Peer to Peer routing unidirectionally
-
Description of issue:
No clients from HQ, even the OVPN server itself reach networks at the remote site, even when routes are pushed from the server and they appear to be correct (please correct me). Remote site clients are able to reach all HQ networks from the remote site (NAS, servers, routed Internet)
Description of network/routing:
- pfSense gateways at both ends with minimal OpenVPN Peer to Peer setup. Configuration in screenshots below
- Client WAN traffic at remote site is routed through OVPN connection to HQ, works brilliantly
- Unreachable LAN clients at the remote site are at 10.10.10.0/24 and 10.20.20.0/24
- Tunneled network is an unnecesary large /24 network, should not be relevant
Other relevant finds:
-
The OVPN server itself is unable to ping clients at the remote site. Nothing shows up in the firewall logs at either side
-
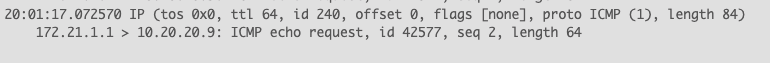
Packet capture at the remote (client) site shows absolutely zero traffic even if the server routes traffic to its OpenVPN network address. Packet capture from HQ shows the ICMP packets on the OVPN server interface:
Other relevant settings:
-
"Allow all-rules at both ends on the OpenVPN tab (not the OpenVPN optional interface)"
-
LAN firewall rules at remote site to force all LAN traffic to use OVPN interface as the gateway
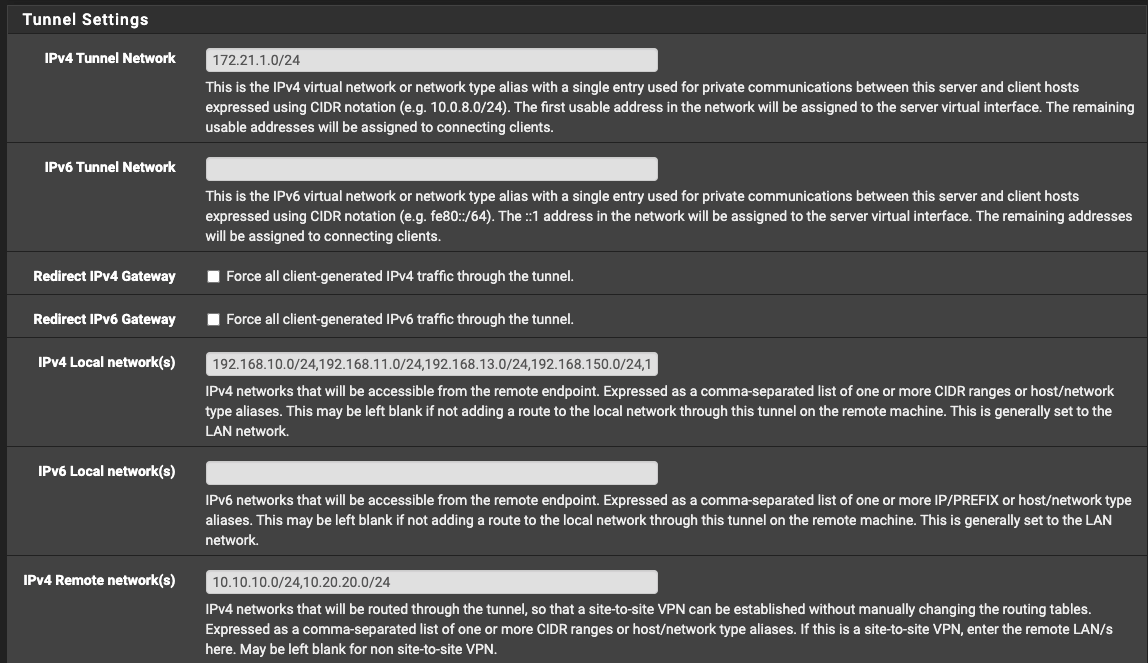
Server settings at HQ:
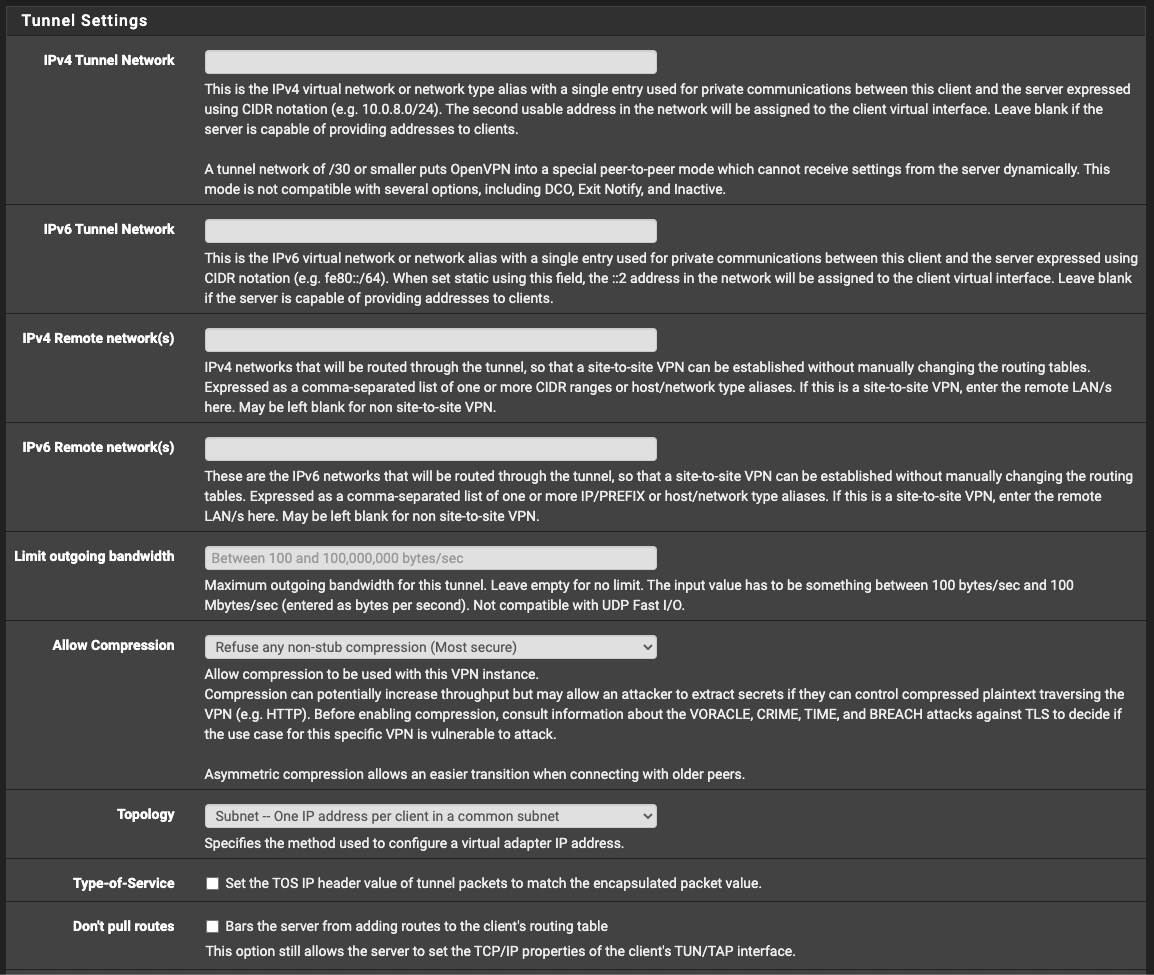
Client settings at remote site, where all traffic is routed through HQ:
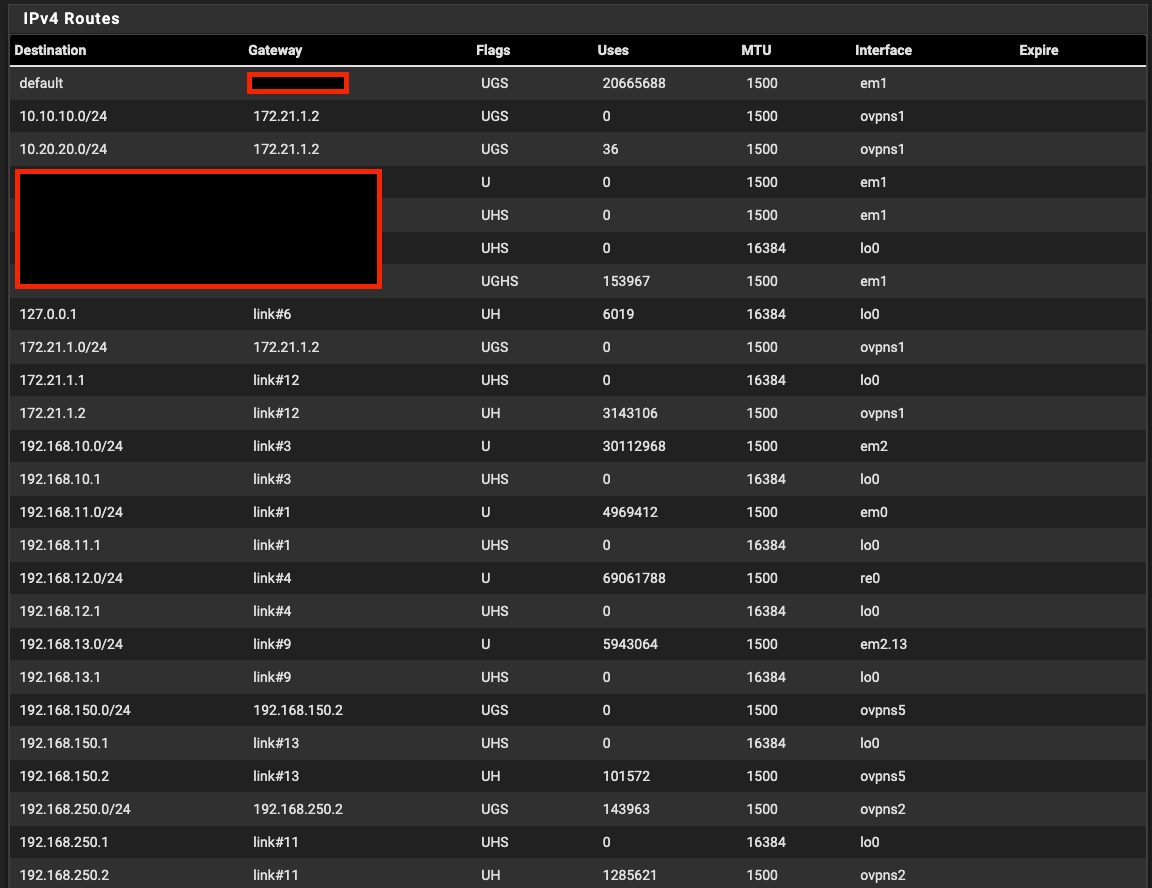
Routes at HQ, OVPN server. Notice how the route for 10.20.20.0/24 has the IP address of the remote site OpenVPN client in the OpenVPN tunnel network listed (172.21.1.2):
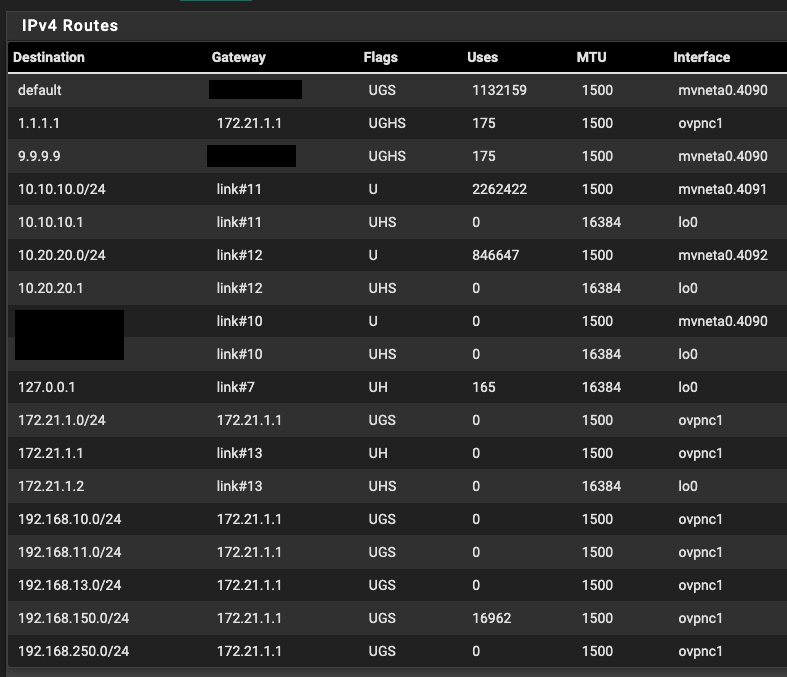
Routes at remote site, OVPN client:
I have spent tens of hours troubleshooting and reading great posts by this awesome community here and on Reddit, but I am running out of ideas. Help would be greatly appreciated
-
@aviatorpaal
First, it's a peer to peer, you need to use a /30 or /31 as tunnel. Otherwise you need client specific overrides, so the tunnel is relevant actually.Second, you have no settings on the client side.
Fill in the tunnel, and remote networks.
OpenVPN sets routes for you by those settings. -
This post is deleted! -
Thanks for suggesting this solution, I believe everything is working now!
Netgate docs, in their configuration example unfortunately uses a /24 as the tunnel network, which led to the confusion:
Routes are now setup as you described and I am able to ping clients from both sides of the firewalls.
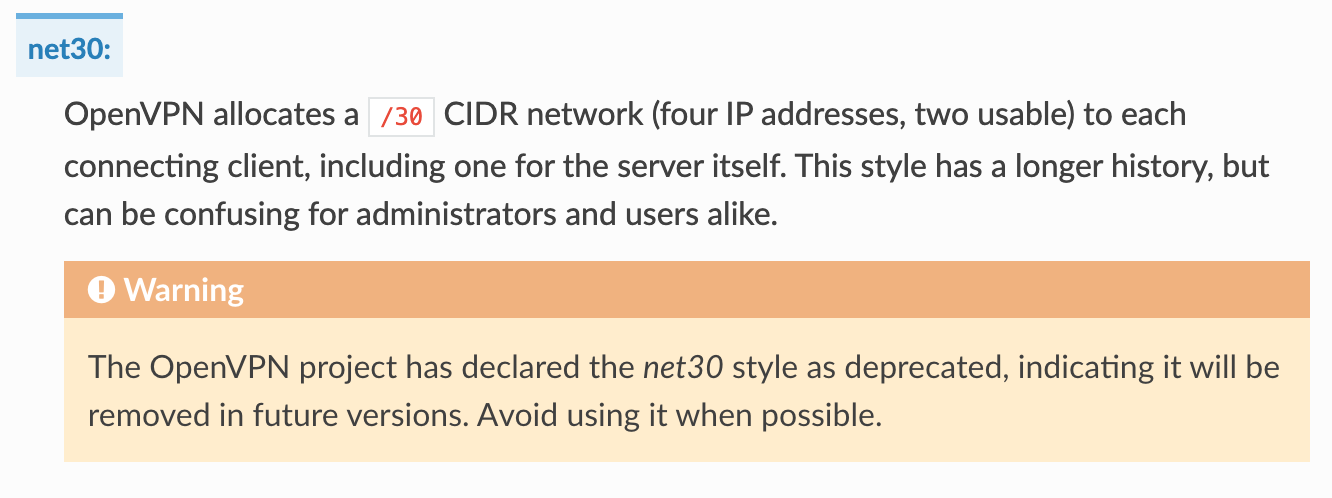
Note: I did not use the "net30" topology option, as this will be deprecated, according to pfSense:
-
@aviatorpaal said in Peer to Peer routing unidirectionally:
Netgate docs, in their configuration example unfortunately uses a /24 as the tunnel network, which led to the confusion:
You should read the whole document: