VLAN tagging / Interface Config - Help
-
Current Setup:
Switch:
Port 23 is set only to VLAN 90
Port 24 is tagged with 1,20,30,200. I did not have 90 on there since the other port is connected to IGC1 which is set up for 90.4100:
IGC1 connects to Port 23
IGC0 connects to Port 24IGC1 does not have DHCP or anything configured on it other than VLAN 90
IGC1.90 has DHCP and firewall rulesIGC0 does have DHCP for some of my APs, and core devices such as the 4100- those devices are not on a VLAN. There are also 3 other VLANs.
IGC0.10, 20 30, 200 have DHCP rules and firewall rules.I have a couple of questions (reference the screen shot for more information)
- How should port 24 be configured as for as PVID and VLAN member for 1?
- If a device on port 1 tries to reach a device on VLAN 90 (firewall rules allow for this and it does work), does the desktop on Port 1 go to port 24 to
pfsense, pfense tells it it's on vlan 90 and to go to ICG1 then IGC1 says to go to port 6 (assuming 6 is the device)? How does the routing work?
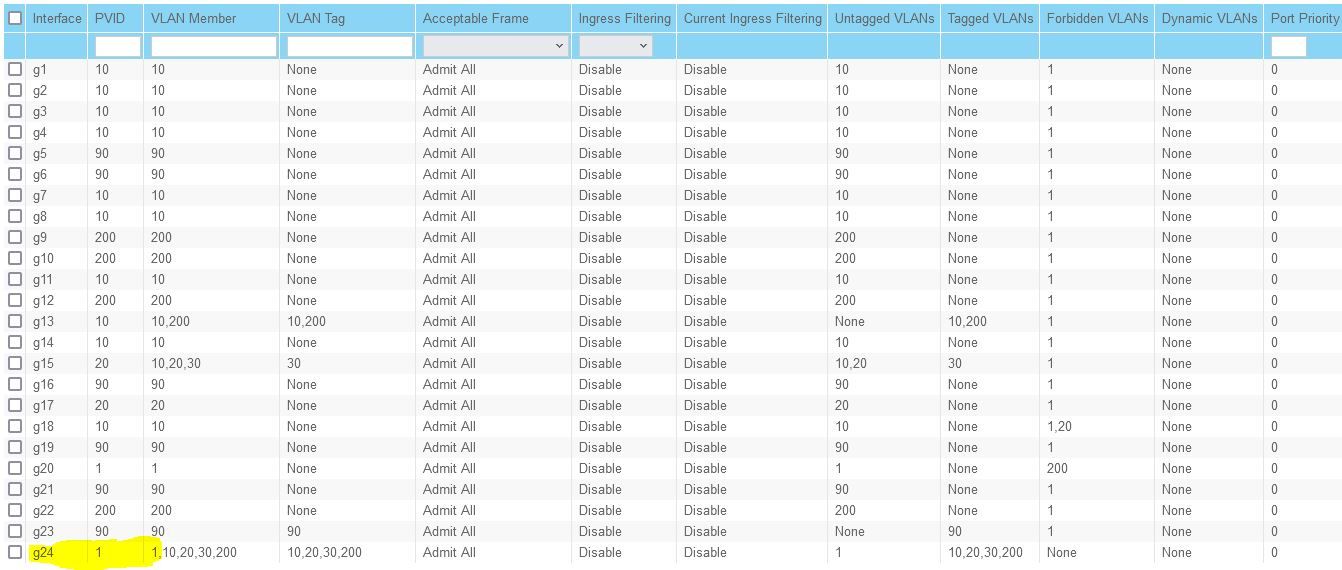
Please keep in mind, VLANs are new to me and am still learning. Thank you! -
@creationguy
First off, you don't need vlan 90 in pfSense if you're using an actual interface. Just untag vlan 90 on port 23 and use the parent interface in pfSense. Nothing wrong with how you have it, just letting you know it didn't need to be done.question 1, it's fine the way it is but why not get rid of vlan 1 all together? Use anything else, example my favorite car is an Oldsmobile 442 so my default vlan is 442. Only reason is vlan 1 is kinda taboo because almost every switch in the world uses is as default so "best practice" is to not use it but you still can, I have someone who refuses to not use it and he has a vpn into my system that sends vlan 1 to my side. Not sure why and don't care why he uses it but it works.
Anyway, question 2, yes, routing would go to pfSense then to the other network.
-
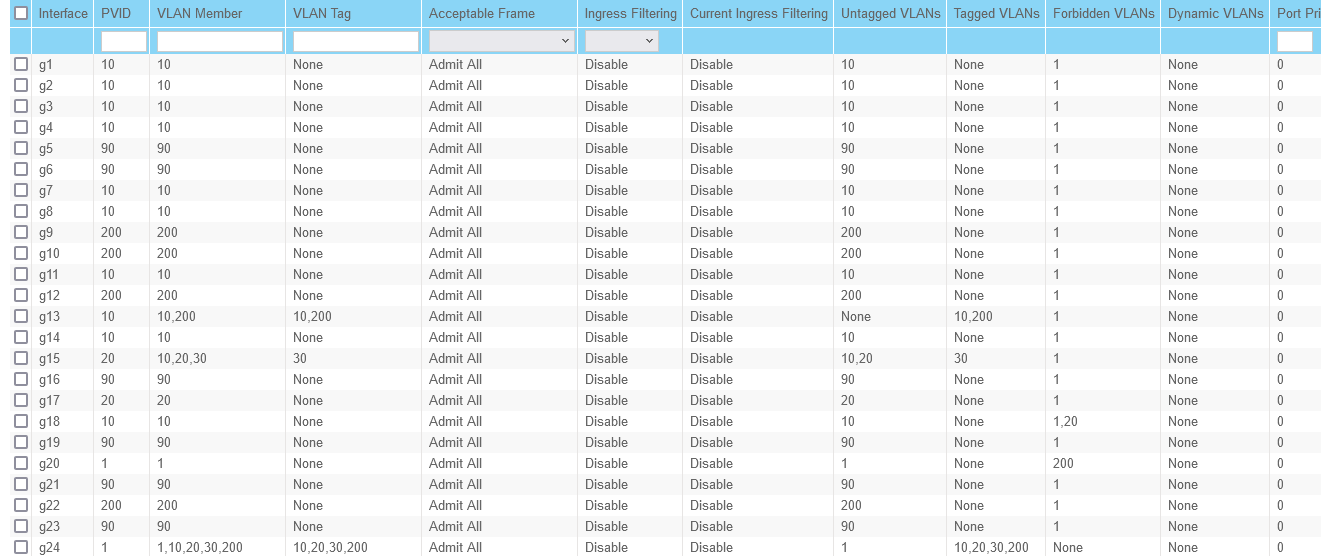
@jarhead When I tried to apply the new changes to port 24, I got the attached error.
I set PVID to 10 and removed 1 from VLAN member.

I'm going to try your suggestion for IGC1, I keep PVID and Member at 90 and should be fine?
-
@creationguy
That error is because you still have vlan 1 set as your management vlan. If you change the management vlan you will be able to remove pvid 1 from all ports. -
@jarhead said in VLAN tagging / Interface Config - Help:
@creationguy
That error is because you still have vlan 1 set as your management vlan. If you change the management vlan you will be able to remove pvid 1 from all ports.I am going to test more, but I think it's because the switch is on the vlan 1 ip range, I haven't fixed a couple of things on the pfsense side yet.
As far as VLAN 90 goes, I untagged it on the switch port, recreated the DHCP settings, firewall rules from IGC1.90 to IGC1 and removed IGC1.90 as well as the VLAN. Everything seems to be working fine. CAMLAN cannot see other LANS, other VLANs other than the ones allowed, cannot access CAMLAN and nor can it access the internet, just like before.
-
@creationguy Somewhere in that switch you can set IP's for management.
Set an IP on the vlan you want to manage it from, then connect to that IP.
You should then be able to change the remaining ports off of vlan 1.
Make sure you change the default vlan to the one you want to manage it from. Might say default vlan, native vlan, management vlan, something like that. -
@jarhead With this switch, it's not possible the change VLAN 1 to VLAN x, it's hard coded. I've tried, I am willing to accept that I'm wrong if I am, but I don't think that I am.
I'm going to attempt a couple of things this weekend so I can remove 1 from g24 one of which is changing the switch's IP. It's getting an IP from pfsense IGC0 that is configured for DHCP to give out the IP range it has. It's not on IGC0.10 or 20, etc.
-
@creationguy Never said to change vlan1, chances are you can't, but stop using it.
Vlan1 will always be in the switch. But it doesn't need to be used.