Alias Native not combining ASN enumeration with custom list in same rule
-
I have an IPv4 list which contains a list of ASN which are being retrieved and enumerated properly. It's marked as Alias Native.
But in that list of ASNs I have a custom CIDR list in the same rule in the section at the bottom in the "IPv4 Custom_List" area containing a list of CIDR networks, one per line.
It seems that the custom addresses are not being added to the Alias. I've had to create a new rule just with the IPv4 Custom_List and then have two f/w rules on the same i/f.
Am I doing it wrong? Should I be able to do this in one Alias list?
-
Here I list 3 ASNs:
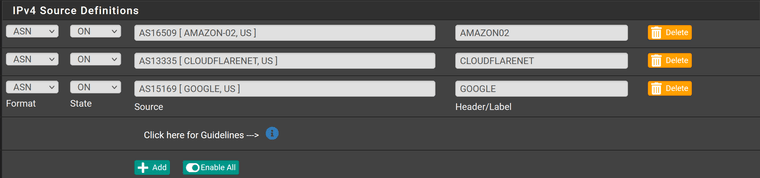
Then I add manual CIDRs to the custom section:
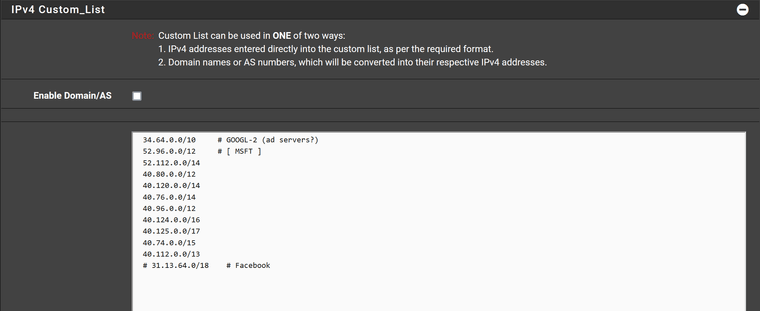
But in the resulting Alias file the custom CIDRs are NOT there:
File successfully loaded: Total Lines: 3318
Log/File Path: /var/db/aliastables/pfB_ASN_List_v4.txt... 8.48.132.0/23 8.48.134.0/24 23.227.37.0/24 23.227.38.0/23 64.68.192.0/24 65.110.63.0/24 66.235.200.0/24 68.67.65.0/24 91.234.214.0/24 103.21.244.0/24 103.22.200.0/23 ... -
@lohphat I just duplicated what you showed and not having any issues. Did you actually enable the list?
Did you look at the right table under diagnostics?
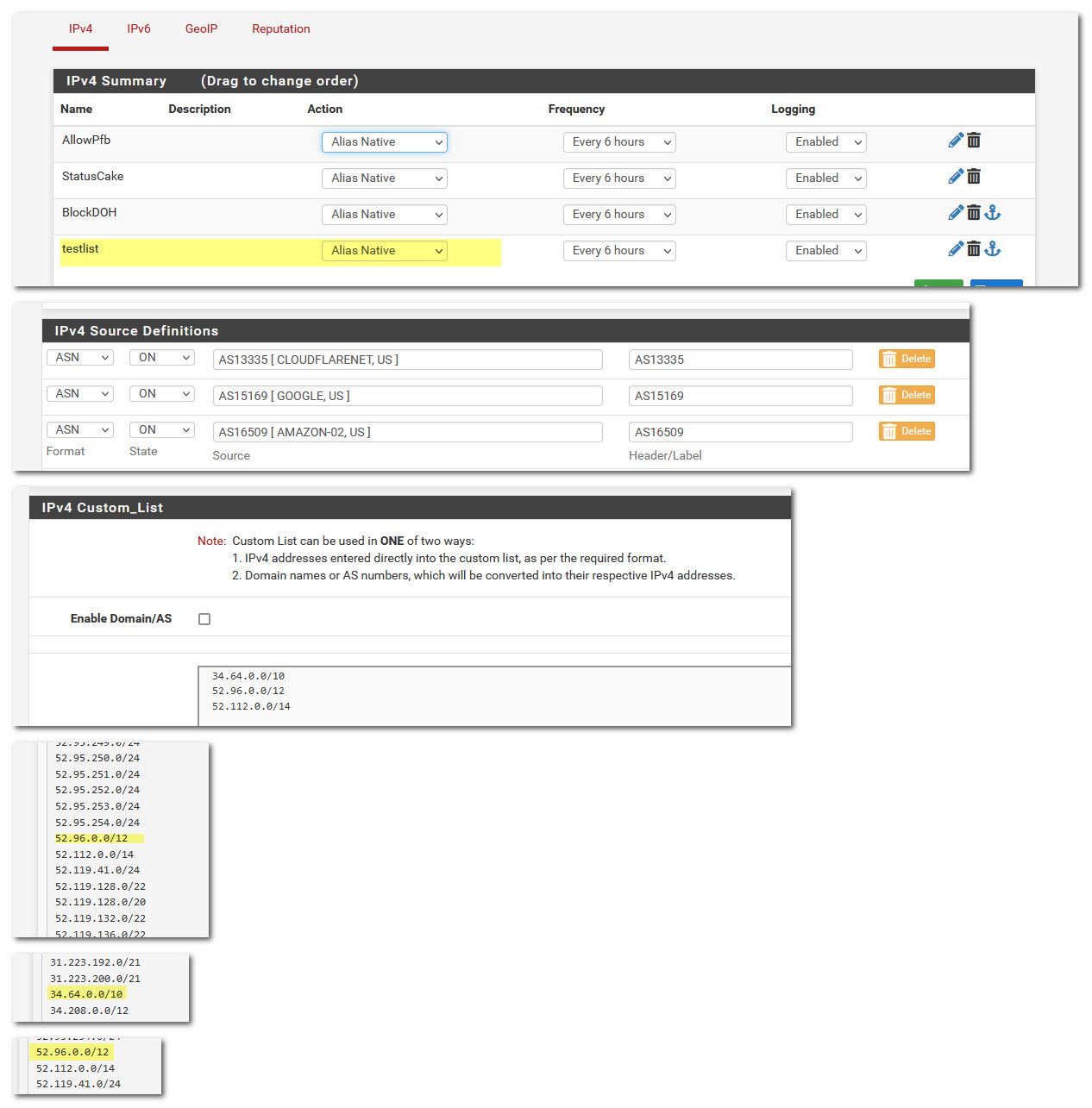
-
@johnpoz Yes, or I wouldn't have been able to paste from the resulting alias.
-
@lohphat what you posted is no where close to have downloaded those ASNs I thought I showed like 8000 some entries..
I can not duplicate your problem..
-
@johnpoz I just pasted the segment of where the CIDRs should have been. The alias is 3318 lines now,
Alias table IP Counts ----------------------------- 23826 total 16716 /var/db/aliastables/pfB_PRI1_v4.txt 3763 /var/db/aliastables/pfB_ASN_List_v6.txt 3318 /var/db/aliastables/pfB_ASN_List_v4.txt 16 /var/db/aliastables/pfB_PRI1_6_v6.txt 11 /var/db/aliastables/pfB_ASN_List_CIDR_v4.txt 2 /var/db/aliastables/pfB_ASN_List_CIDR_v6.txt -
@lohphat I show way more IPs in those ASNs
[ AS16509_v4 ] Downloading update . Downloading ASN: 16509... completed . completed .. [ AS13335_v4 ] Downloading update [ 10/15/22 13:27:59 ] . Downloading ASN: 13335... completed . completed .. [ AS15169_v4 ] Downloading update [ 10/15/22 13:28:01 ] . Downloading ASN: 15169... completed . completed .. ===[ Aliastables / Rules ]========================================== No changes to Firewall rules, skipping Filter Reload Updating: pfB_asntest_v4 1 table created.9753 addresses added.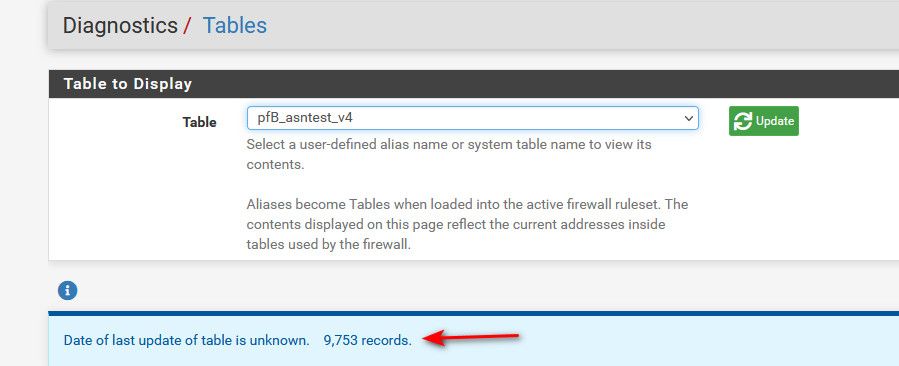
-
@johnpoz Could it be that the "#" comments are throwing it off? There's no help text I can find about that section even though it mentions "IPv4 addresses entered directly into the custom list, as per the required format." but doesn't say what the "required format" is.
-
@lohphat If you don't know, you ain't worthy.

-
@johnpoz said in Alias Native not combining ASN enumeration with custom list in same rule:
13335
I have De-Duplication and CIDR Aggregation enabled too.
[ AS16509_v4 ] Downloading update [ 10/15/22 15:12:43 ] . Downloading ASN: 16509... completed . completed .. Aggregation Stats: ------------------ Original Final ------------------ 7329 2902 ------------------ [ AS15169_v4 ] Downloading update [ 10/15/22 15:12:49 ] . Downloading ASN: 15169... completed . completed .. Aggregation Stats: ------------------ Original Final ------------------ 818 84 ------------------ [ AS13335_v4 ] Downloading update [ 10/15/22 15:12:51 ] . Downloading ASN: 13335... completed . completed .. Aggregation Stats: ------------------ Original Final ------------------ 1606 361 ------------------ [ ASN_List_custom_v4 ] Reload [ 10/15/22 15:12:53 ] . completed .. -
OK, I think I found the core problem: partial PEBKAC
Where I was looking for the custom CIDR blocks was in "Firewall / pfBlockerNG / Log Browser" not in "Diagnostics / Tables".
The custom CIDRs are correctly listed in the latter in a correctly sorted order.
BUT they ARE in the "Firewall / pfBlockerNG / Log Browser" at the END of the file, partially sorted. The Custom list is sorted but just appended to the main file.
Completely unexpected behavior.
I was unaware of the "Diagnostics / Table" section and didn't expect a difference in content.
-
@lohphat said in Alias Native not combining ASN enumeration with custom list in same rule:
I was unaware of the Diagnostics / Table" section .....
Don't feel bad, I was also not aware of the Diagnostics/Table section either, but THANKS to @johnpoz , I learned something new today as well.
-
Shouldn't the CIDR aggregation merge these 2607:f8b0:4000:: CIDRs into the main 2607:f8b0::/32 network?
From: PfB_ASN_List_v6 Table
2607:f8b0::/32 2607:f8b0:4000::/48 2607:f8b0:4001::/48 2607:f8b0:4002::/48 2607:f8b0:4003::/48 2607:f8b0:4004::/48 2607:f8b0:4005::/48 2607:f8b0:4006::/48 2607:f8b0:4007::/48 2607:f8b0:4008::/48 2607:f8b0:4009::/48 2607:f8b0:400a::/48 2607:f8b0:400b::/48 2607:f8b0:400c::/48 2607:f8b0:400d::/48 2607:f8b0:400e::/48 2607:f8b0:400f::/48 2607:f8b0:4010::/48 2607:f8b0:4011::/48 2607:f8b0:4012::/48 2607:f8b0:4013::/48 2607:f8b0:4014::/48 2607:f8b0:4015::/48 2607:f8b0:4016::/48 2607:f8b0:480e::/48 2607:f8b0:480f::/48 2607:fb90:c150::/48 -
@lohphat said in Alias Native not combining ASN enumeration with custom list in same rule:
2607:f8b0::/32
yeah you would think.. @BBcan177 would know ;) I don't really load any IPv6 addresses into pfblocker at all.
-
@johnpoz Given that aggregation stats are given in the logs when IPv4 ASNs are downloaded but not IPv6 ASNs, it may be that aggregation only applies to IPv4 at this time. The settings descriptions need updating to reflect this apparent limitation.
IPv4 update log:
[ AS16509_v4 ] Downloading update [ 10/15/22 19:24:44 ] . Downloading ASN: 16509... completed . completed .. Aggregation Stats: ------------------ Original Final ------------------ 7329 2902 ------------------ [ AS13335_v4 ] Downloading update [ 10/15/22 19:24:50 ] . Downloading ASN: 13335... completed . completed .. Aggregation Stats: ------------------ Original Final ------------------ 1606 361 ------------------ [ AS15169_v4 ] Downloading update [ 10/15/22 19:24:52 ] . Downloading ASN: 15169... completed . completed .. Aggregation Stats: ------------------ Original Final ------------------ 818 84 ------------------ [ ASN_List_custom_v4 ] Reload [ 10/15/22 19:24:54 ] . completed ..IPv6 update log:
[ AS8075_v6 ] Downloading update . Downloading ASN: 8075... completed . completed .. [ AS13335_v6 ] Downloading update [ 10/15/22 19:24:55 ] . Downloading ASN: 13335... completed . completed .. [ AS15169_v6 ] Downloading update [ 10/15/22 19:24:57 ] . Downloading ASN: 15169... completed . completed .. [ AS16509_v6 ] Downloading update [ 10/15/22 19:24:58 ] . Downloading ASN: 16509... completed . completed .. [ ASN_List_custom_v6 ] Reload [ 10/15/22 19:25:33 ] . completed ..Note the lack of "Aggregation Stats" in the IPv6 logs.
-
@lohphat said in Alias Native not combining ASN enumeration with custom list in same rule:
Note the lack of "Aggregation Stats" in the IPv6 logs.
There are probably a lot of things to do with IPv6 in this package that are not implemented yet because IPv6 is still fairly new and not that widely used. I wouldn't expect those updates to be done for another year or so given that the maintainer of this package, @BBcan177 , has limited time right now to devote to this package. He is quite busy working other things.
I would say to just post any issues you find with IPv6 and he will work them as time permits. -
@jdeloach I understand. But if simple updates to UI text to set expectations and clarify before features are implemented, that seems a reasonable course.
I'm from the world of software development so I do understand the pressures, but small incremental changes can make a big difference.
IPv6 is here and if you network can handle it, the large players are using it (e.g. YouTube content), and some countries ONLY have IPv6 addressing. We have to get used to it sooner than later.
-
@jdeloach said in Alias Native not combining ASN enumeration with custom list in same rule:
IPv6 is still fairly new and not that widely used.
Not sure if 20 some years counts as fairly new ;) Arin made their first assignments of IPv6 back in 1999. But not that widely used I would agree with.. We all get it, its the future.. But currently to be honest, there is zero reason to have it, other than a learning tool.
Name 1 actual resource that would require you to have it? Just one, been asking that question for years here, and have yet to get an answer..
I am all for moving towards it, and I have been playing with it for 13 years + but have yet to find and actual requirement that says yeah I have to have that.. My isp currently doesn't even provide it. I get my ipv6 from a HE tunnel.
Sure in some parts of the world - hey that is what the ISP gives you.. And then they convert your ispv6 to an ipv4 on their network via say 464XLAT. And with the billions of phones on the globe yeah ipv4 isn't going to cut it.. Now think about cars all being connected as we move towards self driving, etc. IPv4 can't really handle that.. But, still - what actual main public resource requires IPv6? Name one?? Name one game that requires you to have IPv6 to play on your consoles.. And that really should be a driving force for people demanding IPv6 from their ISPs, etc.
We are like 20 years in, and ISPs still can not get it right.. Hand your users a /48 prefix, assign that to them.. So it doesn't change every other day.. Let them do with that what they will.. Its not like there is not enough already assigned IPv6 space to give like everyone on the planet 4000 some /48's each. Or a /56 or even a /60 for gosh sake.. And the amount of available IPv6 is just the very tip of the iceberg of the total available space, etc. But ISP continue to hand out single /64s that change when the wind blows, etc.
If you are new to IPv6, be ready for a learning curve, be ready for issues and problems - Its just much easier to just not use it, unless your stuck with it - ie your in some isp that won't actually give you a public IPv4, and you want to have inbound unsolicited traffic. And then just hope your users that want to access your resource actually have IPv6, or are smart enough to setup a IPv6 tunnel, etc.
Sorry IPv6 is one of those topics that just drives me nuts, especially after a few cocktails ;) I want it to move forward, I want it to be done right, but I have been banging my head against a wall for like 10 years at work, and have yet to see progress - and I work for a major player.. And have seen no real progress other than in the mobile device space. Finally a year or so ago I got to assign a /32 from arin for use in some car related project - that has not gone anywhere really.
-
@johnpoz I agree. I owe you some cocktails for all the sh!t I've stirred up anyway.

I view IPv6 akin to saying please and thank you -- you don't NEED to use them, but it makes the world a better place if you do. It's not about either/or IPv4 vs IPv6 it's AND.
I've been beating on IPv6 for years too but I'm lucky my ISP supports it and pissed that FiOS STILL doesn't in many markets (but that's changing).
Local nets and IoT will be using IPv4 NAT (RCT1918) for the foreseeable future, but like any new thing, the more we encourage its use, the sooner well get there.
More than 40% of users hitting Google are IPv6 clients. It's no longer a "niche":
And in the US and EU , the adoption rate is more than 50%:
-
@johnpoz said in Alias Native not combining ASN enumeration with custom list in same rule:
But, still - what actual main public resource requires IPv6? Name one?? Name one game that requires you to have IPv6 to play on your consoles..
I can't but many people will have to use IPv6 to vpn into their own homes in the near future around my place.
And pfSense is not doing a great job regarding dynamic IPv6, so the people in this forum might be last ones, who will be using IPv6. I reduced it to one host at home.
dhcpd is almost eol so I hope we get better dynamic IPv6 support in the future?!