$10 BTC Bounty: Squid Proxy - Whitelist Per Source IP
-
Think I'm going coocoo a bit here.
If
denyis set in Groups ACL -Default access [all] access deny, nothing passes (curl example.org):<div id="content"> <p>The following error was encountered while trying to retrieve the URL: <a href="https://https/*">https://https/*</a></p> <blockquote id="error"> <p><b>Unable to forward this request at this time.</b></p> </blockquote> <p>This request could not be forwarded to the origin server or to any parent caches.</p> <p>Some possible problems are:</p> <ul> <li id="network-down">An Internet connection needed to access this domains origin servers may be down.</li> <li id="no-peer">All configured parent caches may be currently unreachable.</li> <li id="permission-denied">The administrator may not allow this cache to make direct connections to origin servers.</li> </ul> <p>Your cache administrator is <hidden></a>.</p> <br> </div> <hr> <div id="footer"> <p>Generated Wed, 05 Oct 2022 05:52:46 GMT by baseplate (squid)</p> <!-- ERR_CANNOT_FORWARD --> </div> </body></html>
If
allowis set in Groups ACL -Default access [all] access allow, literally everything passes.
My config:
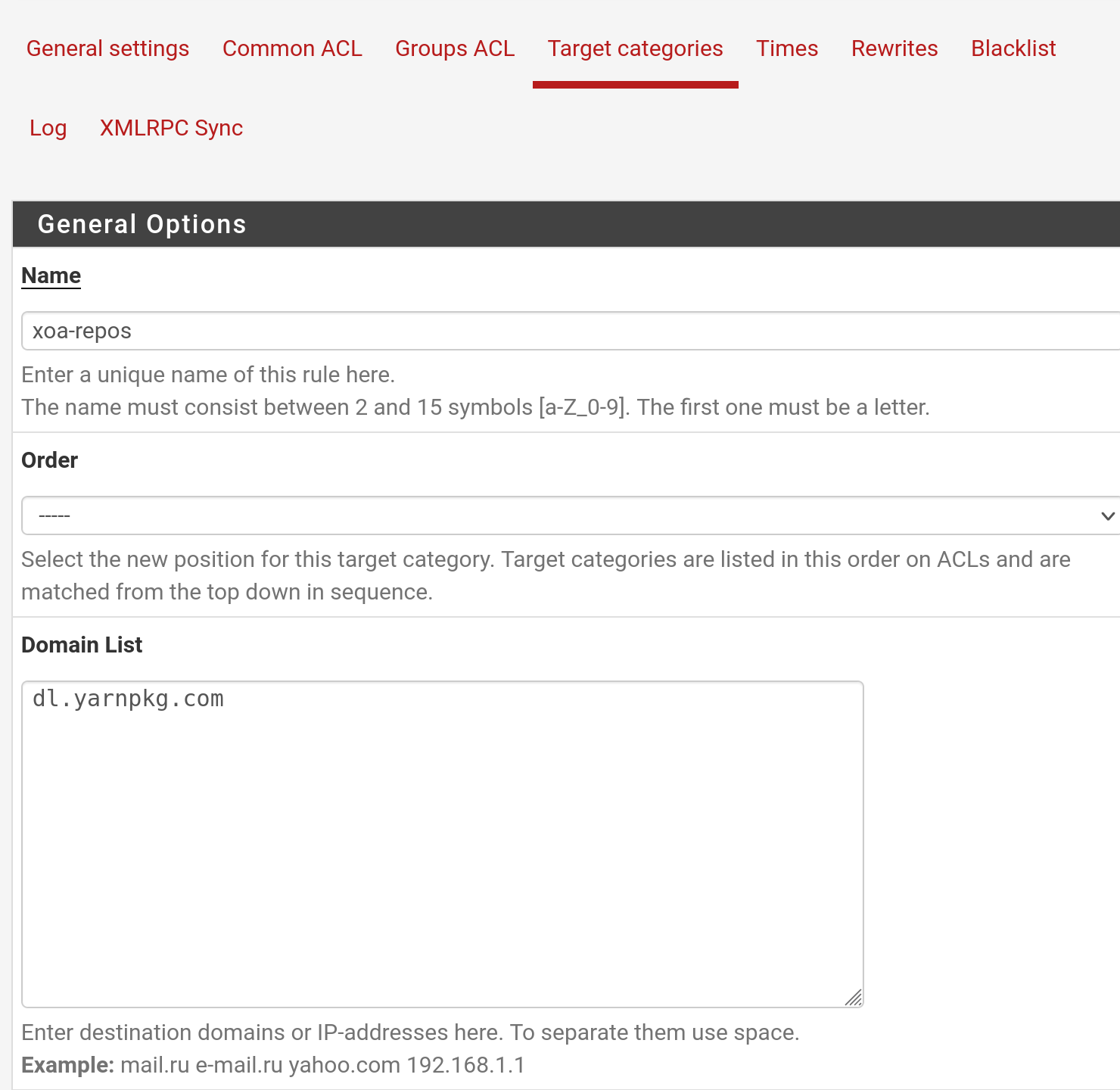
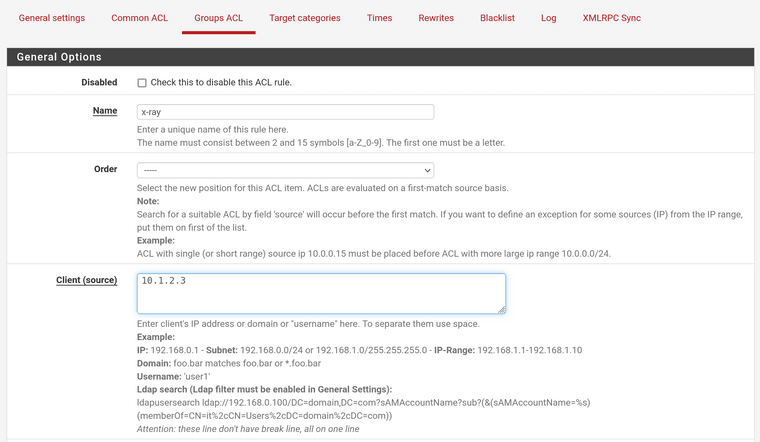
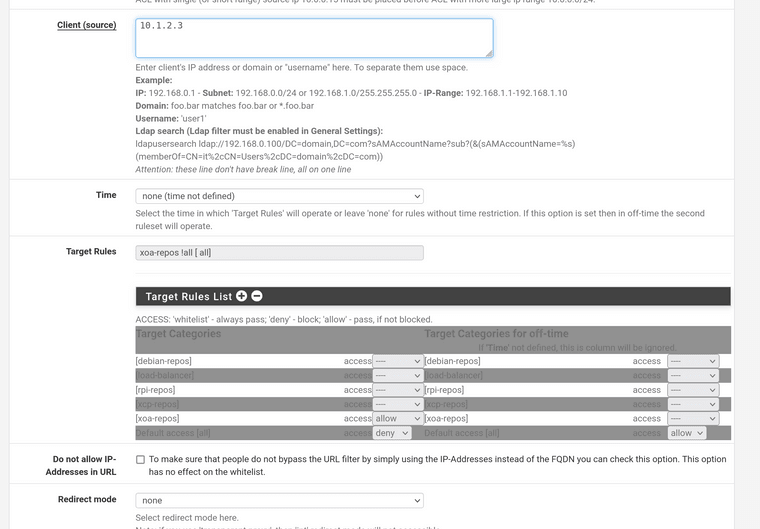
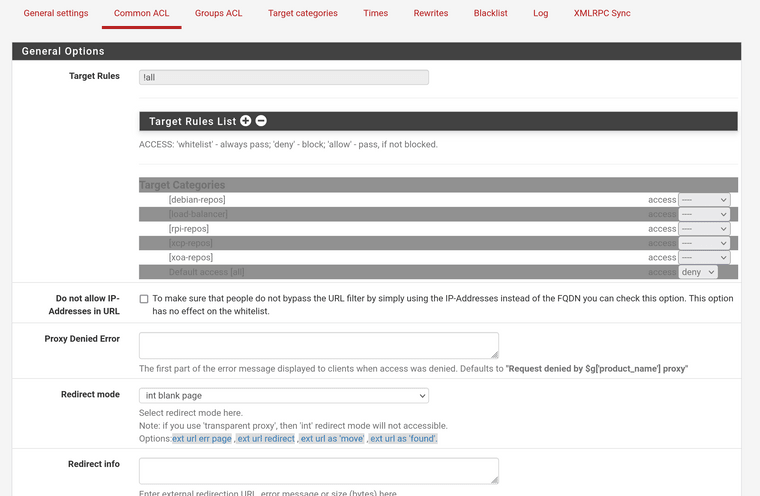
-
Squid works properly by itself without squidguard, relevant config:
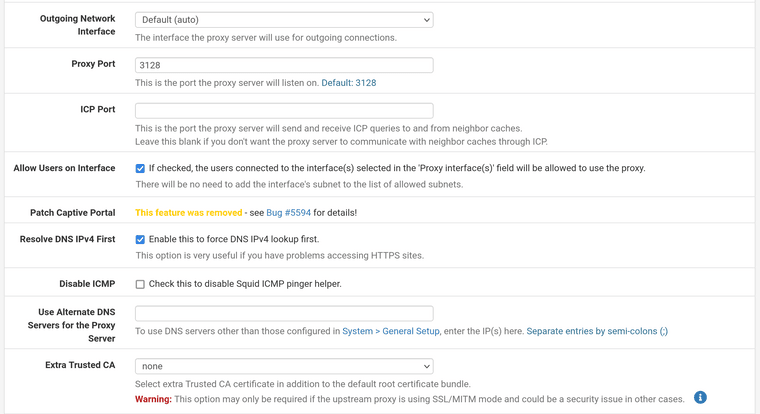
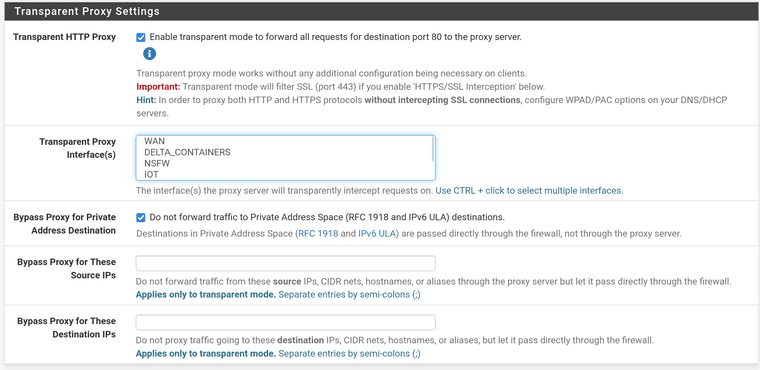
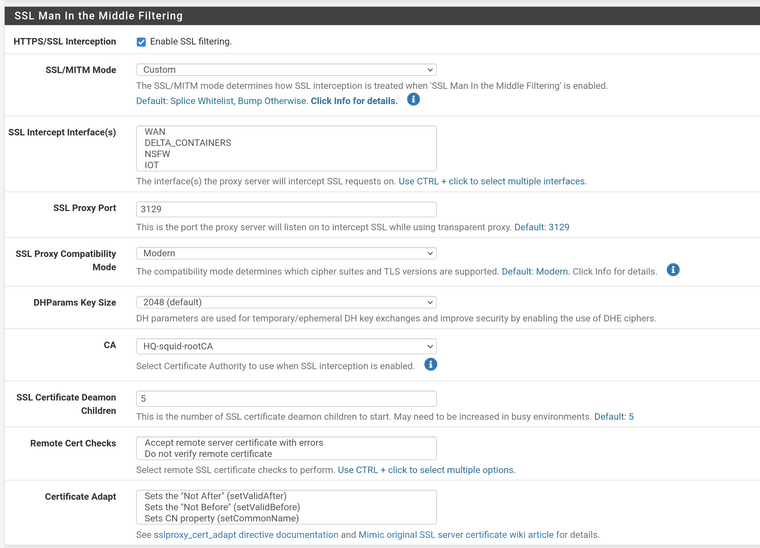
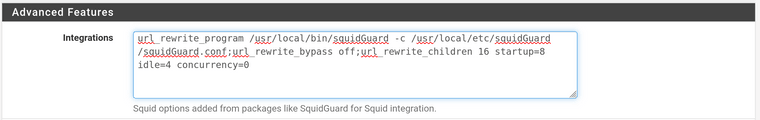
Custom Options (SSL/MITM):# some source IPs that should not be MITM-ed acl splice_only src 10.2.3.4 acl splice_only src 10.3.4.5 acl splice_only src 10.4.5.6 ssl_bump peek step1 ssl_bump splice splice_only ssl_bump bump all -
@foolcoconut You create your groups via Squidguard - Group ACLs. For each group, you edit the Target Rules List to determine where they can go. For you, you would only need a simple whitelist and then block all else.
-
@kom Exactly what I posted in the screenshots above, a single whitelist/allow (neither work) for a target group, and deny everything else.
-
@foolcoconut When you make changes to squidguard , are you going back to the General Settings tab, clicking Save and then Apply? You have to apply your changes or nothing works and I've seen many people get burned by this.
-
@kom Of course, that's why I've been doing this for 3 days 8 hours daily. Because every time both squid and squidguard need about 3 mintues to fully restart.
-
@foolcoconut I have it working here (per-user) but I don't use transparent proxy as I find that to be a real PITA.
-
@kom Did you configure it to be exclusively per user, or do you know if it's possible for it to have:
group1: user1
group2: user1 user2 user3
group3: user3 user4etc.
And as for the transparent proxy, well god damn it if it doesn't work with it, because it's a great feature.
-
@foolcoconut I have ACLs for individual users as well as for an IP range but there is no overlap. I don't know how squidguard would handle that. It seems to do thing top-down so it might hit on the first match and ignore the rest.
If I was you, I would redo it all and start with a simple single-user example with squid in explicit mode. Once you get that working, you can then start adding your layers and note if/where it breaks.
-
@kom Well, you didn't technically solve my problem, but you did help lead me in the correct path. I'll send you a DM to further discuss the delivery of a small appreciation token, for your time spent.
As a solution, I've implemented SG rules per host and disabled the transparent proxy option in squid, apparently that was causing issues. Everything now works as it would make sense, otherwise I would have literally lost my mind troubleshooting and trying the same thing in 15 different ways over and over.
-
@foolcoconut Transparent mode seems more convenient but I've found it to be a major pain in the ass. I use explicit mode along with WPAD to help clients find the proxy, and DHCP option 252.
Don't forget to add a block rule on LAN for tcp80,443 to force clients to use the proxy. I also created an exemption list and allow any IPs on that list to go direct.
-
@kom My use case was to restrict internet access to internal servers, allowing only permitted URL/IP combos, distro repos, etc. So no need for WPAD (+ I have no idea how it works)
And yes good of you to mention it because I forgot, also blocked all internet access in pfsense rules.