Firewall rules not working for VLANs?
-
I thought that my rules were set up correctly and working but now I am not sure.
Setup:
- I have a Proxmox VLAN, one of the VMs is a linux distro with NMAP installed.
- I have a CAMLAN VLAN, I've set it so that Proxmox cannot talk to CAMLAN, I can't ping it nor reach anything on the network.
I decided to run an nmap and was surprised by the results...
nmap -sP -Pn 10.90.90.1/28It found every single device on that network....
How can I stop that from happening? The entries that came back, they are all statically assigned a DHCP address and I have this checked:
ARP Table Static Entry [] Create an ARP Table Static Entry for this MAC & IP Address pair.As a test, I unchecked the arp setting for one camera and made sure that it was removed from the ARP table, re-ran the nmap and it's still there.
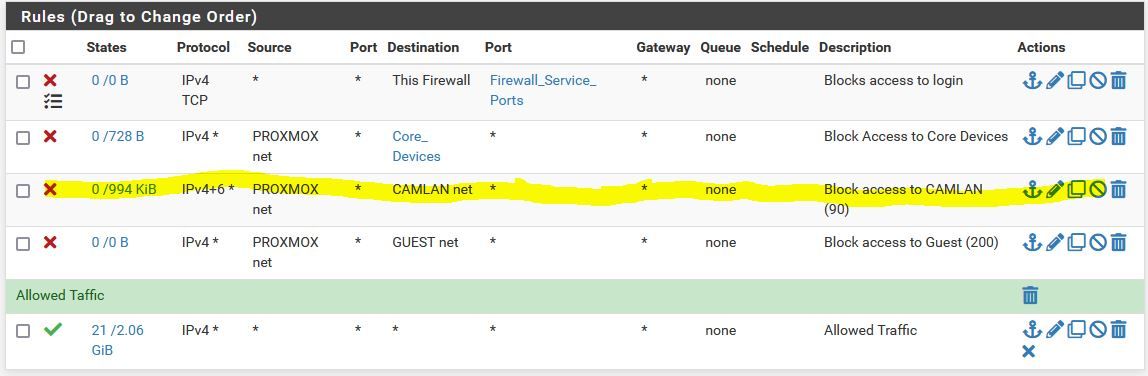
This is the fw rules for Proxmox VLAN
-
I'm really racking my brain on this one, granted I am no expert. All rules are set to block not reject.
I realize that -Pn assumes that the host is up, but the returns for the devices are are really up is what concerned me. It came back with actual host names/FQDN.
-
@creationguy Resolving the hostname doesn't mean there is connectivity.
If these are new block rules and there is an open state it will still pass while the state is open.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/firewall.html#new-rules-are-not-appliedAny errors when loading rules?
https://docs.netgate.com/pfsense/en/latest/troubleshooting/firewall.html#ruleset-failing-to-load
...though the 994 KB means packets are hitting that rule. -
@steveits
They are old rules, but I did reset the states, same results.
The rules work as far as not being able to reach HTTP on those cameras, can't ping, SMB, etc.CAMLAN is on IGC0 on my 4100; I don't have a VLAN set to that interface as you can but the ports are all set to VLAN 90 (CAMLAN).
 IGC1 is on port 23.
IGC1 is on port 23.Edit: It shouldn't even know about the host names, that seems like a security concern to me.
-
@creationguy Are the hostnames being registered in pfSense? (for example the "register DHCP leases in DNS" option, which has the side effect of restarting unbound at every renewal)
If not, what is providing DNS? I'd expect that is what is resolving the IPs to hostnames.
-
@creationguy said in Firewall rules not working for VLANs?:
It came back with actual host names/FQDN.
because it asked dns for their names.. Here I just scanned an IP from my dmz.
Just scanning the 1 IP for my test.. There is no device on this IP 192.168.9.33 from a pi in my dmz 192.168.3.10
I just created a dummy dns record for it via host override
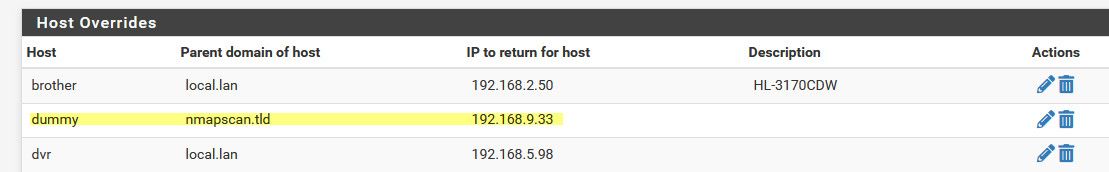
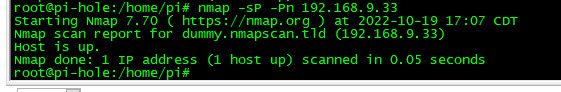
Here I scanned via your cmd an another non active IP.. Says its up.. but how could that be, there is no such IP on my network.. Notice it didn't come back with a fqdn.
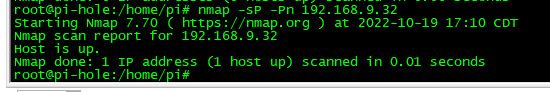
BTW what do think that -sP would do anyway..
-
@steveits
pfsense is handling everything, I had pfblockerNG and Wireguard for packages. I have Quad9 DNS over TLS set up for external.I do have:
Static DHCP
Register DHCP static mappings in the DNS ResolverSelected. I am not sure if I did that or if it's default.
@johnpoz
Why would DNS respond? Wouldn't my firewall rules stop that? -
@creationguy where would it be blocked, you have a any any rule there at the end.
Here I just did a sniff while I scanned another IP that doesn't exist.. 192.168.9.31
See the dns query and answer
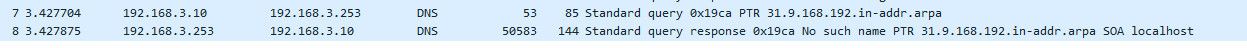
I don't see a rule blocking access to dns 53 on pfsense IP on that interface..
-
@johnpoz
Hmm, I wouldn't want to block 53 then devices couldn't query externally or services internally when needed.I can't block it from querying DNS for a specified vlan right?
The reason as to why I have the VLAN set up is to segment the cameras from being accessed, which is working, I just thought that it would also not being to tell what IS there, even by DNS.
I ran port scan on NVR, and maybe I am misunderstanding the results since -Pn assumes that the device is up.
nmap -p 8086 -Pn 10.90.90.2 Starting Nmap 7.80 ( https://nmap.org ) at 2022-10-19 22:37 UTC Nmap scan report for NVR.my.lan (10.90.90.2) Host is up. PORT STATE SERVICE 8086/tcp filtered d-s-n Nmap done: 1 IP address (1 host up) scanned in 2.04 secondsThis port is not in use:
nmap -p 8089 -Pn 10.90.90.2 Starting Nmap 7.80 ( https://nmap.org ) at 2022-10-19 22:39 UTC Nmap scan report for NVR.my.lan (10.90.90.2) Host is up. PORT STATE SERVICE 8089/tcp filtered unknown Nmap done: 1 IP address (1 host up) scanned in 2.04 seconds -
@creationguy your not understanding what its telling you.. It shows its filtered, ie it couldn't get there. But yeah it knows that 8086 is d-s-n, per is file of services
https://nmap.org/book/nmap-services.html
https://svn.nmap.org/nmap/nmap-services
Why don't you log your block rule - then do your port scan.. Do you see it hit your rule and get dropped..
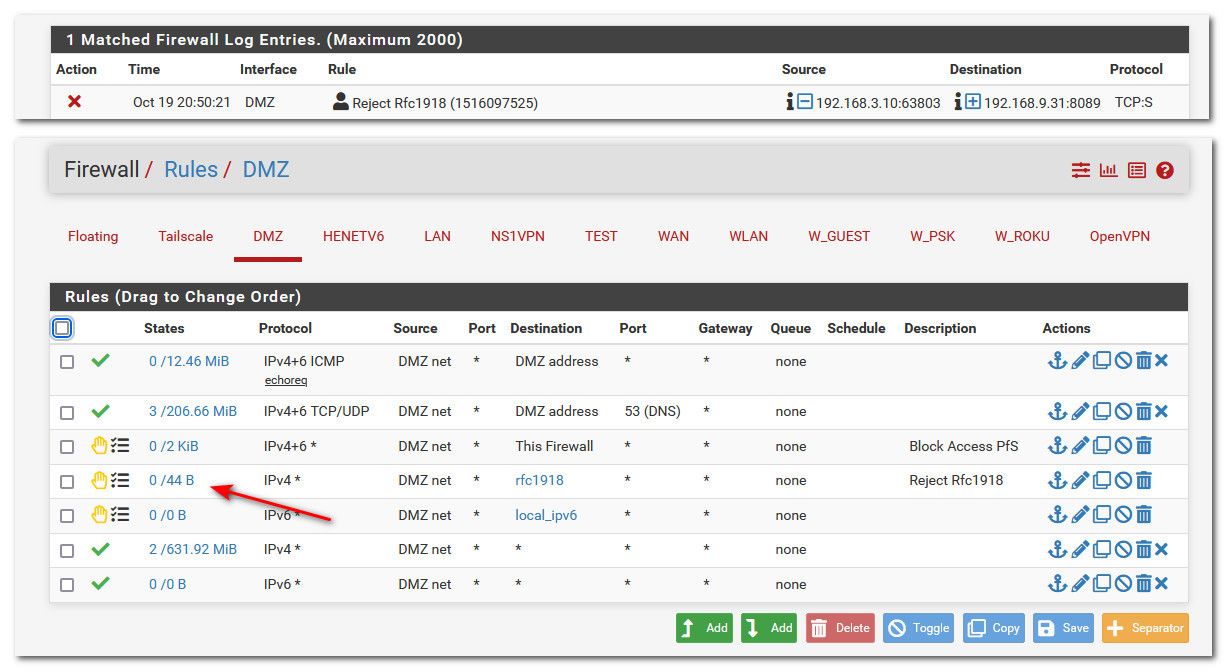
Here is see my dmz rules.
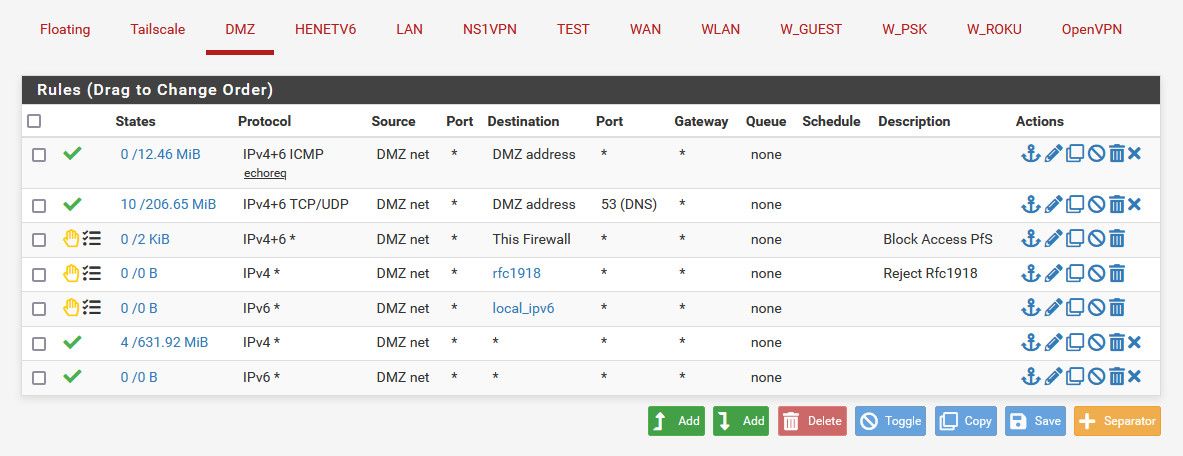
I then do a scan - mine comes back closed, because I set to reject
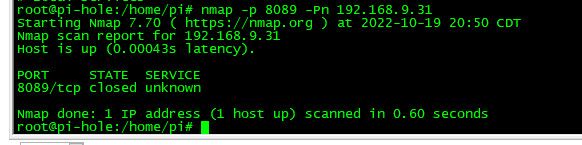
Now notice my firewall hit that is blocked that connection, and notice on my rules now it shows traffic to that rule, that was evaluated and blocked it.
for your dns question.. You could setup views to only allow it to resolve specific local stuff, but that would be a bit of leg work on your part. Putting in just what you want it to see locally.
edit: here is thread were I went over doing that
https://forum.netgate.com/post/1024683If you don't want it to resolve anything local, its much easier - just block it from pfsense on port 53 and set it to use some external dns.
Another option for stuff that you want it to resolve locally, might be just set host file on the box, or point it to another dns on your network that that only has the local resources you want it to resolve.
-
@johnpoz
Logging does show that it's being blocked. I was not understanding the State and Service, thank you for the links. Service was just telling me what that port is registered for/to do.With the FW rule of block, state shows filtered, with it set to reject, it shows closed. I suppose if something did a similar scan on the network and found my camera host names, it's not a BIG deal as it can't reach them. I also tried telnetting into that ip and port and got rejected.
-
@creationguy I normally use reject for local stuff like this.. If your not going to allow it, might as well tell the client - hey your not getting there, vs having it try with retrans and just bang its head against a wall.
I wouldn't suggest you ever use reject externally, unless for a specific purpose - I reject on traceroute ports so that traceroute works.