3.1.0_6 UPDATE
-
Ok so is there a 3.1.0_6 for PfSense+? Don't see the usual message traffic generated on updates.
-
@jmv43-0 _5 came out the other day but only for 2.6 apparently.
Per the last comment in https://redmine.pfsense.org/issues/13154, _6 doesn't include (i.e. reverts if patched) the CPU usage/logging bug fix, although that's listed as an Aug. 31 commit at https://github.com/pfsense/FreeBSD-ports/commits/devel/net/pfSense-pkg-pfBlockerNG-devel.
-
@steveits said in 3.1.0_6 UPDATE:
came out the other day but only for 2.6 apparently.
It is also available for plus, updated yesterday.
-
@mcury said in 3.1.0_6 UPDATE:
It is also available for plus, updated yesterday
OK, I didn't notice that before seeing posts about _6 today.
Edit: interesting, I looked at a 2.6 just now and it is still only offering _5.
-
OK, I didn't notice that before seeing posts about _6 today.
I run pfS+ (22.05) and 3.1.0_6 where able to install today as
I found out, but it could also be earlier available to get,
because I was not the whole week looking over or in the pfSense firewall.And the update is eating my ram and cpu horse power.
Would be nice to see a patch for it, but I don´t really know
how to get the Commit ID for it to install the patch.It is really sad that the patch will not be shown in the Patches field, because many users sitting in that "trap" I think.
-
@dobby_ You can edit the file from the Diagnostics menu: https://redmine.pfsense.org/issues/13156#note-3
Change ) to a space.
-
@steveits
Thank for the hint I used it.EDIT: (17.10.2022)
For me the patch does the trick! All numbers are normal again since that "patch".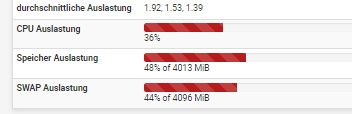
-
@dobby_ Concur, took me a while to chase down thru notes and past posts in Netgate Forums and reddit to get to a fix.
JMV
-
@jmv43-0
I really think the is owed to the different versions of pfSense
2.6 stable and 2.7 devel and on the other side pfblocker-ng
as stable, 3.1.0_4, 3.1.0_5 and actual 3.1.0_6. So the patch is
really unique and must match exactly to the versions you
installed. Or better said it should be clear and save that this
patch is also matching whatever combination you have installed. At my site it was pfs+ (22.05) together with
pfBlocker-NG devel 3.1.0_6 (upgraded to it before ~24 hours)But finding it really out for me was not so easy until the post from @SteveITS he wrote below my post.
-
@dobby_ said in 3.1.0_6 UPDATE:
All numbers are normal again since that "patch".
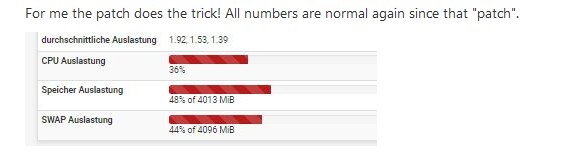
That "load average" and swap usage, are these current numbers ? Or from before ?
-
That "load average" and swap usage, are these
current numbers ?This are the current numbers after applying the patch!
Or from before ?
And this are also the numbers before I updated pfSense (pfs+ 22.05) to pfblockerng (3.1.0_6), after upgrade to pfblockerng 3.1.0_6 I got nearly 50 % Swap usage and something around +/-91 % RAM usage, and CPU was
spiking up to something around 60% - 80%. -
@dobby_ said in 3.1.0_6 UPDATE:
This are the current numbers after applying the patch!
When the swap space start to get used, see that as a signal that your device, starting with memory, can't cope any more.
Two solutions :
Lower significantly the work load.
Double your memory and CPU. -
When the swap space start to get used, see that as a
signal that your device, starting with memory, can't
cope any more.Ok that is right, but in normal the half of the ram and
swap is free and this over a long time only if ClamAV,
snort and pfblocker-ng are updating the lists and rules
it goes here and there nearly 70 % of both, but after the update it goes back to the above shown levels.Two solutions :
Lower significantly the work load.Could be the way for me, I run Snort, Squid & SquidGuard,
and pfBlocker-NG plus ClamAV on a PC Engines APU4D4.
In the future it comes on top of all, WiFi with Captive Portal and FreeRadius.Double your memory and CPU.
In the near future this is planed for the whole setup.
Only some MacBooks, 1 PC and 1 Laptop at home usage.
So I really don´t know what to take I am between some
different solutions and not at the moment ready to chose.But thanks anyway for the tip, you were right with the ram
and cpu load. The older APU will then be a GPS based NTP
and OpenLDAP server with some other services for the LAN. -
@dobby_ said in 3.1.0_6 UPDATE:
Snort, Squid & SquidGuard, plus ClamAV
Just for my own curiosity : knowing that 99,x % of all traffic is TLS these days, so the traffic payload is completely random for pfSense, what should ClamAV do ? Scanning virus in the packet headers ?
-
@gertjan said in 3.1.0_6 UPDATE:
what should ClamAV do ? Scanning virus in the packet headers ?
I use Squid as a caching-proxy and let ClamAV do the av scanning on it.
-
Ok, that's the way to do it ;)
-
@mcury said in 3.1.0_6 UPDATE:
@steveits said in 3.1.0_6 UPDATE:
came out the other day but only for 2.6 apparently.
It is also available for plus, updated yesterday.
I wonder whats going on here… Rumors have it that it is Netgate that maintains this package now and @BBcan177 is no longer on board.
Regardless if that is true or not, it makes less than NO sense to release not one but two minor fixes of the package where the most glaring obvious bug i still present.
Has the package been hijacked, and is now delivering malware instead?We need some proper information about these release from whoever is responsible for the included changes and who approved it.
-
Hi,
as far as I can see, has the content of pfblockerng.inc between line 4136 and 4142 completely been reworked (that was the part that made the problems
https://redmine.pfsense.org/issues/13154 )But I agree - a clarification from Netgate or whoever would be very much appreciated!
Regards,
fireodo -
Has the package been hijacked, and is now delivering
malware instead?Why? Because Netgate is now the maintainer? Then you could not trust the whole system (pfSense) and this makes
no sense for me. If I trust someone (Netgate) and use his entire system I will also trust them if they (Netgate) maintain a package!We need some proper information about these release
from whoever is responsible for the included changes
and who approved it.Thinking one step ahead please, it is better in my eyes getting the hands on a package that is available and present, then one is not maintained any more!
I will be more lucky with a patch, given in a short time
that is working, I mean it is better then watching out the whole ticket parade and not patch is available. -
@fireodo said in 3.1.0_6 UPDATE:
Hi,
as far as I can see, has the content of pfblockerng.inc between line 4136 and 4142 completely been reworked (that was the part that made the problems
https://redmine.pfsense.org/issues/13154 )But I agree - a clarification from Netgate or whoever would be very much appreciated!
Regards,
fireodoIf that is completely reworked, why does it still suffer the same issue then? I haven't updated yet because of this, and as far as I can tell people are still applying the same "fix" by removing the ")" in line 4136. So something is still the same in that section.