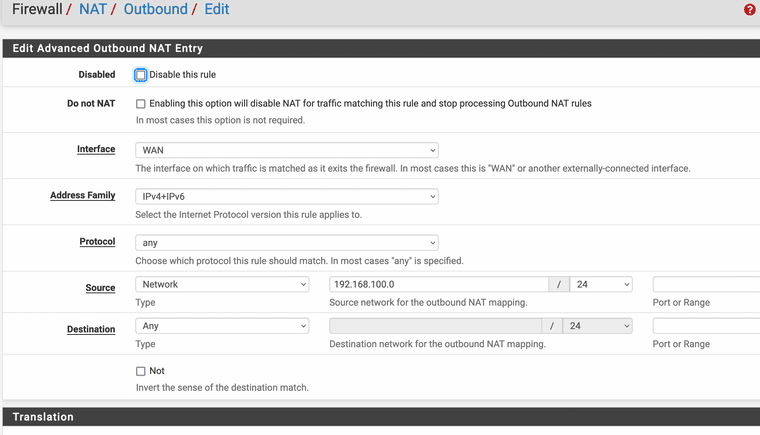
Outbound NAT for OPT2 (which is VLAN 4082, port #2) to WAN
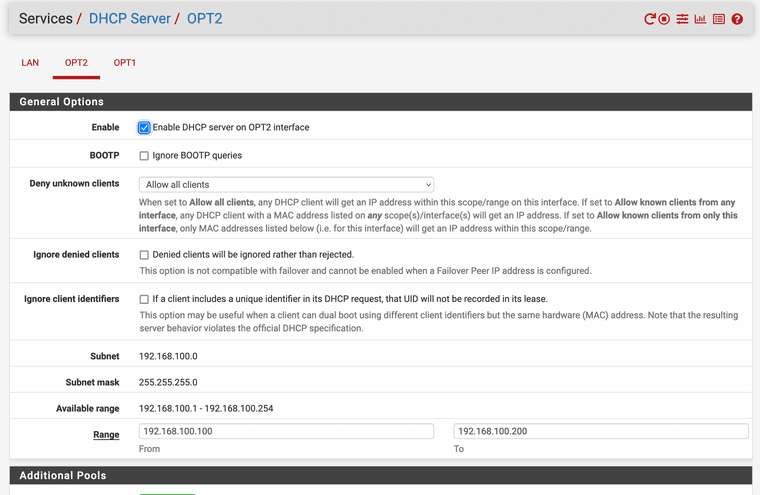
DHCP server looks good:
Thanks in advance!
-
@pourts Don't do manual outbound NAT, use hybrid instead. What is in floating rules?
-
@bob-dig
Apologies... I was having problems with the Akismet spam filter.I changed to Hybrid NAT.
No floating rules at all. Zero. Should I have some? -
P pourts referenced this topic on
-
@pourts if your not going to pull routes from the vpn client.. Which to be honest is better way, since now you can policy route the specific clients or sure a whole vlan out the vpn.. While your non vpn clients would just use your normal isp connection.
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html
And yes the hybrid outbound nat is also a better option.. This way if you add new vlans, they will auto get added, etc. All you have to worry about is your hybrid nat for clients you want to send out the vpn via your policy route.
edit: here you go, see hybrid nat that includes all my local networks, since they are all 192.168 address. I can then policy route anything I want out the vpn
So see my normal IP, then I created a policy route for my .100 pc.. Then I when somewhere new so a new state was created an it was routed out my vpn connection
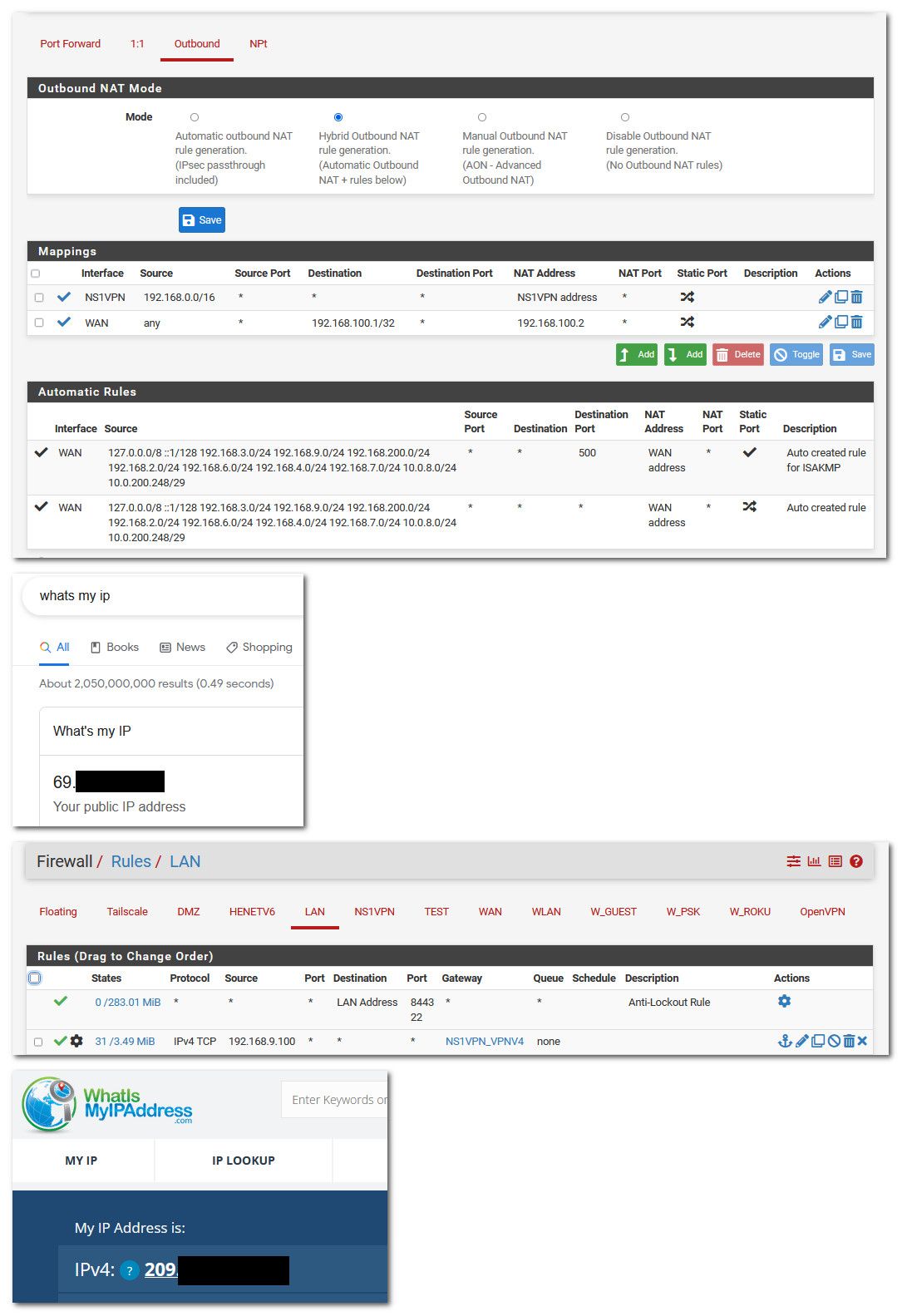
Just going to a different site for my public IP was easier then killing my machines existing states..
-
@johnpoz Success! Thanks for the help. It took me a couple times to understand what was meant by policy routing, because "policy routing" isn't an option in any of the GUI menus.
Thanks for linking the chapter in the Docs about policy routing.
-
@pourts said in OpenVPN Client working, but other ports & VLANs now offline:
because "policy routing" isn't an option in any of the GUI menus.
Sure it is ;) The gateway you want to send the traffic out of is policy routing ;)
Glad you got it sorted.
Hope you paid attention to the bypassing policy routing in that section, users always seem to fail to understand if you force traffic out say a vpn gateway, that it won't be able to get to your other vlans/networks that are local. So you have to have a rule above your policy route rule that allows for access you want locally.