Alias to block cameras from WAN only working for some cams
-
@jims If your saying the Ips are in the alias, then they would be blocked. Do a search in the state table for an IP of a camera your saying has access. Make sure there are no states for this IP.
Or you have a rule allowing this traffic before your rule with the alias that blocks. Do you have any rules in the floating tab? Please post the rules on the interface the cameras are connected to.
Not at all familiar with states.
Well that is how a stateful firewall works ;) so you might want to do a bit of reading about them - just saying ;)
https://docs.netgate.com/pfsense/en/latest/monitoring/status/firewall-states.html#firewall-states
-
@johnpoz I went to Diagnostics>states and entered the IP for the filter expression. Then deleted the 2 states. Still had access and even more states appeared - 14 of them. Those might be from the connection check the camera does to several sites. My older cameras of the same make show no states and no access. Has the camera firmware gotten smarter on how
 to bypass things?
to bypass things? -
@jims A device can’t bypass a firewall on its own. Try restarting the pfSense. That also clears states. :)
Are the new cameras issuing IPv6? You only blocked 4…
-
@steveits Not sure. I assigned them a IPv4 address. How would I check that? And how would I block?
-
@jims You're not blocking the internet, you're blocking the WAN net. Change that to any.
-
@jarhead AKA make an alias of RFC1918 addresses (https://docs.netgate.com/pfsense/en/latest/firewall/aliases.html) and set the destination to that alias but choose the "inverse" option.
-
@rcoleman-netgate
Wouldn't even need that since it's all on one subnet but yes, that is the usual way of doing it. -
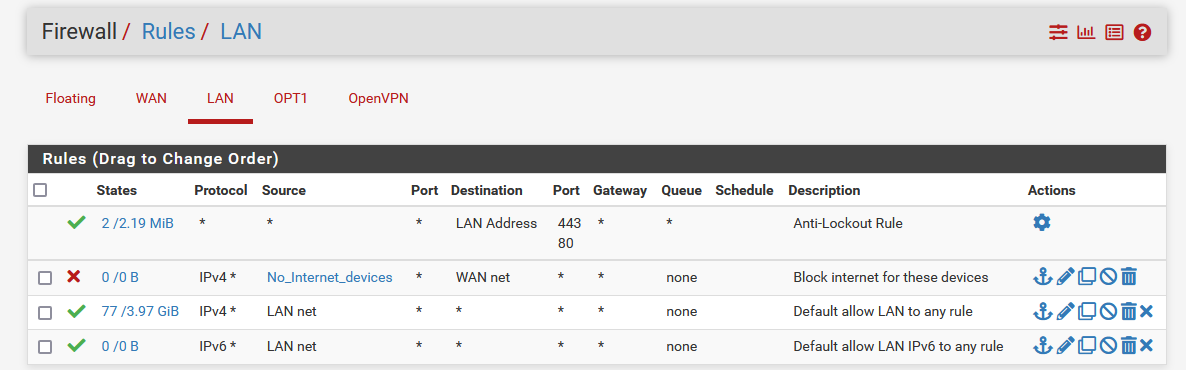
@jims as mentioned that is just wan net, not the internet so not sure how you think its blocking any of your camera's and the rule doesn't even show any evaluations. see that 0/0 B means no traffic that his hit pfsense has even matched that rule.
So either they all have states already, or they are not trying to go to whatever network is on your wan net, and going to just the internet..
Wan net is just that the network on your wan, so for example if your wan address was 1.2.3.x with a /24 mask then that rule would block going to 1.2.3.0-255, it would block say 8.8.8.8 or any other address that is not 1.2.3.X
If your wanting to block them from going to the internet that rule is not correct, any as destination would be the internet. If you want them to talk to anything say on your Opt1 network, or pfsense you would need a rule above your block any rule to allow the traffic you want.
And not a fan of using any ! rules, its easier to understand and read your rules when your explicit on where they can or can not go, ! or inverse rules make it harder at a glance to see exactly where they can or can not go.
-
@jarhead Fair point. Having an RFC1918 rule, though, is a good idea either way, especially if you're like me and have cameras on many subnets depending on the trustworthiness of the company that made them.
All in one subnet solution:
Destination: Inverse selection of "INTERFACE_NAME NET" -
@jarhead I don't understand the difference between WAN and internet. My pfsense box has two network ports - the one connected to my internet modem (WAN) and the other connected to my LAN. It seems that setting that destination to any would keep the cameras from connecting to anything but perhaps that is ok as all connections to the cameras should be initiated by the DVR (or my PC if I am accessing them directly for some reason)?
-
@jims said in Alias to block cameras from WAN only working for some cams:
difference between WAN and internet.
I thought I was pretty clear on this already?
WAN net is just the network you are connected to get to the internet.. This is just any network like 192.168.0.0/24 etc.. but from ISP it is public network say 1.2.3.0/21 or something - the internet is every possible public IP on the planet.. If you block something from going to say your wan net 1.2.3.0/21 - it doesn't stop it from going to say 8.8.8.8 or 9.9.9.9 or 42.51.62.102 etc.
If you want to stop something from going to the internet the destination would be ANY, if you want to just stop it from going to your wan net, ie my 1.2.3.0/21 example then you would use Wan Net as your destination..
-
@jims said in Alias to block cameras from WAN only working for some cams:
@jarhead I don't understand the difference between WAN and internet. My pfsense box has two network ports - the one connected to my internet modem (WAN) and the other connected to my LAN. It seems that setting that destination to any would keep the cameras from connecting to anything but perhaps that is ok as all connections to the cameras should be initiated by the DVR (or my PC if I am accessing them directly for some reason)?
Does what John said make sense to you? He is explaining it exactly but you may not understand it.
Just keep in mind, any of the "net" aliases, wan net, lan net etc, are just the directly connected network. So the WAN net is the subnet your ISP assigned to your service.
Let's say you're public ip is 10.10.10.3 with a subnet of 24, and your gateway is 10.10.10.1.
By blocking the WAN net, that's the only network you blocked. Chances are you'll never need to access anything on that network so you're not really blocking the cameras from anything.
Now, your traffic from your LAN goes to your gateway (10.10.10.3 in this example), then goes to your ISP's gateway (10.0.0.1) and then out to the internet, BUT none of your traffic is destined for anything on that network so it goes right out to the internet still.As for the ANY rule, you only have one subnet, so local traffic never even goes to your pfSense, it's layer 2 traffic only. So using ANY there will block it from entering the firewall and be blocked as you want it to, but you can still access it locally.