pfblocker working on ip but not DNS, not sure how to fix
-
I am new to pfsense, and have done a new setup with pfblocker. It seems to be working for IP blocking but I cant get the DNS blocking to function properly. I think the issue is DNS resolver related
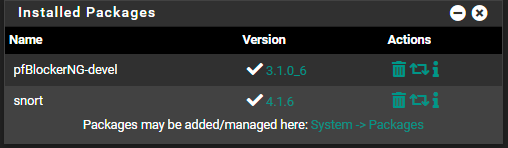
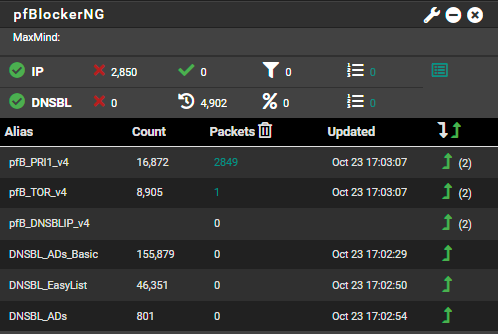
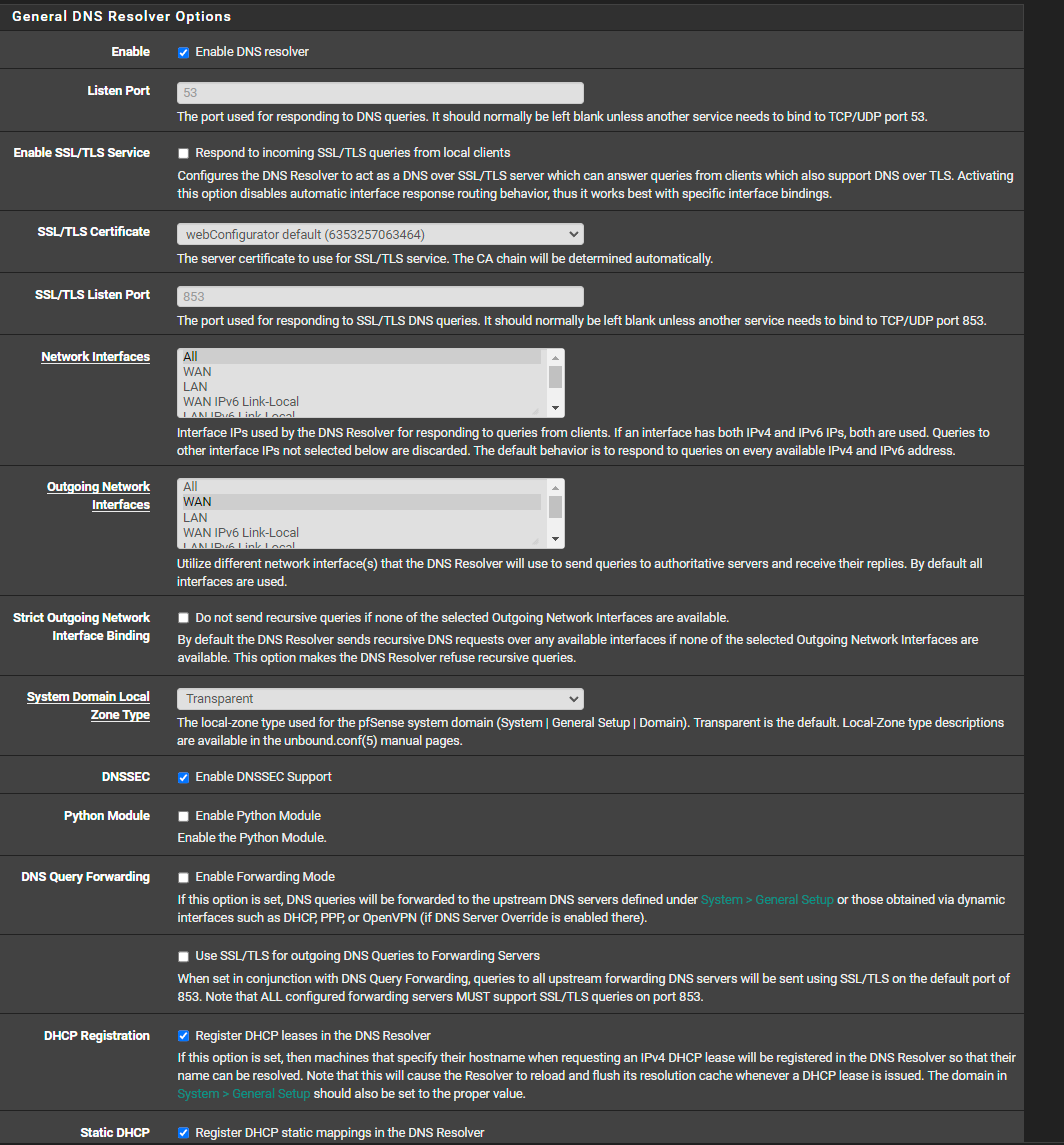
Not sure why devices keep referring to cloudflare dns
-
@canaryforge said in pfblocker working on ip but not DNS, not sure how to fix:
Not sure why devices keep referring to cloudflare dns
What devices ?
What is the DNS these devices use ?Example : if you set a device a device so that it uses 8.8.8.8 as a DNS, then pfSense (and pfBlocker) will never receive DNS requests from this device.
-
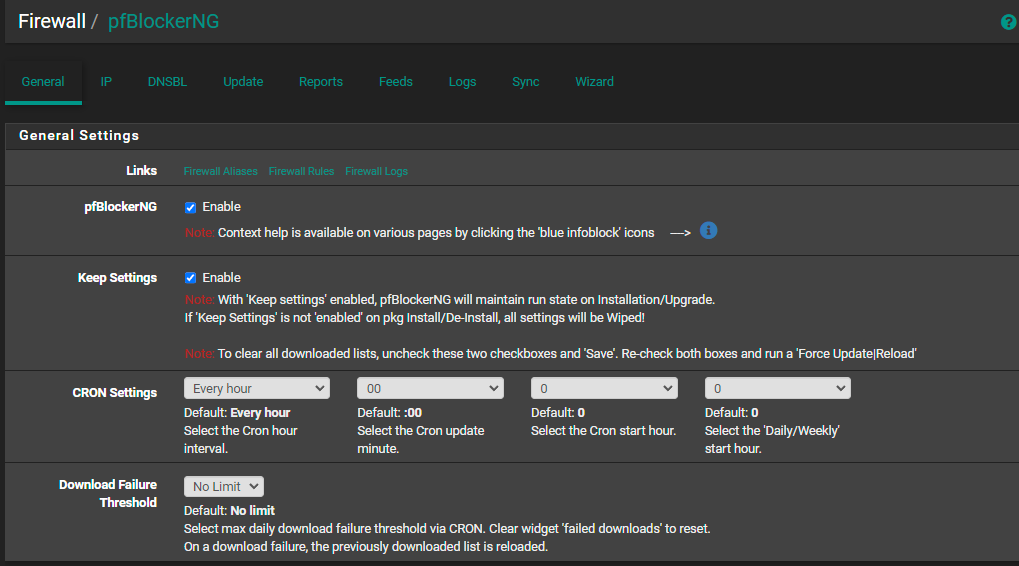
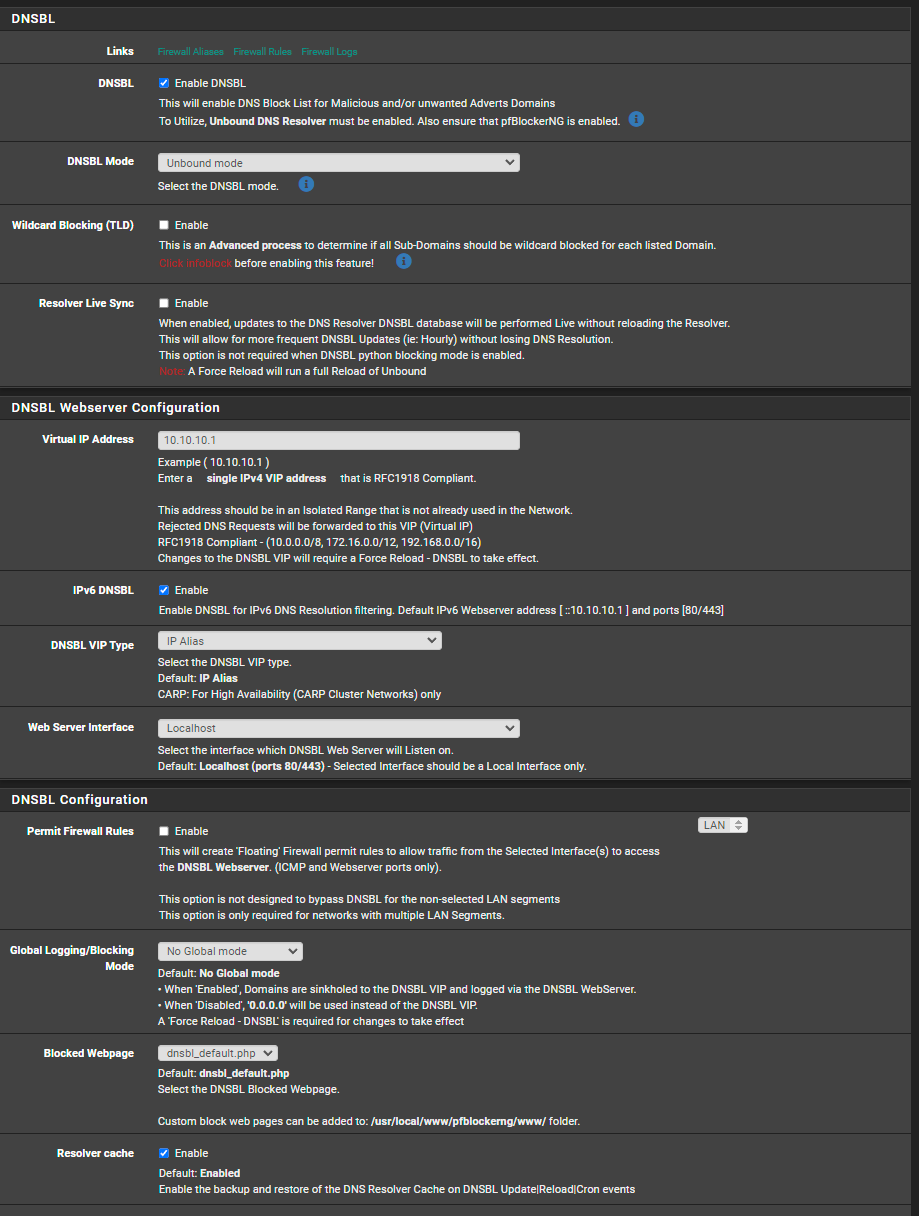
Hi canarygorge I am a basic user, but I will try to help. Expanding on Gertjan post. You need to have your network devices use local PFsense DNS in order for PF blocker DNSBL to be useful. Sometimes you have to force your devices and apps to do this. They will happily default to the DNS provider that has paid the company of that particular app or OS to be their default DNS. So as a start I would add blocking external client DNS queries to your firewall rules. Once these rules are in. Reset your state table. You can find the rules on the PF sense dashboard. Go to help, then click on PF sense book. From the book scroll down to the bottom until you see recipes. From there, click on DNS, and then blocking external DNS queries to get your rule set. You will also want to start learning about doh and dot. Hopefully this will give you the blocking that you are looking for. Also, even though you didn’t ask for it I’m going to suggest some settings that I think will help you at this stage. Looking at your pics that you posted.
For the time being turn off snort, as I understand, on a home net work without any open ports, it’s not very useful at all.
On general DNS resolver options,check enable python module
Uncheck DHCP registration. as I understand, this option does not go well with PF blocker and causes DNS resolve to stop and reload often causing a DNS bottleneck.
Last on the PFblocker general settings, I would change your corn settings from every hour to once a day. It’s been my experience in the past that if you query these lists, too often, they will block you.
I hope this helps you out. -
@uglybrian said in pfblocker working on ip but not DNS, not sure how to fix:
elp. Expanding on Gertjan post. You need to have your network devices use local PFsense DNS in order for PF blocker DNSBL to be useful. Sometimes you have to force your devices and apps to do this. They will happily default to the DNS provider that has paid the company of that particular app or OS to be their default DNS. So as a start I would add blocking external client DNS queries to your firewall rules. Once these rules are in. Reset your state table. You can find the rules on the PF sense dashboard. Go to help, then click on PF sense book. From the book scroll down to the bottom until you see recipes. From there, click on DNS, and then blocking external DNS queries to get your rule set. You will also want to start learning about doh and dot. Hopefully this will give you the blocking that you are looking for. Also, even though you didn’t ask for it I’m going to suggest some settings that I think will help you at this stage. Looking at your pics that you posted.
For the time being turn off snort, as I understand, on a home net work without any open portsHi
@Uglybrian @Gertjan
I did a factory reset and issue was fixed.
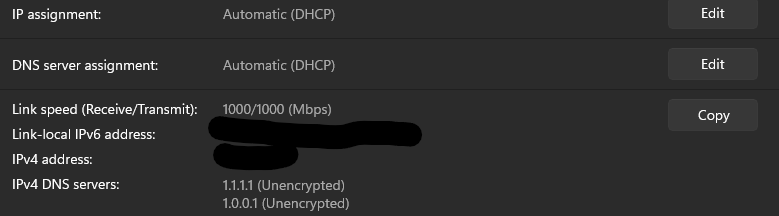
My PC (and all other devices as I dont manually set DNS) is set to use Automatic (DHCP) DNS server. I think during my initial configuration I had set the cloudflare dns as secondary DNS resolvers for pfsense. After removing these secondary DNS resolvers, my network was still using them. During the factory reset process, I declined to enter any secondary DNS server IPs and the resulting setup used the pfsense DNS resolver.Thanks
-
@uglybrian
Hello again,I went and followed some of the advice you gave. So teh recipe book mentioned DoT and DoH. Before I got started this project, I was using my PC settings to specify the 1.1.1.1 DNS and to use DoH. From what I read in the recipe it looks like theres no point in encrypting DNS queries to my own resolver?
I guess if you use a public resolver wanting to encrypt your DNS queries makes more sense?
Actually to test my firewall rule, I set my pc's IPv4 DNS settings to 1.1.1.1 and I still got through. I will check my configuration again
-
Nevermind, external DNS firewall rules started working after a few minutes
Also, I found this page on how to configure the DoT and followed the guide
-
@canaryforge said in pfblocker working on ip but not DNS, not sure how to fix:
it looks like theres no point in encrypting DNS queries to my own resolver?
If you don't trust your own network, the Wifi, cables, switches and router (pfSense) you could consider encrypting the DNS locally.
Be aware : You should use set up unbound to use a trusted certificate (from for example Letsencrypt) and indicate your pfSense hostname which must be in the certificate SAN list.
See the final note here.Without extra software, Windows 10 and below can't use DoT. From what I've read, Windows 11 is capable.
-
Interesting, thanks for this. So what is the process being done here between external DNS and my resolver. Does it go something like pfSense will use any cached resolutions first, and if the entry is not there, pfsense will query the external dns provider and then save to cache?
-
@canaryforge said in pfblocker working on ip but not DNS, not sure how to fix:
Does it go something like pfSense will use any cached resolutions first, and if the entry is not there, pfsense will query the external dns provider and then save to cache?
100 % exact.