Exempt IPSEC Traffic Suricata
-
@overcon said in Exempt IPSEC Traffic Suricata:
That is a great idea, I will do a trace and check those IPs, I didn't even think of that. Let me do that and I will get back.
Not every IP address in a trace matters. Only the gateway you talk to, or that your IPSEC VPN is connected to. Intervening IPs along the hop route do not matter as Suricata will never see them.
-
@bmeeks said in Exempt IPSEC Traffic Suricata:
@overcon said in Exempt IPSEC Traffic Suricata:
That is a great idea, I will do a trace and check those IPs, I didn't even think of that. Let me do that and I will get back.
Not every IP address in a trace matters. Only the gateway you talk to, or that your IPSEC VPN is connected to. Intervening IPs along the hop route do not matter as Suricata will never see them.
I didn't find any of the IP's in the block or alert pages (that isn't already excluded). I checked for my gateway and the last pingable device in the traceroute, which I don't know where it is 208.115.251.46. Anyway, I have searched for my public IPs, my gateway IP, my IPSEC tunnel IPs, the cameras IP, the server that polls the cameras IP, and the last replying IP when I did a TR to the IP of the remote server.
-
@overcon said in Exempt IPSEC Traffic Suricata:
I didn't find any of the IP's in the block or alert pages (that isn't already excluded).
That last part in parentheses is confusing me. What do you mean by "that isn't already excluded"?
The task here is pretty simple. Assume the camera is IP 1.2.3.4 and the remote server querying the camera has the IP 4.3.2.1.
- If you don't see 1.2.3.4 or 4.3.2.1 in the list of alerts on the ALERTS tab, and
- you don't see either of those two IP addresses in the list on the BLOCKS tab, and
- finally, you don't see either of those IP addresses in the list of addresses in the snort2c table when looking under DIAGNOSTICS > TABLES in the pfSense menu; then Suricata is not blocking the device. Something else is going on.
Perhaps, if you have this traffic encapsulated in an IPSEC tunnel, one of the two tunnel endpoint IPs is getting blocked ?? Have you checked for those?
It might be easier for you to just disable Suricata in this situation.
-
@bmeeks said in Exempt IPSEC Traffic Suricata:
@overcon said in Exempt IPSEC Traffic Suricata:
I didn't find any of the IP's in the block or alert pages (that isn't already excluded).
That last part in parentheses is confusing me. What do you mean by "that isn't already excluded"?
The task here is pretty simple. Assume the camera is IP 1.2.3.4 and the remote server querying the camera has the IP 4.3.2.1.
- If you don't see 1.2.3.4 or 4.3.2.1 in the list of alerts on the ALERTS tab, and
- you don't see either of those two IP addresses in the list on the BLOCKS tab, and
- finally, you don't see either of those IP addresses in the list of addresses in the snort2c table when looking under DIAGNOSTICS > TABLES in the pfSense menu; then Suricata is not blocking the device. Something else is going on.
Perhaps, if you have this traffic encapsulated in an IPSEC tunnel, one of the two tunnel endpoint IPs is getting blocked ?? Have you checked for those?
It might be easier for you to just disable Suricata in this situation.
I mean I have already excluded rules that were triggering on those IPs, in alerts.
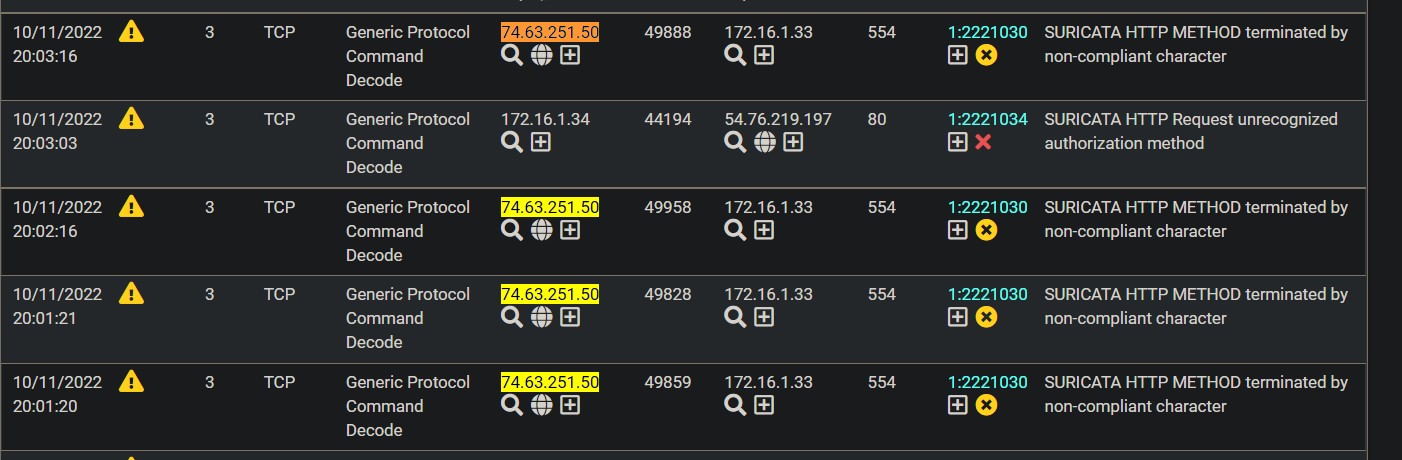
Like these. I have already excluded these rules; which are triggering on the remote IP and the local IP. I do not see either IP for the ends of the IPSEC tunnel listed, and I have them in the PASS list. I also have my public IPs in the passlist, and while I do see them in the alerts list, I don't see them in relation to the IPCAM or the remote servers IP.
I am going to check the snort2c right now. Sorry, I was going to check it last night, but I did an update on my mail server (to 22.04), and it killed it, so I was trying to see if I could fix that.
There are seven alerts that reference the IPs, all those rules are excluded (disabled).
-
@bmeeks I checked the snort2c, and I don't see any of the IPs I am dealing with listed.
Should I suppress all the alerts to see if maybe they are triggering even though I have them disabled? I haven't done that yet. The thing I don't get is when the camera gets blocked, I have searched the blocks and cannot find any IP related to the camera.
-
@overcon said in Exempt IPSEC Traffic Suricata:
@bmeeks I checked the snort2c, and I don't see any of the IPs I am dealing with listed.
Should I suppress all the alerts to see if maybe they are triggering even though I have them disabled? I haven't done that yet. The thing I don't get is when the camera gets blocked, I have searched the blocks and cannot find any IP related to the camera.
If you do not see any IP related to the camera in the blocks listed on the BLOCKS tab nor in the IP's shown in snort2c table when viewing it under DIAGNOSTICS > TABLES, then Suricata is not your problem and looking through rules is wasted time. Suricata cannot block without placing the IP in the snort2c table. That table is literally how the custom plugin that does Legacy Mode blocking works. It puts the IP in that table, and then the pfSense firewall engine performs the actual block of traffic. So no related IP in that table means Suricata is not the root cause of your issue.
I know how all that works because I wrote the code for the custom plugin that does the Legacy Mode blocking.
-
@bmeeks said in Exempt IPSEC Traffic Suricata:
So no related IP in that table means Suricata is not the root cause of your issue.
I believe you, I just can't see how it can't be a Suricata issue if clearing all the blocks allows the camera to resume working.
-
@overcon said in Exempt IPSEC Traffic Suricata:
@bmeeks said in Exempt IPSEC Traffic Suricata:
So no related IP in that table means Suricata is not the root cause of your issue.
I believe you, I just can't see how it can't be a Suricata issue if clearing all the blocks allows the camera to resume working.
Have you gone to DIAGNOSTICS > TABLES in the pfSense menu, selected the snort2c table in the drop-down, and then examined all the IP addresses displayed?
Those IP addresses are the only thing Suricata is blocking. If clearing blocks (if by that you mean going to the BLOCKS tab in Suricata and clicking the Clear button) restores the camera to operating status, then you are not looking for the correct IP when trying to find why the camera is blocked. There is no other answer possible. Only IP addresses in the snort2c table are blocked (by Suricata), so if you do not see the correct IP in the table, then Suricata is not blocking it. Conversely, if clearing blocks (which empties the snort2c table of IP addresses) restores the camera's operation, then the only logical conclusion is you are searching for the wrong IP when looking in the table and on the BLOCKS tab.
-
@bmeeks said in Exempt IPSEC Traffic Suricata:
@overcon said in Exempt IPSEC Traffic Suricata:
@bmeeks said in Exempt IPSEC Traffic Suricata:
So no related IP in that table means Suricata is not the root cause of your issue.
I believe you, I just can't see how it can't be a Suricata issue if clearing all the blocks allows the camera to resume working.
Have you gone to DIAGNOSTICS > TABLES in the pfSense menu, selected the snort2c table in the drop-down, and then examined all the IP addresses displayed?
Those IP addresses are the only thing Suricata is blocking. If clearing blocks (if by that you mean going to the BLOCKS tab in Suricata and clicking the Clear button) restores the camera to operating status, then you are not looking for the correct IP when trying to find why the camera is blocked. There is no other answer possible. Only IP addresses in the snort2c table are blocked (by Suricata), so if you do not see the correct IP in the table, then Suricata is not blocking it. Conversely, if clearing blocks (which empties the snort2c table of IP addresses) restores the camera's operation, then the only logical conclusion is you are searching for the wrong IP when looking in the table and on the BLOCKS tab.
I only searched for the IPs I know that are involved. I can't confirm with 100% that they are not sending traffic from another IP, as I don't know how their systems are configured. I just know the IP they gave me and that they told me traffic would only come from it (so I could lock it down in my firewall rules).
They also sent me a list of all their IPs, which I plugged into an ALIAS. I will change the rule to use that and see if that changes anything. The reason I haven't done that is that I assumed the firewall would drop any traffic that wasn't from the specified IP in the rule and Suricata wouldn't be involved since the firewall would drop any traffic before Suricata would see it, but I'll give it a go and see.
The next time it gets blocked, I will search the snort2c table and see if any of those IPs are in there.
-
@bmeeks I think I found it! So I waited until it blocked it again. Then I searched the snort2c list and found the remote IP of the server. So I confirmed it was getting blocked. Then I searched the alerts, but I increased the list count to 5000 instead of 500 and turned off auto-refresh. Then I found this new alert:
#SURICATA HTTP URI terminated by non-compliant character
suppress gen_id 1, sig_id 2221029So I suppressed that one, removed the IP in the snort2c table, and the camera came back up!
So now, I just have to see if it holds! I will set the firewall back up to allow that IP and see if it makes a difference since I don't think changing it to the alias with all their IPs made a difference.
Thanks for the patient help on this!
Here is the site with the camera: